
A number of menace actors are compromising Microsoft 365 accounts in phishing assaults that leverage the OAuth system code authorization mechanism.
Attackers trick victims into getting into a tool code on Microsoft’s reliable system login web page, unknowingly authorizing an attacker-controlled software and granting them entry to the goal account with out stealing credentials or bypassing multi-factor authentication (MFA).
Though the tactic isn’t new, e-mail safety agency Proofpoint says that these assaults have elevated considerably in quantity since September, and contain each financially motivated cybercriminals like TA2723 and state-aligned menace actors.
“Proofpoint Menace Analysis has noticed a number of menace clusters utilizing system code phishing to trick customers into granting a menace actor entry to their Microsoft 365 account,” the safety firm warned, including that widespread campaigns utilizing these assault flows are “extremely uncommon.”
Instruments and campaigns
The assault chains that Proofpoint noticed within the campaigns have slight variations, however all of them contain tricking victims into getting into a tool code on Microsoft’s reliable system login portals.
In some instances, the system code is offered as a one-time password, whereas the lure generally is a token re-authorization notification in others.
The researchers noticed two phishing kits used within the assaults, specifically SquarePhish v1 and v2, and Graphish, which simplify the phishing course of.
SquarePhish is a publicly obtainable purple teaming device that targets OAuth system grant authorization flows by way of QR codes, mimicking reliable Microsoft MFA/TOTP setups.
Graphish is a malicious phishing equipment shared on underground boards, supporting OAuth abuse, Azure App Registrations, and adversary-in-the-middle (AiTM) assaults.
Concerning the campaigns Proofpoint noticed, the researchers highlighted three within the report:
- Wage bonus assaults – A marketing campaign utilizing document-sharing lures and localized firm branding to entice recipients to click on hyperlinks to attacker-controlled web sites. Victims are then instructed to finish “safe authentication” by getting into a offered code on Microsoft’s reliable system login web page, which authorizes an attacker-controlled software.
.jpg)
Supply: Proofpoint
- TA2723 assaults – An actor concerned in high-volume credential-phishing, beforehand identified for spoofing Microsoft OneDrive, LinkedIn, and DocuSign, that began utilizing OAuth system code phishing in October. Proofpoint assesses that early phases of those campaigns probably used SquarePhish2, with later waves doubtlessly shifting to the Graphish phishing equipment.
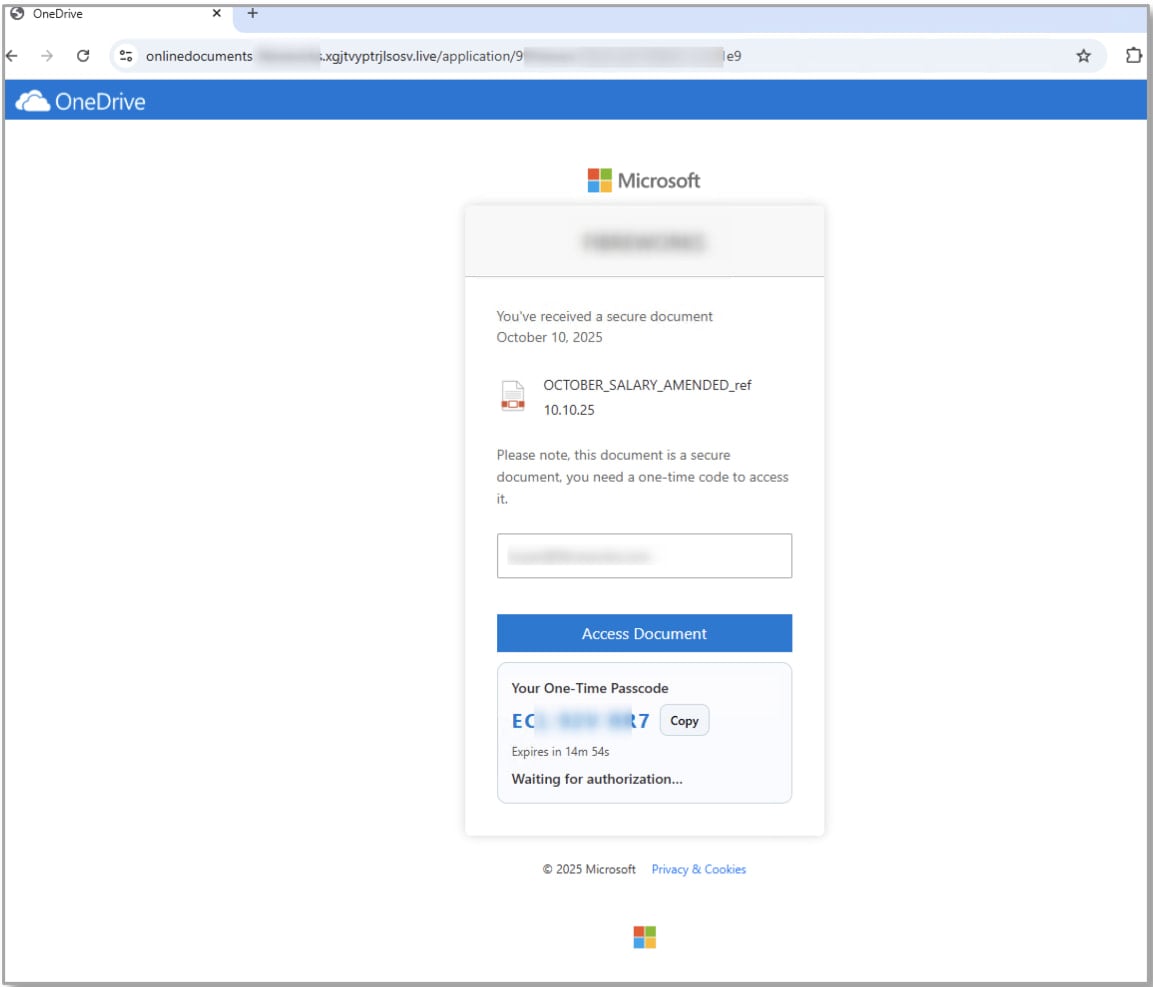
Supply: Proofpoint
- State-aligned exercise – Since September 2025, Proofpoint noticed a suspected Russia-aligned menace actor tracked as UNK_AcademicFlare abusing OAuth system code authorization for account takeover. The actor makes use of compromised authorities and army e-mail accounts to construct rapport earlier than sharing hyperlinks that spoof OneDrive, main victims into a tool code phishing workflow. The exercise primarily targets authorities, tutorial, suppose tank, and transportation sectors within the U.S. and Europe.
