
The North Korean hacker group Konni (Opal Sleet, TA406) is utilizing AI-generated PowerShell malware to focus on builders and engineers within the blockchain sector.
Believed to be related to APT37 and Kimsuky exercise clusters, Konni has been energetic since not less than 2014 and has been seen focusing on organizations in South Korea, Russia, Ukraine, and numerous international locations in Europe.
Based mostly on samples analyzed by Examine Level researchers, the menace actor’s newest marketing campaign focuses on targets within the Asia-Pacific area, because the malware was submitted from Japan, Australia, and India.
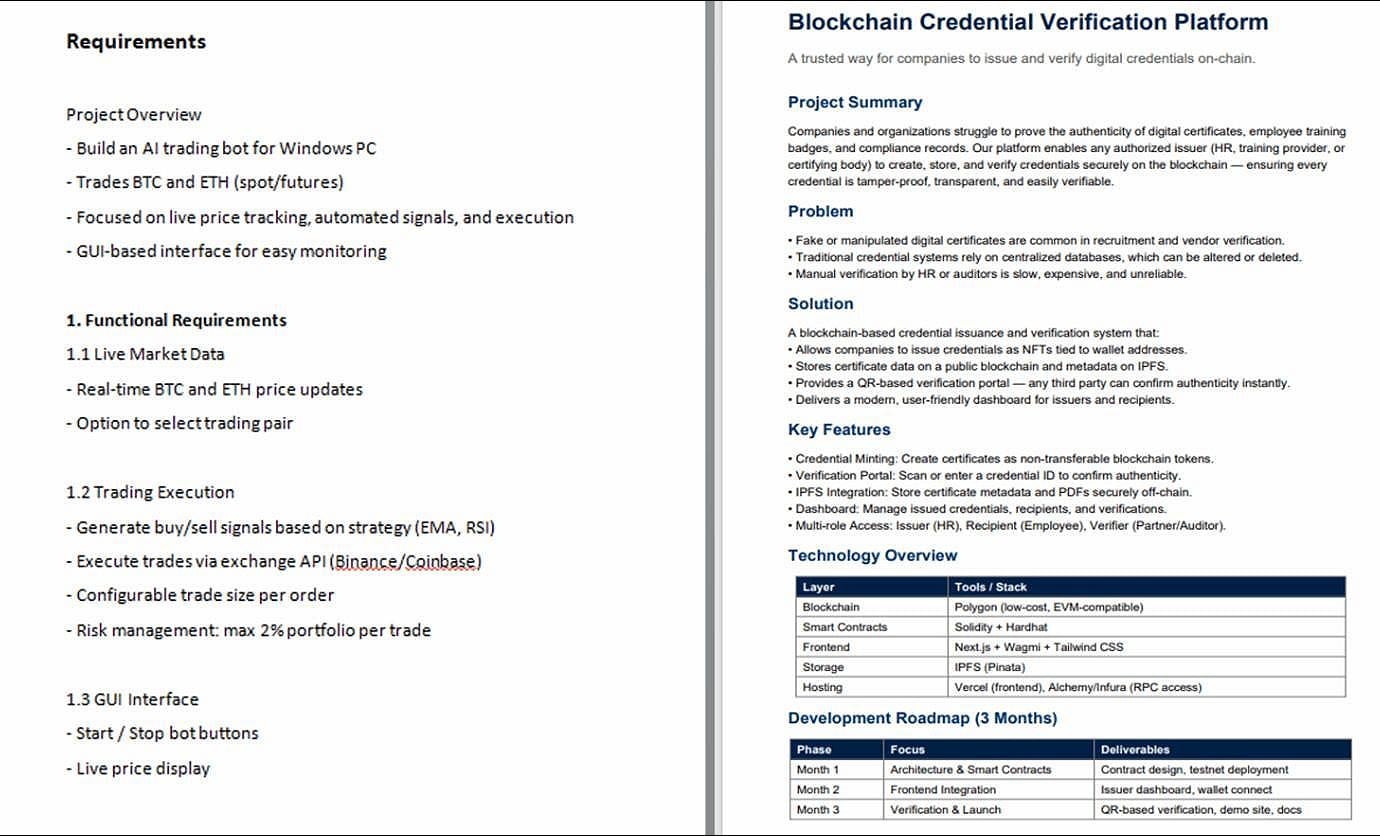
The assault begins with the sufferer receiving a Discord-hosted hyperlink that delivers a ZIP archive containing a PDF lure and a malicious LNK shortcut file.
The LNK runs an embedded PowerShell loader that extracts a DOCX doc and a CAB archive containing a PowerShell backdoor, two batch information, and a UAC bypass executable.
Launching the shortcut file causes the DOCX to open and to execute one batch file included within the cupboard file.
Supply: Examine Level
The lure DOCX doc means that the hackers wish to compromise growth environments, which might present them “entry to delicate belongings, together with infrastructure, API credentials, pockets entry, and in the end cryptocurrency holdings.”
The primary batch file creates a staging listing for the backdoor and the second batch file, and creates an hourly scheduled process masquerading as a OneDrive startup process.
