
Whether or not it’s logging into electronic mail, provisioning a digital machine, or accessing a CRM platform, Id and Entry Administration (IAM) is the digital spine of labor.
But, as organizations develop, the controls meant to safeguard these identities usually fail to maintain tempo with the size, velocity, and complexity of right now’s environments.
A standard friction level on this panorama is granting momentary entry, or Simply-In-Time (JIT) entry, to delicate purposes. IT groups are sometimes caught within the center: enterprise models count on instant entry to keep up productiveness, whereas safety groups and auditors demand zero gaps and clear trails.
This text explores a pre-built Tines workflow designed to resolve this particular problem: Grant Non permanent Software Entry. The workflow helps groups stability velocity with safety by way of orchestration.
The issue: scaling entry equals scaling danger
“Scaling entry equals scaling danger,” notes Stephen McKenna, IT Operations Technician at Tines in a current weblog publish on IAM orchestration. Each “joiner, mover, or leaver” occasion spawns a series of modifications.
In lots of organizations, these modifications are dealt with manually throughout patchwork techniques. Some purposes plug into Single Signal-On (SSO) shortly, whereas others require guide provisioning.
When a person wants JIT entry, maybe a developer wants manufacturing entry for debugging, or a contractor wants entry for a particular venture, the guide course of usually seems to be like this:
- Gradual Response Occasions: The person submits a ticket, which sits in a queue till an analyst sees it.
- Everlasting Privilege Creep: As soon as entry is granted, analysts usually neglect to revoke it. “Non permanent” entry turns into everlasting, resulting in privilege accumulation that attackers can exploit.
- Audit Nightmares: Proof of who accredited the entry, when it was granted, and when it was revoked is scattered throughout emails, Slack messages, and ticket feedback.
With out orchestration, accounts linger and privileges pile up.
Find out how trendy IT Ops groups use orchestration to handle capability, enhance reliability, and scale infrastructure with out burnout.
This sensible information exhibits learn how to substitute guide workflows with predictable, automated operations utilizing the instruments you have already got.
The answer: automated, time-bound provisioning
The Grant Non permanent Software Entry workflow automates your entire lifecycle of a JIT entry request.
By orchestrating instruments like Jira Software program, Okta, and Slack, the workflow ensures that entry is granted shortly, accredited correctly, and, most significantly, revoked mechanically when the time is up.
Right here is an outline of how the workflow operates:
1. Self-Service Request As an alternative of sending an electronic mail or DM, the person visits a Tines Web page—a easy, drag-and-drop net kind. They choose the applying they want (e.g., “AWS Manufacturing Console”), the period of entry required (e.g., “2 hours”), and the enterprise justification.
2. Automated Approval Routing Upon submission, Tines mechanically identifies the person’s supervisor or the applying proprietor. It sends a wealthy notification by way of Slack (or Microsoft Groups) to that approver. This message accommodates the request particulars and interactive “Approve” or “Deny” buttons.
3. Instantaneous Provisioning If accredited, the workflow triggers an API name to Okta. It provides the person to the precise Okta group related to that utility. This occurs immediately—no guide clicking by an IT admin required. Concurrently, a ticket is created or up to date in Jira Software program to log the approval for compliance functions.
4. The “Time-Out” That is the essential safety step. The workflow enters a “wait” state for the period specified by the person (e.g., 2 hours).
5. Automated Revocation As soon as the timer expires, Tines wakes up and performs the cleanup. It calls the Okta API once more to take away the person from the group, successfully revoking entry. Lastly, it updates the Jira ticket to “Closed” and notifies the person by way of Slack that their session has ended.
The advantages
Implementing this clever workflow delivers instant worth throughout three key pillars:
- Enforced Least Privilege: By automating the revocation of entry, you eradicate the chance of “lingering accounts.” Entry is granted just for the precise time wanted, decreasing the assault floor.
- Audit-Prepared Compliance: Each step—request, approval, provisioning, and revocation—is logged mechanically in Jira. When auditors ask for proof of entry controls, you will have a single supply of fact with out chasing down screenshots.
- Improved Person Expertise: Customers get entry in minutes, not days. They do not have to attend for an admin to return from lunch to click on a button in Okta.
- Effectivity: IT analysts are free of the repetitive “click-ops” work of including and eradicating customers from teams, permitting them to deal with higher-value safety duties.
Configuring the workflow
You needn’t begin from scratch. This workflow is obtainable as a pre-built story within the Tines Library.
Step 1: Import the Story: Go to the Tines Library and seek for Grant momentary utility entry. Click on “Import” to convey the template into your tenant.
