
Greater than 28,200 Citrix situations are weak to a crucial distant code execution vulnerability tracked as CVE-2025-7775 that’s already being exploited within the wild.
The vulnerability impacts NetScaler ADC and NetScaler Gateway and the vendor addressed it in updates launched yesterday.
In line with the U.S. Cybersecurity and Infrastructure Safety Company (CISA) and Citrix, the safety concern has been exploited as a zero-day vulnerability.
The variations affected by CVE-2025-7775 are 14.1 earlier than 14.1-47.48, 13.1 before13.1-59.22, 13.1-FIPS/NDcPP earlier than 13.1-37.241-FIPS/NDcPP, and 12.1-FIPS/NDcPP as much as 12.1-55.330-FIPS/NDcPP.
Citrix doesn’t present any mitigations or workarounds and urges admins to improve the firmware instantly.
Web scans performed by the menace monitoring platform The Shadowserver Basis quickly after the flaw was disclosed present that there have been greater than 28,000 Citrix situations weak to CVE-2025-7775.
Many of the weak situations are positioned in america (10,100), adopted by Germany (4,300), the UK (1,400), the Netherlands (1,300), Switzerland (1,300), Australia (880), Canada (820), and France (600).
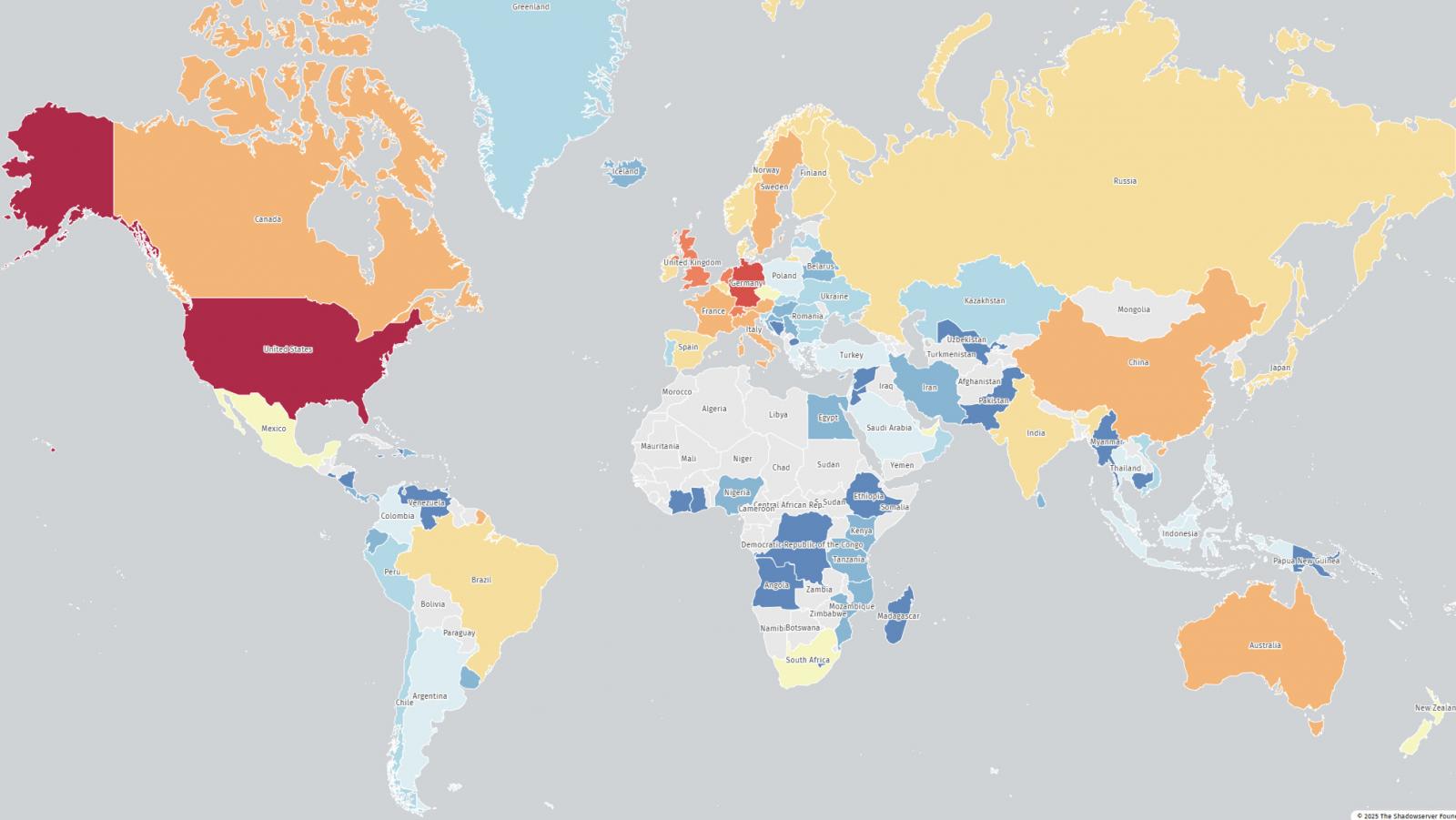
Supply: The Shadowserver Basis
Citrix didn’t share indicators of compromise related to the exploitation exercise.
Nonetheless, the seller specifies that CVE-2025-7775 impacts NetScaler when configured as a Gateway/AAA digital server (VPN, ICA Proxy, CVPN, RDP Proxy), as LB digital servers (HTTP/SSL/HTTP_QUIC) certain to IPv6 or DBS IPv6 companies, or as a CR digital server with kind HDX.
In any case, admins are really useful to improve to one of many following releases, which handle the difficulty:
- 14.1-47.48 and later
- 13.1-59.22 and later
- 13.1-FIPS / 13.1-NDcPP 13.1-37.241 and later
- 12.1-FIPS / 12.1-NDcPP 12.1-55.330 and later
Citrix additionally disclosed two different, high-severity flaws in its safety bulletin: CVE-2025-7776 (reminiscence overflow denial-of-service) and CVE-2025-8424 (improper entry management on the administration interface).
It’s famous that variations 12.1 and 13.0 (non-FIPS/NDcPP) are additionally weak; nevertheless, they’ve reached Finish of Life standing, so prospects nonetheless utilizing these variations should improve to a supported launch.
CISA has already added the crucial CVE-2025-7775 vulnerability to its Recognized Exploited Vulnerabilities (KEV) catalog. The company is giving federal businesses till August 28 to use the patches from the seller or give up utilizing the affected merchandise, underlining the severity of the difficulty and the chance related to exploitation.


