
A newly found marketing campaign dubbed “Stayin’ Alive” has been focusing on authorities organizations and telecommunication service suppliers throughout Asia since 2021, utilizing all kinds of “disposable” malware to evade detection.
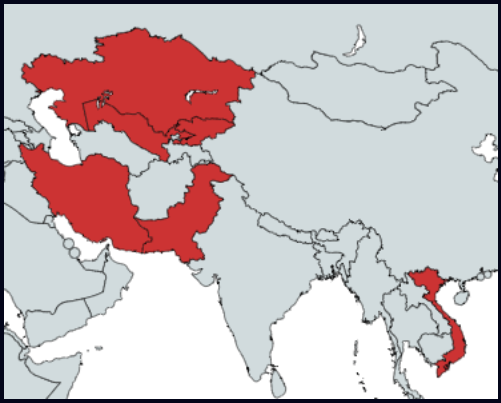
A lot of the marketing campaign’s targets seen by cybersecurity agency Verify Level are primarily based in Kazakhstan, Uzbekistan, Pakistan, and Vietnam, whereas the marketing campaign continues to be underway.
The assaults seem to originate from the Chinese language espionage actor often known as ‘ToddyCat,’ which depends on spear-phishing messages carrying malicious attachments to load quite a lot of malware loaders and backdoors.
The researchers clarify that the risk actors use many several types of {custom} software, which they consider are disposable to assist evade detection and stop linking assaults to one another..
“The huge set of instruments described on this report are custom-made and certain simply disposable. Because of this, they present no clear code overlaps with any identified toolset, not even with one another,” explains Verify Level.
Assault begins with an electronic mail
The assault begins with a spear-phishing electronic mail crafted to focus on particular people in key organizations, urging them to open the hooked up ZIP file.
The archive comprises a digitally signed executable named to match the e-mail context and a malicious DLL that exploits a vulnerability (CVE-2022-23748) in Audinate’s Dante Discovery software program to side-load the “CurKeep” malware on the system.
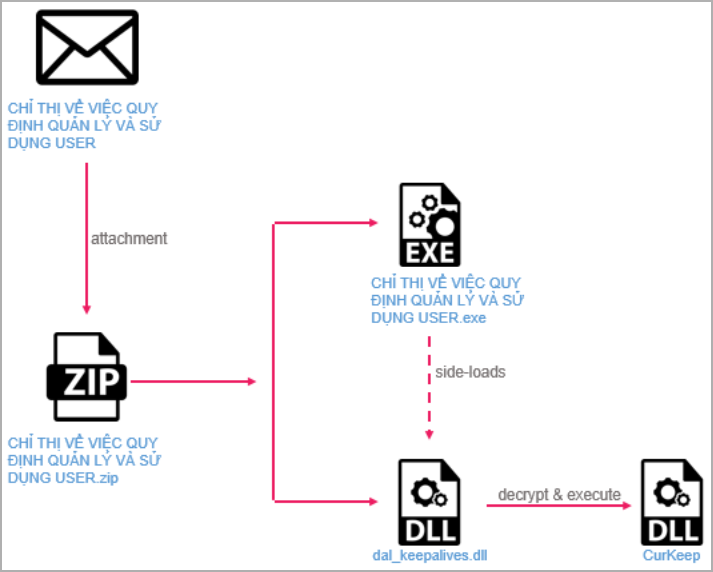
CurKeep is a 10kb backdoor that establishes persistence on the breached machine, sends system information to the command-and-control (C2) server, after which waits for instructions.
The backdoor can exfiltrate a listing record for the sufferer’s Program Recordsdata, indicating what software program is put in on the pc, execute instructions and ship the output to the C2 server, and deal with file-based duties as instructed by its operators.
Past CurKeep, the marketing campaign makes use of different instruments, primarily loaders, executed primarily by means of related DLL side-loading strategies.
Notable ones embrace the CurLu loader, CurCore, and CurLog loader, every with distinctive functionalities and an infection mechanisms.
CurCore is probably the most attention-grabbing of the secondary payloads, as it will possibly create recordsdata and populate their contents with arbitrary information, execute distant instructions, or learn a file and return its information in base64 encoded type.
One other notable backdoor that stands out from the remainder is ‘StylerServ,’ which acts as a passive listener that screens visitors on 5 ports (60810 by means of 60814) for a particular XOR-encrypted configuration file (‘stylers.bin’).
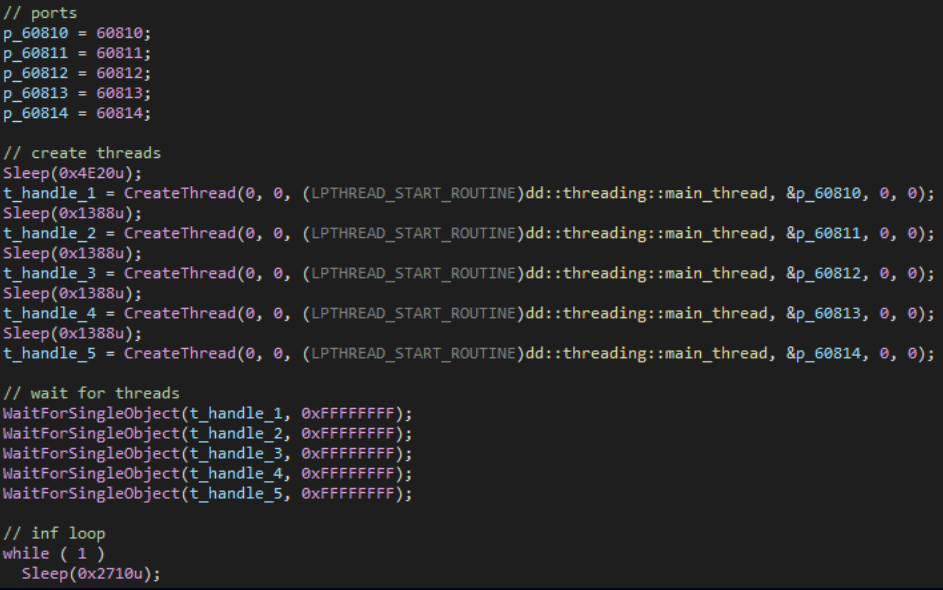
The report doesn’t specify the precise performance or objective of StylerServ or stylers.bin, however it’s possible a part of a stealthy configuration serving mechanism for different malware elements.
Verify Level reviews that “Stayin’ Alive” makes use of numerous samples and variants of those loaders and payloads, typically tailor-made to particular regional targets (language, filenames, themes).
The safety firm says the newly recognized cluster is probably going a section of a broader marketing campaign involving extra undiscovered instruments and assault strategies.
Judging from the big variety of distinct instruments seen within the assaults and their stage of customization, these seem like disposable.
Regardless of the code variations in these instruments, all of them hook up with the identical infrastructure, which Kaspersky beforehand linked to ToddyCat, a gaggle of Chinese language cyber spies.
Replace 10/12 – Shortly after publishing this report, Kaspersky posted an replace on its monitoring of the ToddyCat APT, highlighting new assault strategies and payloads its analysts found not too long ago.
Over the previous yr, Kaspersky noticed a parallel cluster of exercise from the identical risk actor, completely different from the one seen by Verify Level, with two assault variants using reliable VLC executables to load malware utilizing the DLL sideloading approach.
A notable malware deployed in these assaults is ‘Ninja Agent,’ which options file administration, reverse shell, course of administration, and extra.
Different instruments ToddyCat deployed in these assaults embrace LoFiSe (file tracker and stealer), Cobalt Strike (penetration testing suite), DropBox Uploader, and a passive UDP backdoor.


