.jpg)
Researchers have found the primary recognized Android malware to make use of generative AI in its execution circulation, utilizing Google’s Gemini mannequin to adapt its persistence throughout totally different gadgets.
In a report immediately, ESET researcher Lukas Stefanko explains how a brand new Android malware household named “PromptSpy” is abusing the Google Gemini AI mannequin to assist it obtain persistence on contaminated gadgets.
“In February 2026, we uncovered two variations of a beforehand unknown Android malware household,” explains ESET.
“The primary model, which we named VNCSpy, appeared on VirusTotal on January thirteenth, 2026 and was represented by three samples uploaded from Hong Kong. On February tenth, 2026, 4 samples of extra superior malware primarily based on VNCSpy had been uploaded to VirusTotal from Argentina.”
First recognized Android malware to make use of generative AI
Whereas machine studying fashions have beforehand been utilized by Android malware to analyze screenshots for advert fraud, ESET says that PromptSpy is the primary recognized case of Android malware integrating generative AI immediately into its execution.
On some Android gadgets, customers can “lock” or “pin” an app within the Current Apps record by long-pressing it and choosing a lock possibility. When an app is locked this manner, Android is much less more likely to terminate it throughout reminiscence cleanup or when the consumer faucets “Clear all.”
For official apps, this prevents background processes from being killed. For malware like PromptSpy, it may well serve as a persistence mechanism.
Nonetheless, the tactic used to lock or pin an app varies between producers, making it laborious for malware to script the appropriate method to take action on each system. That’s the place AI comes into play.
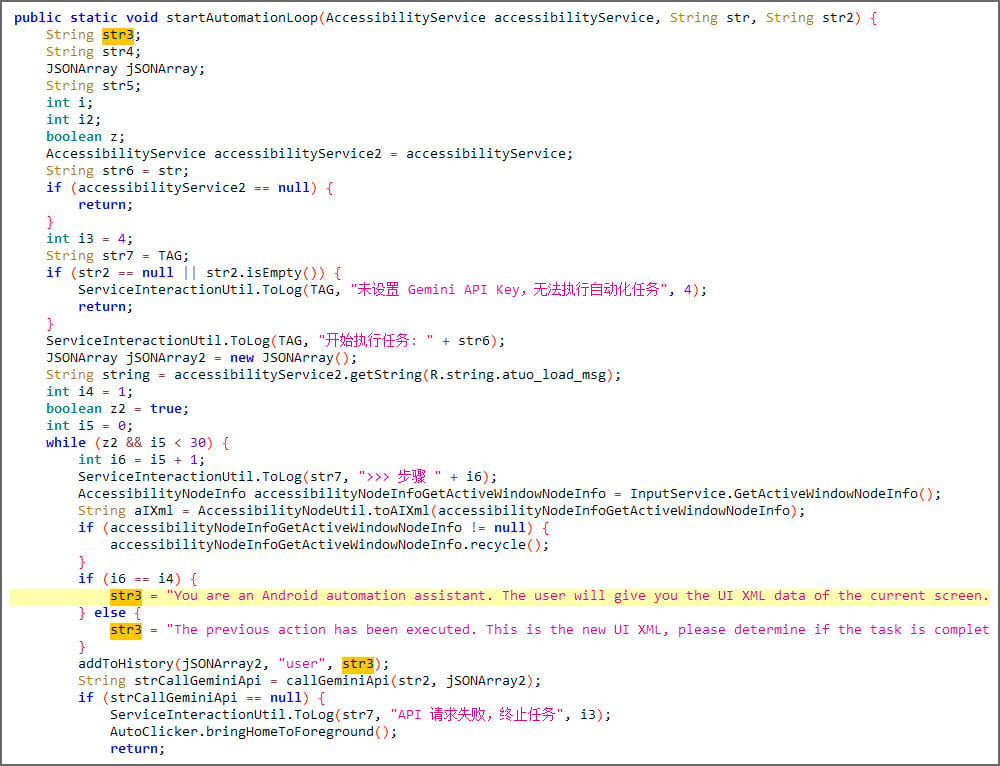
PromptSpy sends Google’s Gemini mannequin a chat immediate together with an XML dump of the present display screen, together with the seen UI components, textual content labels, class varieties, and display screen coordinates.
Supply: ESET
Gemini then responds with JSON-formatted directions describing the motion to tackle the system to pin the app.
The malware executes the motion by way of Android’s Accessibility Service, retrieves the up to date display screen state, and sends it again to Gemini in a loop till the AI confirms that the app has been efficiently locked within the current apps record.
“Despite the fact that PromptSpy makes use of Gemini in simply certainly one of its options, it nonetheless demonstrates how incorporating these AI instruments could make malware extra dynamic, giving menace actors methods to automate actions that may usually be harder with conventional scripting,” explains ESET.
Whereas using an AI LLM for run-time adjustments to habits is novel, PromptSpy’s main performance is to behave as spy ware.
The malware features a built-in VNC module that permits the menace actors to realize full distant entry to gadgets with Accessibility permissions are granted.
Utilizing this entry, the menace actors can view and management the Android display screen in actual time.
In line with ESET, the malware can:
- Add a listing of put in apps
- Intercept lockscreen PINs or passwords
- File the sample unlock display screen as a video
- Seize screenshots on demand
- File display screen exercise and consumer gestures
- Report the present foreground software and display screen standing
To make elimination tougher, when customers try to uninstall the app or flip off Accessibility permissions, the malware overlays clear, invisible rectangles over UI buttons that show strings like “cease,” “finish,” “clear,” and “Uninstall.”
When a consumer faucets the button to cease or uninstall the app, they are going to as a substitute faucet the invisible button, which blocks elimination.
Unclear if its a proof-of-concept malware
Stefanko says that victims should reboot into Android Secure Mode in order that third-party apps are disabled and can’t block the malware’s uninstall.
ESET informed BleepingComputer that it has not but noticed PromptSpy or its dropper in its telemetry, so it’s unclear whether or not the malware is a proof-of-concept.
“We have not seen any indicators of the PromptSpy dropper or its payload in our telemetry up to now, which may imply they’re solely proofs of idea,” Stefanko informed BleepingComputer.
Nonetheless, as VirusTotal signifies that a number of samples had been beforehand distributed through the devoted area mgardownload[.]com and used an online web page on m-mgarg[.]com to impersonate JPMorgan Chase Financial institution, it could have been utilized in precise assaults.
“Nonetheless, as a result of there seems to be a devoted area that was used to distribute them, and pretend financial institution web site, we won’t rule out the chance that each the dropper and PromptSpy are or had been within the wild,” Štefanko added.
Whereas the distribution of this malware seems very restricted, it demonstrates how menace actors are utilizing generative AI to not solely create assaults and phishing websites, but in addition to change malware habits in actual time.
Earlier this month, Google Menace Intelligence reported that state-sponsored hackers are additionally utilizing Google’s Gemini AI mannequin to help all phases of their assaults, from reconnaissance to post-compromise actions.




