
Microsoft has launched a PowerShell script to assist restore an empty ‘inetpub’ folder created by the April 2025 Home windows safety updates if deleted. As Microsoft beforehand warned, this folder helps mitigate a high-severity Home windows Course of Activation privilege escalation vulnerability.
In April, after putting in the brand new safety updates, Home windows customers immediately discovered that an empty C:Inetpub folder was created. As this folder is related to Microsoft’s Web Info Server, customers discovered it complicated that it was created when the net server was not put in.
This brought about some folks to take away the folder, making them susceptible once more to the patched vulnerability. Microsoft mentioned that customers who eliminated it can manually recreate it by putting in Web Info Providers from the Home windows “Flip Home windows Options on or off” management panel.
As soon as IIS is put in, a brand new inetpub folder shall be added to the foundation of the C: drive, with recordsdata and the identical SYSTEM possession because the listing created by the April Home windows safety updates. Additionally, in the event you do not use IIS, you’ll be able to uninstall it utilizing the identical Home windows Options management panel to take away it, leaving the C:inetpub folder behind.
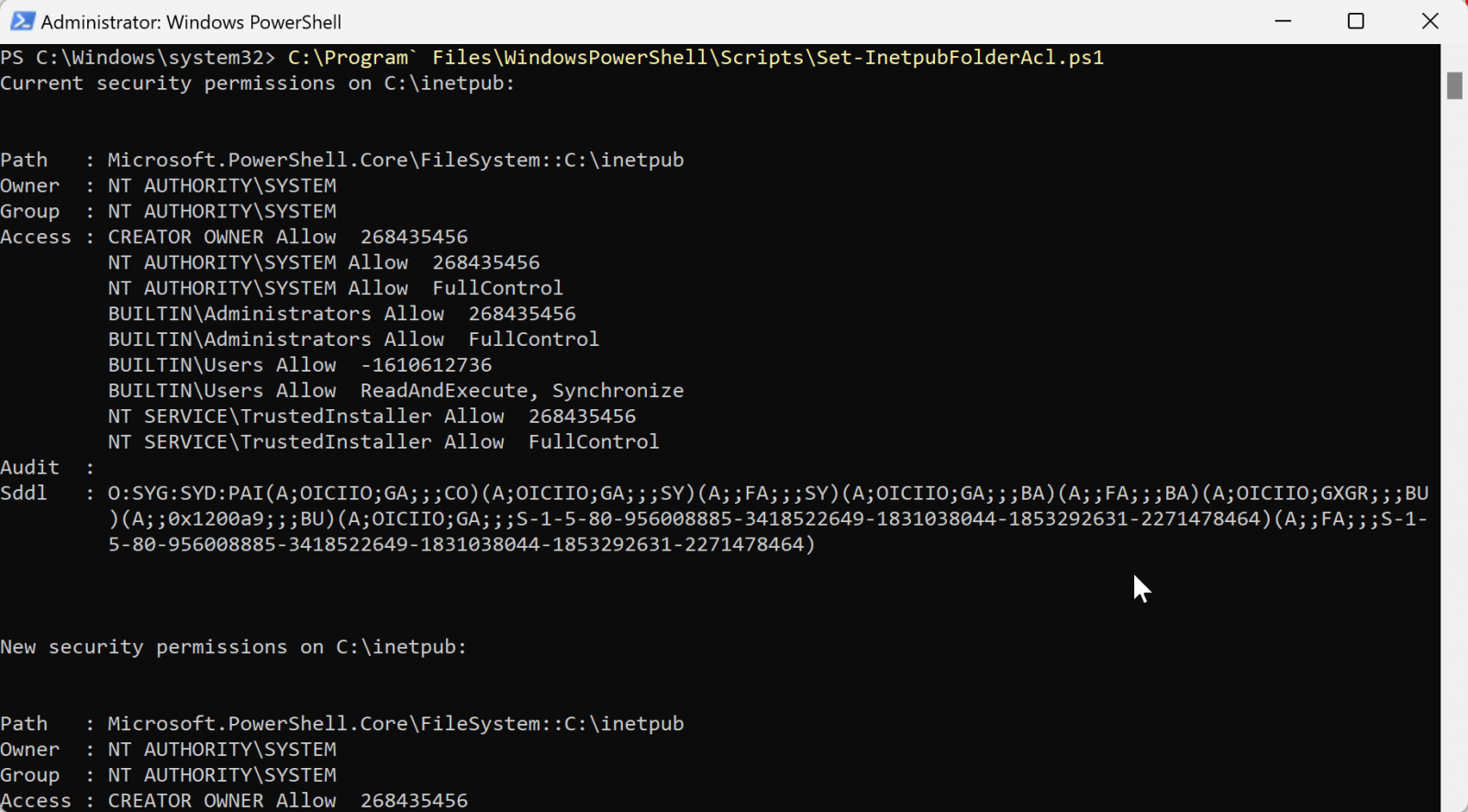
On Wednesday, in a brand new replace to the CVE-2025-21204 advisory, the corporate additionally shared a remediation script that helps admins re-create this folder from a PowerShell shell utilizing the next instructions:
Set up-Script -Identify Set-InetpubFolderAcl
C:Program` FilesWindowsPowerShellScriptsSet-InetpubFolderAcl.ps1As Redmond explains, the script will set the proper IIS permissions to stop unauthorized entry and potential vulnerabilities associated to CVE-2025-21204.
It would additionally replace entry management record (ACL) entries for the DeviceHealthAttestation listing on Home windows Server techniques to make sure it’s safe if created by the February 2025 safety updates.
Microsoft: “Do not delete it.”
The safety flaw (CVE-2025-21204) mitigated by this inetpub folder (mechanically created by April’s safety updates even on techniques the place the IIS net server platform was not beforehand put in) is attributable to an improper hyperlink decision difficulty within the Home windows Replace Stack.
This doubtless signifies that Home windows Replace could observe symbolic hyperlinks on unpatched units in a approach that may let native attackers trick the OS into accessing or modifying unintended recordsdata or folders.
Microsoft says profitable exploitation permits attackers with low privileges to escalate permissions and manipulate or carry out file administration operations within the context of the NT AUTHORITYSYSTEM account.
Whereas eradicating the folder didn’t trigger points utilizing Home windows in our exams, Microsoft advised BleepingComputer it was deliberately created and shouldn’t be deleted. Redmond issued the identical warning in an up to date advisory for the CVE-2025-21204 safety flaw to warn customers to not delete the empty %systemdrivepercentinetpub folder.
“This folder shouldn’t be deleted no matter whether or not Web Info Providers (IIS) is energetic on the goal gadget. This conduct is a part of adjustments that enhance safety and doesn’t require any motion from IT admins and finish customers,” the corporate cautioned.
Cybersecurity professional Kevin Beaumont additionally demonstrated that non-admin customers can abuse this folder to dam Home windows updates from being put in by making a junction between C:inetpub and any Home windows file.


