
The U.S. Cybersecurity and Infrastructure Safety Company (CISA) has ordered authorities businesses to safe their techniques in opposition to a high-severity Gogs vulnerability that was exploited in zero-day assaults.
Designed as an alternative choice to GitLab or GitHub Enterprise and written in Go, Gogs is commonly uncovered on-line for distant collaboration.
Tracked as CVE-2025-8110, this distant code execution (RCE) safety flaw stems from a path traversal weak spot within the PutContents API and permits authenticated attackers to bypass protections applied for a beforehand patched RCE bug (CVE-2024-55947) by overwriting recordsdata outdoors the repository by way of symbolic hyperlinks.
Attackers can abuse this flaw by creating repos containing symbolic hyperlinks pointing to delicate system recordsdata, after which writing information by the symlink utilizing the PutContents API, overwriting targets outdoors the repository. By overwriting Git configuration recordsdata, particularly the sshCommand setting, risk actors can pressure goal techniques to execute arbitrary instructions.
Wiz Analysis found the vulnerability whereas investigating a malware an infection affecting a buyer’s Web-facing Gogs server in July and reported the flaw to Gogs maintainers on July 17. They acknowledged Wiz’s report three months later, on October 30, and launched patches for CVE-2025-8110 final week that add symlink-aware path validation in any respect file-write entry factors.
In keeping with a disclosure timeline shared by Wiz Analysis, a second wave of assaults focusing on this vulnerability as a zero-day was noticed on November 1.
Whereas investigating these campaigns, Wiz researchers discovered over 1,400 Gogs servers uncovered on-line (1,250 of which stay uncovered) and greater than 700 situations displaying indicators of compromise.
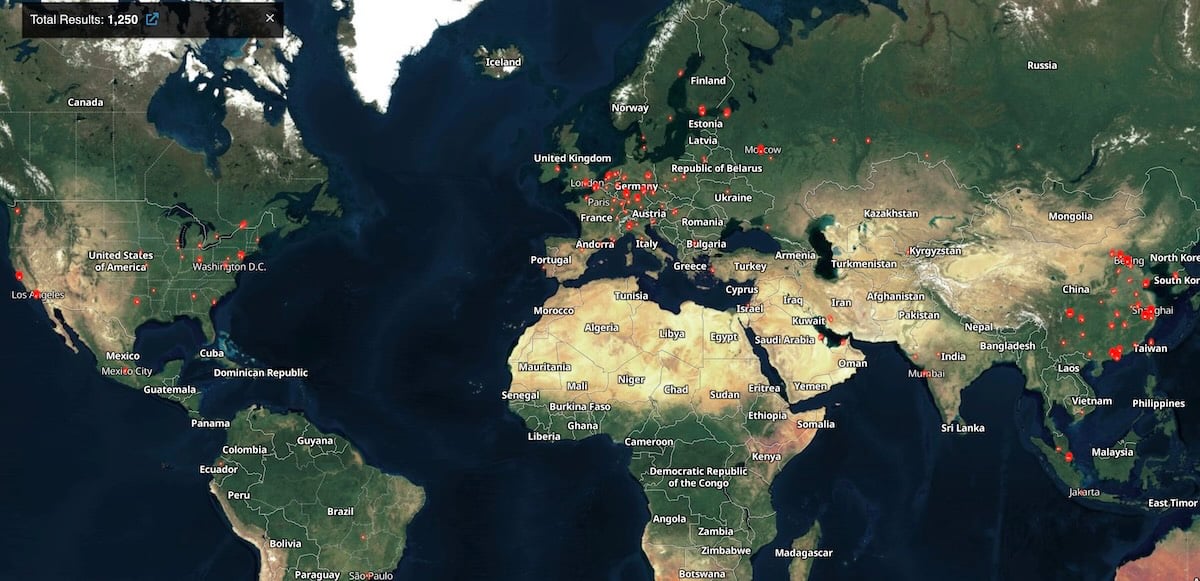
CISA has now confirmed Wiz’s report and added the safety flaw to its record of vulnerabilities exploited within the wild, ordering Federal Civilian Govt Department (FCEB) businesses to patch inside three weeks, by February 2, 2026.
FCEB businesses are non-military U.S. govt department businesses, such because the Division of Power, the Division of Justice, the Division of Homeland Safety, and the Division of State.
“This kind of vulnerability is a frequent assault vector for malicious cyber actors and poses important dangers to the federal enterprise,” CISA warned. “Apply mitigations per vendor directions, comply with relevant BOD 22-01 steerage for cloud companies, or discontinue use of the product if mitigations are unavailable.”
To additional scale back the assault floor, Gogs customers are suggested to disable the default open-registration setting instantly and restrict server entry utilizing a VPN or an permit record.
Moreover, admins who need to test for indicators of compromise on their Gogs occasion ought to search for suspicious use of the PutContents API and for repositories with random eight-character names created in the course of the two assault waves.




