
Virtually a dozen malicious extensions with 1.7 million downloads in Google’s Chrome Internet Retailer may observe customers, steal browser exercise, and redirect to doubtlessly unsafe net addresses.
Many of the add-ons present the marketed performance and pose as professional instruments like colour pickers, VPNs, quantity boosters, and emoji keyboards.
Researchers at Koi Safety, an organization offering a platform for safety self-provisioned software program, found the malicious extensions in Chrome Internet Retailer and reported them to Google.
A number of the extensions are not current however lots of them proceed to be obtainable.
Supply: BleepingComputer
A lot of these extensions are verified, have a whole lot of constructive critiques, and are featured prominently on the Chrome Internet Retailer, deceptive customers about their security.
Customers ought to verify for the next add-ons in Chrome browser and take away them as quickly as attainable:
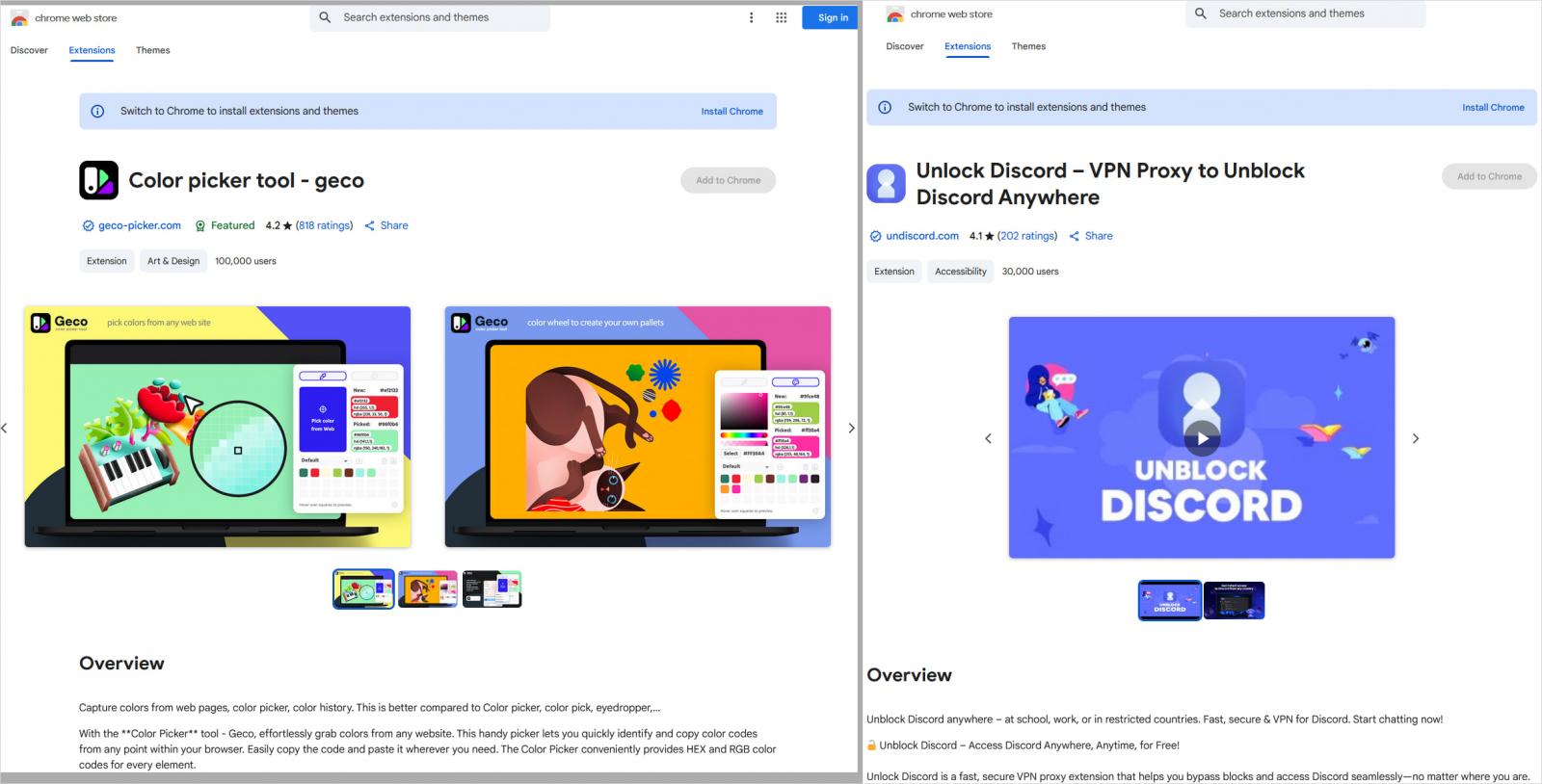
- Colour Picker, Eyedropper — Geco colorpick
- Emoji keyboard on-line — copy&paste your emoji
- Free Climate Forecast
- Video Velocity Controller — Video supervisor
- Unlock Discord — VPN Proxy to Unblock Discord Anyplace
- Darkish Theme — Darkish Reader for Chrome
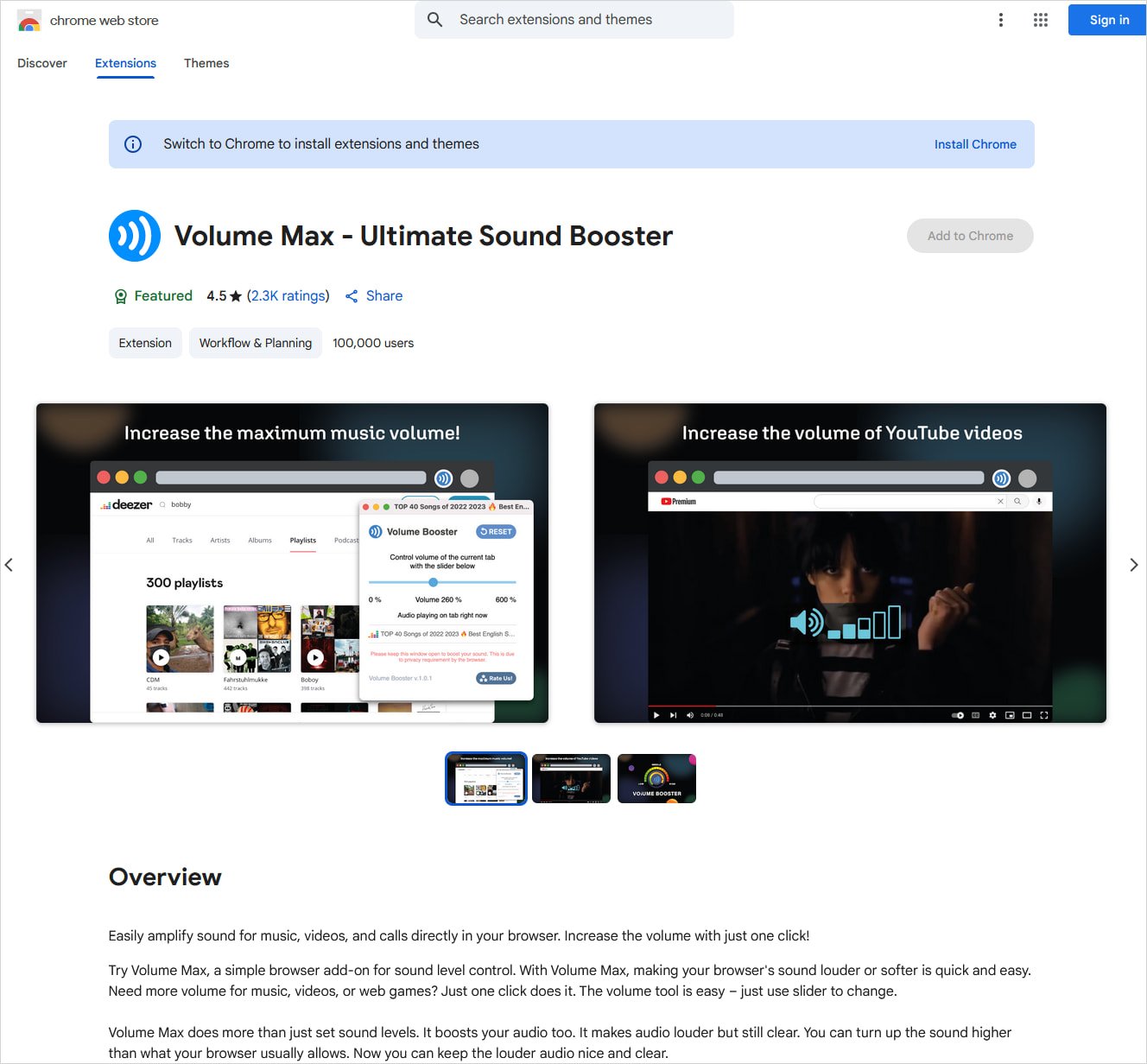
- Quantity Max — Final Sound Booster
- Unblock TikTok — Seamless Entry with One-Click on Proxy
- Unlock YouTube VPN
- Unlock TikTok
- Climate
Certainly one of them, ‘Quantity Max — Final Sound Booster,’ has additionally been flagged by LayerX researchers final month, who warned about its potential for spying on customers; however no malicious exercise might be confirmed on the time.
Supply: BleepingComputer
