
UK-based telecommunications firm Colt Expertise Companies confirms that buyer documentation was stolen as Warlock ransomware gang auctions recordsdata.
The British telecommunications and community providers supplier beforehand disclosed it suffered an assault on August 12, however that is the primary time they confirmed knowledge had been stolen.
“A felony group has accessed sure recordsdata from our methods that will comprise info associated to our prospects and posted the doc titles on the darkish net,” reads an up to date safety incident advisory on Colt’s web site.
“We perceive that that is regarding for you.”
“Clients are capable of request a listing of filenames posted on the darkish net from the devoted name centre.”
This assertion comes after the Warlock Group started promoting on the Ramp cybercrime discussion board what they declare is 1 million paperwork stolen from Colt. The paperwork are being offered for $200,000 and allegedly comprise monetary info, community structure knowledge, and buyer info.
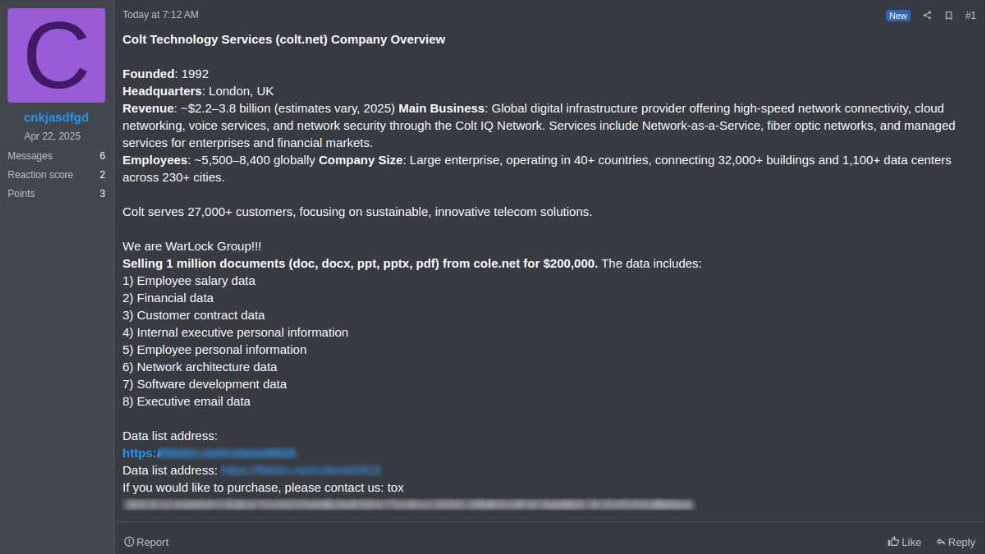
Supply: KELA
BleepingComputer can verify that the Tox ID listed within the discussion board publish matches an ID utilized in earlier variations of the ransomware gang’s ransom notes.
The Warlock Group (aka Storm-2603) is a ransomware gang attributed to Chinese language risk actors who make the most of the leaked LockBit Home windows and Babuk VMware ESXi encryptors in assaults.
When the ransomware gang launched in March 2025, they used LockBit ransomware notes of their assaults, personalized to incorporate a Tox ID for ransom negotiations.
In June, the ransomware gang branded itself because the “Warlock Group,” with personalized ransom notes and darkish net negotiation and knowledge leak websites.
Final month, Microsoft reported that the risk actors had been exploiting a SharePoint vulnerability to breach company networks and deploy ransomware.
In negotiations seen by BleepingComputer, the ransomware gang calls for ransom ranging between $450,000 and hundreds of thousands of {dollars}.



