
The FBI is warning that the BADBOX 2.0 malware marketing campaign has contaminated over 1 million house Web-connected units, changing client electronics into residential proxies which can be used for malicious exercise.
The BADBOX botnet is usually discovered on Chinese language Android-based good TVs, streaming packing containers, projectors, tablets, and different Web of Issues (IoT) units.
“The BADBOX 2.0 botnet consists of hundreds of thousands of contaminated units and maintains quite a few backdoors to proxy companies that cyber felony actors exploit by both promoting or offering free entry to compromised house networks for use for varied felony exercise,” warns the FBI.
These units come preloaded with the BADBOX 2.0 malware botnet or grow to be contaminated after putting in firmware updates and thru malicious Android functions that sneak onto Google Play and third-party app shops.
“Cyber criminals achieve unauthorized entry to house networks by both configuring the product with malicious software program previous to the customers buy or infecting the system because it downloads required functions that comprise backdoors, often through the set-up course of,” explains the FBI.
“As soon as these compromised IoT units are linked to house networks, the contaminated units are inclined to turning into a part of the BADBOX 2.0 botnet and residential proxy services4 identified for use for malicious exercise.”
As soon as contaminated, the units hook up with the attacker’s command and management (C2) servers, the place they obtain instructions to execute on the compromised units, similar to:
- Residential Proxy Networks: The malware routes visitors from different cybercriminals by means of victims’ house IP addresses, masking malicious exercise.
- Advert Fraud: BADBOX can load and click on advertisements within the background, producing advert income for the risk actors.
- Credential Stuffing: By leveraging sufferer IPs, attackers try to entry different folks’s accounts utilizing stolen credentials.
BADBOX 2.0 advanced from the unique BADBOX malware, which was first recognized in 2023 after it was discovered pre-installed in low-cost, no-name Android TV packing containers just like the T95.
Over time, the malware botnet continued increasing till 2024, when Germany’s cybersecurity company disrupted the botnet within the nation by sinkholing the communication between contaminated units and the attacker’s infrastructure, successfully rendering the malware ineffective.
Nevertheless, that didn’t cease the risk actors, with researchers saying they discovered the malware put in on 192,000 units every week later. Much more regarding, the malware was discovered on extra mainstream manufacturers, like Yandex TVs and Hisense smartphones.
Sadly, regardless of the earlier disruption, the botnet continued to develop, with HUMAN’s Satori Risk Intelligence stating that over 1 million client units had grow to be contaminated by March 2025.
