
The Zero Day Initiative is providing a $1 million reward to safety researchers who will reveal a zero-click WhatsApp exploit at its upcoming Pwn2Own Eire 2025 hacking contest.
The report bounty targets zero-click safety flaws that enable code execution with out person interplay on the messaging platform utilized by greater than three billion folks worldwide.
Meta, alongside Synology and QNAP, is co-sponsoring the Pwn2Own Eire 2025 competitors, which is able to happen from October 21 to October 24 in Cork, Eire.
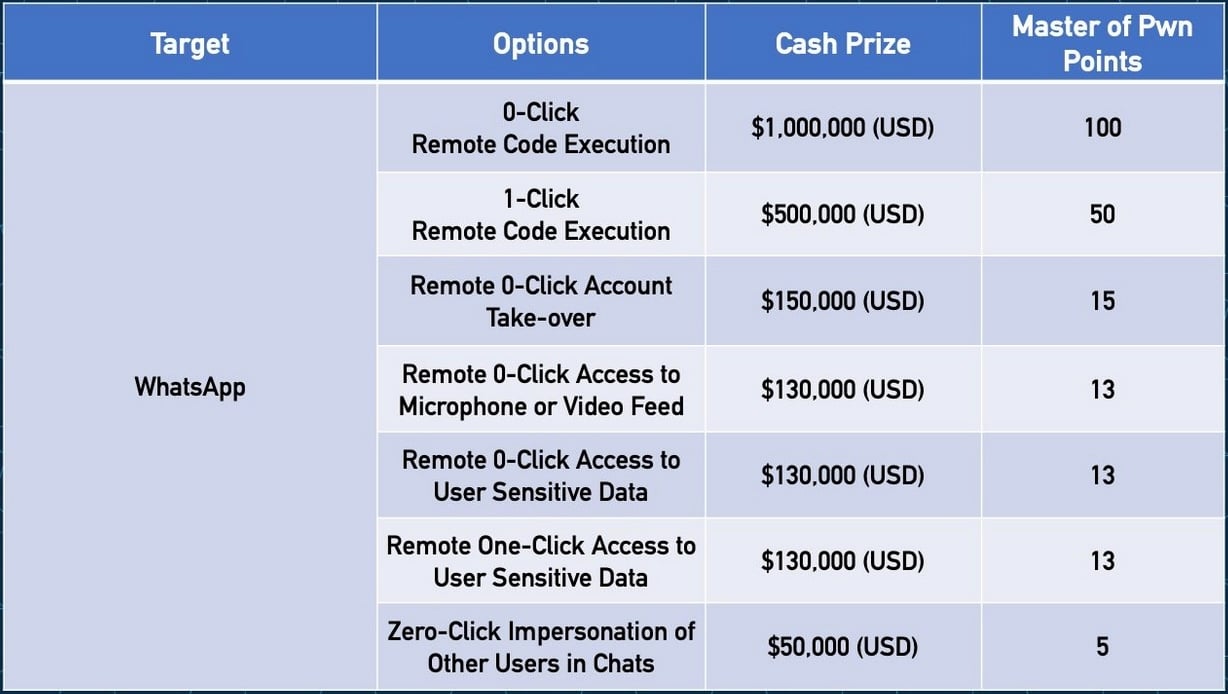
“As you might need guessed from the title, we’re excited to announce that Meta is co-sponsoring this 12 months’s occasion, and they’re hoping to see some nice WhatsApp exploits. They’re so excited for it, we’re placing up $1,000,000 for a 0-click WhatsApp bug that results in code execution,” the Zero Day Initiative introduced Thursday.
“We additionally may have lesser money awards for different WhatsApp exploits, so be sure you try the Messaging part for full particulars. We launched this class final 12 months, however nobody tried it. Maybe a quantity with two commas will present the wanted motivation.”
The competition options eight classes focusing on cellphones, messaging apps, house networking tools, good house units, printers, community storage methods, surveillance tools, and wearable know-how, together with Meta’s Ray-Ban Good Glasses and Quest 3/3S headsets, in addition to Samsung Galaxy S25, Google Pixel 9, and Apple iPhone 16 flagship smartphones.
The ZDI has additionally expanded the assault vectors for the cell class to incorporate USB port exploitation for cell units, requiring contestants to compromise locked telephones by means of bodily connections. Conventional wi-fi protocols, resembling Wi-Fi, Bluetooth, and near-field communication, stay legitimate assault strategies.
Registration closes on October 16 at 5 p.m. Irish Normal Time, with the competition order decided by a random drawing. The Zero Day Initiative operates the occasion to determine vulnerabilities earlier than malicious actors can exploit them, coordinating accountable disclosure with affected distributors.
After the failings are exploited throughout Pwn2Own occasions, distributors have 90 days to launch safety updates earlier than Development Micro’s Zero Day Initiative publicly discloses them.
Final 12 months’s Pwn2Own Eire occasion awarded $1,078,750 for over 70 distinctive zero-day vulnerabilities, with Viettel Cyber Safety amassing $205,000 for flaws demonstrated in QNAP NAS, Sonos audio system, and Lexmark printers.



