The cybercriminals answerable for Kimwolf — a disruptive botnet that has contaminated greater than 2 million units — not too long ago shared a screenshot indicating they’d compromised the management panel for Badbox 2.0, an unlimited China-based botnet powered by malicious software program that comes pre-installed on many Android TV streaming bins. Each the FBI and Google say they’re looking for the folks behind Badbox 2.0, and because of bragging by the Kimwolf botmasters we could now have a a lot clearer thought about that.
Our first story of 2026, The Kimwolf Botnet is Stalking Your Native Community, detailed the distinctive and extremely invasive strategies Kimwolf makes use of to unfold. The story warned that the overwhelming majority of Kimwolf contaminated techniques had been unofficial Android TV bins which might be usually marketed as a approach to watch limitless (pirated) film and TV streaming companies for a one-time price.
Our January 8 story, Who Benefitted from the Aisuru and Kimwolf Botnets?, cited a number of sources saying the present directors of Kimwolf glided by the nicknames “Dort” and “Snow.” Earlier this month, an in depth former affiliate of Dort and Snow shared what they mentioned was a screenshot the Kimwolf botmasters had taken whereas logged in to the Badbox 2.0 botnet management panel.
That screenshot, a portion of which is proven under, reveals seven approved customers of the management panel, together with one which doesn’t fairly match the others: In response to my supply, the account “ABCD” (the one that’s logged in and listed within the high proper of the screenshot) belongs to Dort, who someway found out the way to add their e mail deal with as a legitimate consumer of the Badbox 2.0 botnet.
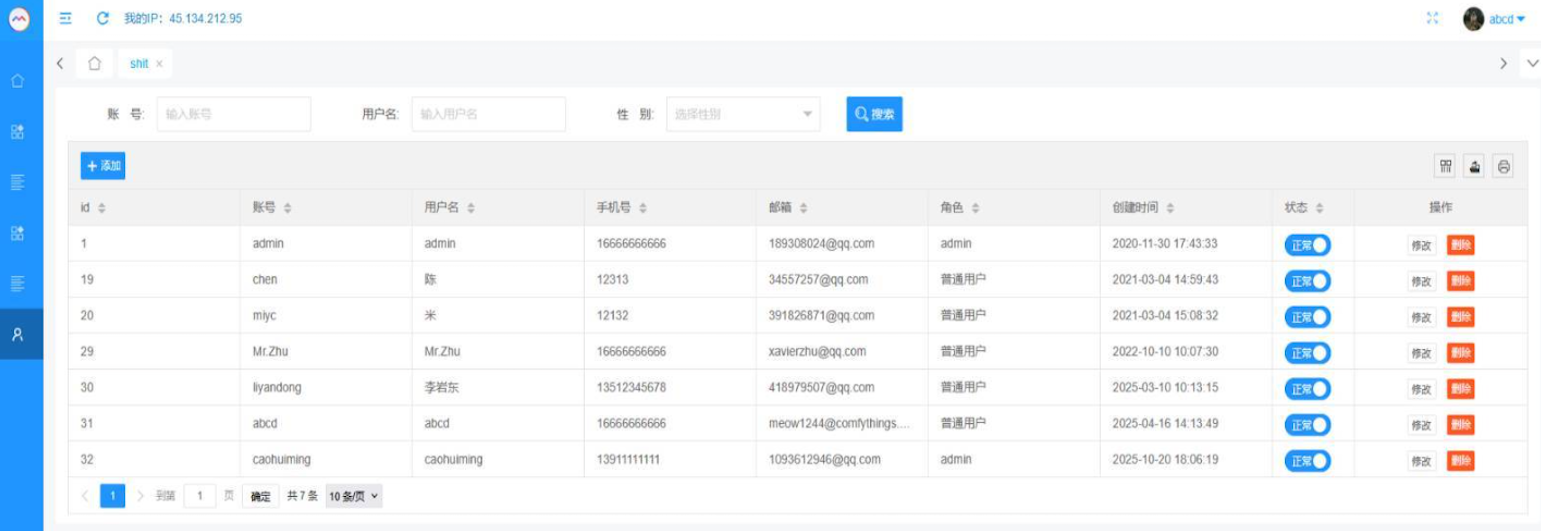
The management panel for the Badbox 2.0 botnet lists seven approved customers and their e mail addresses. Click on to enlarge.
