
An ASUS Reside Replace vulnerability tracked as CVE-2025-59374 has been making the rounds in infosec feeds, with some headlines implying latest or ongoing exploitation.
The CVE paperwork a historic supply-chain assault in an Finish-of-Life (EoL) software program product, not a newly rising menace.
Not all CISA KEVs sign urgency
Current protection of CVE-2025-59374 has framed the problem as a newly related safety threat following its addition to CISA’s Identified Exploited Vulnerabilities (KEV) catalog.
A better look, nonetheless, reveals the truth is far more nuanced.
The CVE paperwork the 2018-2019 “ShadowHammer” supply-chain assault, wherein maliciously modified ASUS Reside Replace binaries have been selectively delivered to a small variety of focused programs.
The CVE entry for the compromise, now-rated a 9.3 (Crucial) on the CVSS scale, states:
“UNSUPPORTED WHEN ASSIGNED” Sure variations of the ASUS Reside Replace consumer have been distributed with unauthorized modifications launched by way of a provide chain compromise. The modified builds may trigger gadgets assembly particular concentrating on situations to carry out unintended actions. Solely gadgets that met these situations and put in the compromised variations have been affected. The Reside Replace consumer has already reached Finish-of-Assist (EOS) in October 2021, and no at the moment supported gadgets or merchandise are affected by this difficulty.
The ‘unsupported when assigned‘ textual content already means that the CVE was filed for an EoL product.
The first vendor advisory linked to within the CVE entry is from 2019. This advisory moreover hyperlinks to an FAQ: https://www.asus.com/help/faq/1018727/ bearing the final up to date timestamp, 2025/12/06 20:09.
Word, nonetheless, this FAQ 1018727 hyperlink existed in that spot again in 2019 when the advisory was first revealed.
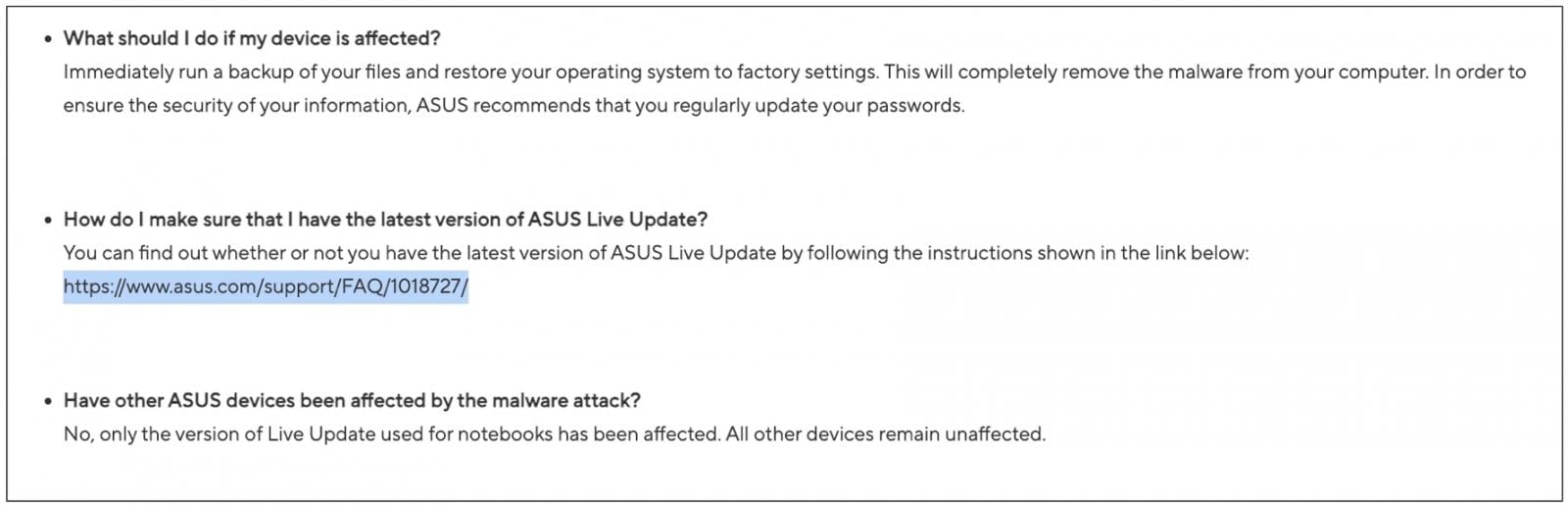
As seen by BleepingComputer, the FAQ web page doesn’t present the first publication timestamp metadata. Slightly, it has merely been up to date this month and reveals the aforementioned December sixth date on the web page.

