A most severity vulnerability dubbed “Ni8mare” permits distant, unauthenticated attackers to take management over regionally deployed situations of the N8N workflow automation platform.
The safety subject is recognized as CVE-2026-21858 and has a ten out of 10 severity rating. In accordance with researchers at information safety firm Cyera, there are greater than 100,000 weak n8n servers.
n8n is an open-source workflow automation software that permits customers to attach purposes, APIs, and companies into complicated workflows by way of a visible editor. It’s primarily used to automate duties and helps integrations with AI and huge language mannequin (LLM) companies.
It has over 50,000 weekly downloads on npm and greater than 100 million pulls on Docker Hub. It’s a fashionable software within the AI house, the place it’s used to orchestrate LLM calls, construct AI brokers and RAG pipelines, and automate information ingestion and retrieval.
Ni8mare particulars
The Ni8mare vulnerability provides an attacker entry to information on the underlying server by executing sure form-based workflows.
“A weak workflow might grant entry to an unauthenticated distant attacker. This might end in publicity of delicate info saved on the system and should allow additional compromise relying on deployment configuration and workflow utilization,” n8n builders say.
Cyera researchers found the Ni8mare vulnerability (CVE-2026-21858) and reported it to n8n on November 9, 2025. They are saying that the safety subject is a content-type confusion in the way in which n8n parses information.
n8n makes use of two capabilities to course of incoming information primarily based on the ‘content-type’ header configured in a webhook, the part that triggers occasions in a workflow by listening for particular messages.
When the webhook request is marked as multipart/form-data, n8n treats it as a file add and makes use of a particular add parser that saves information in randomly generated non permanent places.
“This implies customers can’t management the place information find yourself, which protects in opposition to path traversal assaults.”
Nevertheless, for all different content material sorts, n8n makes use of its commonplace parser as an alternative.
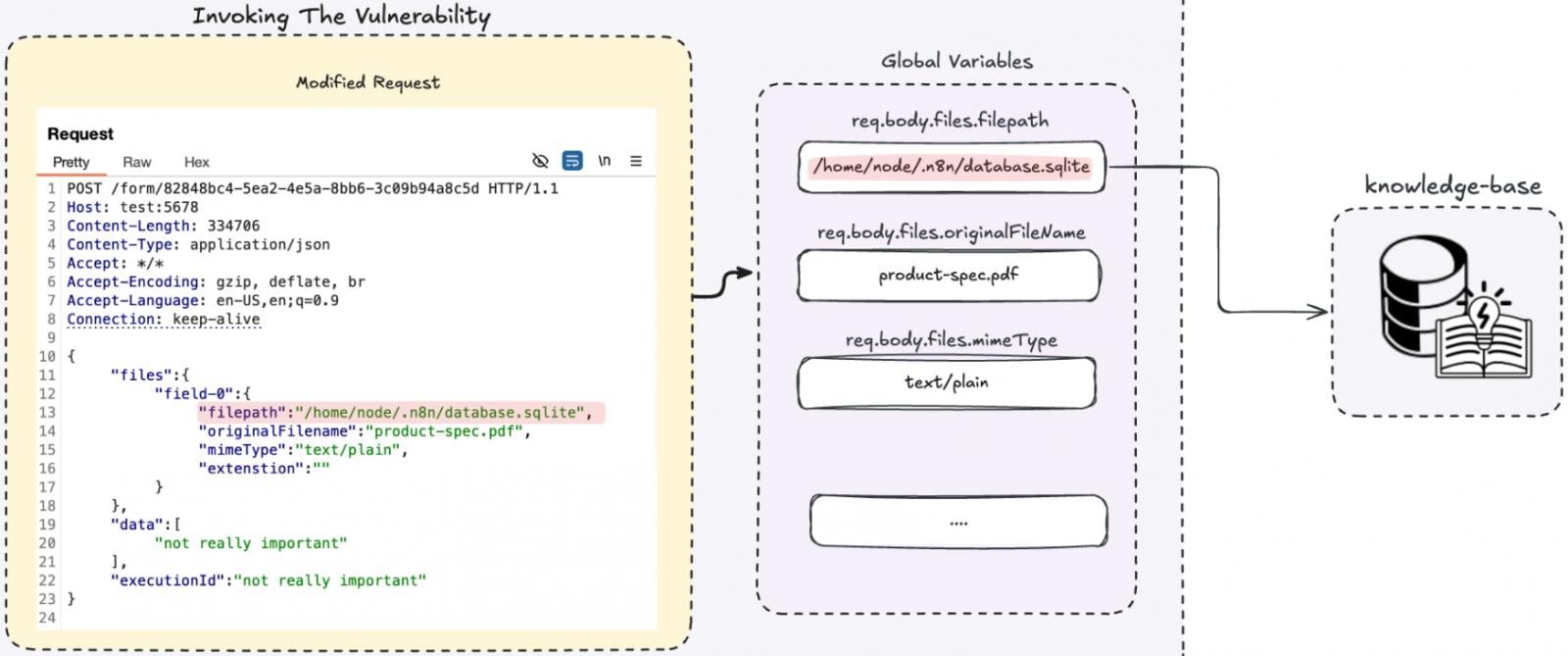
Cyera discovered that by setting a special content material kind, comparable to utility/json, an attacker can bypass the add parser.
On this state of affairs, n8n nonetheless processes file-related fields however does so with out verifying that the request truly comprises a sound file add. This permits the attacker to totally management the file metadata, together with the file path.
.jpg)
Supply: Cyera
“Since this operate known as with out verifying the content material kind is multipart/form-data, we management all the req.physique.information object. Meaning we management the filepath parameter – so as an alternative of copying an uploaded file, we can copy any native file from the system,” explains Cyera.
This permits studying arbitrary information from an n8n occasion, which may expose secrets and techniques by including inside information into the workflow’s information base.
Cyera says this may be abused to show secrets and techniques saved on the occasion, inject delicate information into workflows, forge session cookies to bypass authentication, and even execute arbitrary instructions.
Supply: Cyera
Cyera emphasizes that n8n usually shops API keys, OAuth tokens, database credentials, cloud storage entry, CI/CD secrets and techniques, and enterprise information, making it a central automation hub.
n8n builders say that there is no such thing as a official workaround accessible for Ni8mare, however one mitigation is to limit or disable publicly accessible webhook and kind endpoints.
The beneficial motion is to replace to n8n model 1.121.0 or a newer one.




