
Risk intelligence observations present {that a} single menace actor is liable for a lot of the energetic exploitation of two essential vulnerabilities in Ivanti Endpoint Supervisor Cell (EPMM), tracked as CVE-2026-21962 and CVE-2026-24061.
The safety points have been flagged as actively exploited in zero-day assaults in Ivanti’s safety advisory, the place the corporate additionally introduced hotfixes.
Each flaws acquired a essential severity score and permit an attacker to inject code with out authentication, resulting in distant code execution (RCE) on weak methods.
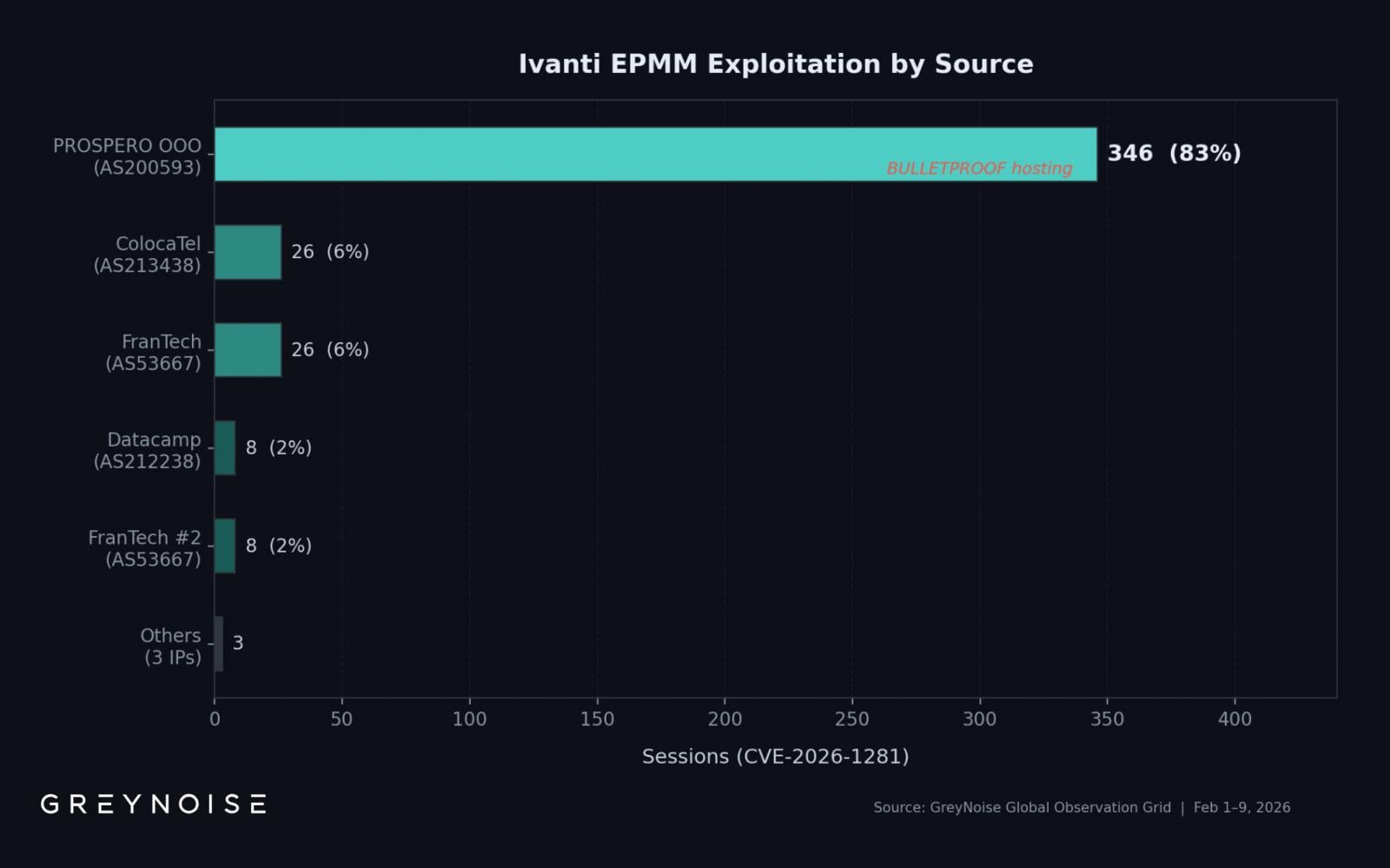
A single IP handle hosted on bulletproof infrastructure is liable for over 83% of exploitation exercise associated to the 2 vulnerabilities, says threat-focused web intelligence firm GreyNoise.
Between February 1st and ninth, the monitoring platform noticed 417 exploitation periods originating from 8 distinctive supply IP addresses, and centered on CVE-2026-21962 and CVE-2026-24061.
The very best quantity, 83%, comes from 193[.]24[.]123[.]42, hosted by PROSPERO OOO (AS200593), which Censys analysts marked as a bulletproof autonomous system used to focus on numerous software program merchandise.
Supply: GreyNoise
A pointy spike occurred on February 8, with 269 recorded periods in a single day. The determine is sort of 13 occasions the each day common of twenty-two periods, GreyNoise famous.
Of the 417 exploitation periods, 354 (85%) used OAST-style DNS callbacks to confirm command execution functionality, pointing to preliminary entry dealer exercise.
Curiously, a number of revealed indicators of compromise (IoCs) embody IP addresses for Windscribe VPN (185[.]212[.]171[.]0/24) current in GreyNoise telemetry as scanning Oracle WebLogic cases, however no Ivanti exploitation exercise.
