
Researchers have discovered that in roughly 80% of circumstances, spikes in malicious exercise like community reconnaissance, focused scanning, and brute-forcing makes an attempt focusing on edge networking gadgets are a precursor to the disclosure of recent safety vulnerabilities (CVEs) inside six weeks.
This has been found by risk monitoring agency GreyNoise, which studies these occurrences aren’t random, however are relatively characterised by repeatable and statistically important patterns.
GreyNoise bases this on information from its ‘International Remark Grid’ (GOG) collected since September 2024, making use of goal statistical thresholds to keep away from results-skewing cherry-picking.
After eradicating noisy, ambiguous, and low-quality information, the agency ended up with 216 occasions that certified as spike occasions, tied to eight enterprise edge distributors.
“Throughout all 216 spike occasions we studied, 50 p.c had been adopted by a brand new CVE inside three weeks, and 80 p.c inside six weeks,” clarify the researchers.
The correlation was notably stronger for Ivanti, SonicWall, Palo Alto Networks, and Fortinet merchandise, and weaker for MikroTik, Citrix, and Cisco. State-sponsored actors have repeatedly focused such programs for preliminary entry and persistence.
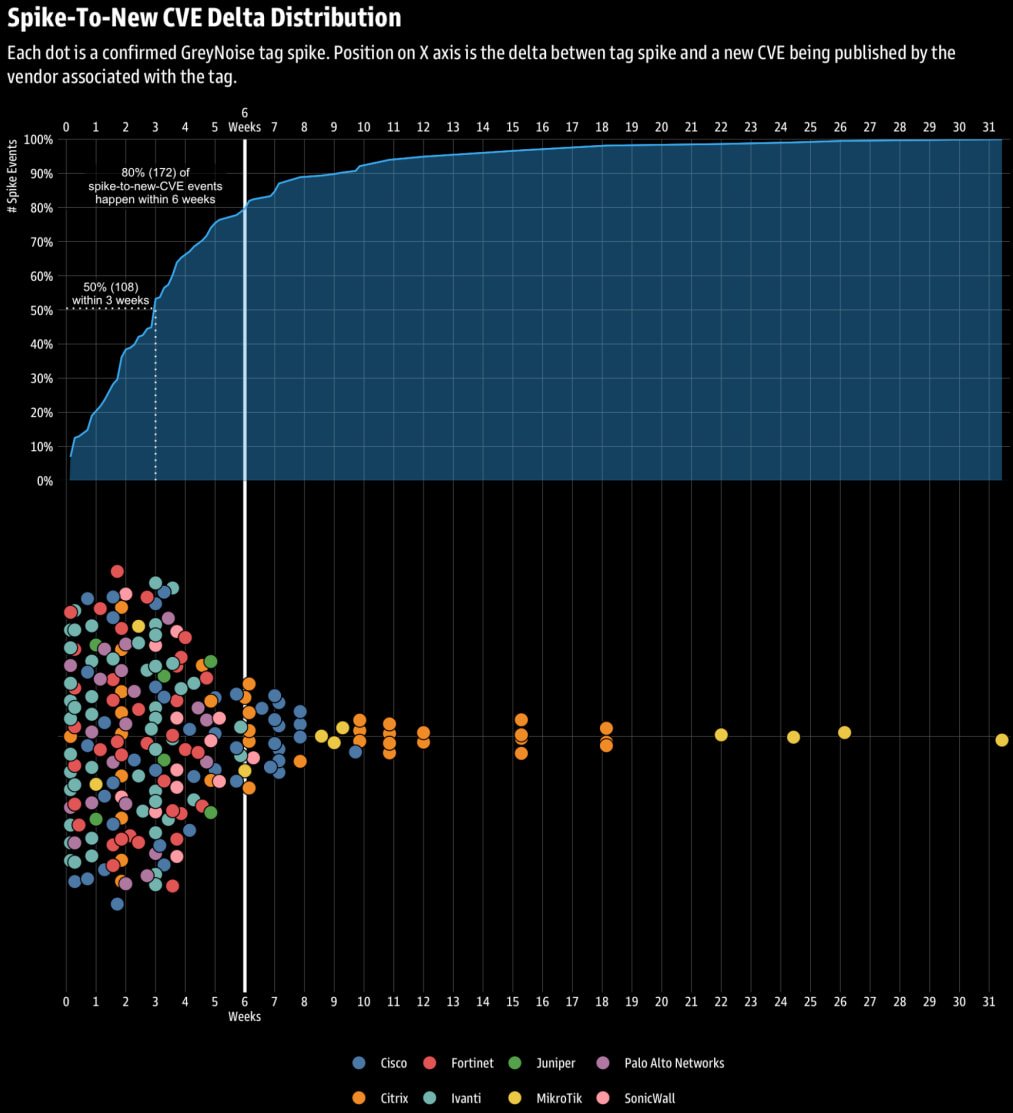
Supply: GreyNoise
GreyNoise notes that within the majority of the circumstances underlying these spikes, the attackers carry out exploit makes an attempt in opposition to older, identified flaws.
