
Written by Ivan Milenkovic, Vice President Threat Expertise EMEA, Qualys
For the higher a part of the final decade,we’ve engaged in a snug fiction round safety and improvement. If we might solely “shift left” and get builders to take a modicum extra duty for safety alongside their coding, testing and infrastructure deployment, the digital world would change into a safer, quicker and cheaper place. As a substitute, the elemental battle between pace and safety has bought worse.
Why did this fail? Builders are below crushing stress. The traditional triangle of mission administration – Quick, Good, Low cost; choose two – has been smashed to items.
Companies demand quick, good, low cost and safe. When push involves shove, “quick” all the time wins. On the identical time, we pushed an excessive amount of cognitive load onto builders who have been already drowning.
Once they select to make use of public container pictures to hurry up improvement, they’re making an attempt to satisfy their objectives, however they’re additionally open to potential threat. So how can we perceive what the actual downside is, after which work to resolve that?
Enterprise calls for beat safety suggestions
There’s a pervasive narrative within the safety business that builders are lazy or careless. That is completely not true. Builders will not be lazy; they’re overloaded, pragmatic professionals reacting to the incentives positioned earlier than them. If their bonus relies on transport options by Friday and the safety scan takes 4 hours to run and blocks the construct, they may discover a means across the scan.
Companies demand outcomes quicker and quicker, which has created an atmosphere the place safety protocols are seen as a barrier to productiveness moderately than an integral a part of engineering. When safety instruments are noisy, sluggish, and disconnected from the workflow, they’re a barrier.
Nevertheless, the results of that is that organisations have misplaced management of what’s truly working of their environments. We now have pipelines that deploy code robotically, infrastructure that scales up and down with out human intervention, and AI brokers that may now write and execute their very own scripts.
Into this high-speed, automated chaos, we deal with public registries like curated libraries, assuming that as a result of a picture is on Docker Hub, it should be secure. However pulling a container from a public registry like Docker Hub is a belief choice.
The likes of Docker, Amazon, Google and Microsoft all function public container registries, so there’s a pure assumption that they’re secure.
This belief is misplaced. By the point that container picture makes it to the deployment pipeline, it’s already a trusted artifact, baked into the applying.
The 2026 Forrester Wave™ for Cloud-Native Utility Safety Platforms (CNAPP) offers goal evaluation round cloud safety.
Discover out why Qualys is without doubt one of the leaders out there at present.
The 34,000 Picture Actuality Test
Qualys Risk Analysis Unit (TRU) just lately performed an exhaustive evaluation of over 34,000 container pictures pulled from public repositories to see what is admittedly occurring beneath the manifest.
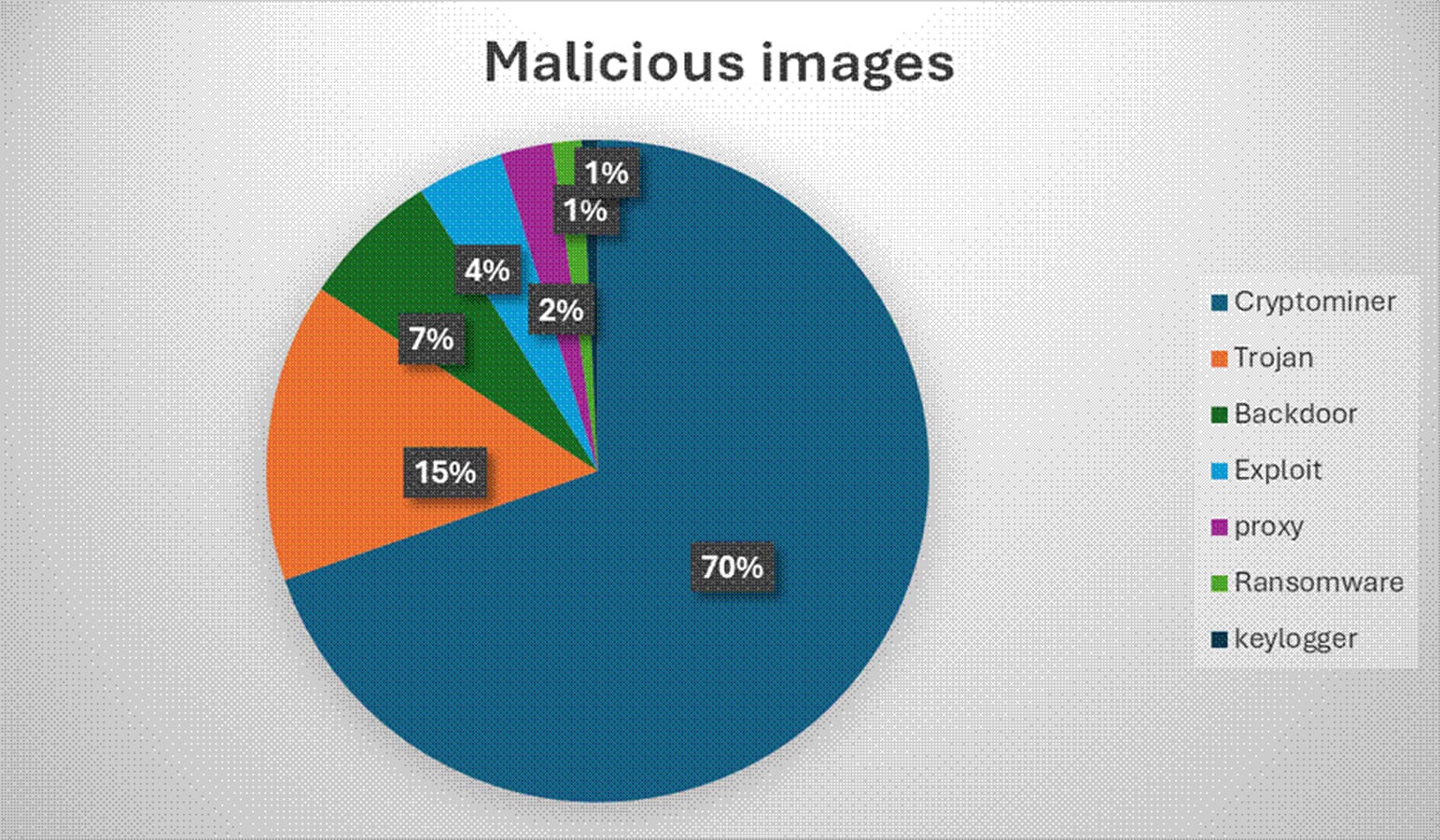
Of that whole, round 2,500 pictures – roughly 7.3 p.c of the pattern – have been malicious. Of the malicious pictures, 70 p.c contained cryptomining software program.