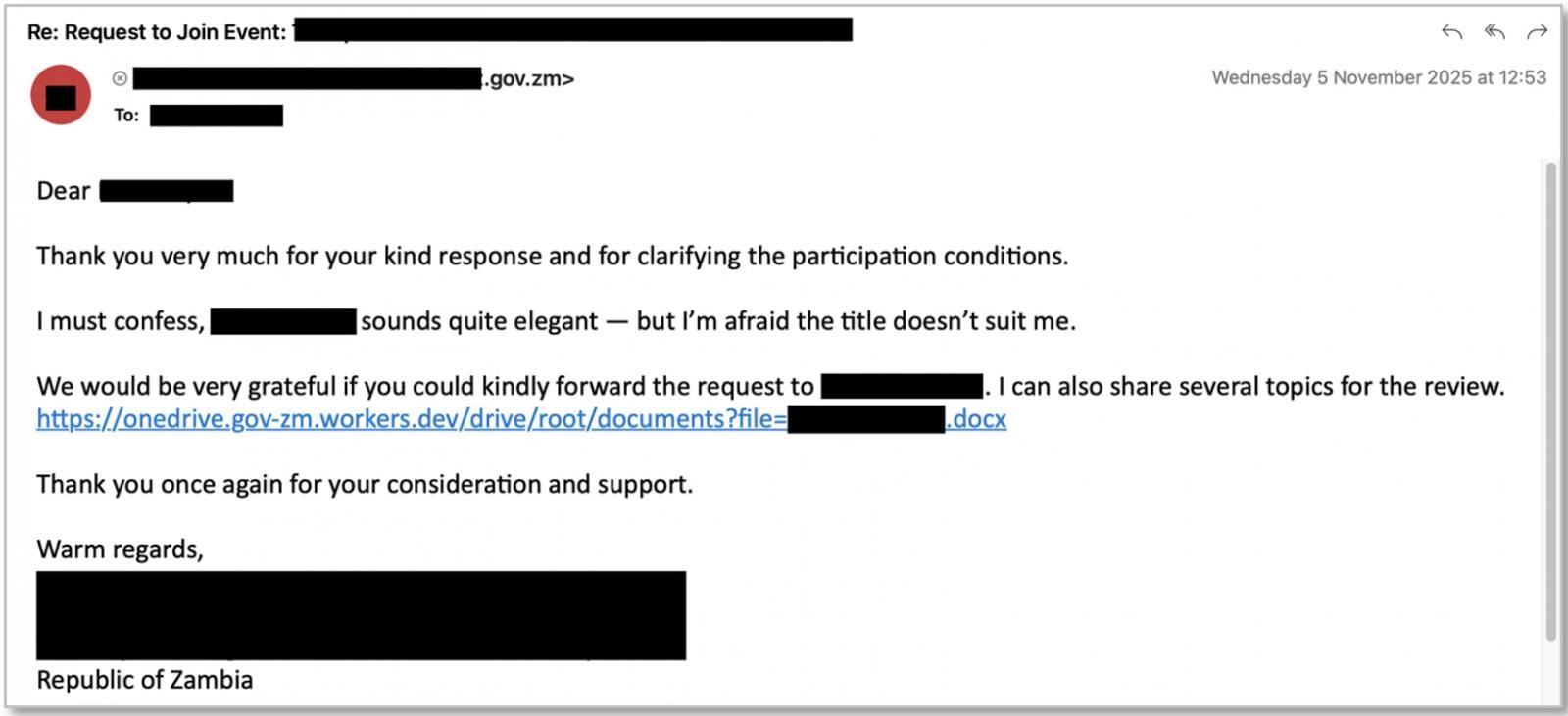
Supply: Proofpoint
To dam these assaults, Proofpoint recommends that organizations use Microsoft Entra Conditional Entry the place doable and think about introducing a coverage on sign-in origin.
Damaged IAM is not simply an IT downside – the impression ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with trendy calls for, examples of what “good” IAM appears like, and a easy guidelines for constructing a scalable technique.




