
The Gootloader malware, usually used for preliminary entry, is now utilizing a malformed ZIP archive designed to evade detection by concatenating as much as 1,000 archives.
In doing so, the malware, which is an archived JScript file, causes many instruments to crash when making an attempt to research it.
Based on researchers, the malicious file is efficiently unpacked utilizing the default utility in Home windows, however instruments counting on 7-Zip and WinRAR fail.
To realize this, the menace actor behind the malware concatenates between 500 and 1,000 ZIP archives, but in addition makes use of different methods to make parsing from evaluation instruments tougher.
The Gootloader malware loader has been lively since 2020 and is utilized by numerous cybercriminal operations, together with ransomware deployments.
After a seven-month break, the operation returned final November, as reported by safety researchers at Huntress Labs and the DFIR Report.
Whereas malformed ZIP archives had been current again then, they got here with minimal modifications, and there have been filename mismatches when making an attempt to extract the information.
To additional strengthen the anti-analysis of this stage, Gootloader operators have now applied much more in depth obfuscation mechanisms, based on Expel researchers analyzing more moderen samples.
Particularly, the next mechanisms at the moment are used to evade detection and evaluation:
- Concatenate as much as a thousand ZIP archives, exploiting the truth that parsers learn from the top of the file.
- Use a truncated Finish of Central Listing (EOCD) that misses two necessary bytes, breaking the parsing by most instruments.
- Randomize disk quantity fields, inflicting instruments to anticipate non-existent multi-disk archives.
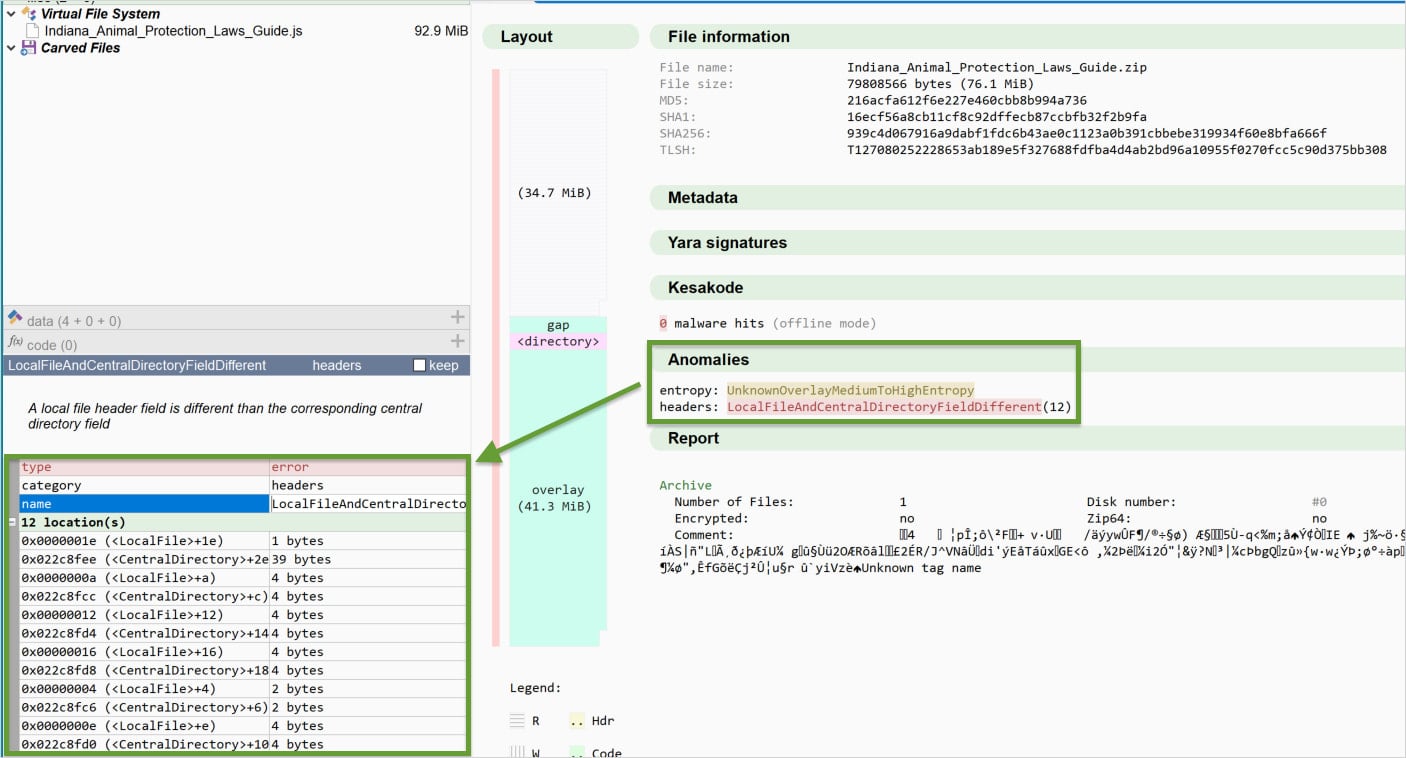
- Add metadata mismatches between the Native File Headers and Central Listing entries.
- Generate distinctive ZIP and JScript samples for every obtain to evade static detection.
- Ship the ZIP as an XOR-encoded blob, which is decoded and repeatedly appended client-side till it reaches the specified measurement, evading network-based detection.
Supply: Expel
As soon as executed on the host, the malware’s JScript prompts through Home windows Script Host (WScript) from a short lived listing and establishes persistence by including shortcut (.LNK) information to the Startup folder that time to a second JScript file.
This payload is executed upon first launch, and with each system boot, triggering CScript with NTFS shortnames, adopted by PowerShell spawning PowerShell.
Whereas Gootloader’s authors added a number of corruption methods to evade detection with out breaking performance, Expel researchers used the structural anomalies that enable defenders to identify the menace. The group additionally shared a YARA rule that “can constantly establish the present ZIP archives.”
The detection depends on recognizing a particular mixture of ZIP header options, a whole bunch of repeating Native File Headers, and EOCD data.
The researchers advocate that defenders change the default software for opening JScript information to Notepad as an alternative of Home windows Script Host, to forestall their execution.
To cut back the assault floor, Expel advises blocking wscript.exe and cscript.exe from executing downloaded content material if JScript information should not wanted.




