
A newly documented Linux botnet named SSHStalker is utilizing the IRC (Web Relay Chat) communication protocol for command-and-control (C2) operations.
The protocol was invented in 1988, and its adoption peaked in the course of the Nineteen Nineties, turning into the primary text-based immediate messaging resolution for group and personal communication.
Technical communities nonetheless admire it for its implementation simplicity, interoperability, low bandwidth necessities, and no want for a GUI.
The SSHStalker botnet depends on basic IRC mechanics resembling a number of C-based bots and multi-server/channel redundancy as an alternative of recent C2 frameworks, prioritizing resilience, scale, and low value over stealth and technical novelty.
Based on researchers at risk intelligence firm Flare, this strategy extends to different traits of SSHStalker’s operation, like utilizing noisy SSH scans, one-minute cron jobs, and a big back-catalog of 15-year previous CVEs.
“What we really discovered was a loud, stitched-together botnet package that mixes old-school IRC management, compiling binaries on hosts, mass SSH compromise, and cron-based persistence. In different phrases scale-first operation that favors reliability over stealth,” Flare says.
Supply: Flare
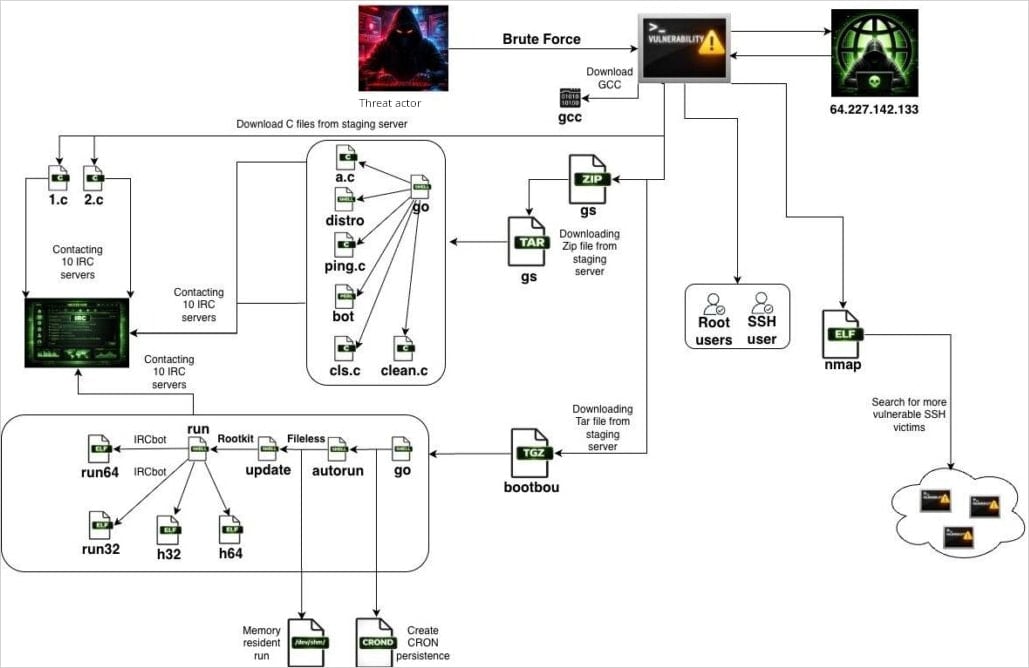
SSHStalker achieves preliminary entry by automated SSH scanning and brute forcing, utilizing a Go binary that masquerades as the favored open-source community discovery utility nmap.
Compromised hosts are then used to scan for extra SSH targets, which resembles a worm-like propagation mechanism for the botnet.
Flare discovered a file with outcomes from practically 7,000 bot scans, all from January, and targeted totally on cloud internet hosting suppliers in Oracle Cloud infrastructure.
As soon as SSHStalker infects a bunch, it downloads the GCC software for compiling payloads on the sufferer system for higher portability and evasion.
The primary payloads are C-based IRC bots with hard-coded C2 servers and channels, which enroll the brand new sufferer within the botnet’s IRC infrastructure.
Subsequent, the malware fetches archives named GS and bootbou, which comprise bot variants for orchestration and execution sequencing.
Persistence is achieved through cron jobs that run each 60 seconds, invoking a watchdog-style replace mechanism that checks whether or not the primary bot course of is operating and relaunches it whether it is terminated.
The botnet additionally comprises exploits for 16 CVEs focusing on Linux kernel variations from the 2009-2010 period. That is used to escalate privileges after the sooner brute-forcing step grants entry to a low-privileged person.
Supply: Flare
Relating to monetization, Flare observed that the botnet performs AWS key harvesting and web site scanning. It additionally consists of cryptomining kits such because the high-performance Ethereum miner PhoenixMiner.
Distributed denial-of-service (DDoS) capabilities are additionally current, although the researchers famous they haven’t but noticed any such assaults. In truth, SSHStalker’s bots presently simply hook up with the C2 after which enter an idle state, suggesting testing or entry hoarding for now.
Flare has not attributed SSHStalker to a selected risk group, although it famous similarities with the Outlaw/Maxlas botnet ecosystem and varied Romanian indicators.
The risk intelligence firm suggests putting monitoring options for compiler set up and execution on manufacturing servers, and alerts for IRC-style outbound connections. Cron jobs with brief execution cycles from uncommon paths are additionally large crimson flags.
Mitigation suggestions embody disabling SSH password authentication, eradicating compilers from manufacturing photos, implementing egress filtering, and proscribing execution from ‘/dev/shm.’
Trendy IT infrastructure strikes quicker than handbook workflows can deal with.
On this new Tines information, learn the way your workforce can scale back hidden handbook delays, enhance reliability by automated response, and construct and scale clever workflows on prime of instruments you already use.




