
Traditionally, cybersecurity fashions have been largely reactive. Organizations would assess vulnerabilities at specified intervals, usually following a safety incident or a scheduled audit. Whereas this technique does have its deserves, the dynamic nature of in the present day’s cyber threats calls for a extra proactive method to cybersecurity.
The usual safety mannequin of point-in-time assessments has labored effectively previously and has their place for distinct use circumstances. However with the rise in zero-day vulnerabilities, polymorphic malware, and Superior Persistent Threats (APTs), there’s an argument for extra frequent, even steady, cybersecurity evaluations.
Let’s discover the variations between these two approaches and the way they might help organizations improve their software safety program, and past.
Conventional internet software pen testing vs. pen testing as a service
Level-in-time assessments are like snap-shots taken at a selected occasion of time. This method is efficient in detecting vulnerabilities that exist solely at that particular second.
Conventional pen testing is one instance of how these assessments are carried out. A staff of moral hackers can be employed to yearly assess and establish vulnerabilities in a corporation’s community, techniques, and apps.
In distinction, pen testing as a service (PTaaS) takes a steady monitoring method. PTaaS is an ongoing course of that mixes guide testing with automated instruments to constantly scan for vulnerabilities and threats.
This method presents a extra proactive type of safety that permits organizations to detect potential weaknesses earlier than they grow to be exploitable.
Whereas point-in-time pen testing assessments present a quick overview of a corporation’s safety posture; PTaaS offers organizations the chance to establish vulnerabilities earlier and take corrective motion earlier than threats grow to be exploitable.
Finest pen testing method for securing internet apps
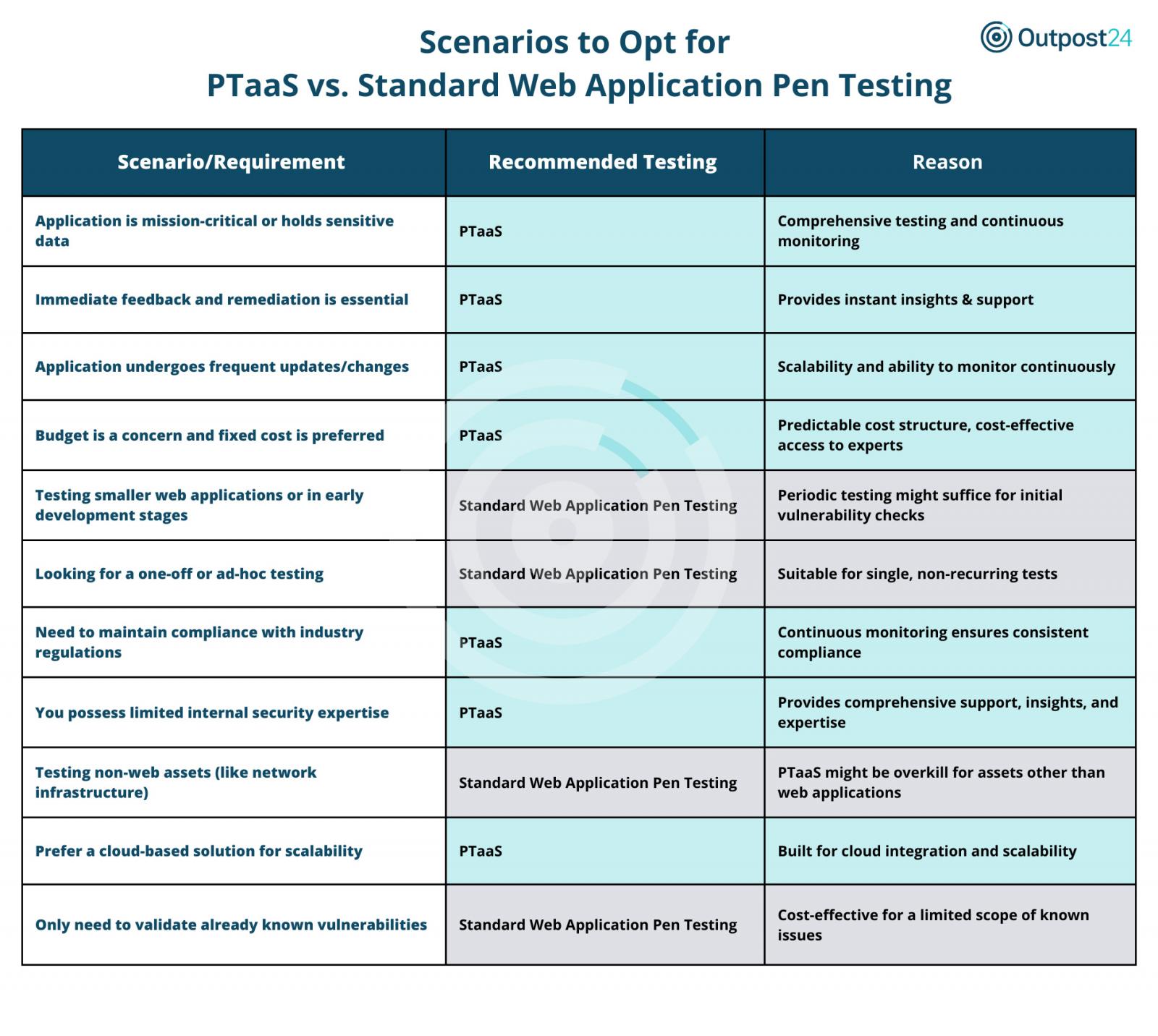
To safe internet purposes, organizations can now select between conventional internet software penetration testing and PTaaS. The choice typically hinges on a corporation’s particular wants and challenges.
PTaaS shines in conditions the place:
- Mission-critical purposes are concerned, demanding complete and steady monitoring.
- Quick suggestions is paramount. PTaaS presents fast detection and remediation help.
- The applying incessantly updates or modifications, requiring scalable, steady vigilance.
- Organizations search a predictable price construction and professional insights with out straining the price range.
- Constant compliance with trade rules is a precedence, and steady monitoring turns into a necessity.
