
Financially motivated risk actors are more and more sabotaging cloud backups along with main information, aiming to maximise leverage in extortion schemes, Google warned in its H2 2025 Cloud Risk Horizons Report, launched at present.
These risk actors might disable backup routines, delete saved information, or alter person permissions to dam restoration makes an attempt.
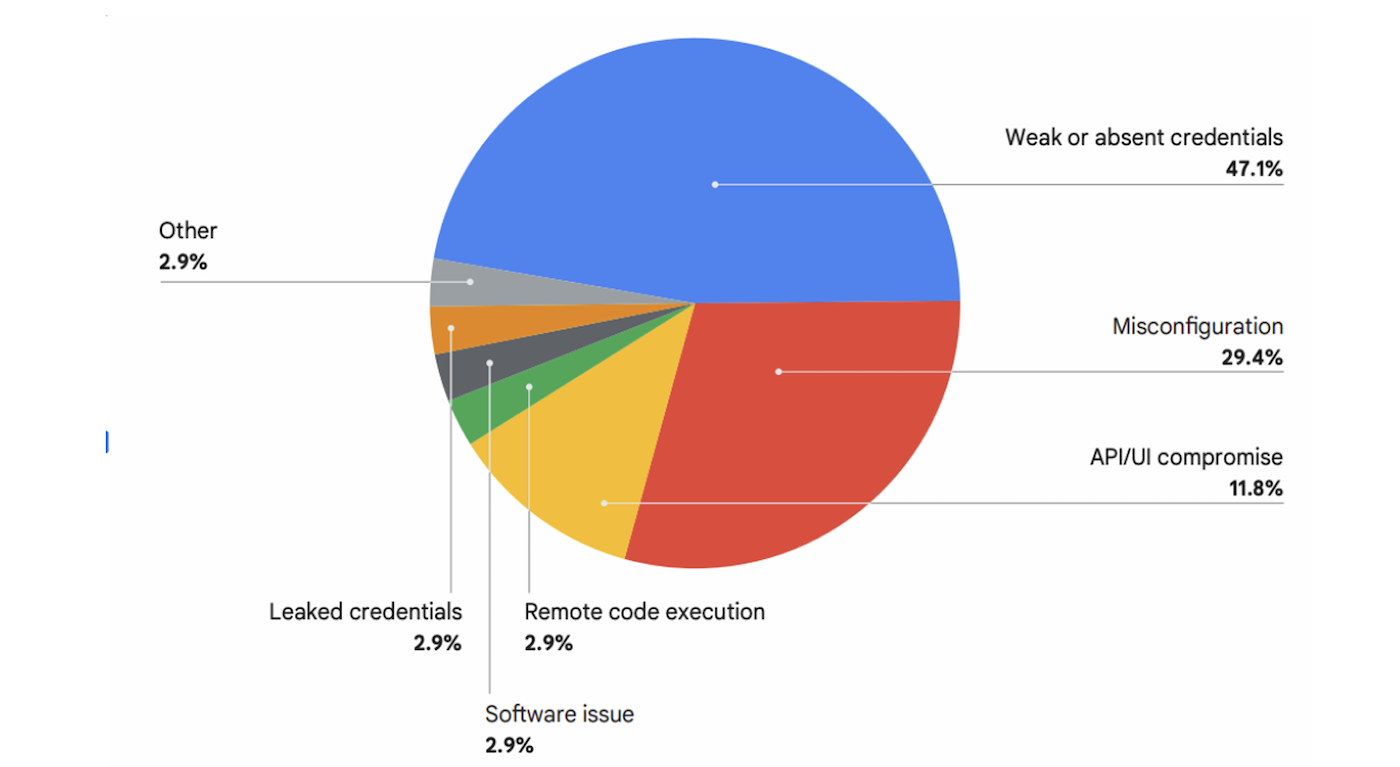
The commonest means risk actors infiltrate cloud environments
Within the second half of 2025, credential compromise accounted for 47% of cloud safety incidents, whereas misconfiguration adopted at 29%, based on Google Cloud. Leaked credentials — current in 2.9% of preliminary entry circumstances — additionally posed a rising concern.
The report famous that the sources of predominant threats had been similar to traits from earlier within the yr. The commonest entry factors had been weak or absent credentials, misconfigurations, and API or UI compromises.
Malware supply through cloud providers additionally rising
Google Cloud recognized these extra cybersecurity risk traits:
- Social engineering and MFA bypass proceed to be frequent ways for getting access to organizations’ cloud environments.
- Decoy PDFs hosted on legit cloud platforms are used to ship malware.
- Cloud providers akin to Google Drive, SharePoint, Dropbox, and GitHub are being misused to host contaminated PDFs.
- Entry through misconfigurations decreased by 4.9%.
- API/UI-based entry dropped by 5.3%.
In two high-profile circumstances, the North Korean state-sponsored risk actor — which Google Cloud calls UNC4899 — has focused cryptocurrency and blockchain industries with assaults that began as social media engineering, and ended with the attackers withdrawing thousands and thousands in cryptocurrency. In each circumstances, the attacker introduced themselves as searching for freelance alternatives for software program growth work, in a single case on LinkedIn and within the different on Telegram.
Greatest practices: Safe entry and monitor suspicious file conduct
Google Cloud really useful the next defensive methods for cloud safety groups:
- Use id and entry administration (IAM) controls, proactive vulnerability administration, and commonly audit permissions.
- Look ahead to leaked credentials utilizing automated detection instruments.
- Keep a strong vulnerability and patch administration program.
- Monitor PDF information or readers launching command and scripting interpreters akin to powershell.exe, in addition to information saved in temp folders attempting to connect with your cloud storage service or opening paperwork.
- Separate signing atmosphere permissions from uploader permissions.
- Stay alert for .desktop information getting used because the boobytrapped PDFs, utilizing them as droppers whereas displaying innocent PDFs on the similar time.
“Whereas there’s no single silver bullet, the info persistently reveals that mastering the basics offers probably the most vital return on funding,” stated Crystal Lister, a safety advisor at Google Cloud Safety, in an e-mail to TechRepublic. “An enormous share of breaches, over 76% based on our newest analysis, start with fundamentals like weak credentials and misconfigurations. Earlier than specializing in refined nation-state actors, guarantee you’ve got a powerful id and entry administration and a strong safety posture to assist forestall the commonest assaults.”
Cloud backup segmentation can cut back danger
Google Cloud additionally prompt separating manufacturing and cloud-based backup infrastructure by designing separate VPC networks on your manufacturing and backup environments. Backup information will be replicated throughout geographical environments by way of frequent cloud providers.
Learn our picks for the 7 greatest encryption software program selections in 2025.


