
A cross-site scripting (XSS) flaw within the web-based management panel utilized by operators of the StealC info-stealing malware allowed researchers to watch lively classes and collect intelligence on the attackers’ {hardware}.
StealC emerged in early 2023 with aggressive promotion on darkish net cybercrime channels. It grew in reputation on account of its evasion and intensive information theft capabilities.
Within the following years, StealC’s developer added a number of enhancements. With the discharge of model 2.0 final April, the malware creator launched Telegram bot help for real-time alerts and a brand new builder that might generate StealC builds primarily based on templates and customized information theft guidelines.
Round that point, the supply code for the malware’s administration panel was leaked, giving researchers a possibility to research it.
CyberArk researchers additionally found an XSS flaw that allowed them to gather browser and {hardware} fingerprints of StealC operators, observe lively classes, steal session cookies from the panel, and hijack panel classes remotely.
“By exploiting the vulnerability, we have been capable of determine traits of the menace actor’s computer systems, together with common location indicators and laptop {hardware} particulars,” the researchers say.
“Moreover, we have been capable of retrieve lively session cookies, which allowed us to realize management of classes from our personal machines.”
Supply: CyberArk
CyberArk didn’t disclose particular particulars concerning the XSS vulnerability to stop StealC operators from rapidly pinpointing and fixing it.
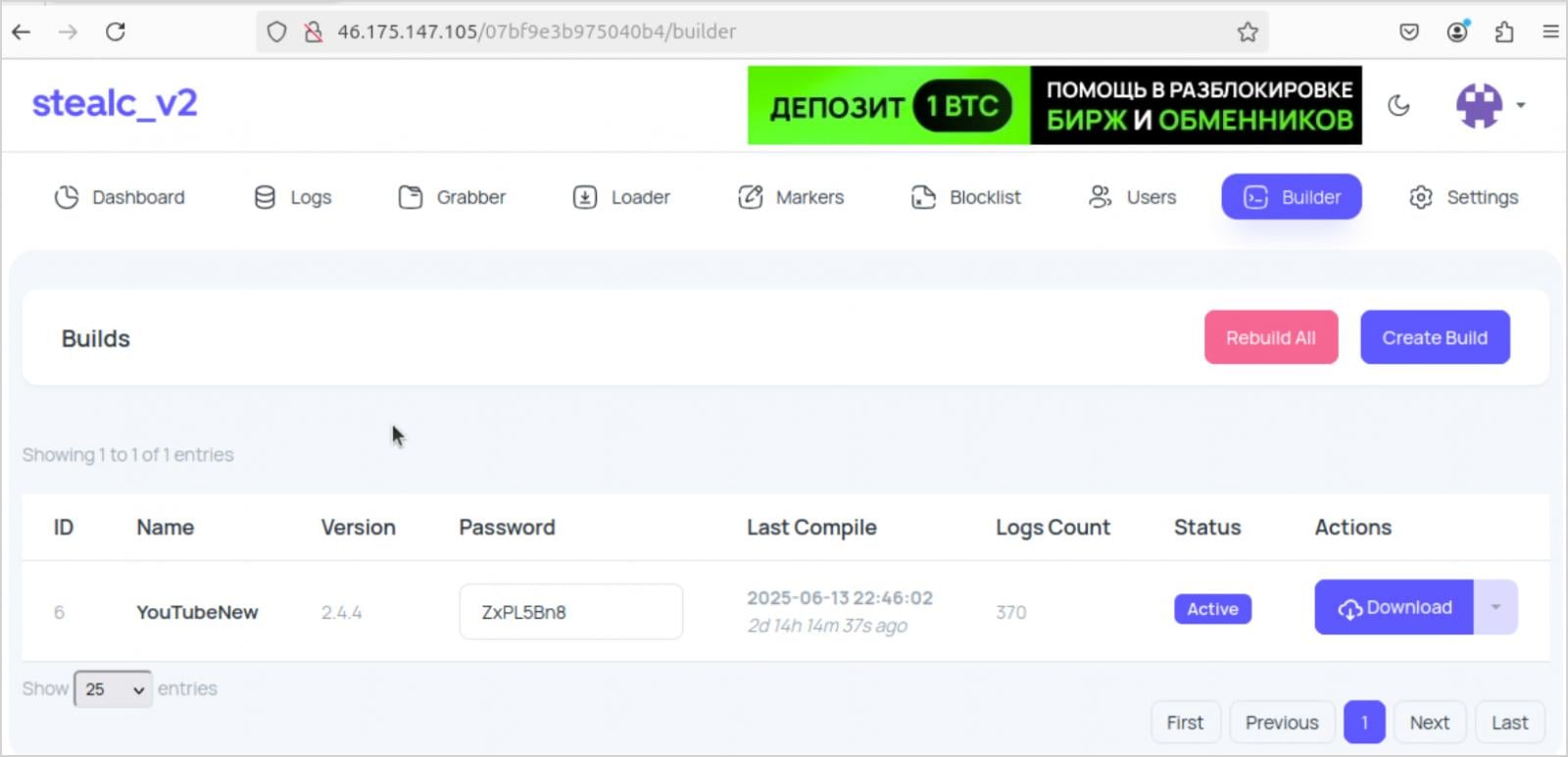
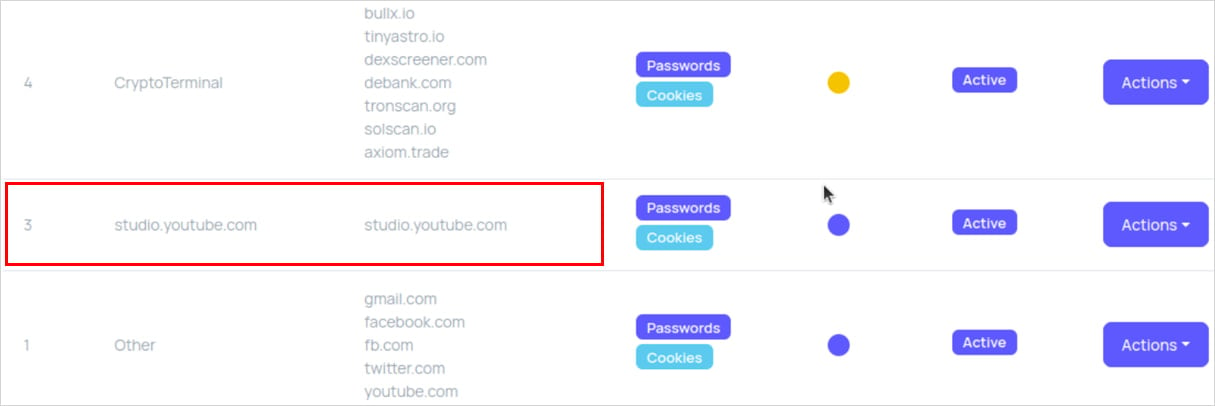
The report highlights one case of a StealC buyer, known as ‘YouTubeTA’, who hijacked previous, reliable YouTube channels probably utilizing compromised credentials, and planted infecting hyperlinks.
