Figuring out Your Software program Provide Chain
Software program complexity is rising at unprecedented ranges. The typical software program provide chain now incorporates artifacts from open-source repositories, internally developed code, software program developed by third-parties, and commercial-off-the-shelf (COTS) software program. All of this combines to run your corporation.
The questions surrounding the software program provide chain vary from its visibility to its trustworthiness to the origin of the bits and bytes. The 2025 LevelBlue Knowledge Accelerator: Software program Provide Chain and Cybersecurity takes an empirical take a look at how organizations understand visibility, put money into, and are ready to remediate assaults of their software program provide chain.
Attackers Know Your Software program Provide Chain Weaknesses
Throughout organizations, there are similarities within the software program provide chain that attackers can simply determine and exploit. Adversaries are on the lookout for a straightforward method into your group by unpatched software program, insecure and customary third-party APIs, or recognized open-source vulnerabilities.
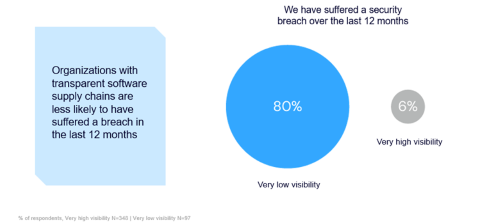
Gaining entry by these recognized vulnerabilities enable adversaries to infiltrate your methods by the final mile; your software program. A key factor in thwarting these assaults on the software program provide chain is larger visibility. LevelBlue’s new analysis finds that organizations with clear software program provide chains are much less prone to undergo a breach. The information reveals that 80% of organizations with low software program provide chain visibility have suffered a breach over the previous 12 months in comparison with solely 6% of these with excessive visibility struggling a breach in the identical timeframe.
Obtain your complimentary copy of the brand new LevelBlue Knowledge Accelerator: Software program Provide Chain and Cybersecurity to study extra in regards to the want for visibility of the software program provide chain.
Is Anybody Actually Ready for Software program Provide Chain Assaults?
Software program provide chain assaults are on the rise and can proceed to be a primary entry level for adversaries.
The brand new LevelBlue analysis examined software program provide chain:
- Visibility
- Funding
- Chance of assault
- Preparedness for remediation
- Engagement with software program suppliers about safety credentials
The outcomes are shocking with:
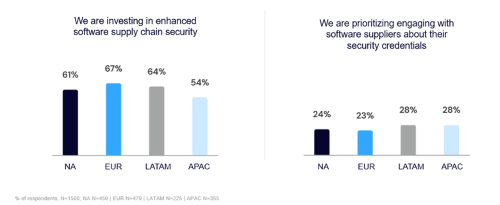
- Low visibility
- Excessive funding
- Excessive chance of assault
- Excessive stage of confidence for remediation of assault
- Low engagement with software program suppliers about their safety credentials
This seeming disconnect in visibility, funding, and preparedness is constant world wide. How is your group making ready and planning for a software program provide chain assault?
Construct a Framework for Software program Provide Chain Preparedness
Use the LevelBlue analysis to assist your group put together for assaults in opposition to the software program provide chain by following these 4 prompt steps.
1. Interact Executives – The C-suite is conscious of the dangers posed by low visibility of the software program provide chain and understands it as a enterprise crucial. Use this alignment to safe assets and speed up transformation.
2. Map Your Provide Chain Dependencies – Conduct cross-functional danger assessments to uncover probably the most weak areas in your provider and growth pipelines. Align your groups on short-term visibility targets and long-term danger discount.
3. Spend money on the Applicable Expertise – Implement risk detection, vulnerability administration, and AI-driven publicity administration and evaluation.
4. Demand Transparency from Suppliers – Interact the suppliers of your software program provide chain in common safety critiques. Require a software program invoice of fabric (SBOM), assess their safety posture, and require steady compliance.
Obtain Your Complimentary Copy of the New Analysis
The 2025 LevelBlue Knowledge Accelerator Report gives region-specific knowledge, C-suite insights, and a roadmap for enhancing your software program provide chain visibility.
Proceed to ship enterprise impression by cyber resilience by securing your software program provide chain.
The content material supplied herein is for normal informational functions solely and shouldn’t be construed as authorized, regulatory, compliance, or cybersecurity recommendation. Organizations ought to seek the advice of their very own authorized, compliance, or cybersecurity professionals relating to particular obligations and danger administration methods. Whereas LevelBlue’s Managed Menace Detection and Response options are designed to assist risk detection and response on the endpoint stage, they aren’t an alternative to complete community monitoring, vulnerability administration, or a full cybersecurity program.