This process reads an XOR-encrypted PowerShell script from disk and decrypts it for in-memory execution. Lastly, it deletes itself to wipe the indicators of an infection.
Supply: Examine Level
AI-generated backdoor
The PowerShell backdoor itself is closely obfuscated utilizing arithmetic-based string encoding, runtime string reconstruction, and execution of the ultimate logic through ‘Invoke-Expression.’
The researchers say that the PowerShell malware “strongly signifies AI-assisted growth slightly than conventional operator-authored malware.”
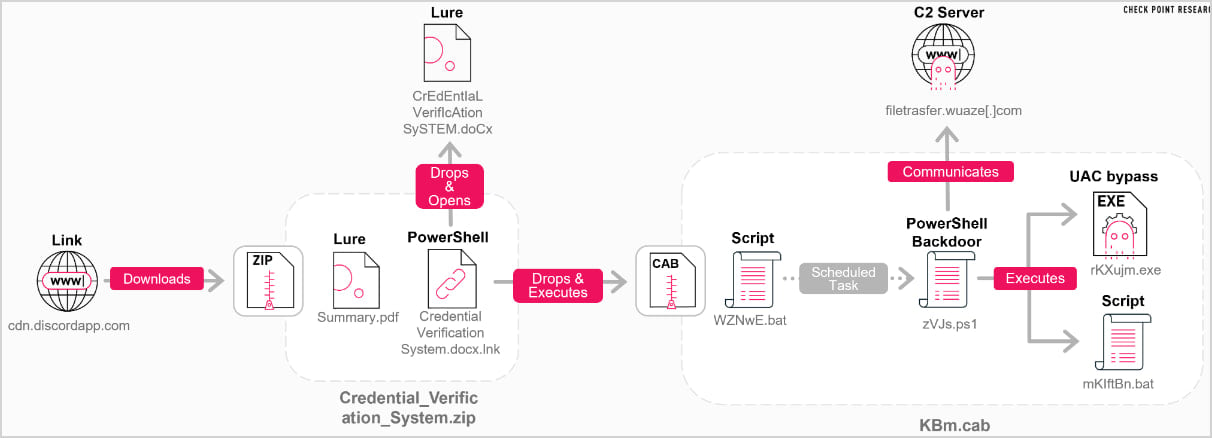
The proof resulting in this conclusion consists of the clear, structured documentation on the high of the script, which is uncommon for malware growth; its modular, clear structure; and the presence of a “# <– your everlasting mission UUID” remark.
Supply: Examine Level
“This phrasing is very attribute of LLM-generated code, the place the mannequin explicitly instructs a human person on tips on how to customise a placeholder worth,” explains Examine Level.
“Such feedback are generally noticed in AI-produced scripts and tutorials.”
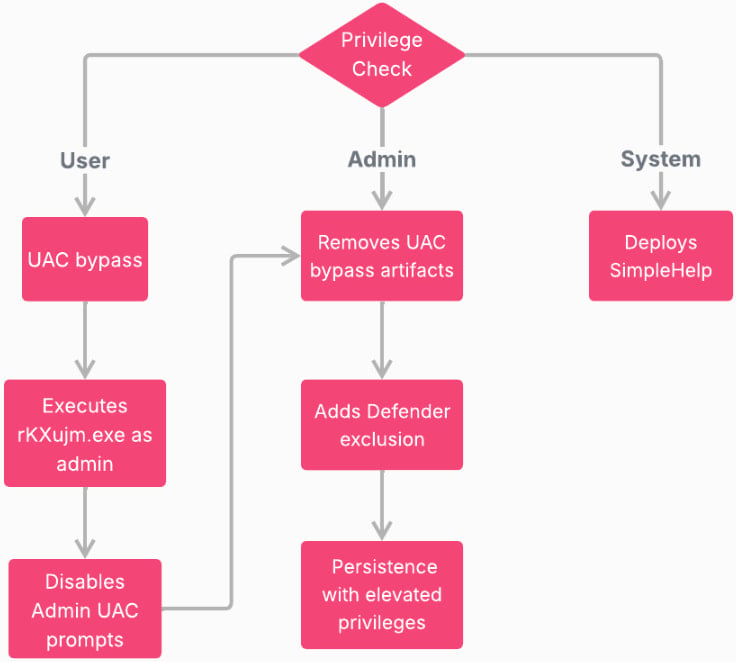
Earlier than execution, the malware performs {hardware}, software program, and person exercise checks to make sure it’s not operating in evaluation environments, after which generates a novel host ID.
Subsequent, relying on what execution privileges it has on the compromised host, it follows a separate path of motion as proven within the following diagram.
Supply: Examine Level
As soon as the backdoor is absolutely operating on the contaminated gadget, it periodically contacts the command-and-control (C2) server to ship fundamental host metadata and polls the server at randomized intervals.
If the C2 response comprises PowerShell code, it turns it right into a script block and executes it asynchronously through background jobs.
Examine Level attributes these assaults to the Konni menace actor primarily based on earlier launcher codecs, lure filename and script title overlaps, and commonalities within the execution chain construction with earlier assaults.
The researchers have revealed indicators of compromise (IoCs) related to this latest marketing campaign to assist defenders defend their belongings.