The cybercriminal ran malware campaigns all through 2025, amassing over 5,000 sufferer logs, stealing roughly 390,000 passwords and 30 million cookies (most of them non-sensitive).
Supply: CyberArk
Screenshots from the menace actor’s panel point out that the majority infections occurred when victims looked for cracked variations of Adobe Photoshop and Adobe After Results.
By leveraging the XSS flaw, the researchers may decide that the attacker used an Apple M3-based system with English and Russian language settings, used the Japanese European time zone, and was accessing the web by way of Ukraine.
Their location was uncovered when the menace actor forgot to attach the StealC panel via VPN. This revealed their actual IP deal with, which was linked to Ukrainian ISP TRK Cable TV.
CyberArk notes that malware-as-a-service (MaaS) platforms allow speedy scaling but in addition pose a big threat of publicity to menace actors.
BleepingComputer has contacted CyberArk to ask why they selected to reveal the StealC XSS flaw now. Researcher Ari Novick stated that they hope to trigger disruption to the operation, since there was “a spike in current months within the variety of StealC operators, probably in response to the drama round Lumma a few months in the past.”
“By posting the existence of the XSS we hope to trigger a minimum of some disruption in the usage of the StealC malware, as operators re-evaluate utilizing it. Since there at the moment are comparatively many operators, it appeared like a first-rate alternative to doubtlessly trigger a reasonably important disruption within the MaaS market.”
It is price range season! Over 300 CISOs and safety leaders have shared how they’re planning, spending, and prioritizing for the yr forward. This report compiles their insights, permitting readers to benchmark methods, determine rising tendencies, and evaluate their priorities as they head into 2026.
Find out how high leaders are turning funding into measurable influence.