(BleepingComputer)
The archived pages assist us set up the aim of the web page, and why latest updates made to the web page don’t essentially imply a renewed threat from the 2019 difficulty.
The FAQ entry seems to be ASUS’ placeholder web page, periodically revised to supply info on the improve path, i.e. the newest model customers ought to undertake for the seller’s Reside Replace utility.
Moreover, the web page continues to show (older) remediation steering with screenshots bearing 2019 dates:
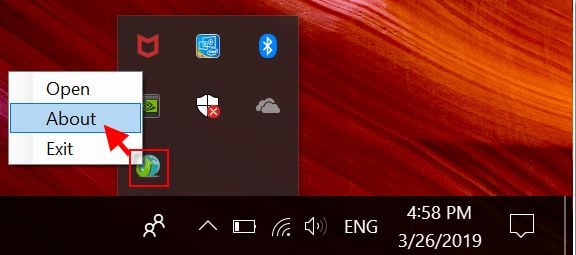
To get extra details about the 2025 CVE project, BleepingComputer reached out to ASUS nicely upfront of publishing however we didn’t hear again.
We moreover reached out to CISA to know what prompted the CVE’s addition to the KEV catalog.
CISA declined to supply further remark, as an alternative pointing BleepingComputer to language in Binding Operational Directive 22-01, which notes:
“Addition of a vulnerability to the KEV catalog doesn’t point out that CISA is observing present lively exploitation. If there’s correct reporting of lively exploitation, any vulnerability, regardless of its age, can qualify for KEV catalog addition”
Taken collectively, the proof suggests the CVE project displays a retrospective classification effort, formally documenting a well known assault that predated CVE issuance.
Sensible steering for customers
You must nonetheless guarantee that you’ve the newest, patched model of the product.
In keeping with the CVE entry, the affected software program, ASUS Reside Replace, reached Finish-of-Assist (EOS) in October 2021, with “no at the moment supported gadgets or merchandise are affected by this difficulty.”
