Image this: you have hardened each laptop computer in your fleet with actual‑time telemetry, speedy isolation, and automatic rollback. However the company mailbox—the entrance door for many attackers—continues to be guarded by what’s successfully a Nineteen Nineties-era filter.
This is not a balanced strategy. Electronic mail stays a main vector for breaches, but we regularly deal with it as a static stream of messages as a substitute of a dynamic, post-delivery setting. This setting is wealthy with OAuth tokens, shared drive hyperlinks, and years of delicate knowledge.
The dialog must shift. We must always cease asking, “Did the gateway block the dangerous factor?” and begin asking, “How shortly can we see, include, and undo the harm when an attacker inevitably will get in?”
Taking a look at e mail safety via this lens forces a elementary shift towards the identical assume-breach, detect-and-respond mindset that already revolutionized endpoint safety.
The day the wall crumbled
Most safety professionals know the statistics. Phishing and credential theft proceed to dominate breach studies, and the monetary affect of Enterprise Electronic mail Compromise typically outweighs ransomware. However the knowledge tells a extra fascinating story, one which mirrors the decline of legacy antivirus.
A decade in the past, AV was good at catching recognized threats, however zero-day exploits and novel malware slipped previous. Endpoint Detection and Response (EDR) emerged as a result of groups wanted visibility after an attacker was already on the machine.
Electronic mail is following the identical script. Safe Electronic mail Gateways (SEGs) nonetheless filter spam and commodity phishing campaigns moderately nicely. What they miss are the assaults that outline the fashionable risk panorama:
- Payload-less Enterprise Electronic mail Compromise (BEC)
- Malicious hyperlinks which might be weaponized after supply
- Account takeovers utilizing stolen credentials that contain no malware in any respect
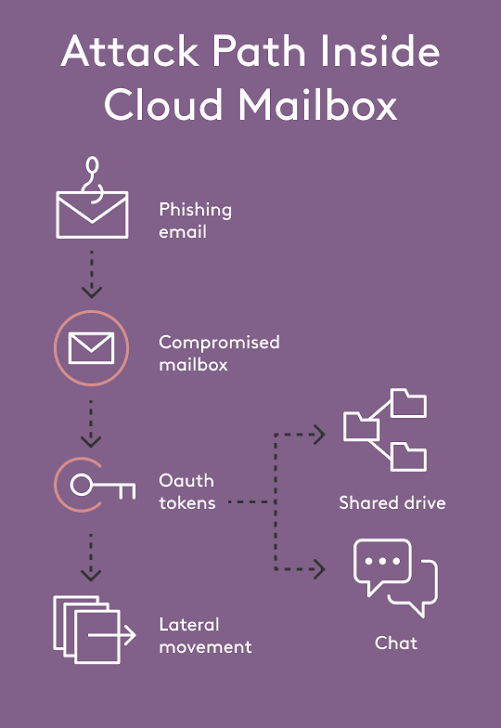
As soon as a single mailbox is compromised, the attacker features entry to a related graph of OAuth functions, shared recordsdata, chat histories, and calendar invitations inside Microsoft 365 or Google Workspace. Shifting laterally via this graph not often triggers one other SEG alert. The harm occurs fully contained in the cloud workspace.
What e mail safety can be taught from the endpoint
Within the endpoint world, the breakthrough wasn’t a greater blacklist. It was the belief that prevention have to be paired with steady visibility and quick, automated response. EDR platforms gave us the power to document course of bushes, registry modifications, and community calls. When a risk was detected, a bunch might be remoted and modifications might be rolled again, all from a single console.
Now think about giving e mail directors the identical tremendous‑powers: a rewind button for messages, OAuth scopes and file shares; the power to freeze—or a minimum of MFA‑problem—a mailbox the moment a dangerous rule is created; and a timeline that exhibits who learn which delicate thread after credentials have been stolen.
This mix of capabilities is what a contemporary, EDR-like strategy to e mail safety offers. It is a easy thought: assume an attacker will ultimately land in a mailbox and construct the tooling wanted to detect, examine, and include the fallout.
The API-first second that made it potential
For years, including post-delivery controls to e mail required fragile journaling configurations or heavyweight endpoint brokers. The cloud suites quietly solved this drawback for us.