Badbox has a storied historical past that effectively predates Kimwolf’s rise in October 2025. In July 2025, Google filed a “John Doe” lawsuit (PDF) towards 25 unidentified defendants accused of working Badbox 2.0, which Google described as a botnet of over ten million unsanctioned Android streaming units engaged in promoting fraud. Google mentioned Badbox 2.0, along with compromising a number of kinds of units prior to buy, can also infect units by requiring the obtain of malicious apps from unofficial marketplaces.
Google’s lawsuit got here on the heels of a June 2025 advisory from the Federal Bureau of Investigation (FBI), which warned that cyber criminals had been gaining unauthorized entry to house networks by both configuring the merchandise with malware previous to the consumer’s buy, or infecting the machine because it downloads required purposes that comprise backdoors — often through the set-up course of.
The FBI mentioned Badbox 2.0 was found after the unique Badbox marketing campaign was disrupted in 2024. The unique Badbox was recognized in 2023, and primarily consisted of Android working system units (TV bins) that had been compromised with backdoor malware prior to buy.
KrebsOnSecurity was initially skeptical of the declare that the Kimwolf botmasters had hacked the Badbox 2.0 botnet. That’s, till we started digging into the historical past of the qq.com e mail addresses within the screenshot above.
CATHEAD
A web based seek for the deal with 34557257@qq.com (pictured within the screenshot above because the consumer “Chen“) reveals it’s listed as a degree of contact for a variety of China-based expertise corporations, together with:
–Beijing Hong Dake Wang Science & Know-how Co Ltd.
–Beijing Hengchuang Imaginative and prescient Cell Media Know-how Co. Ltd.
–Moxin Beijing Science and Know-how Co. Ltd.
The web site for Beijing Hong Dake Wang Science is asmeisvip[.]internet, a site that was flagged in a March 2025 report by HUMAN Safety as considered one of a number of dozen websites tied to the distribution and administration of the Badbox 2.0 botnet. Ditto for moyix[.]com, a site related to Beijing Hengchuang Imaginative and prescient Cell.
A search on the breach monitoring service Constella Intelligence finds 34557257@qq.com at one level used the password “cdh76111.” Pivoting on that password in Constella reveals it’s identified to have been utilized by simply two different e mail accounts: daihaic@gmail.com and cathead@gmail.com.
Constella discovered cathead@gmail.com registered an account at jd.com (China’s largest on-line retailer) in 2021 beneath the title “陈代海,” which interprets to “Chen Daihai.” In response to DomainTools.com, the title Chen Daihai is current within the unique registration information (2008) for moyix[.]com, together with the e-mail deal with cathead@astrolink[.]cn.
By the way, astrolink[.]cn is also among the many Badbox 2.0 domains recognized in HUMAN Safety’s 2025 report. DomainTools finds cathead@astrolink[.]cn was used to register greater than a dozen domains, together with vmud[.]internet, yet one more Badbox 2.0 area tagged by HUMAN Safety.
XAVIER
A cached copy of astrolink[.]cn preserved at archive.org reveals the web site belongs to a cellular app growth firm whose full title is Beijing Astrolink Wi-fi Digital Know-how Co. Ltd. The archived web site reveals a “Contact Us” web page that lists a Chen Daihai as a part of the corporate’s expertise division. The opposite particular person featured on that contact web page is Zhu Zhiyu, and their e mail deal with is listed as xavier@astrolink[.]cn.
