
Automotive large Scania confirmed it suffered a cybersecurity incident the place risk actors used compromised credentials to breach its Monetary Providers programs and steal insurance coverage declare paperwork.
Scania instructed BleepingComputer that the attackers emailed a number of Scania workers, threatening to leak the info on-line except their calls for had been met.
Scania is a significant Swedish producer of heavy vans, buses, and industrial and marine engines and is a member of the Volkswagen Group.
The corporate, which is understood for its sturdy fuel-efficient engines, employs over 59,000 folks and has an annual income of $20.5 billion, promoting over 100,000 automobiles yearly.
Late final week, risk monitoring platform Hackmanac noticed a hacking discussion board submit by a risk actor named ‘hensi,’ who’s promoting information they claimed to have stolen from ‘insurance coverage.scania.com,’ providing it to a single unique purchaser.
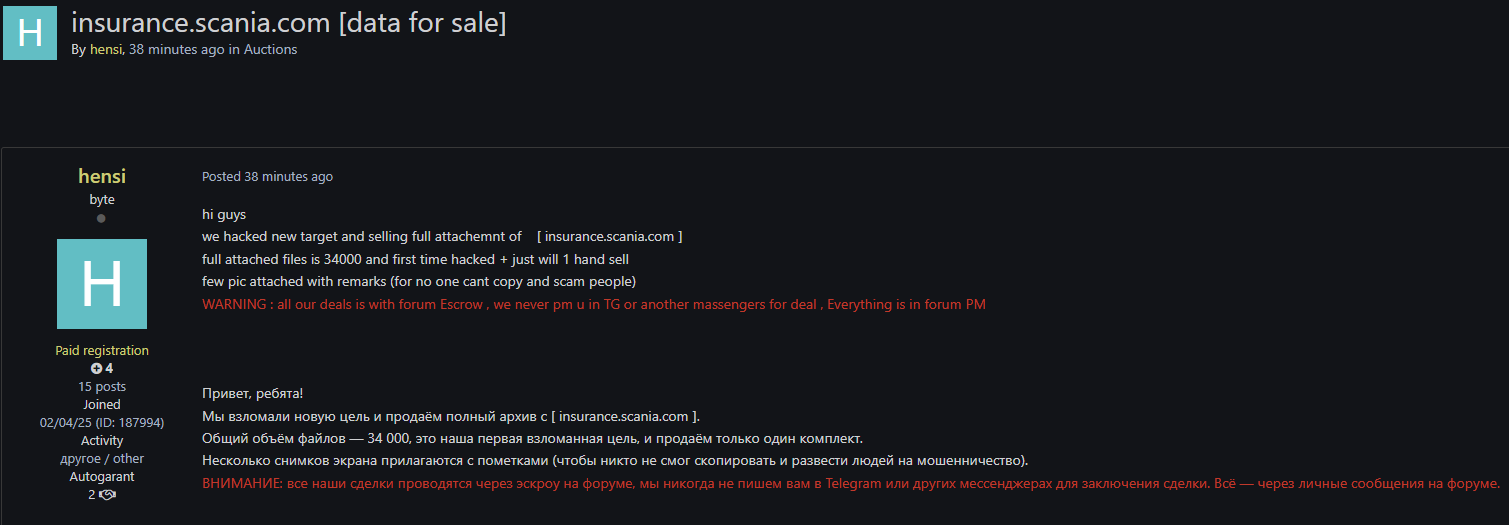
Supply: @H4ckmanac | X
Scania confirmed the breach to BleepingComputer, stating that their programs had been breached on Might 28, 2025, utilizing an exterior IT associate’s credentials stolen by infostealer malware.
“We will verify there was a safety associated incident within the utility “insurance coverage.scania.com”, the appliance is supplied by an exterior IT associate,” acknowledged a Scania spokesperson.
“On the twenty eighth and twenty ninth of Might, a perpetrator used credentials for a professional exterior person to achieve entry to a system used for insurance coverage functions; our present assumption is that the credentials utilized by the perpetrator had been leaked by a password stealer malware.”
“Utilizing the compromised account, paperwork associated to insurance coverage claims had been downloaded.”
Insurance coverage declare paperwork are prone to comprise private and presumably delicate monetary or medical information, so the incident may have a big influence on these affected. Right now, the variety of uncovered people stays undefined.
The breach was adopted by an extortion part the place the attackers contacted Scania workers immediately utilizing a @proton.me e mail tackle to extort the corporate, following up with the publication of samples of the stolen information on hacking boards.
“Early on the thirtieth (CEST) the attacker despatched emails from proton.me to numerous Scania workers threatening to reveal the info.”
“A follow-up e mail with related content material got here later from an unrelated third occasion whose e mail had been compromised. The info was later leaked by an actor named Hensi.”
The compromised utility is now not reachable on-line, and an investigation into the incident has been launched.
In the meantime, Scania instructed BleepingComputer that the breach had restricted influence and that it notified privateness authorities concerning the incident.
Patching used to imply complicated scripts, lengthy hours, and limitless hearth drills. Not anymore.
On this new information, Tines breaks down how fashionable IT orgs are leveling up with automation. Patch sooner, scale back overhead, and give attention to strategic work — no complicated scripts required.


