
Prison IP (criminalip.io), the AI-powered menace intelligence and assault floor monitoring platform developed by AI SPERA, is now formally built-in into Palo Alto Networks’ Cortex XSOAR.
The mixing embeds real-time exterior menace context, publicity intelligence, and automatic multi-stage scanning immediately into Cortex XSOAR’s orchestration engine, giving safety groups increased incident accuracy and sooner response than typical log-centric approaches.
For Palo Alto Networks, extensively thought to be the worldwide chief in cybersecurity, Cortex XSOAR is a central hub for SOC automation. With Prison IP added as an integration by way of the Cortex Market,
Cortex XSOAR can now supply customers the flexibility to judge suspicious IPs and domains not solely by way of static fame information but additionally by way of behavioral indicators, publicity historical past, infrastructure correlations, and AI-driven menace scoring, with out requiring further techniques or analyst-driven lookups.
AI Context to Deal with the Limits of Log-Solely Incident Response
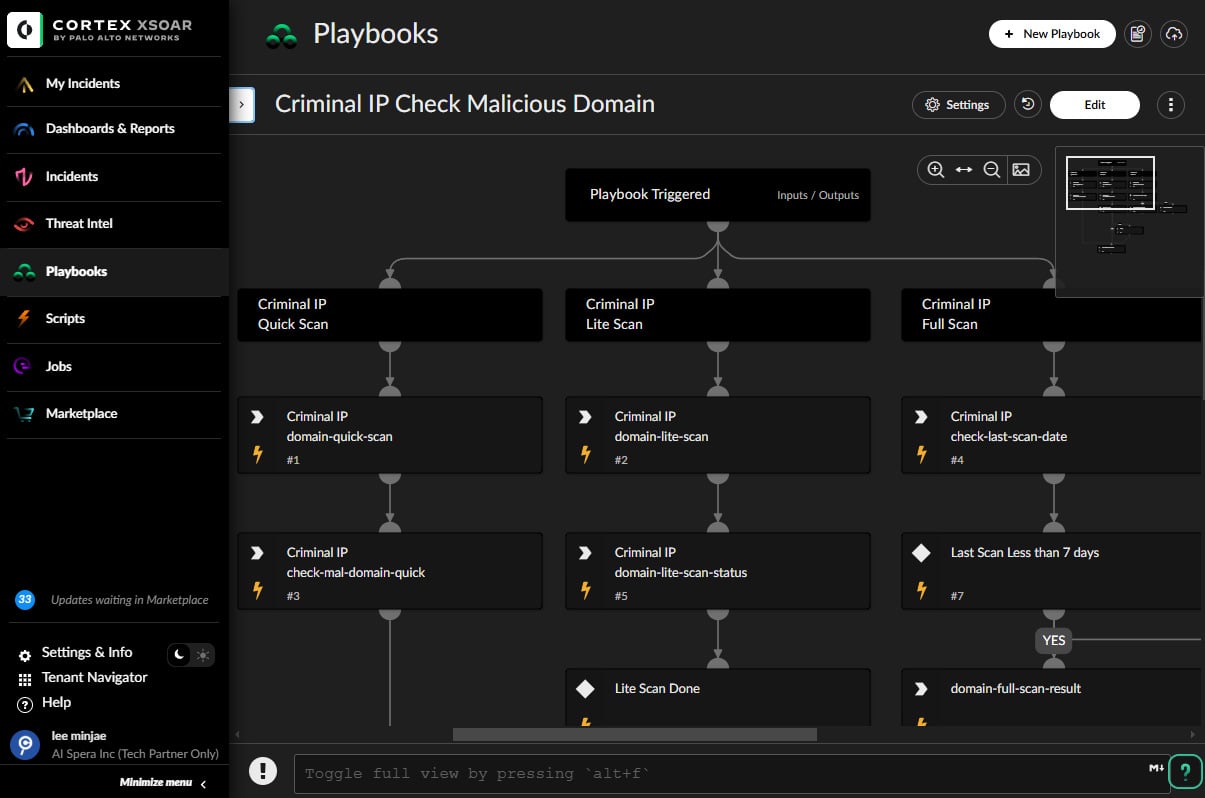
Fashionable SOC groups face overwhelming alert volumes, but conventional enrichment nonetheless relies on static fame feeds with restricted context, usually lacking port publicity, CVE ties, certificates reuse, DNS modifications, or anonymization conduct.
Prison IP fills this hole by constantly analyzing world internet-facing property and correlating IP conduct, area exercise, SSL/TLS information, port states, CVE publicity, IDS hits, and masking indicators.
When an alert consists of an IP or area, Cortex XSOAR can routinely pull this enriched intelligence into the lively incident through a playbook, permitting analysts to evaluate intent and severity with out leaving Cortex SOAR.
Entry Prison IP’s Menace Intelligence wanted to proactively establish, analyze, and reply to rising threats.
Powered by AI and OSINT, it delivers menace scoring, fame information, and real-time detection of a wide selection of malicious indicators, starting from C2 servers and IOCs to masking companies like VPNs, proxies, and nameless VPNs, throughout IPs, domains, and URLs. Its API-first structure ensures seamless integration into safety workflows to spice up visibility, automation, and response.
Multi-Stage Scanning and Exterior Publicity Linking
Cortex XSOAR playbooks can set off Prison IP’s automated three-stage scanning workflow: starting with a Fast Lookup, escalating to a Lite Scan, after which performing a Full Scan for full assault floor evaluation.
Full Scan outcomes are delivered as structured stories inside Cortex XSOAR, with generic polling making certain the workflow continues with out handbook effort.
Past alert-driven enrichment, the combination additionally hyperlinks inside telemetry with open-internet intelligence offering historic conduct, C2 relationships, anonymization indicators, abuse information, and SSL correlations for every indicator.
Cortex XSOAR can even schedule Micro Assault Floor Administration scans to evaluate uncovered ports, certificates validity, susceptible companies, and outdated software program, providing light-weight, steady ASM capabilities that assist organizations establish weaknesses earlier than they’re exploited.
Accelerating the Shift Towards Intelligence-Pushed Autonomous Safety

The mixing between Palo Alto Networks and Prison IP displays a broader development towards autonomous safety operations. By combining Cortex XSOAR’s automation and orchestration capabilities with Prison IP’s real-time exterior evaluation, SOC groups can automate choices that beforehand required handbook analysis throughout a number of intelligence sources.
This reduces response occasions, improves the accuracy of incident classification, and minimizes analyst fatigue—points which have grown extra extreme as alert volumes and AI-generated threats proceed to rise.
Prison IP is already current on Azure, AWS, and Snowflake marketplaces and maintains integrations with greater than 40 safety distributors, together with Cisco, Fortinet, and Tenable. Its growth into the Palo Alto Networks ecosystem units the inspiration for additional integrations throughout XDR and cloud safety options.
AI SPERA CEO Byungtak Kang said that the combination “demonstrates the rising significance of AI-driven menace intelligence and publicity analytics in enterprise safety operations,” including that Prison IP goals to play a central position in serving to organizations transition towards totally autonomous protection architectures.
Study extra: https://cortex.market.pan.dev/market/particulars/CriminalIP/
Sponsored and written by Prison IP.