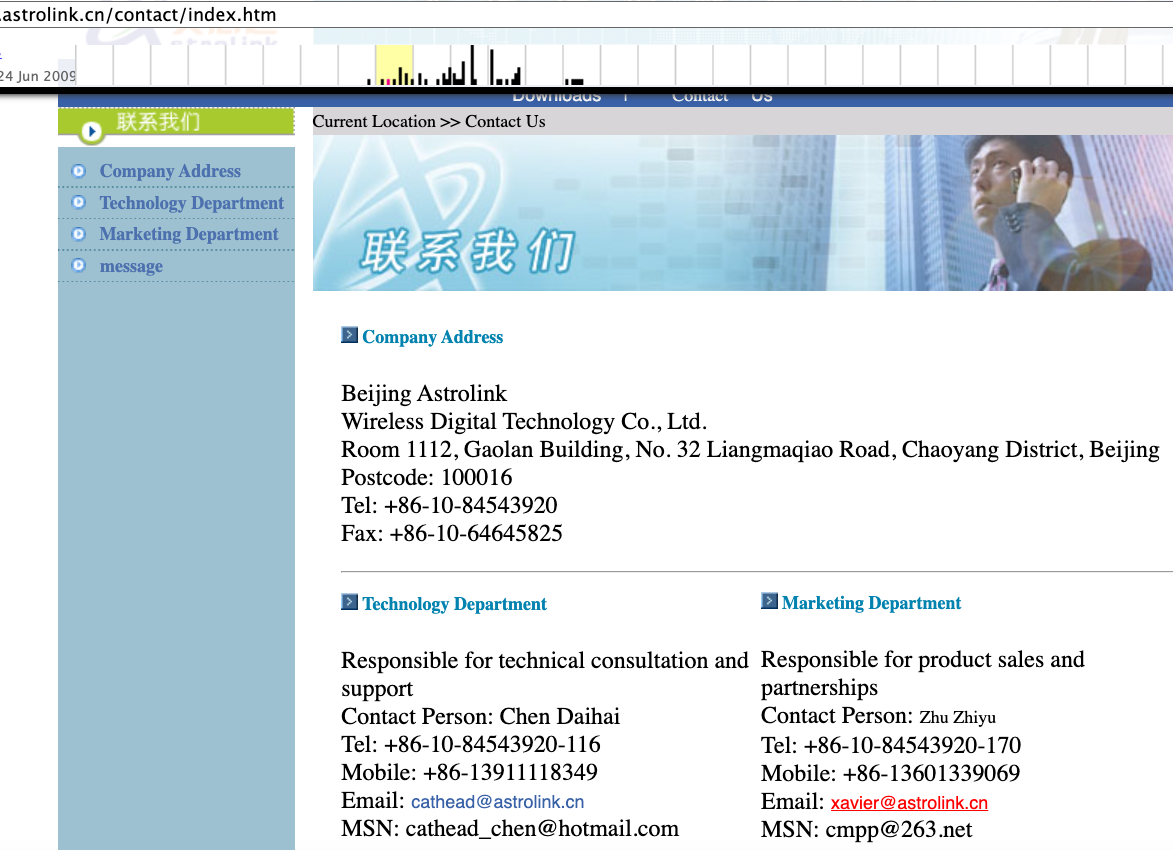
A Google-translated model of Astrolink’s web site, circa 2009. Picture: archive.org.
Astute readers will discover that the consumer Mr.Zhu within the Badbox 2.0 panel used the e-mail deal with xavierzhu@qq.com. Looking out this deal with in Constella reveals a jd.com account registered within the title of Zhu Zhiyu. A reasonably distinctive password utilized by this account matches the password utilized by the deal with xavierzhu@gmail.com, which DomainTools finds was the unique registrant of astrolink[.]cn.
ADMIN
The very first account listed within the Badbox 2.0 panel — “admin,” registered in November 2020 — used the e-mail deal with 189308024@qq.com. DomainTools reveals this e mail is discovered within the 2022 registration information for the area guilincloud[.]cn, which incorporates the registrant title “Huang Guilin.”
Constella finds 189308024@qq.com is related to the China cellphone quantity 18681627767. The open-source intelligence platform osint.industries reveals this cellphone quantity is linked to a Microsoft profile created in 2014 beneath the title Guilin Huang (桂林 黄). The cyber intelligence platform Spycloud says that cellphone quantity was utilized in 2017 to create an account on the Chinese language social media platform Weibo beneath the username “h_guilin.”
