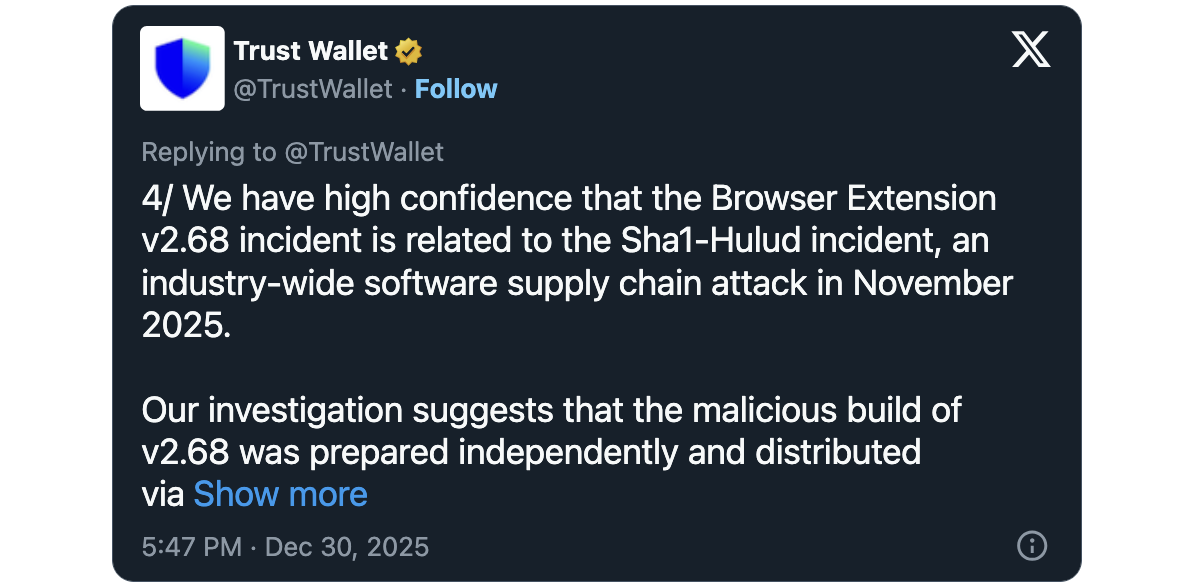
Belief Pockets believes the compromise of its net browser to steal roughly $8.5 million from over 2,500 crypto wallets is probably going associated to an “industry-wide” Sha1-Hulud assault in November.
Belief Pockets, a crypto pockets utilized by over 200 million individuals, permits customers to retailer, ship, and obtain Bitcoin, Ethereum, Solana, and 1000’s of different cryptocurrencies and digital tokens by way of an online browser extension and free cell apps.
As BleepingComputer beforehand reported, this December twenty fourth incident resulted within the theft of thousands and thousands of {dollars} in cryptocurrency from the compromised wallets of Belief Pockets customers.
This occurred after attackers added a malicious JavaScript file to model 2.68.0 of Belief Pockets’s Chrome extension, which stole delicate pockets information and enabled menace actors to execute unauthorized transactions.
“Our Developer GitHub secrets and techniques have been uncovered within the assault, which gave the attacker entry to our browser extension supply code and the Chrome Net Retailer (CWS) API key,” the corporate stated in a Tuesday replace.
“The attacker obtained full CWS API entry by way of the leaked key, permitting builds to be uploaded straight with out Belief Pockets’s customary launch course of, which requires inside approval/handbook overview.”
As Belief Pockets defined, within the subsequent stage of the assault, the menace actor registered the area metrics-trustwallet.com and the subdomain api.metrics-trustwallet.com to host malicious code, which was later referenced in a trojanized model of the Belief Pockets extension.
The modified model of the official extension was constructed utilizing supply code obtained by way of uncovered GitHub developer secrets and techniques, permitting the attacker to embed malicious code that collected delicate pockets information with out conventional code injection.
Utilizing a leaked CWS key, the attacker printed model 2.68 to the Chrome Net Retailer, which was robotically launched after passing overview, bypassing Belief Pockets’s inside approval processes.
In response to the incident, Belief Pockets revoked all launch APIs to dam makes an attempt to launch new variations and ensured that the hackers could not steal further pockets information by reporting the malicious domains to the NiceNIC registrar, which promptly suspended them.
Belief Pockets has additionally began reimbursing affected customers and warned them that menace actors are at present impersonating Belief Pockets assist accounts, pushing faux compensation types, and working scams by way of Telegram advertisements.
The Shai-Hulud malware marketing campaign
Sha1-Hulud (also called Shai-Hulud 2.0) was a provide chain assault concentrating on the npm software program registry, which lists over 2 million packages.
In the course of the preliminary Shai-Hulud outbreak in early September, menace actors compromised over 180 npm packages utilizing a self-propagating payload and used it to steal developer secrets and techniques and API keys with the TruffleHog instrument.
Shai-Hulud 2.0 grew exponentially and impacted over 800 packages after including over 27,000 malicious packages to the npm repository that used malicious code to gather developer and CI/CD secrets and techniques and publish them on GitHub.
In complete, Sha1-Hulud uncovered round 400,000 uncooked secrets and techniques and printed stolen information throughout over 30,000 GitHub repositories, with over 60% of the leaked NPM tokens nonetheless legitimate as of December 1st.
“Attackers are perfecting credential harvesting operations utilizing the npm ecosystem and GitHub,” Wiz safety researchers warned final month.
“Given the attackers’ growing sophistication and success up to now, we predict continued assaults, each utilizing comparable TTPs and leveraging the credential trove harvested thus far.”