Cybersecurity researchers have found a beforehand undocumented superior backdoor dubbed Deadglyph employed by a risk actor often called Stealth Falcon as a part of a cyber espionage marketing campaign.
“Deadglyph’s structure is uncommon because it consists of cooperating parts – one a local x64 binary, the opposite a .NET meeting,” ESET mentioned in a new report shared with The Hacker Information.
“This mix is uncommon as a result of malware sometimes makes use of just one programming language for its parts. This distinction may point out separate improvement of these two parts whereas additionally benefiting from distinctive options of the distinct programming languages they make the most of.”
It is also suspected that using completely different programming languages is a deliberate tactic to hinder evaluation, making it much more difficult to navigate and debug.
Not like different conventional backdoors of its variety, the instructions are obtained from an actor-controlled server within the type of further modules that enable it to create new processes, learn information, and acquire info from the compromised methods.
Stealth Falcon (aka FruityArmor) was first uncovered by the Citizen Lab in 2016, linking it to a set of focused spyware and adware assaults within the Center East aimed toward journalists, activists, and dissidents within the U.A.E. utilizing spear-phishing lures embedding booby-trapped hyperlinks pointing to macro-laced paperwork to ship a customized implant able to executing arbitrary instructions.

A subsequent investigation undertaken by Reuters in 2019 revealed a clandestine operation referred to as Challenge Raven that concerned a bunch of former U.S. intelligence operatives who have been recruited by a cybersecurity agency named DarkMatter to spy on targets vital of the Arab monarchy.
Stealth Falcon and Challenge Raven are believed to be the identical group based mostly on the overlaps in ways and concentrating on.
The group has since been linked to the zero-day exploitation of Home windows flaws resembling CVE-2018-8611 and CVE-2019-0797, with Mandiant noting in April 2020 that the espionage actor “used extra zero-days than another group” from 2016 to 2019.
Across the similar time, ESET detailed the adversary’s use of a backdoor named Win32/StealthFalcon that was discovered to make use of the Home windows Background Clever Switch Service (BITS) for command-and-control (C2) communications and to realize full management of an endpoint.
Deadglyph is the newest addition to Stealth Falcon’s arsenal, in response to the Slovak cybersecurity agency, which analyzed an intrusion at an unnamed governmental entity within the Center East.
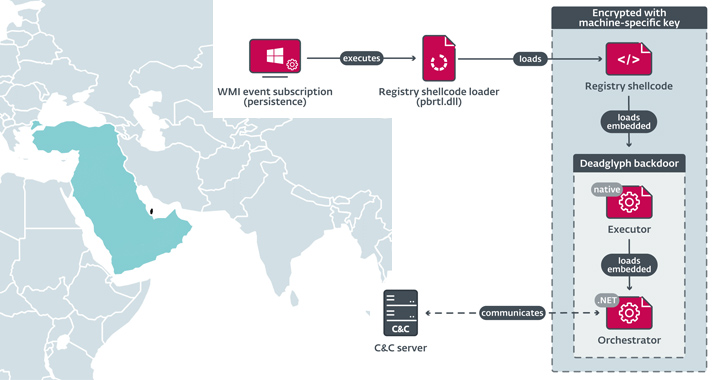
The precise technique used to ship the implant is at present unknown, however the preliminary part that prompts its execution is a shellcode loader that extracts and masses shellcode from the Home windows Registry, which subsequently launches Deadglyph’s native x64 module, known as the Executor.
The Executor then proceeds with loading a .NET part often called the Orchestrator that, in flip, communicates with the command-and-control (C2) server to await additional directions. The malware additionally engages in a collection of evasive maneuvers to fly underneath the radar, counting the power to uninstall itself.
The instructions obtained from the server are queued for execution and may fall into one in every of three classes: Orchestrator duties, Executor duties, and Add duties.
“Executor duties provide the power to handle the backdoor and execute further modules,” ESET mentioned. “Orchestrator duties provide the power to handle the configuration of the Community and Timer modules, and likewise to cancel pending duties.”
AI vs. AI: Harnessing AI Defenses Towards AI-Powered Dangers
Able to deal with new AI-driven cybersecurity challenges? Be a part of our insightful webinar with Zscaler to deal with the rising risk of generative AI in cybersecurity.
Among the recognized Executor duties comprise course of creation, file entry, and system metadata assortment. The Timer module is used to ballot the C2 server periodically together with the Community module, which implements the C2 communications utilizing HTTPS POST requests.
Add duties, because the title implies, enable the backdoor to add the output of instructions and errors.
ESET mentioned it additionally recognized a management panel (CPL) file that was uploaded to VirusTotal from Qatar, which is claimed to have functioned as a place to begin for a multi-stage chain that paves the way in which for a shellcode downloader that shares some code resemblances with Deadglyph.
Whereas the character of the shellcode retrieved from the C2 server stays unclear, it has been theorized that the content material may doubtlessly function the installer for the Deadglyph malware.
Deadglyph will get its title from artifacts discovered within the backdoor (hexadecimal IDs 0xDEADB001 and 0xDEADB101 for the Timer module and its configuration), coupled with the presence of a homoglyph assault impersonating Microsoft (“Ϻicrоsоft Corpоratiоn”) within the Registry shellcode loader’s VERSIONINFO useful resource.
“Deadglyph boasts a variety of counter-detection mechanisms, together with steady monitoring of system processes and the implementation of randomized community patterns,” the corporate mentioned. “Moreover, the backdoor is able to uninstalling itself to attenuate the probability of its detection in sure instances.”