
Faux Bitwarden websites are pushing installers purportedly for the open-source password supervisor that carry a brand new password-stealing malware that safety researchers name ZenRAT.
The malware is distributed to Home windows customers by way of web sites that imitate the reputable Bitwarden website and depend on typosquatting to idiot potential victims.
Centered on Home windows customers
The aim of ZenRAT is to gather browser knowledge and credentials together with particulars concerning the contaminated host, a conduct in keeping with an data stealer.
Cybercriminals can use the main points to create a fingerprint of the compromised system that can be utilized to entry an account as if the reputable consumer logged in.
Safety researchers at cybersecurity firm Proofpoint found ZenRAT after receiving in August a pattern of the malware from Jérôme Segura, Senior Director of Risk Intelligence at Malwarebytes.
The distribution level was “a really convincing lookalike to the true bitwarden.com” with a website identify particularly chosen to trick guests into believing they have been accessing the official useful resource – bitwariden[.]com.
supply: Proofpoint
Contained in the faux Bitwarden set up bundle, Proofpoint researchers discovered a malicious .NET executable that could be a distant entry trojan (RAT) with info-stealing options they’re now monitoring as ZenRAT.
The malicious web site offers the faux Bitwarden bundle solely to Home windows customers, in any other case, it redirects to a cloned web page of an opensource.com article concerning the password supervisor.
When making an attempt to obtain the Bitwarden model for Linux or Mac, the consumer is redirected to the official obtain web page of the software program, Proofpoint notes.
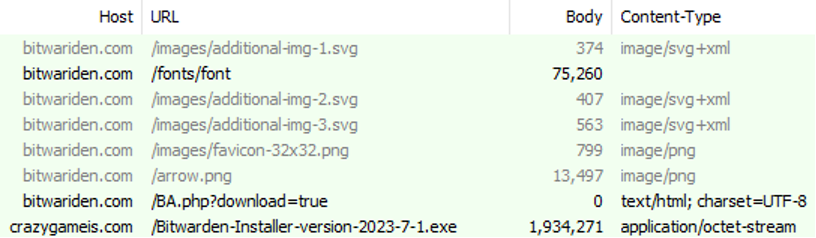
The malicious Bitwarden installer for Home windows is delivered from crazygameis[.]com, one other faux URL for the reputable browser-based gaming platform CrazyGames.
supply: Proofpoint
The researchers do not know the way potential victims land on the faux Bitwarden website however phishing campaigns by way of Google adverts have been used previously to focus on Bitwarden customers particularly.
Stealing knowledge, evading evaluation
As soon as working, ZenRAT makes use of WMI queries and different system instruments to gather knowledge concerning the host, which incorporates:
- CPU Title
- GPU Title
- OS Model
- Put in RAM
- IP tackle and Gateway
- Put in Antivirus
- Put in Functions
The main points above are delivered to the command and management (C2) server in a ZIP archive that additionally consists of knowledge and credentials collected from the net browser.
Earlier than speaking with the C2, although, ZenRAT makes certain that the host isn’t in a restricted area (Belarus, Kyrgyzstan, Kazakhstan, Moldova, Russia, and Ukraine).
The malware additionally checks whether it is working in a digital machine or a sandbox, an indication that researchers are analyzing it.
Nonetheless, the researchers additionally found some unusual data within the installer’s metadata, similar to claiming to be the {hardware} data app Speccy, from Piriform.
One other peculiarity is knowledge concerning the signer of the installer. Though the digital certificates isn’t legitimate, ZenRAT’s installer lists Tim Kosse, the developer of the open-source FileZilla FTP software program, because the signer.
Regardless of having capabilities particular to an data stealer, Proofpoint has discovered proof suggesting that the malware is designed to be modular and its capabilities might be expanded; nonetheless, no different modules have been noticed within the wild.
The Bitwarden password supervisor has elevated in recognition currently as it’s thought to be a greater different to different merchandise available on the market. With a rising consumer base, the software program and its customers develop into a goal as cybercriminals take benefit