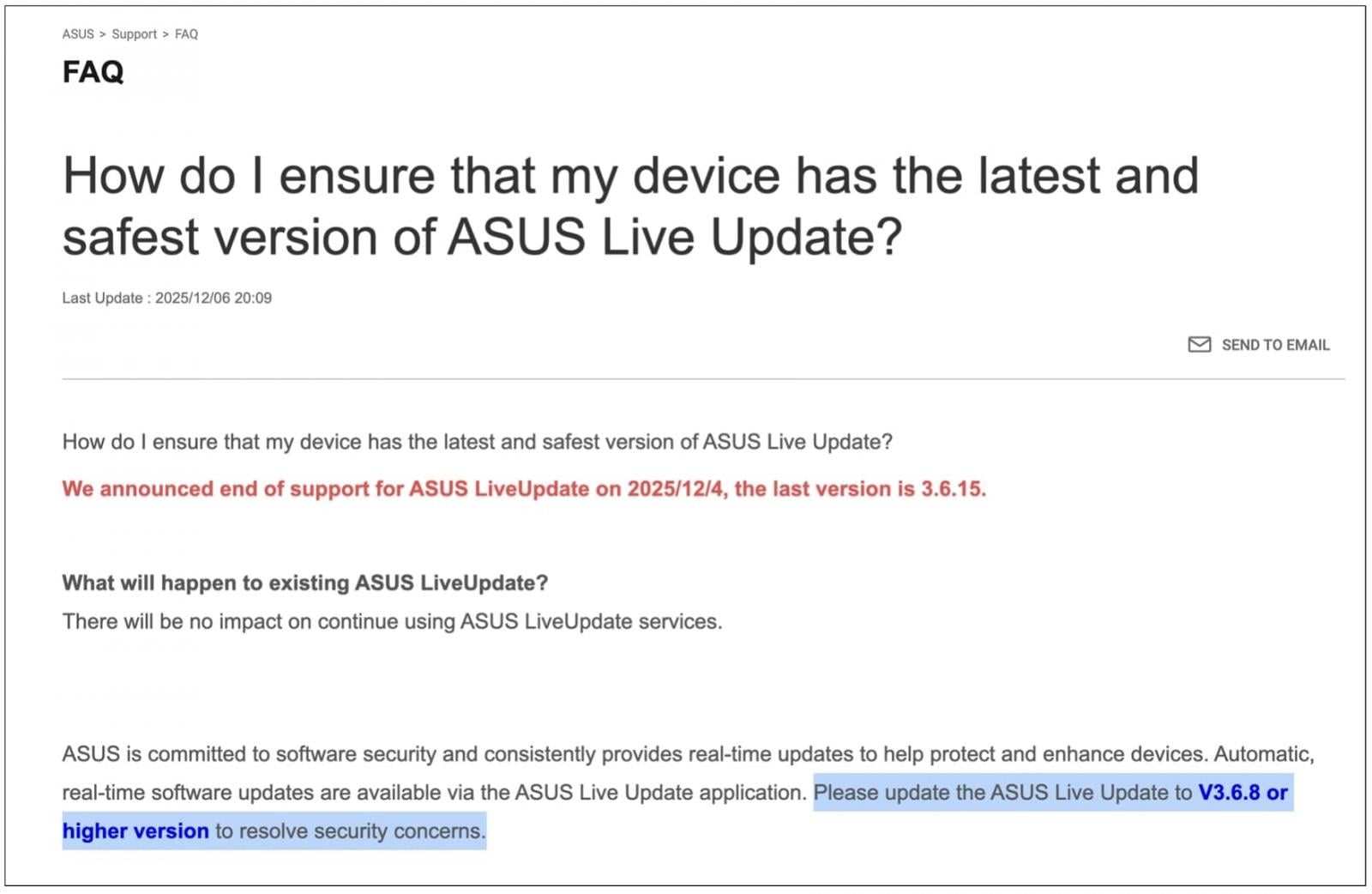
The up to date ASUS FAQ web page from this month, nonetheless, contradicts this wording, implying that the help definitively ended on December 4, 2025:
“We introduced finish of help for ASUS LiveUpdate on 2025/12/4, the final model is 3.6.15.“
(BleepingComputer)
Earlier copies (2019-22) of the FAQ really helpful upgrading to “V3.6.8 or greater model to resolve safety considerations,” as a repair for the problem was applied in that model on the time. That dated recommendation has been left as-is on the up to date FAQ from this month.
The discharge 3.6.15, nonetheless, is now listed because the “final model.” That model apparently existed as early as March 2024 if not earlier than, which means there isn’t any new urgency to improve—opposite to the same old call-to-action following latest provide chain compromises.
CVE-2025-59374 formalizes a well-documented historic assault. FAQ updates, older remediation steering, the utility’s newest launch, and CISA context present the web page was up to date for documentation functions, to not tackle a brand new exploit, impose patching necessities, or sign rapid threat.
Safety groups ought to due to this fact be aware when treating CISA-linked CVEs as pressing, notably for retired software program or long-resolved incidents.
Damaged IAM is not simply an IT downside – the affect ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with fashionable calls for, examples of what “good” IAM appears like, and a easy guidelines for constructing a scalable technique.