The researchers word that the PROSPERO OOO IP handle they noticed “will not be on broadly revealed IOC lists, that means defenders blocking solely revealed indicators are seemingly lacking the dominant exploitation supply.”
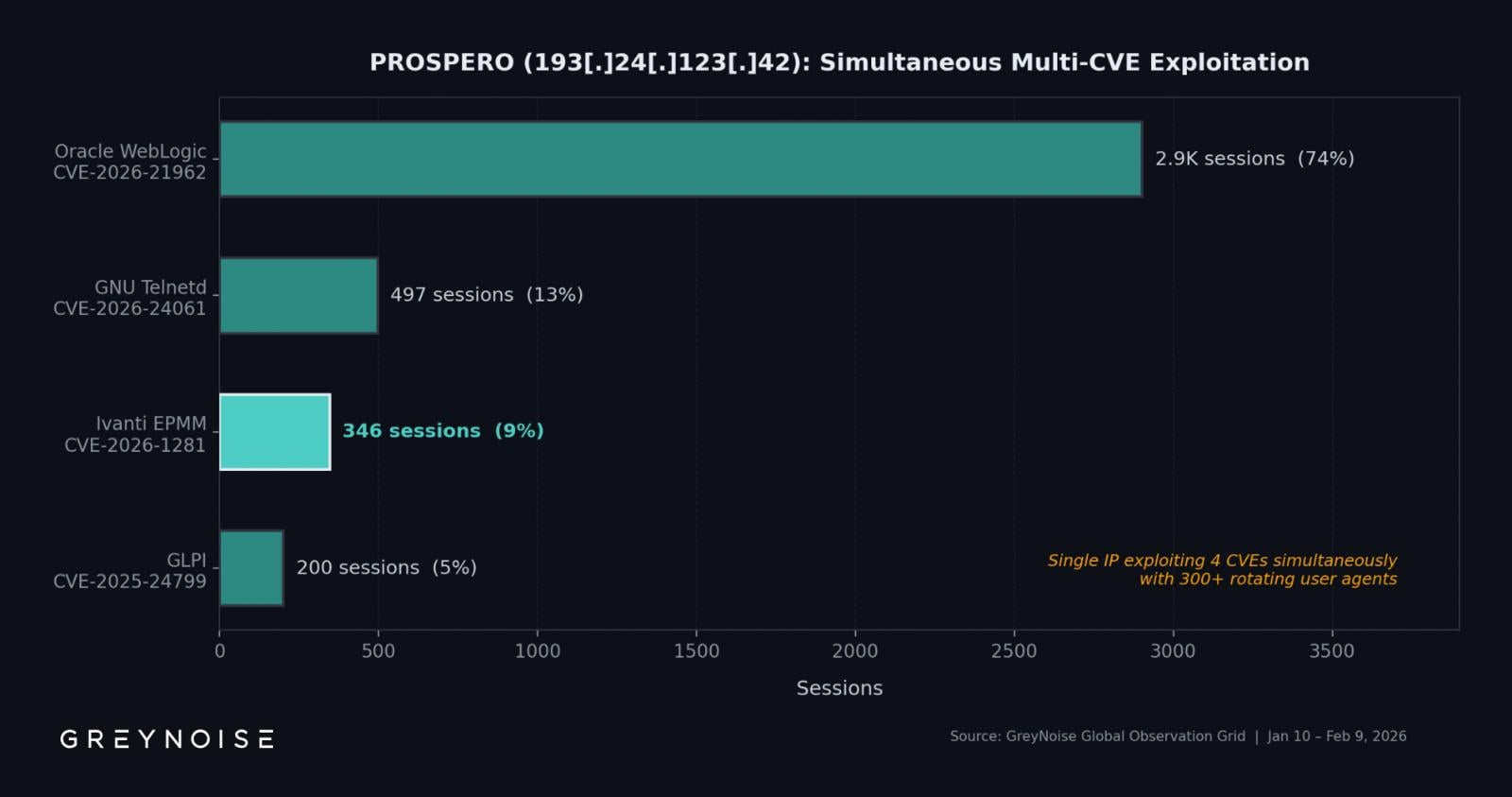
This IP will not be restricted to Ivanti focusing on, because it concurrently exploited three extra vulnerabilities: CVE-2026-21962 in Oracle WebLogic, CVE-2026-24061 in GNU Inetutils Telnetd, and CVE-2025-24799 in GLPI.
The Oracle WebLogic flaw had the lion’s share in session volumes, dwarfing the remaining with 2,902 periods, adopted by the Telnetd situation with 497 periods.
Exploitation exercise seems absolutely automated, rotating between 300 person brokers.
Supply: GreyNoise
Ivanti’s fixes for CVE-2026-1281 and CVE-2026-1340 are usually not everlasting. The corporate promised to launch full patches within the first quarter of this yr, with the discharge of EPMM model 12.8.0.0.
Till then, it is suggested to make use of RPM packages 12.x.0.x for EPMM variations 12.5.0.x, 12.6.0.x, and 12.7.0.x, and RPM 12.x.1.x for EPMM variations 12.5.1.0 and 12.6.1.0.
The seller notes that probably the most conservative strategy is to construct a alternative EPMM occasion and migrate all information there. Directions on how to do this are obtainable right here.
Trendy IT infrastructure strikes sooner than handbook workflows can deal with.
On this new Tines information, find out how your group can scale back hidden handbook delays, enhance reliability by means of automated response, and construct and scale clever workflows on high of instruments you already use.




