
The Russian APT28 hacking group (aka ‘Strontium’ or ‘Fancy Bear’) has been focusing on authorities entities, companies, universities, analysis institutes, and assume tanks in France because the second half of 2021.
The risk group, which is taken into account a part of Russia’s navy intelligence service GRU, was lately linked to the exploitation of CVE-2023-38831, a distant code execution vulnerability in WinRAR, and CVE-2023-23397, a zero-day privilege elevation flaw in Microsoft Outlook.
The Russian hackers have been compromising peripheral units on crucial networks of French organizations and transferring away from using backdoors to evade detection.
That is in keeping with a newly printed report from ANSSI (Agence Nationale de la sécurité des systèmes d’data), the French Nationwide Company for the Safety of Data Techniques, that carried out investigations on the actions of the cyber-espionage group.
Community reconnaissance and preliminary entry
ANSSI has mapped the TTPs (strategies, techniques, and procedures) of APT28, reporting that the risk group makes use of brute-forcing and leaked databases containing credentials to breach accounts and Ubiquiti routers on focused networks.
In a single case from April 2023, the attackers ran a phishing marketing campaign that tricked the recipients into operating PowerShell that uncovered their system configuration, operating processes, and different OS particulars.
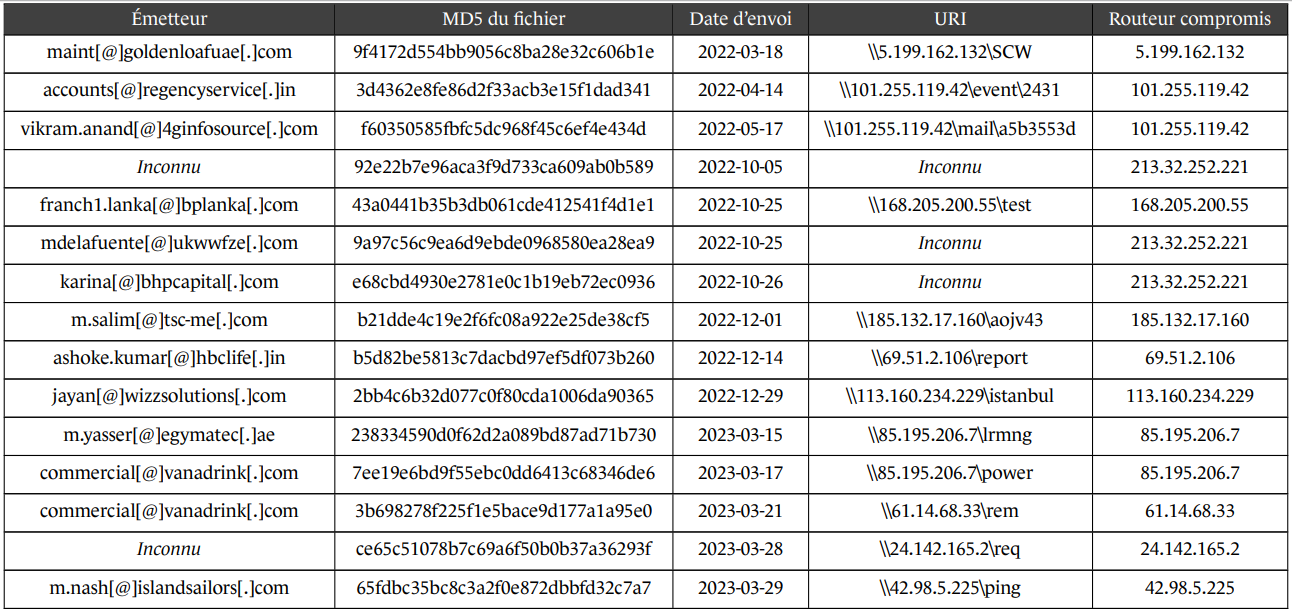
Between March 2022 and June 2023, APT28 despatched emails to Outlook customers that exploited the then zero-day vulnerability now tracked as CVE-2023-23397, inserting the preliminary exploitation a month sooner than what was lately reported.