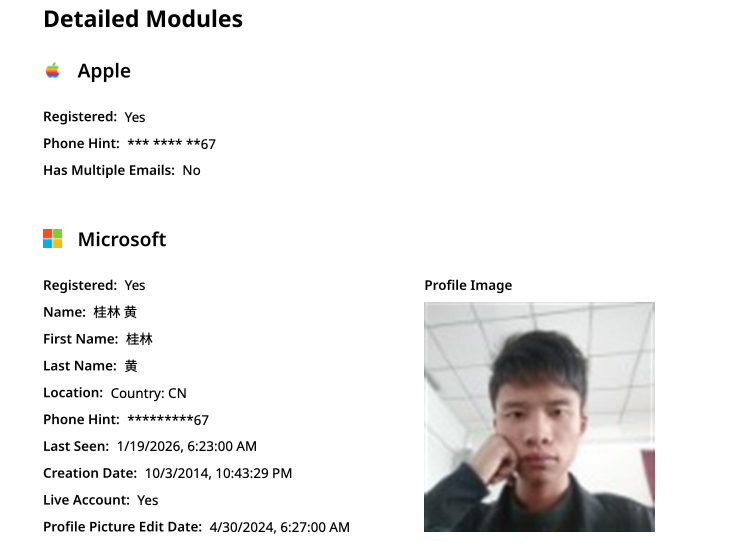
The general public data connected to Guilin Huang’s Microsoft account, in line with the breach monitoring service osintindustries.com.
The remaining three customers and corresponding qq.com e mail addresses had been all linked to people in China. Nonetheless, none of them (nor Mr. Huang) had any obvious connection to the entities created and operated by Chen Daihai and Zhu Zhiyu — or to any company entities for that matter. Additionally, none of those people responded to requests for remark.
The thoughts map under consists of search pivots on the e-mail addresses, firm names and cellphone numbers that recommend a connection between Chen Daihai, Zhu Zhiyu, and Badbox 2.0.
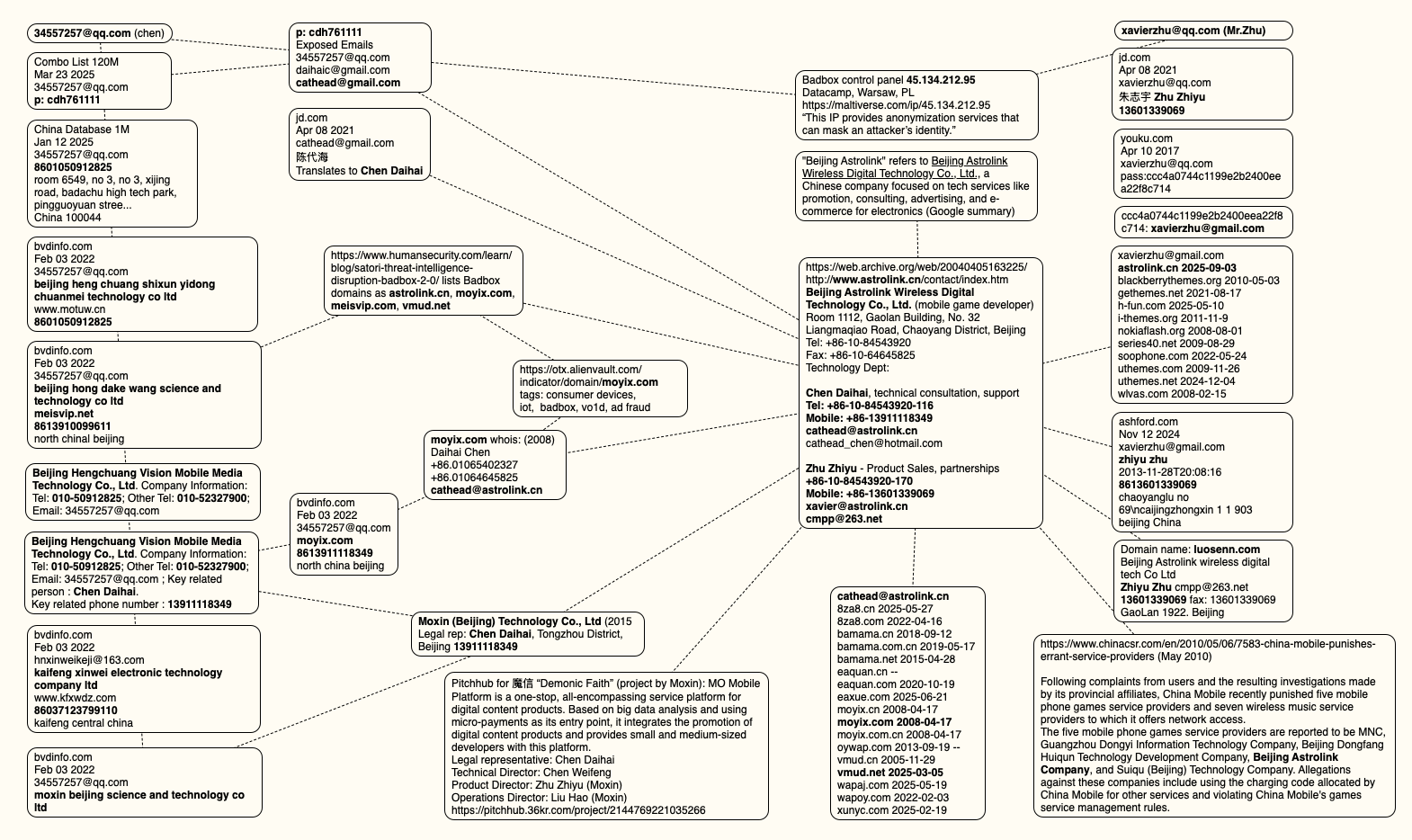
This thoughts map consists of search pivots on the e-mail addresses, firm names and cellphone numbers that seem to attach Chen Daihai and Zhu Zhiyu to Badbox 2.0. Click on to enlarge.
UNAUTHORIZED ACCESS
The concept that the Kimwolf botmasters might have direct entry to the Badbox 2.0 botnet is a giant deal, however explaining precisely why that’s requires some background on how Kimwolf spreads to new units. The botmasters found out they might trick residential proxy companies into relaying malicious instructions to weak units behind the firewall on the unsuspecting consumer’s native community.
The weak techniques sought out by Kimwolf are primarily Web of Issues (IoT) units like unsanctioned Android TV bins and digital picture frames that haven’t any discernible safety or authentication built-in. Put merely, in case you can talk with these units, you may compromise them with a single command.
Our January 2 story featured analysis from the proxy-tracking agency Synthient, which alerted 11 completely different residential proxy suppliers that their proxy endpoints had been weak to being abused for this sort of native community probing and exploitation.
Most of these weak proxy suppliers have since taken steps to stop clients from going upstream into the native networks of residential proxy endpoints, and it appeared that Kimwolf would not be capable to rapidly unfold to tens of millions of units just by exploiting some residential proxy supplier.
Nonetheless, the supply of that Badbox 2.0 screenshot mentioned the Kimwolf botmasters had an ace up their sleeve the entire time: Secret entry to the Badbox 2.0 botnet management panel.
“Dort has gotten unauthorized entry,” the supply mentioned. “So, what occurred is regular proxy suppliers patched this. However Badbox doesn’t promote proxies by itself, so it’s not patched. And so long as Dort has entry to Badbox, they’d be capable to load” the Kimwolf malware straight onto TV bins related to Badbox 2.0.
The supply mentioned it isn’t clear how Dort gained entry to the Badbox botnet panel. But it surely’s unlikely that Dort’s current account will persist for for much longer: All of our notifications to the qq.com e mail addresses listed within the management panel screenshot obtained a duplicate of that picture, in addition to questions in regards to the apparently rogue ABCD account.