On high of this, 42 p.c of pictures contained greater than 5 secrets and techniques that could possibly be used to get entry to different sources or accounts. This contains worthwhile gadgets like AWS entry keys, GitHub API tokens, and database credentials baked immediately into the picture layers.
In our evaluation, the most important points round malicious containers are nonetheless quite simple. Typosquatting is without doubt one of the most typical strategies that attackers use to get their malicious containers downloaded. The usual recommendation to “examine the spelling” is important, sure, however it is usually a low-energy response to a high-stakes downside.
Telling a developer to “be extra cautious” is just not a safety technique. Whereas public registries are useful for pace, we shouldn’t be letting builders pull from public registries in any respect.
In a mature atmosphere, each exterior picture must be proxied by means of an inside artifact repository that acts as a quarantine zone. But that want for pace is just not going to go away. As a substitute, we’ve to work on assist builders transfer quicker whereas preserving safety in place.
This does imply extra work for the infrastructure crew, however that work ought to allow builders to maneuver forward quicker and with much less threat.
Shift down
The logic is that it’s cheaper to repair a bug throughout design or coding than in manufacturing. Due to this fact, transferring safety earlier within the Software program Growth Life Cycle (SDLC) ought to scale back dangers later. Whereas this is smart in principle, it asks builders to scan their very own code, examine their very own dependencies, and handle their very own infrastructure.
In actuality, we simply shifted the ache onward. It asks builders to handle vulnerabilities, configuration hardening, secret detection, compliance auditing, and so forth. On the identical time, these builders are measured totally on function velocity.
“Shift left” was speculated to make safety collaborative. As a substitute, it merely moved the issue into each developer’s IDE. To repair this downside, we’ve to make safety inside infrastructure the default, moderately than by design.
This includes actual collaboration between builders and safety – builders have to know what they wish to obtain and what will probably be required of what they construct, whereas safety should work round these necessities to allow them to be delivered securely. Each groups are accountable, however they each should work on the pace that the enterprise wants.
In observe, we will create a “golden path” for builders. In the event that they use the usual templates, the pre-approved base pictures, and the official CI pipelines, safety is free. In the event that they wish to go “off-road” and construct one thing customized, then they should do the extra work of safety opinions and guide configurations.
That is additionally one thing that must be flagged again to the enterprise from the beginning, so safety and improvement current a united entrance round what the price is.
Taking this strategy incentivises safe deployment by making it the trail of least resistance. It strikes the duty down the stack to the infrastructure layer, managed by a specialised Platform Engineering crew. And if one thing totally different is required, that work will be achieved collaboratively to make sure it’s proper first time, moderately than resulting in extra points that should be remediated.
For instance, as an alternative of asking a developer to please allow versioning on a particular S3 bucket, the platform crew writes a coverage utilizing Terraform modules, Crossplane compositions, or Open Coverage Agent that merely does not enable a bucket to exist with out versioning. The developer actually can’t make the error.
The platform corrects it robotically or rejects the request. Equally, builders should not have to recollect container scanning of their workflows, the CI pipeline ought to do it robotically. The admission controller ought to reject non-compliant pictures earlier than they ever hit a cluster. The developer does not must know the way the scan works, solely that in the event that they attempt to deploy a essential vulnerability, the door will probably be locked.
“Shift down” additionally means automating the repair. For example if a vulnerability is present in a base picture, the platform ought to robotically generate a Pull Request to improve it. If a runtime safety device detects a container behaving badly (e.g., spawning a shell for persistence), it should not simply ship an alert. It ought to kill the pod and isolate the node autonomously.
Slightly than sticking with present methods of working throughout safety and improvement, we’ve to react to what’s taking place. This may imply we essentially change how we function throughout groups.
If we proceed with the “shift left” mentality of piling cognitive load onto builders, we’ll fail. We are going to burn them out, and they’re going to bypass our controls merely to allow them to get what must be achieved for the enterprise.
As a substitute, safety must be proactive round implement and assist the correct platforms for the enterprise, to allow them to be made safe robotically.
Sponsored and written by Qualys.


