
Fashionable infostealers have expanded credential theft far past usernames and passwords. Over the previous 12 months, campaigns have accelerated, concentrating on customers with little distinction between company staff and people on private units.
These infections routinely harvest credentials alongside broader session information and person exercise. The ensuing datasets are aggregated and offered by preliminary entry brokers, then reused throughout assaults concentrating on each private and enterprise environments.
To raised perceive the scope and implications of this exercise, Specops researchers analyzed greater than 90,000 leaked infostealer dumps, comprising over 800 million rows of information collected throughout energetic infections.
The datasets included credentials, browser cookies, looking historical past, and system-level recordsdata saved regionally on compromised machines.
What emerges is a transparent image of how infostealer dumps permit attackers to affiliate technical information with actual customers, organizations, and behavioral patterns, making a single an infection beneficial lengthy after the preliminary compromise.
When stolen credentials change into identification information
The largest threat is how simply infostealer information ties a number of accounts and behaviors again to at least one actual particular person. These dumps routinely expose reused account names throughout providers, Home windows usernames, recordsdata saved in person directories, energetic session information, and detailed information of exercise throughout environments.
Mixed, these indicators let attackers transfer from a single compromised credential to figuring out a person, their employer, and doubtlessly their position inside a corporation.
This convergence collapses the boundary between private {and professional} identification that many safety fashions nonetheless assume exists. What could begin as a compromise on a private system can shortly escalate into enterprise-level threat.
Specops Password Coverage helps organizations break this hyperlink by constantly scanning Energetic Listing towards a database of greater than 5.4 billion known-compromised credentials, moderately than solely checking passwords at creation or reset.
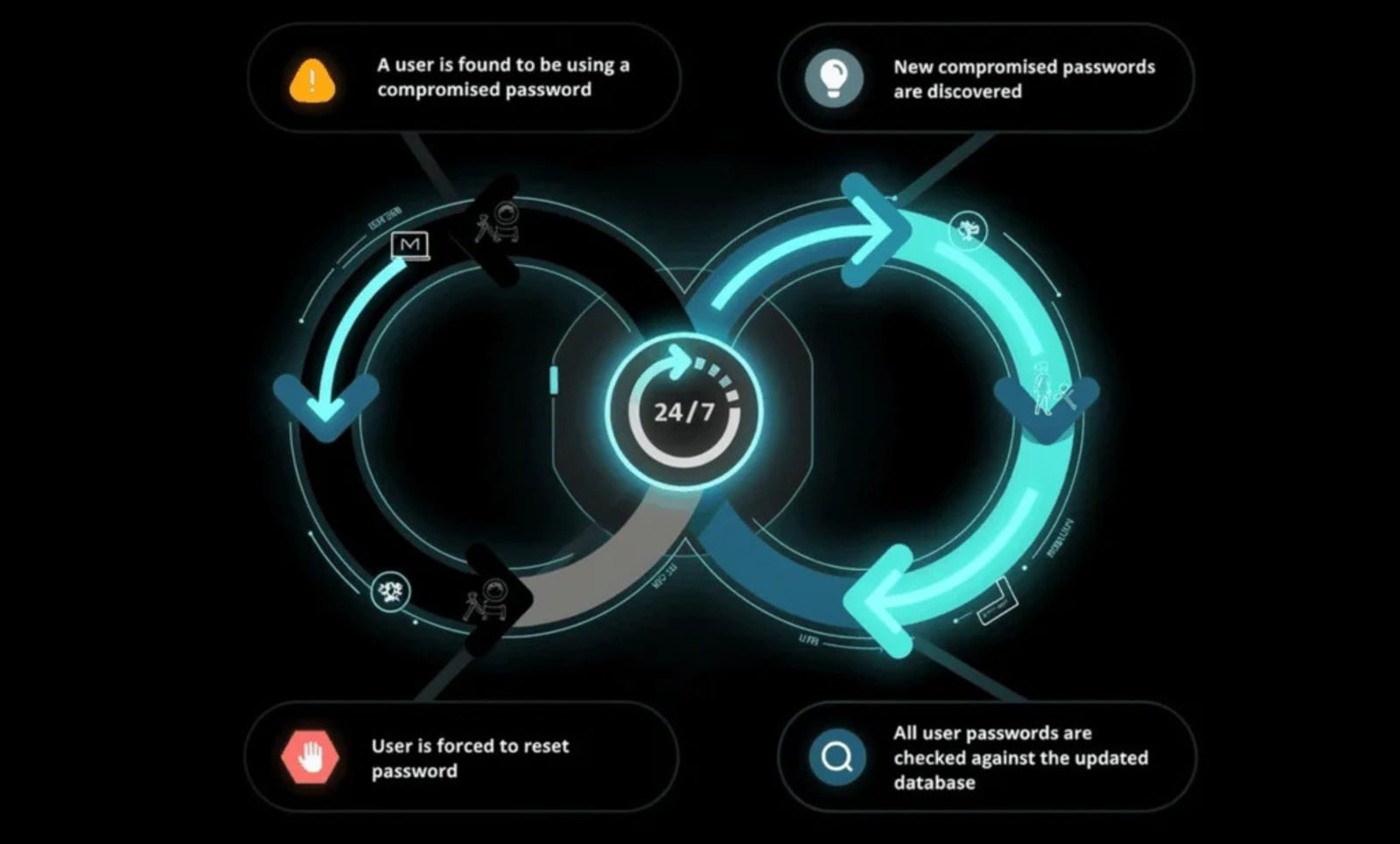
Credentials which have already been uncovered are blocked from being set or reused, even when they technically adjust to coverage, lowering the danger of compromised passwords being reused throughout private and company accounts.
