
Infostealers like Atomic MacOS Stealer (AMOS) signify excess of a standalone malware. They’re foundational parts of a mature cybercrime economic system constructed round harvesting, buying and selling, and operationalizing stolen digital identities.
Moderately than performing as the top aim, fashionable stealers operate as large-scale information assortment engines that feed underground markets, the place stolen credentials, periods, and monetary information are purchased and offered to gasoline account takeovers, fraud, and follow-on intrusions.
What makes these campaigns significantly efficient is their extremely opportunistic social engineering strategy: attackers repeatedly adapt to expertise tendencies, abusing trusted platforms, widespread software program, search engines like google and yahoo, and even rising AI ecosystems to trick customers into executing malware themselves.
This mixture of industrialized information monetization and adaptive social engineering has made infostealers one of the vital dependable and scalable entry factors in in the present day’s cybercrime panorama.
Within the new 2026 Enterprise Infostealer Id Publicity report, Flare researchers spotlight the rising dominance of infostealers inside the cybercrime economic system and the increasing affect of id publicity on organizations.
On this article, we study the AMOS infostealer as a case research, exploring its evolution, operational mannequin, and real-world exercise throughout its energetic years.
How Do Infostealers Work?
Infostealers function as one of the vital vital enablers within the fashionable cybercrime kill chain as a result of they rework a single an infection into large-scale credential, session, and id compromise.
On the whole, as soon as executed on a sufferer machine, an infostealer quickly enumerates browsers, system credential shops, crypto wallets, messaging apps, and native information, extracting authentication information, session cookies, and delicate paperwork earlier than exfiltrating them to attacker-controlled infrastructure.
ClawHavoc – The Most Current Marketing campaign
Current analysis by Koi safety reminded us that AMOS infostealer dissemination methods are cunningly designed to search out weaknesses and exploit each section of expertise customers to steal their credentials.
The analysis describes ClawHavoc as a large-scale supply-chain marketing campaign concentrating on the OpenClaw and ClawHub ecosystem (A very talked-about private AI assistant) by poisoning the talent market itself.
Whereas the precise particulars are spectacular, what issues extra is the underlying tactic. AMOS distributors are capitalizing on OpenClaw’s reputation as AI-hyped software program.
As customers rush to put in it for private or organizational positive aspects, attackers see a chance to bundle AMOS malware inside it to steal helpful PII, credentials, and delicate information.
The supply mannequin: attackers uploaded expertise (OpenClaw add-ons) that seemed respectable: crypto instruments, productiveness utilities, YouTube helpers, finance or Google Workspace integrations, and so forth.
As soon as put in, the malware might steal credentials, crypto pockets information, browser periods, SSH keys, and different delicate information, highlighting how AI agent extension ecosystems can change into high-impact distribution channels when market vetting is weak.
That is the newest marketing campaign, let’s bear in mind how it began…
Flare tracks over 1 million new stealer logs weekly from darkish net markets and Telegram channels.
Detect compromised credentials, energetic session cookies, and company entry earlier than menace actors weaponize them in account takeover assaults.
AMOS the Malware – First Sighting of AMOS
AMOS first appeared round Could 2023 on a Telegram channel.
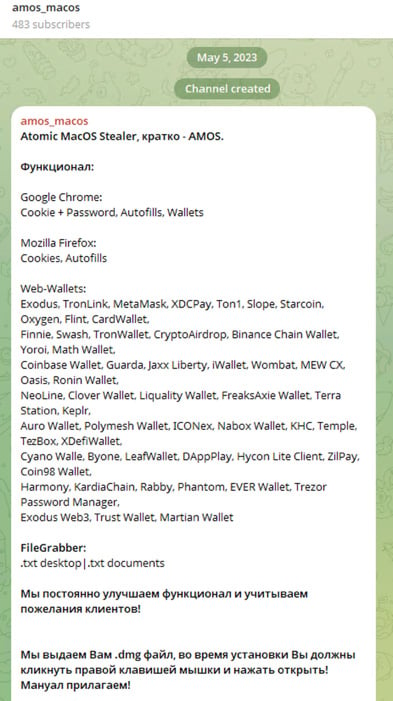
Stating its capabilities, which embrace exporting passwords from the Mac keychain, file grabber, system information, and macOS password exfiltration, browser session theft, crypto pockets information theft with varied infostealer administration capabilities (web-panel, exams, Telegram logs, and so forth).
Again then, the price was $1000 per thirty days, paid by means of USDT(TRC20), ETH, or BTC.
Since then, AMOS infostealer has change into part of the underground ecosystem, menace actors are prepared to purchase stealer logs that have been extracted from infostealers (corresponding to AMOS) with a view to use them as an preliminary entry to their very own nefarious enterprise.
For example, under you’ll be able to see {that a} Russian-speaking menace actor coping with Crypto pockets theft is in search of related AMOS logs.
View in Flare – join a free trial to entry
AMOS Modus-Operandi
Historically, AMOS is disseminated like each identified and widespread infostealers, corresponding to phishing hyperlinks, phishing emails, trojanized installers, and click on baits, however all through current years we’ve got additionally seen some extra noticeable campaigns.