Throughout this era, the attackers additionally exploited CVE-2022-30190 (aka “Follina”) within the Microsoft Home windows Help Diagnostic Device and CVE-2020-12641, CVE-2020-35730, CVE-2021-44026 within the Roundcube utility.
The instruments used within the first phases of the assaults embody the Mimikatz password extractor and the reGeorg visitors relaying device, in addition to the Mockbin and Mocky open-source companies.
ANSSI additionally reviews that APT28 makes use of a spread of VPN purchasers, together with SurfShark, ExpressVPN, ProtonVPN, PureVPN, NordVPN, CactusVPN, WorldVPN, and VPNSecure.
Knowledge entry and exfiltration
As a cyber-espionage group, knowledge entry and exfiltration are on the core of Strontium’s operational objectives.
ANSSI has noticed the risk actors retrieving authentication data utilizing native utilities and stealing emails containing delicate data and correspondence.
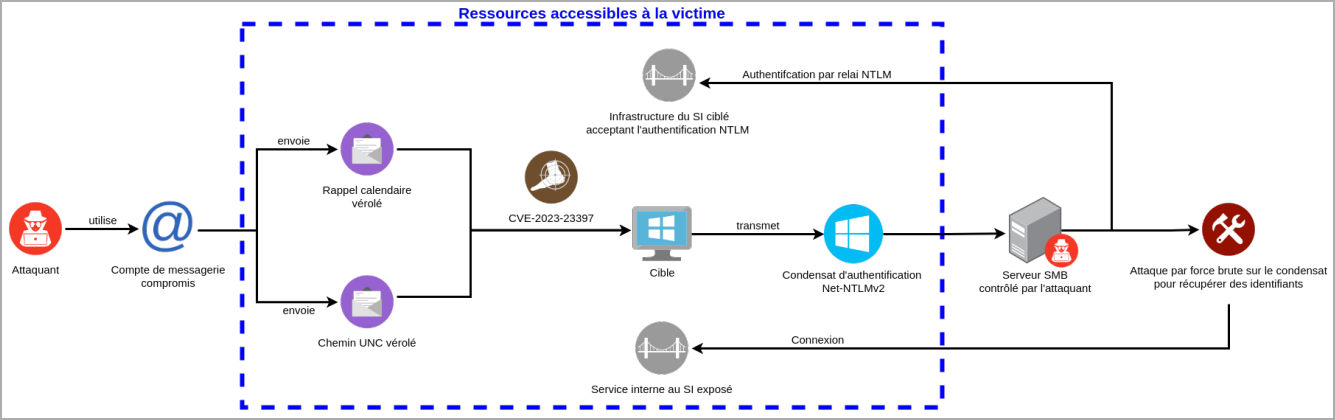
Particularly, the attackers exploit CVE-2023-23397 to set off an SMB connection from the focused accounts to a service beneath their management, permitting the retrieval of the NetNTLMv2 authentication hash, which can be utilized on different companies, too.
APT28’s command and management server (C2) infrastructure depends on professional cloud companies, comparable to Microsoft OneDrive and Google Drive, to make the alternate much less more likely to increase any alarms by visitors monitoring instruments.
Lastly, ANSSI has seen proof that the attackers accumulate knowledge utilizing the CredoMap implant, which targets data saved within the sufferer’s internet browser, comparable to authentication cookies.
Mockbin and the Pipedream service are additionally concerned within the knowledge exfiltration course of.
Protection suggestions
ANSSI emphasizes a complete strategy to safety, which entails assessing dangers. Within the case of the APT28 risk, specializing in e-mail safety is essential.
The company’s key suggestions round e-mail safety embody:
- Make sure the safety and confidentiality of e-mail exchanges.
- Use safe alternate platforms to stop e-mail diversions or hijacks.
- Reduce the assault floor of webmail interfaces and cut back dangers from servers like Microsoft Change.
- Implement capabilities to detect malicious emails.
For extra particulars on ANSSI’s findings and protection ideas, try the full report right here.