Microsoft Graph and Google’s Workspace APIs now expose the mandatory telemetry—mailbox audit logs, message IDs, sharing occasions, and permission modifications—securely over OAuth. The identical APIs that present visibility additionally present management. They’ll revoke a token, pull a delivered message from each inbox, or take away a forwarding rule in seconds.
The sensors and the actuators are already baked into the platform. We simply want to attach them to a workflow that looks like EDR. As we have argued in our submit, The Evolution of Electronic mail Safety, this richness of telemetry is what permits safety groups to maneuver past the whack-a-mole of tuning filter guidelines. As an alternative of ready for a person to report a phish, the platform can discover an impossible-travel sign-in, see that the account instantly created 5 new sharing hyperlinks, and robotically remediate the chance.
Why this issues for lean safety groups
A Director of Safety at a small and even mid-size firm is usually the whole safety division, juggling vulnerability administration, incident response, and compliance. Software sprawl is the enemy.
An EDR-like strategy to e mail collapses a number of fragmented controls—SEG coverage, DLP, incident response playbooks, SaaS-to-SaaS monitoring—right into a single floor. There aren’t any MX document modifications, no brokers to deploy, and no dependency on customers clicking a “report phish” button.
Extra importantly, it produces metrics that matter. As an alternative of citing an arbitrary “catch fee,” you possibly can reply board-level questions with concrete knowledge:
- How shortly can we detect a compromised mailbox?
- How a lot delicate knowledge was accessible earlier than containment?
- What number of dangerous OAuth grants have been revoked this quarter?
These numbers describe precise danger discount, not theoretical filter efficacy.
A practical solution to transfer ahead
This does not should be an summary train. The trail ahead is incremental, and every step offers a tangible safety profit.
- Allow native audit logs. Each Microsoft 365 and Google Workspace embody intensive logging. That is the bottom fact you may want for any future automation.
- Centralize your telemetry. In your SIEM or log platform, begin searching for alerts of compromise: sudden mail rule creation, mass file downloads, uncommon sign-in areas, and new OAuth grants.
- Check automated response. Use the native APIs to check “message clawback” with a phishing simulation. Each Microsoft Graph and the Gmail API supply these endpoints out of the field.
- Consider devoted platforms. Decide them on their breadth of protection, the sophistication of their post-compromise playbooks, and the velocity between detection and automatic motion.
This journey turns guesswork into proof, a dwell breach right into a contained incident, and retains the human effort required proportional to your staff’s measurement.
The underside line
Nobody in 2025 would argue that endpoint antivirus is ample by itself. We assume prevention will ultimately be bypassed, so we construct for detection and response. Electronic mail deserves the identical pragmatic strategy.
In fact inbound detection stays essential. But when your safety stack cannot additionally inform you who learn a delicate contract after a mailbox takeover or forestall that publicity robotically then you might be nonetheless working within the antivirus period. The attackers have moved on. Your inbox, like your laptop computer, is prepared for an improve.
The place Materials Safety matches in
Materials Safety was constructed on the premise we have explored right here: e mail is a dynamic, high-value setting that wants post-delivery defenses, not simply one other pre-delivery filter.
As a result of Materials integrates straight with Microsoft 365 and Google Workspace through their native APIs, deployment takes hours, not months, with no disruption to mail move.
As soon as related, Materials information the identical high-quality‑grained telemetry that powers EDR on the endpoint—each mailbox rule, OAuth grant, file share, and signal‑in occasion—then layers on automated playbooks that shrink a breach window from days to minutes. A suspicious signal‑in can set off a simply‑in‑time MFA problem, whereas delivered phish are clawed again throughout each inbox earlier than they’re even learn. Historic mail is wrapped in zero‑data encryption that forces re‑authentication, so stolen credentials alone cannot unlock years of delicate knowledge.
Maybe most significantly for safety groups of 1, Materials folds these controls right into a single, searchable timeline. You possibly can reply board‑stage questions—What was accessed? Who noticed it? How shortly did we include it?—with out stitching collectively half a dozen logs.
Briefly, Materials brings the “assume breach, detect quick, reply quicker” ethos of recent endpoint protection to the inbox, turning e mail from a perennial blind spot into a completely monitored, quickly recoverable asset.