
A brand new pattern of the ToneShell backdoor, usually seen in Chinese language cyberespionage campaigns, has been delivered via a kernel-mode loader in assaults towards authorities organizations.
The backdoor has been attributed to the Mustang Panda group, also referred to as HoneyMyte or Bronze President, that often targets authorities businesses, NGOs, suppose tanks, and different high-profile organizations worldwide.
Safety researchers at Kaspersky analyzed a malicious file driver discovered on pc techniques in Asia and found that it has been utilized in campaigns since a minimum of February 2025 towards authorities organizations in Myanmar, Thailand, and different Asian international locations.
Proof confirmed that the compromised entities had prior infections with older ToneShell variants, PlugX malware, or the ToneDisk USB worm, additionally attributed to state-sponsored Chinese language hackers.
New kernel-mode rootkit
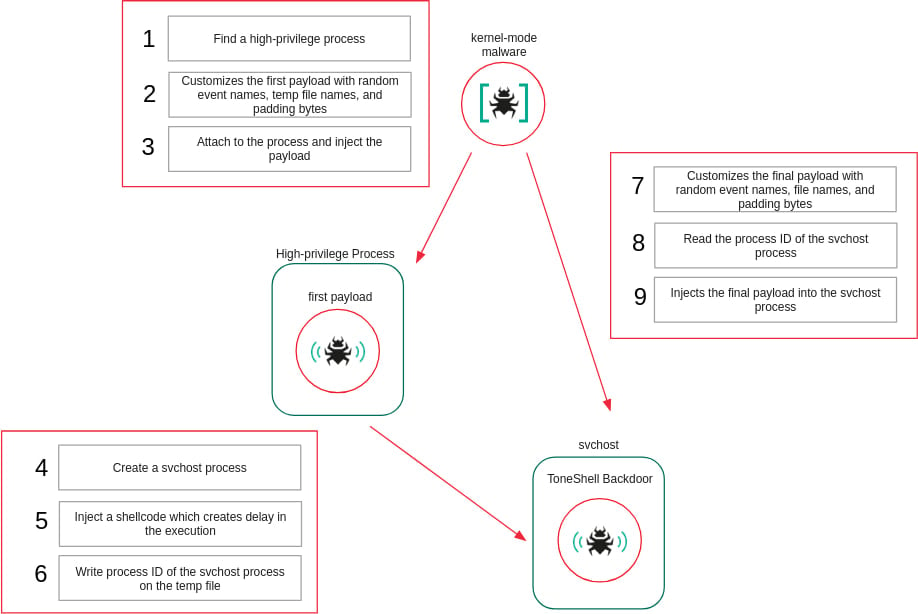
In response to Kaspersky, the brand new ToneShell backdoor was deployed by a mini-filter driver named ProjectConfiguration.sys and signed with a stolen or leaked certificates legitimate between 2012 and 2015 and issued to Guangzhou Kingteller Expertise Co., Ltd.
Mini-filters are kernel-mode drivers that plug into the Home windows file-system I/O stack and might examine, modify, or block file operations. Safety software program, encryption instruments, and backup utilities usually use them.
ProjectConfiguration.sys embeds two user-mode shellcodes in its .knowledge part, every executed as a separate user-mode thread to be injected into user-mode processes.
To evade static evaluation, the driving force resolves required kernel APIs at runtime by enumerating loaded kernel modules and matching perform hashes, moderately than importing features instantly.
It registers as a mini-filter driver and intercepts file-system operations associated to deletion and renaming. When such operations goal the driving force itself, they’re blocked by forcing the request to fail.
The driving force additionally protects its service-related registry keys by registering a registry callback and denying makes an attempt to create or open them. To make sure precedence over safety merchandise, it selects a mini-filter altitude above the antivirus-reserved vary.
Moreover, the rootkit interferes with Microsoft Defender by modifying the configuration of the WdFilter driver so it isn’t loaded into the I/O stack.
To protect injected user-mode payloads, the driving force maintains a listing of protected course of IDs, denies deal with entry to these processes whereas the payloads are executing, and removes safety as soon as execution completes.
“That is the primary time we’ve seen ToneShell delivered via a kernel-mode loader, giving it safety from user-mode monitoring and benefiting from the rootkit capabilities of the driving force that hides its exercise from safety instruments,” says Kaspersky.
Supply: Kaspersky
New ToneShell variant
The brand new variant of the ToneShell backdoor that Kaspersky analyzed options modifications and stealth enhancements. The malware now makes use of a brand new host identification scheme based mostly on a 4-byte host ID market as an alternative of the 16-byte GUID used beforehand, and likewise applies community site visitors obfuscation with pretend TLS headers.
When it comes to the supported distant operations, the backdoor now helps the next instructions:
- 0x1 — Create a short lived file for incoming knowledge
- 0x2 / 0x3 — Obtain file
- 0x4 — Cancel obtain
- 0x7 — Set up a distant shell by way of a pipe
- 0x8 — Obtain operator command
- 0x9 — Terminate shell
- 0xA / 0xB — Add file
- 0xC — Cancel add
- 0xD — Shut connection
Kaspersky advises that reminiscence forensics is essential in uncovering ToneShell infections backed by the brand new kernel-mode injector.
The researchers have excessive confidence in attributing the brand new ToneShell backdoor pattern to the Mustang Panda cyberespionage group. They assess that the risk actor has advanced its techniques, methods, and procedures to realize operational stealth and resilience.
The cybersecurity firm offers in its report a brief record of indicators of compromise (IoCs) to assist organizations detect Mustang Panda intrusions and defend towards them.
Damaged IAM is not simply an IT downside – the influence ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with trendy calls for, examples of what “good” IAM seems to be like, and a easy guidelines for constructing a scalable technique.