Verizon’s Knowledge Breach Investigation Report discovered stolen credentials are concerned in 44.7% of breaches.
Effortlessly safe Energetic Listing with compliant password insurance policies, blocking 4+ billion compromised passwords, boosting safety, and slashing assist hassles!
The place infostealers get your information and the way they abuse it
The dataset contained credentials and session information related to a large vary of providers, illustrating how infostealer information exposes each identification and entry.
Skilled and enterprise-linked providers
LinkedIn, GitHub, Microsoft Groups, Outlook, and company domains appeared continuously within the dataset. LinkedIn alone accounted for practically 900,000 information, offering a direct path from stolen information to actual names, job titles, and organizational affiliations.
For menace actors, this data permits focused phishing, social engineering, and prioritization of entry that will lead deeper into enterprise environments, particularly the place password reuse exists.
Private identification and social platforms
YouTube, Fb, and related social media platforms additionally made high-volume appearances. These providers usually include actual names, photographs, and social connections, making it simpler to validate the identification of a compromised person and hyperlink them to different accounts.
This correlation makes focused exploitation far simpler.
Delicate and high-risk providers
The dataset additionally included credentials and cookies related to delicate providers, together with authorities and tax-related domains such because the IRS and the Canada Income Company, in addition to grownup content material platforms. Entry to those providers introduces dangers past conventional account takeover.
In earlier incidents, menace actors have used information from grownup platforms as leverage for extortion and blackmail. When that exercise could be linked again to a person’s actual identification and employer, the potential affect escalates shortly.
Safety-aware but nonetheless uncovered
Domains equivalent to Shodan and even mil.gov appeared throughout the dataset, reinforcing an uncomfortable actuality: technical consciousness doesn’t equal immunity.
Safe practices adopted in company environments don’t at all times lengthen to private methods, but publicity on these methods can nonetheless create enterprise threat.
Why infostealers stay so efficient
Infostealer publicity isn’t pushed by a single failure, however by a mix of frequent behaviors repeated at scale. Customers set up functions from illicit sources, reuse passwords throughout private and company accounts, and depend on browser-based credential storage for comfort.
Browser-stored credentials and fee information are particularly beneficial to attackers.
When an infostealer compromises a system, these shops present attackers with fast entry to high-value data, considerably rising the affect of a single an infection.
Lowering affect after credential theft
As soon as infostealer information has been collected and circulated, prevention is not the one problem. The actual query is how shortly defenders can neutralize it earlier than it’s reused for lateral motion, account takeover, or ransomware deployment.
As a result of infostealer dumps usually flow into for weeks or months earlier than detection, efficient mitigation should assume that some credentials are already uncovered.
Password reuse stays some of the dependable methods attackers operationalize infostealer information. Credentials harvested from private units are routinely examined towards company environments, cloud providers, and distant entry methods, usually with success even when these passwords meet commonplace complexity necessities.
Disrupting reuse instantly reduces the operational worth of infostealer datasets and shortens their window of exploitation.
Mixed with stronger password insurance policies that assist longer passphrases and steady enforcement, these controls shift password safety from a static configuration train to an energetic containment measure.
Id publicity more and more begins exterior the company perimeter, so lowering the reuse and downstream affect of stolen credentials stays some of the efficient methods to interrupt infostealer-driven assault chains.
To see how Specops Password Coverage helps block compromised passwords and scale back credential reuse in Energetic Listing, request a dwell demo from a Specops professional.
Sponsored and written by Specops Software program.