The researchers imagine that this both facilitates the invention of recent weaknesses or the invention of internet-exposed endpoints that may be focused within the subsequent section of the assault, which leverages novel exploits.
A “Mine Canary”
Historically, defenders reply after a CVE is revealed, however GreyNoise’s findings present that attacker conduct could be a main indicator and a software for organizing proactive defenses.
These pre-disclosure spikes give defenders a window to organize, improve monitoring, and harden programs in opposition to a possible assault, even when a safety replace doesn’t defend them they usually aren’t conscious of which system element or perform is definitely focused.
GreyNoise recommends that scanning exercise be carefully monitored and origin IPs promptly blocked, as this excludes them from reconnaissance that sometimes results in precise assaults in a while.
The researchers underline that scans for older flaws are to be anticipated in these circumstances, as attackers goal to catalog uncovered property. Therefore, these should not be disregarded as failed makes an attempt to breach fully-patched endpoints.
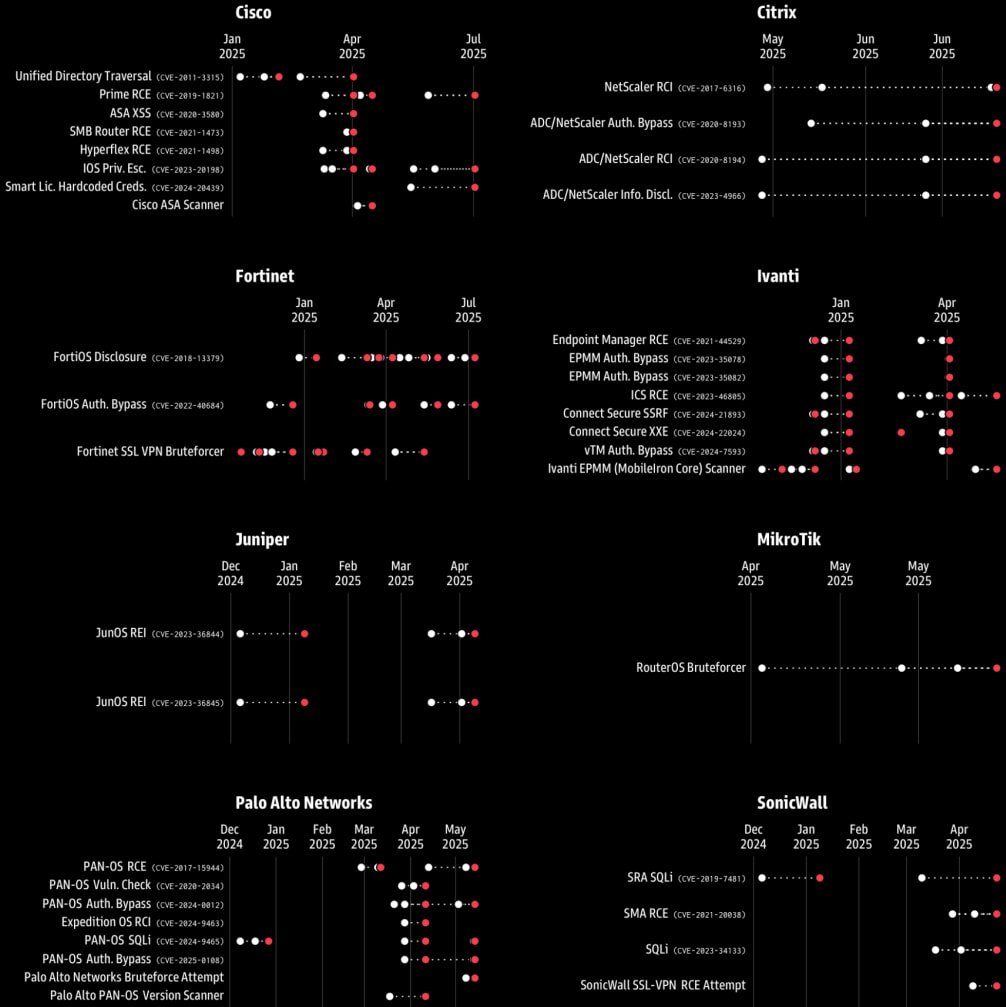
Supply: GreyNoise
On a associated growth, Google’s Venture Zero introduced that it’ll start informing the general public {that a} vulnerability has been found inside every week, serving to system admins bolster their defenses whereas distributors work on growing a patch.
Venture Zero will now share the seller/venture and product impacted by the brand new flaw, the invention time, and disclosure deadline (nonetheless at 90 days).
Missing technical particulars, proof-of-concept exploits, or every other data that might tip attackers, Google expects this alteration to haven’t any antagonistic impact on safety whereas on the identical time serving to cut back the “patch hole.”