This new bigger botnet is now being known as BADBOX 2.0 to point a brand new monitoring of the malware marketing campaign.
“This scheme impacted greater than 1 million client units. Gadgets linked to the BADBOX 2.0 operation included lower-price-point, “off model”, uncertified tablets, linked TV (CTV) packing containers, digital projectors, and extra,” explains HUMAN.
“The contaminated units are Android Open Supply Venture units, not Android TV OS units or Play Defend licensed Android units. All of those units are manufactured in mainland China and shipped globally; certainly, HUMAN noticed BADBOX 2.0-associated visitors from 222 nations and territories worldwide.”
Researchers at HUMAN estimate that the BADBOX 2.0 botnet spans 222 nations, with the best variety of compromised units in Brazil (37.6%), the USA (18.2%), Mexico (6.3%), and Argentina (5.3%).
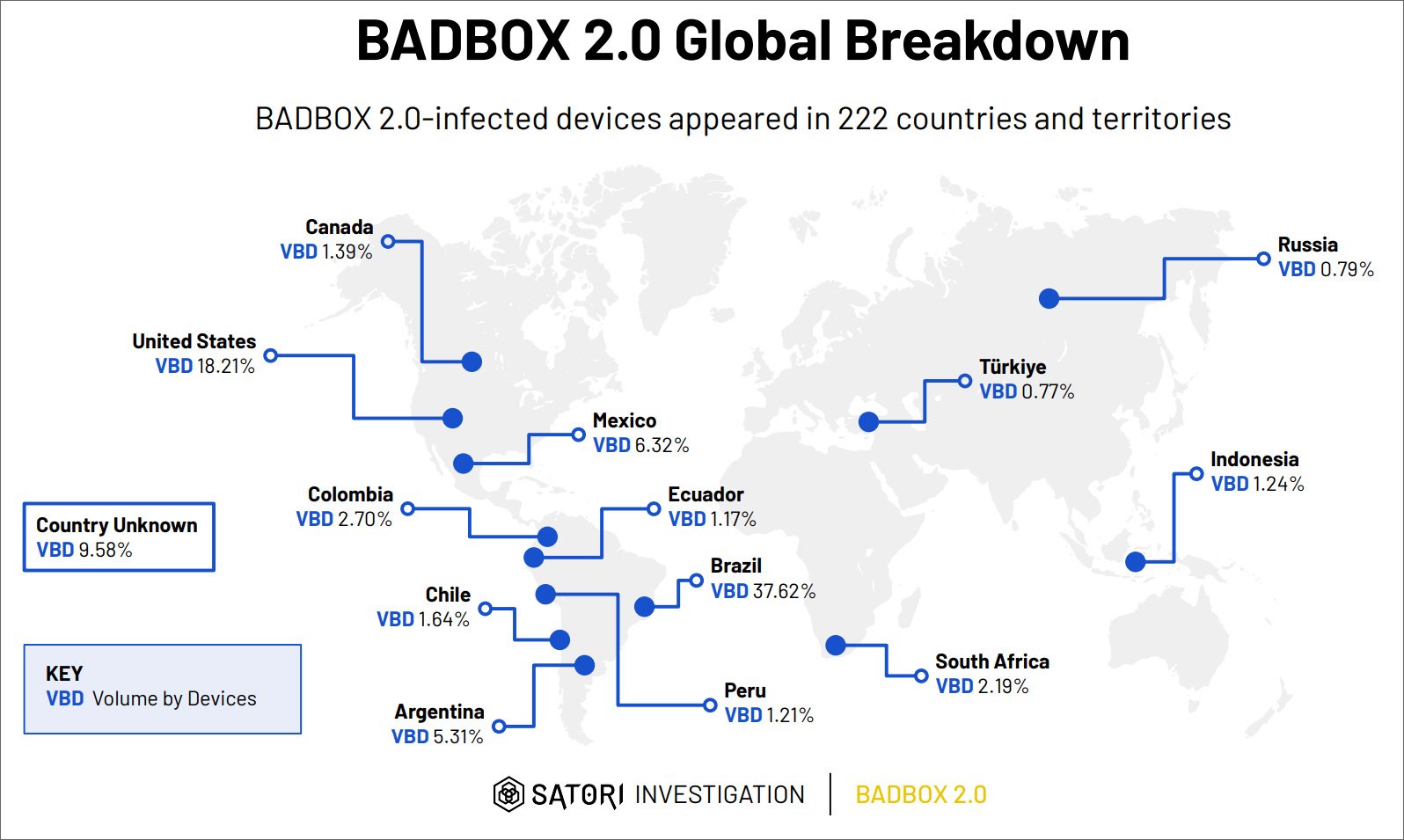
Supply: HUMAN Satori
In a joint operation led by HUMAN’s Satori group and Google, Development Micro, The Shadowserver Basis, and different companions, the BADBOX 2.0 botnet was disrupted once more to forestall over 500,000 contaminated units from speaking with the attacker’s servers.
Nevertheless, even with that disruption, the botnet continues to develop as shoppers buy extra compromised merchandise and join them to the Web.
An inventory of units identified to be impacted by the BADBOX malware are listed beneath:
| Machine Mannequin | Machine Mannequin | Machine Mannequin | Machine Mannequin |
| TV98 | X96Q_Max_P | Q96L2 | X96Q2 |
| X96mini | S168 | ums512_1h10_Natv | X96_S400 |
| X96mini_RP | TX3mini | HY-001 | MX10PRO |
| X96mini_Plus1 | LongTV_GN7501E | Xtv77 | NETBOX_B68 |
| X96Q_PR01 | AV-M9 | ADT-3 | OCBN |
| X96MATE_PLUS | KM1 | X96Q_PRO | Projector_T6P |
| X96QPRO-TM | sp7731e_1h10_native | M8SPROW | TV008 |
| X96Mini_5G | Q96MAX | Orbsmart_TR43 | Z6 |
| TVBOX | Good | KM9PRO | A15 |
| Transpeed | KM7 | iSinbox | I96 |
| SMART_TV | Fujicom-SmartTV | MXQ9PRO | MBOX |
| X96Q | isinbox | Mbox | R11 |
| GameBox | KM6 | X96Max_Plus2 | TV007 |
| Q9 Stick | SP7731E | H6 | X88 |
| X98K | TXCZ |
Signs of a BADBOX 2.0 an infection embody suspicious app marketplaces, disabled Google Play Defend settings, TV streaming units marketed as being unlocked or in a position to entry free content material, units from unknown manufacturers, and suspicious Web visitors.
Moreover, this malware is usually discovered on units not Google Play Defend licensed.
The FBI strongly advises shoppers to guard themselves from the botnet by following these steps:
- Assess all IoT units linked to house networks for suspicious exercise.
- By no means obtain apps from unofficial marketplaces providing “free streaming” apps.
- Monitor Web visitors to and from house networks.
- Hold all units in your house up to date with the most recent patches and updates.
Lastly, if you happen to suspect your system is compromised, you must isolate it from the remainder of the community and limit its Web entry, successfully disrupting the malware.