- There’s restricted inner safety experience, making exterior complete help very important.
- A cloud-based resolution is most well-liked for its scalability and integration capabilities.
- Seamless integration with CI/CD pipelines is required, particularly in agile growth environments.
Customary internet software pen testing is right when:
- The main focus is on smaller internet purposes or these within the early phases, the place periodic checks can suffice.
- The necessity is for one-off or ad-hoc checks with out the requirement of ongoing monitoring.
- The intention is to check non-application property like community infrastructure, the place a specialised method is more cost effective.
- The first objective is to validate identified vulnerabilities, providing a focused and cost-effective resolution.
- Detailed evaluation of particular vulnerabilities, akin to Cross-Web site Scripting (XSS) or SQL Injection, is required.
In essence, each testing strategies provide precious insights, however the context determines one of the best match. Organizations ought to align their selection with their distinctive challenges to make sure optimum cybersecurity outcomes.
Embracing the continual monitoring method throughout the board
Past securing internet purposes, improvements like Endpoint Assault Floor Administration (EASM) and Threat-Primarily based Vulnerability Administration (RBVM) have emerged as sport changers for elevating a corporation’s cybersecurity posture.
EASM allows organizations to realize a holistic view into their exterior assault floor. Its automated method allows group to cut back the chance of a cyberattack by figuring out and analyzing susceptible property in actual time, even these they don’t learn about.
Traditionally, vulnerability administration was a reactive sport, typically plagued with the problem of ‘alert fatigue’. However Threat-Primarily based Vulnerability Administration (RBVM) modified that narrative. Reasonably than flagging each vulnerability as seen in conventional vulnerability scanning, RBVM instruments prioritize them based mostly on contextual danger. This helps organizations make higher selections about which vulnerabilities to handle first.
Because the contours of cyber threats evolve, so should our defence mechanisms. Embracing steady monitoring in PTaaS, EASM, and RBVM, isn’t just a technique – it is crucial for companies in in the present day’s digital panorama.
Recognizing this shift, Outpost24 presents cybersecurity options that present a unified, steady, and proactive method to enhance cyber resilience.
From internet software testing at scale, to assault floor evaluation and vulnerability administration, we assist group tackle potential points earlier than they escalate.

