
A fourth wave of the “GlassWorm” marketing campaign is concentrating on macOS builders with malicious VSCode/OpenVSX extensions that ship trojanized variations of crypto pockets purposes.
Extensions within the OpenVSX registry and the Microsoft Visible Studio Market increase the capabilities of a VS Code-compatible editor by including options and productiveness enhancements within the type of improvement instruments, language help, or themes.
The Microsoft market is the official extension retailer for Visible Studio Code, whereas OpenVSX serves as an open, vendor-neutral different, primarily utilized by editors that don’t help or select to not depend on Microsoft’s proprietary market.
The GlassWorm malware first appeared on the marketplaces in October, hidden inside malicious extensions utilizing “invisible” Unicode characters.
As soon as put in, the malware tried to steal credentials for GitHub, npm, and OpenVSX accounts, in addition to cryptocurrency pockets information from a number of extensions. Moreover, it supported distant entry by means of VNC and may route visitors by means of the sufferer’s machine through a SOCKS proxy.
Regardless of the general public publicity and elevated defenses, GlassWorm returned in early November on OpenVSX after which once more in early December on VSCode.
GlassWorm again on OpenVSX
Koi Safety researchers found a brand new GlassWorm marketing campaign that targets macOS methods solely, a departure from the earlier ones that centered solely on Home windows.
As an alternative of the invisible Unicode seen within the first two waves, or compiled Rust binaries used within the third one, the newest GlassWorm assaults use an AES-256-CBC–encrypted payload embedded in compiled JavaScript within the OpenVSX extensions:
- studio-velte-distributor.pro-svelte-extension
- cudra-production.vsce-prettier-pro
- Puccin-development.full-access-catppuccin-pro-extension
The malicious logic executes after a 15-minute delay, doubtless in an try and evade evaluation in sandboxed environments.
As an alternative of PowerShell, it now makes use of AppleScript, and as an alternative of Registry modification, it makes use of LaunchAgents for persistence. The Solana blockchain-based command-and-control (C2) mechanism stays unchanged, although, and researchers say that there’s additionally infrastructure overlap.
Aside from concentrating on over 50 browser crypto extensions, developer credentials (GitHub, NPM), and browser information, GlassWorm now additionally makes an attempt to steal Keychain passwords.
Moreover, it now contains a new functionality the place it checks for {hardware} cryptocurrency pockets apps like Ledger Dwell and Trezor Suite on the host, and replaces them with a trojanized model.
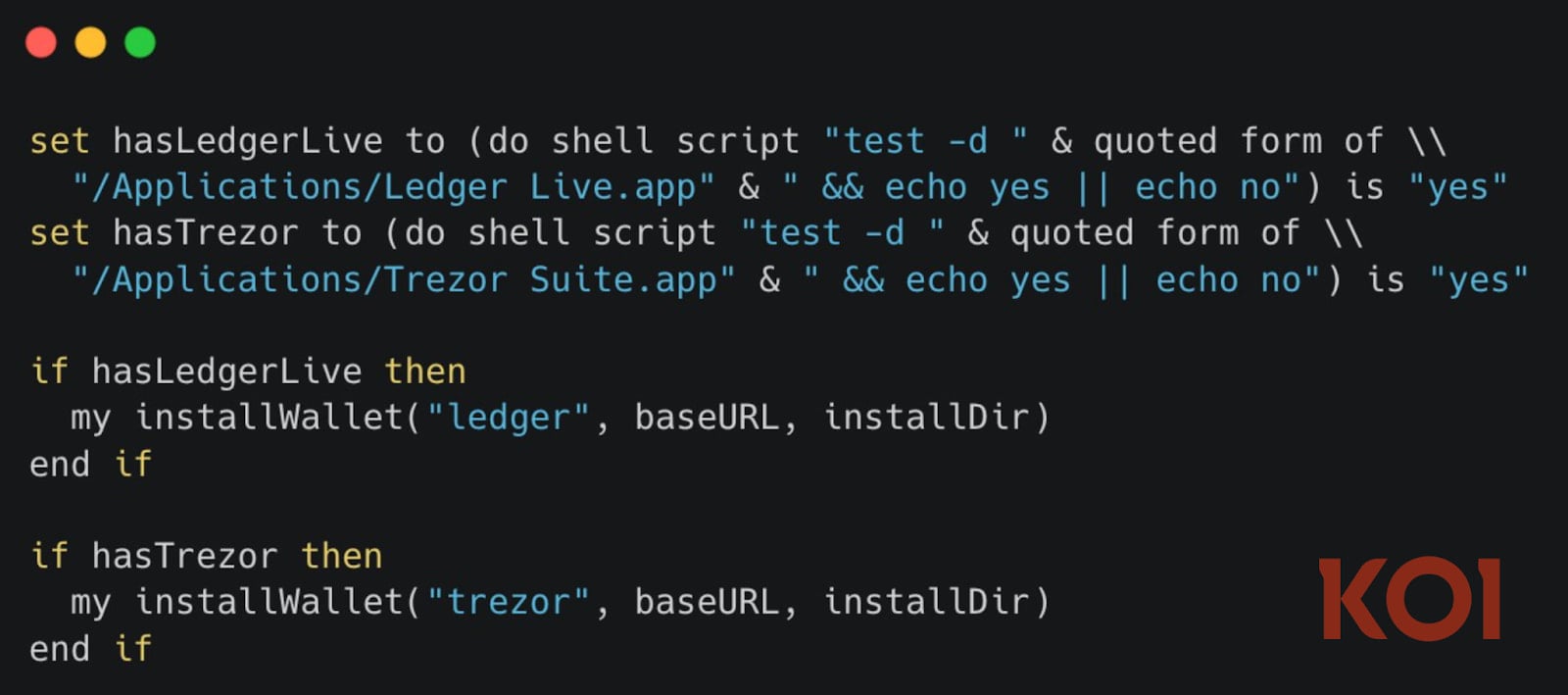
Supply: Koi Safety
Nonetheless, Koi Safety notes that this mechanism is presently failing as a result of the trojanized wallets are returning empty recordsdata.
“This might imply the attacker remains to be getting ready the macOS pockets trojans, or the infrastructure is in transition,” explains Koi Safety.
“The aptitude is constructed and prepared – it is simply ready for payloads to be uploaded. All different malicious performance (credential theft, keychain entry, information exfiltration, persistence) stays absolutely operational.”
When BleepingComputer checked if the malicious extensions have been nonetheless obtainable on OpenVSX, the platform confirmed a warning for 2 of them, informing that their writer was unverified.

Supply: BleepingComputer
The obtain counters present greater than 33,000 installs, however such figures are continuously manipulated by risk actors to make the recordsdata seem extra reliable.
Builders who’ve put in any of the three extensions are beneficial to take away them instantly, reset their GitHub account passwords, revoke their NPM tokens, test their system for indicators of an infection, or reinstall it.




