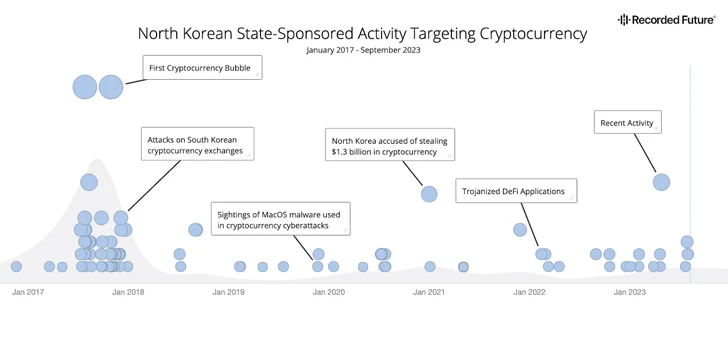
Risk actors from the Democratic Folks’s Republic of Korea (DPRK) are more and more focusing on the cryptocurrency sector as a main income era mechanism since not less than 2017 to get round sanctions imposed towards the nation.
“Though motion out and in of and throughout the nation is closely restricted, and its common inhabitants is remoted from the remainder of the world, the regime’s ruling elite and its extremely educated cadre of pc science professionals have privileged entry to new applied sciences and data,” cybersecurity agency Recorded Future mentioned in a report shared with The Hacker Information.
“The privileged entry to sources, applied sciences, info, and generally worldwide journey for a small set of chosen people with promise in arithmetic and pc science equips them with the required expertise for conducting cyber assaults towards the cryptocurrency business.”
The disclosure comes because the U.S. Treasury Division imposed sanctions towards Sinbad, a digital forex mixer that has been put to make use of by the North Korea-linked Lazarus Group to launder ill-gotten proceeds.
The menace actors from the nation are estimated to have stolen $3 billion price of crypto property over the previous six years, with about $1.7 billion plundered in 2022 alone. A majority of those stolen property are used to immediately fund the hermit kingdom’s weapons of mass destruction (WMD) and ballistic missile packages.
“$1.1 billion of that whole was stolen in hacks of DeFi protocols, making North Korea one of many driving forces behind the DeFi hacking pattern that intensified in 2022,” Chainalysis famous earlier this February.
A report revealed by the U.S. Division of Homeland Safety (DHS) as a part of its Analytic Change Program (AEP) earlier this September additionally highlighted the Lazarus Group’s exploitation of DeFi protocols.
“DeFi trade platforms enable customers to transition between cryptocurrencies with out the platform ever taking custody of the client’s funds as a way to facilitate the transition,” the report mentioned. “This enables DPRK cyber actors to find out precisely when to transition stolen cryptocurrency from one sort of cryptocurrency to a different, enabling attribution to be tougher to find out and even hint.”
The cryptocurrency sector is among the many high targets for state-sponsored North Korean cyber menace actors, as repeatedly evidenced by the myriad campaigns carried out in latest months.
DPRK hackers are identified for adeptly pulling off social engineering methods to focus on workers of on-line cryptocurrency exchanges after which lure their victims with the promise of profitable jobs to distribute malware that grants distant entry to the corporate’s community, finally permitting them to empty all obtainable property and transfer them to numerous DPRK managed wallets.
Different campaigns have employed comparable phishing ways to entice customers into downloading trojanized cryptocurrency apps to steal their property in addition to watering gap assaults (aka strategic internet compromises) as an preliminary entry vector, alongside partaking in airdrop scams and rug pulls.
One other notable tactic adopted by the group is use of blending providers to hide the monetary path and cloud attribution efforts. Such providers are sometimes supplied on cryptocurrency trade platforms that don’t make use of know your buyer (KYC) insurance policies or anti-money laundering (AML) rules.
“Absent stronger rules, cybersecurity necessities, and investments in cybersecurity for cryptocurrency companies, we assess that within the close to time period, North Korea will nearly definitely proceed to focus on the cryptocurrency business because of its previous success in mining it as a supply of further income to assist the regime,” Recorded Future concluded.