
Ransomware gangs have lately joined ongoing assaults concentrating on a Microsoft SharePoint vulnerability chain, a part of a broader exploitation marketing campaign that has already led to the breach of not less than 148 organizations worldwide.
Safety researchers at Palo Alto Networks’ Unit 42 have found a 4L4MD4R ransomware variant, primarily based on open-source Mauri870 code, whereas analyzing incidents involving this SharePoint exploit chain (dubbed “ToolShell”).
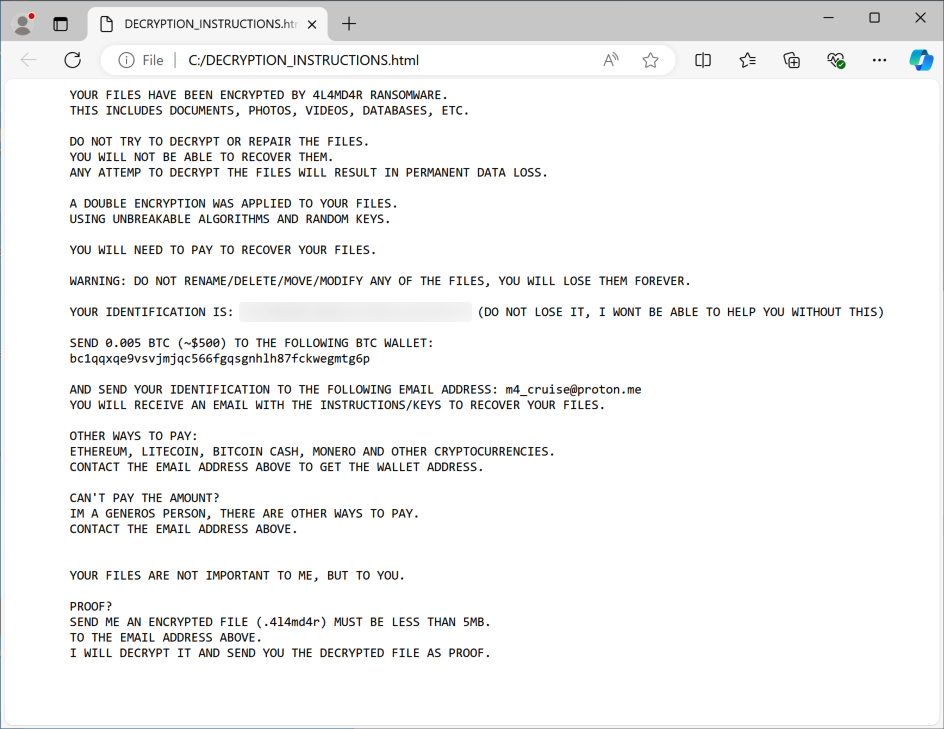
The ransomware was detected on July 27 after discovering a malware loader that downloads and executes the ransomware from theinnovationfactory[.]it (145.239.97[.]206).
The loader was noticed following a failed exploitation try that exposed malicious PowerShell instructions designed to disable safety monitoring on the focused system.
“Evaluation of the 4L4MD4R payload revealed that it’s UPX-packed and written in GoLang. Upon execution, the pattern decrypts an AES-encrypted payload in reminiscence, allocates reminiscence to load the decrypted PE file, and creates a brand new thread to execute it,” Unit 42 mentioned.
The 4L4MD4R ransomware encrypts recordsdata on the compromised system and calls for a fee of 0.005 Bitcoin, producing ransom notes and encrypted file lists on contaminated programs.
Microsoft and Google have additionally linked the ToolShell assaults to Chinese language menace actors, with Microsoft safety researchers naming three separate state-backed hacking teams: Linen Hurricane, Violet Hurricane, and Storm-2603.
To this point, quite a few high-profile targets have been compromised on this ongoing marketing campaign, together with the U.S. Nationwide Nuclear Safety Administration, the Division of Training, Florida’s Division of Income, the Rhode Island Basic Meeting, and authorities networks in Europe and the Center East.
“Microsoft has noticed two named Chinese language nation-state actors, Linen Hurricane and Violet Hurricane exploiting these vulnerabilities concentrating on internet-facing SharePoint servers,” Microsoft mentioned. “As well as, we’ve noticed one other China-based menace actor, tracked as Storm-2603, exploiting these vulnerabilities. Investigations into different actors additionally utilizing these exploits are nonetheless ongoing.”
Dutch cybersecurity agency Eye Safety first detected ToolShell exploitation concentrating on CVE-2025-49706 and CVE-2025-49704 in zero-day assaults, initially figuring out 54 compromised organizations, together with authorities entities and multinational firms. Verify Level Analysis subsequently revealed exploitation indicators courting to July 7, concentrating on authorities, telecommunications, and know-how organizations throughout North America and Western Europe.
Microsoft has patched the 2 flaws with the July 2025 Patch Tuesday updates and assigned two new CVE IDs (CVE-2025-53770 and CVE-2025-53771) for zero-days exploited to compromise totally patched SharePoint servers.
Eye Safety Chief Know-how Officer Piet Kerkhofs has additionally informed BleepingComputer that the precise scope extends far past preliminary estimates, with the agency’s information indicating that the attackers have contaminated not less than 400 servers with malware throughout the networks of not less than 148 organizations, a lot of which have been compromised for prolonged intervals.
The Cybersecurity and Infrastructure Safety Company (CISA) has added the CVE-2025-53770 distant code execution vulnerability, a part of the ToolShell exploit chain, to its catalog of exploited flaws and ordered federal businesses to safe their programs inside 24 hours.