Focusing on LastPass Customers
In an underground discussion board, we noticed a put up about LastPass that warned of an ongoing AMOS marketing campaign.
This marketing campaign was concentrating on macOS customers by means of faux functions distributed by way of fraudulent GitHub repositories, the place attackers impersonate over 100 well-known software program manufacturers to extend legitimacy.
The operation depends on web optimization poisoning throughout Google and Bing to push these malicious repositories into search outcomes, finally main victims to ClickFix-style pages that socially engineer them into pasting Terminal instructions, which obtain and execute the AMOS payload.
The marketing campaign is especially resilient as a result of attackers repeatedly generate new GitHub repositories utilizing automated account creation, highlighting how trusted developer platforms and search engines like google and yahoo are more and more abused as scalable malware distribution infrastructure.
AI-Pushed Dissemination Channels
ClawHavoc wasn’t AMOS’s first AI marketing campaign. In December 2025, Huntress reported that AMOS is concentrating on ChatGPT customers. The menace actors used the ChatGPT shared chat function to host malicious “set up guides” straight on a trusted area (chatgpt.com), making the lure considerably extra convincing.
Victims are pushed there primarily by way of paid search advertisements (web optimization poisoning/malvertising) selling a faux “ChatGPT Atlas browser for macOS”, then instructed to run a one-line terminal command, successfully turning the consumer into the execution mechanism.
This instance exhibits but once more that menace actors are weaponizing AI content material hype as a part of their malware distribution.
Conventional Dissemination Channels
Fashionable macOS infostealer campaigns rely closely on social engineering–pushed distribution reasonably than technical exploits. Menace actors generally create faux installers for widespread software program corresponding to Tor Browser, Photoshop, or Microsoft Workplace, packaging malware inside realistic-looking DMG disk photographs.
In parallel, they use malvertising by means of platforms like Google Adverts to drive victims to spoofed obtain websites that carefully mimic respectable distributors.
For instance, customers looking for respectable software program could also be redirected to look-alike domains internet hosting malicious installers that silently deploy stealers corresponding to AMOS.
One other rising tactic is using instruction-based execution methods (usually known as ClickFix), the place victims are guided to run instructions themselves within the macOS Terminal.
As a substitute of exploiting system vulnerabilities, attackers depend on convincing set up directions, which finally execute the malware payload. For example, asking customers to pull information into Terminal or paste instructions.
Collectively, these strategies replicate a shift towards abusing consumer belief, model impersonation, and legit distribution channels to bypass conventional safety controls and enhance an infection success charges.
The Underground Economic system Mannequin
The AMOS ecosystem operates as a structured Malware-as-a-Service (MaaS) provide chain, the place the builders (usually tracked in underground boards as AMOS sellers or associates) present the stealer platform, updates, infrastructure parts, and generally administration panels for a subscription price traditionally marketed round ~$1,000 per thirty days, sometimes paid in cryptocurrency.
Downstream menace actors buy entry to the stealer package, customise lures or distribution channels (malvertising, faux installers, phishing, web optimization poisoning, supply-chain abuse, or social engineering campaigns), and give attention to maximizing an infection quantity.
The first output is a listing of stolen credentials, PII, and session logs. This turns into a tradable commodity in underground markets.
These stealer logs are bought by secondary actors corresponding to entry brokers, account takeover specialists, and crypto cash-out operators, who use them for follow-on operations, together with SaaS account compromise, monetary fraud, ransomware preliminary entry, or cryptocurrency theft.
This multi-stage monetization mannequin turns AMOS infections right into a repeatable income pipeline, the place every actor within the chain focuses on growth, distribution, or monetization, reflecting the broader industrialization of the trendy infostealer economic system.
Not like conventional malware that focuses on persistence, protection evasion, lateral motion, or destruction, infostealers prioritize pace, information protection, and stealth, permitting attackers to rapidly convert stolen information into usable entry.
The ensuing “stealer logs” are then offered or traded in underground markets, the place different menace actors use them for account takeover, lateral motion, fraud, or follow-on assaults, defacto making infostealers a foundational data-supply layer for the broader cybercrime economic system.
The distributor layer is the place we sometimes see the “revolutionary” or “artistic” facet of those campaigns – and it’s what normally makes the headlines. That is the layer behind narratives like “AMOS is now concentrating on AI apps” or “AMOS campaigns are hitting LastPass customers.”
In actuality, the core malware builders usually stay constant, sometimes including a brand new function or bettering packaging and evasion, however the underlying functionality set adjustments incrementally.
The downstream log shoppers additionally are likely to function with established, repeatable monetization methods.
The distributors, nonetheless, are those driving actual marketing campaign evolution: they determine who to focus on, outline marketing campaign scope, select distribution channels, and repeatedly refine the psychological and social engineering methods used to control victims as a part of their operational playbook.
Be taught extra by signing up for our free trial.
Sponsored and written by Flare.


