A China-based hacking group is deploying Warlock ransomware on Microsoft SharePoint servers susceptible to widespread assaults concentrating on the lately patched ToolShell zero-day exploit chain.
Non-profit safety group Shadowserver is at present monitoring over 420 SharePoint servers which might be uncovered on-line and stay susceptible to these ongoing assaults.
“Though Microsoft has noticed this risk actor deploying Warlock and Lockbit ransomware prior to now, Microsoft is at present unable to confidently assess the risk actor’s goals,” the corporate stated in a Wednesday report.
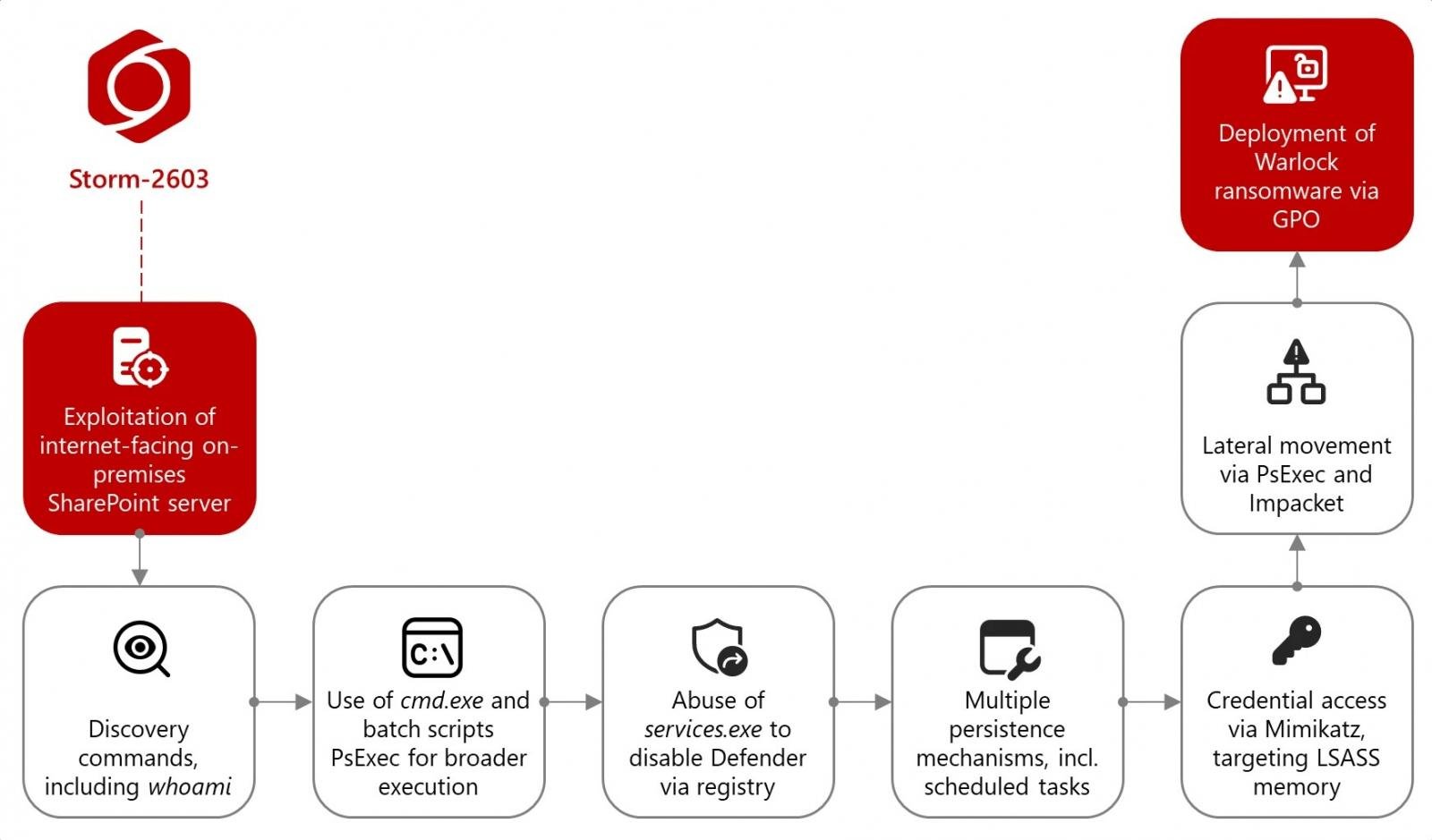
“Beginning on July 18, 2025, Microsoft has noticed Storm-2603 deploying ransomware utilizing these vulnerabilities.
After breaching the victims’ networks, Storm-2603 operators use the Mimikatz hacking device to extract plaintext credentials from LSASS reminiscence.
They then transfer laterally with PsExec and the Impacket toolkit, executing instructions through Home windows Administration Instrumentation (WMI), and modifying Group Coverage Objects (GPOs) to ship Warlock ransomware throughout compromised methods.
“Prospects ought to apply the on-premises SharePoint Server safety updates instantly and comply with the detailed mitigation steering in our weblog,” Microsoft additionally warned.
Microsoft Risk Intelligence researchers have additionally linked the Linen Hurricane and Violet Hurricane Chinese language state-backed hacking teams with these assaults on Tuesday, days after Dutch cybersecurity agency Eye Safety first detected zero-day assaults exploiting the CVE-2025-49706 and CVE-2025-49704 vulnerabilities.
Since then, Eye Safety CTO Piet Kerkhofs informed BleepingComputer that the variety of breached entities is far bigger, with “most of them already compromised for a while already.” In response to the cybersecurity firm’s statistics, the attackers have to date contaminated no less than 400 servers with malware and breached 148 organizations worldwide.
CISA additionally added the CVE-2025-53770 distant code execution flaw, a part of the identical ToolShell exploit chain, to its catalog of vulnerabilities exploited within the wild, ordering US federal companies to safe their methods inside a day.
Nonetheless, earlier this week, the Division of Vitality confirmed that the Nationwide Nuclear Safety Administration (the U.S. nuclear weapons company) was breached within the ongoing Microsoft SharePoint assaults, though the company has but to search out proof that delicate or categorized info was compromised within the incident.
Bloomberg reported that the attackers have additionally hacked into methods on the US Division of Training, the Rhode Island Normal Meeting, and Florida’s Division of Income, in addition to networks of European and Center Japanese governments.
The Washington Submit additionally reported that the Division of Well being and Human Providers’ Nationwide Institutes of Well being (the U.S. medical analysis company) was additionally breached.
Replace July 24, 06:15 EDT: Revised story to make it clearer that Storm-2603 is a China-based risk actor.
CISOs know that getting board buy-in begins with a transparent, strategic view of how cloud safety drives enterprise worth.
This free, editable board report deck helps safety leaders current threat, influence, and priorities in clear enterprise phrases. Flip safety updates into significant conversations and sooner decision-making within the boardroom.