Based on the researchers, the malicious performance is carried out within the background service employee of every extension utilizing the Chrome Extensions API, registering a listener that’s triggered each time a person navigates to a brand new webpage.
The listener captures the URL of the visited web page and exfiltrates the knowledge to a distant server together with a singular monitoring ID for every person.
The server can reply with redirection URLs, hijacking the person’s searching exercise and doubtlessly taking them to unsafe locations which will allow cyberattacks.
Though the likelihood is there, it ought to be famous that Koi Safety has not noticed malicious redirections of their testing.
Moreover, the malicious code was not current within the preliminary variations of the extensions, however was launched at a later time by way of updates.
Google’s auto-update system silently deploys the latest variations to customers with out requiring any person approval or interplay.
Provided that a few of these extensions had been secure for years, it’s attainable that they had been hijacked/compromised by exterior actors who launched the malicious code.
BleepingComputer contacted a number of publishers to inquire about this risk, however we’ve got not but heard again from any of them.
Earlier than publishing this text, Koi Safety researchers found that cybercriminals have additionally planted malicious extensions within the official retailer for Microsoft Edge, which reveals a complete depend of 600,000 downloads.
“Mixed, these eighteen extensions have contaminated over 2.3 million customers throughout each browsers, creating one of many largest browser hijacking operations we’ve documented,” the researchers say.
They advocate customers take away all listed extensions instantly, clear the searching knowledge to purge any monitoring identifiers, verify the system for malware, and monitor accounts for suspicious exercise.