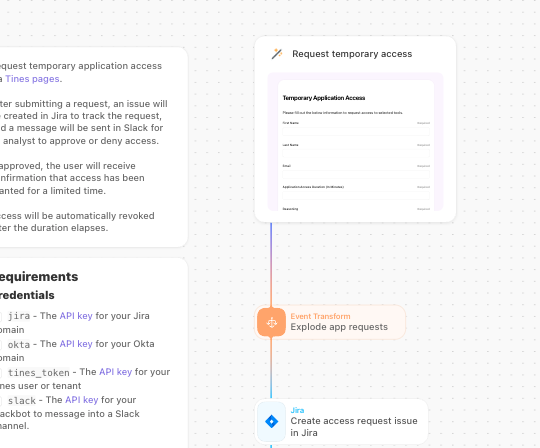
Step 2: Join Your Instruments: The workflow depends on Credentials to speak to your exterior instruments. You’ll need to attach:
- Okta: To handle group memberships.
- Jira Software program: To trace requests and approvals.
- Slack: For notifications and interactive approval messages.

Step 3: Configure the Tines Web page: Open the “Web page” aspect within the workflow. You possibly can customise the shape fields to match your group’s particular purposes. For instance, you would possibly create a dropdown menu itemizing “Salesforce Admin,” “AWS Write Entry,” and “GitHub Admin.”
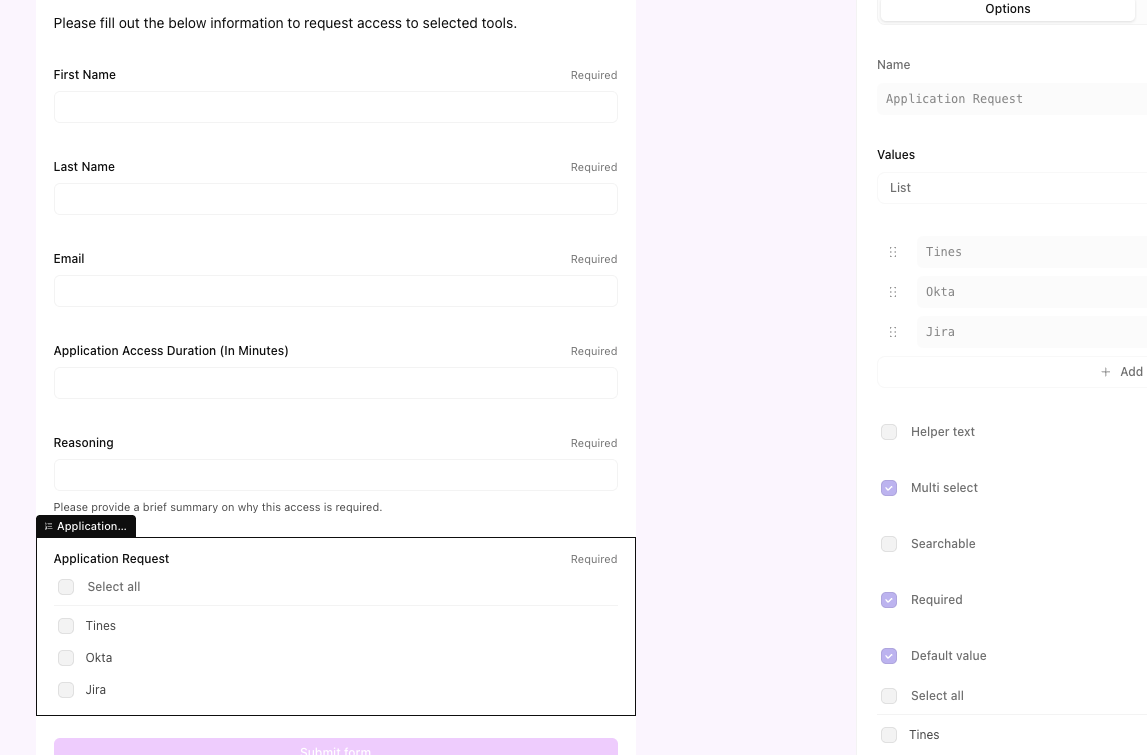
Step 4: Set Your Insurance policies: Alter the logic to suit your safety insurance policies. You would possibly need to cap the utmost period at 4 hours or require a second stage of approval for extremely delicate apps. As a result of Tines is versatile, you’ll be able to drag and drop these further logic blocks proper onto the canvas.
Step 5: Check and Publish: Run a take a look at request to make sure the Slack notifications fireplace and the Okta group modifications happen as anticipated. As soon as verified, publish the Web page and share the hyperlink along with your crew.
To do this workflow for your self, you’ll be able to join a free Tines account.
Sponsored and written by Tines.


