
A menace actor focusing on uncovered Docker APIs has up to date its malicious tooling with extra harmful performance that would lay the inspiration for a posh botnet.
The exercise was first reported in June by cybersecurity firm Pattern Micro. whose researchers analyzed scripts and malicious code that dropped a cryptominer and relied on the Tor community to cover their id.
Akamai researchers found new tooling that doesn’t deploy a miner however a extra advanced payload that may block entry to compromised Docker APIs.
An infection chain
The attackers seek for uncovered Docker API (port 2375) on a weak host and ship a container creation request utilizing a modified Alpine Linux picture that features a base64-encoded shell command.
The container executes the decoded shell command, which installs curl and tor, launches a Tor daemon within the background, and waits for the affirmation of the connection by accessing Amazon’s checkip.amazonaws.com service over a SOCKS5 proxy.
As soon as Tor is energetic, the container downloads and executes a second-stage shell script (docker-init.sh) from a Tor hidden service utilizing curl.
The docker-init.sh script allows persistent SSH entry by appending an attacker-controlled public key to /root/.ssh/authorized_keys on the mounted host filesystem.
It writes a base64-encoded cron job on the host, which executes each minute and blocks exterior entry to port 2375 utilizing whichever firewall utility is obtainable (iptables, nftables, ufw, and so on.).
Moreover, it installs instruments like masscan, zstd, libpcap, and torsocks to assist scanning, propagation, and evasion.
Subsequent, the malware downloads a Zstandard-compressed Go binary (system-linux-ARCH.zst) over Tor, decompresses it to /tmp/system, grants execute permissions, and runs it.
The Go binary capabilities as a dropper, extracting and executing an embedded second-stage binary, and parses the host’s utmp file to establish logged-in customers.
Supply: Akamai
Botnet constructing conduct
The binary scans for different uncovered Docker APIs, makes an attempt to contaminate them by way of the identical container creation methodology, and removes competitor containers after gaining entry.
This self-replication mechanism is a core trait of botnet brokers that sometimes infect new nodes autonomously, with out requiring exterior course.
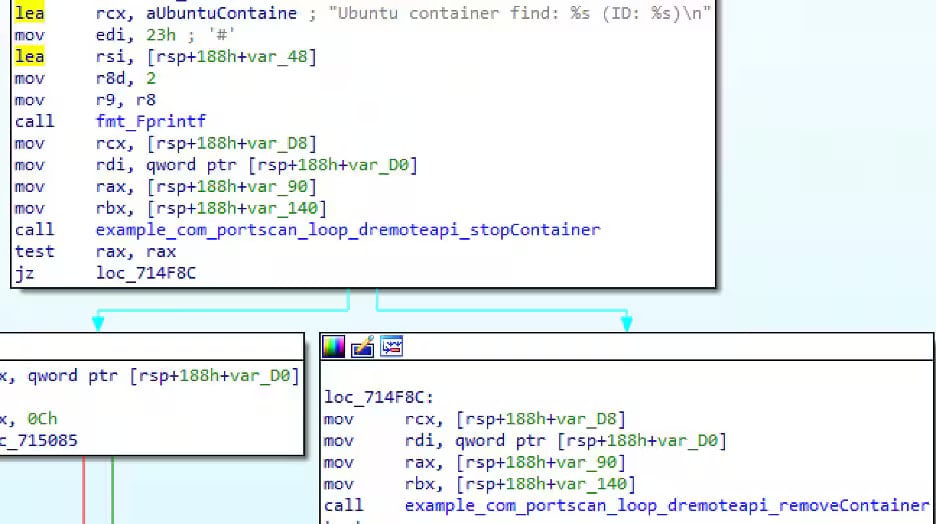
Supply: Akamai
Akamai highlights the presence of inactive logic for exploiting Telnet (port 23) utilizing default router credentials and for interacting with Chrome’s distant debugging interface (port 9222).
This means potential future growth alternatives for credential theft, browser session hijacking, distant file obtain, and distributed denial-of-service (DDoS) assaults.
“A few of the underlying mechanisms lead us to consider this variant is an preliminary model of a posh botnet,” Akamai’s researchers say, noting that they “haven’t discovered an entire model of it up to now.”
Akamai’s discovery exhibits evolution from opportunistic Docker exploitation right into a multi-vector menace with capabilities for lateral motion, persistence, and (dormant for now) choices for credential theft and browser hijacking.


