
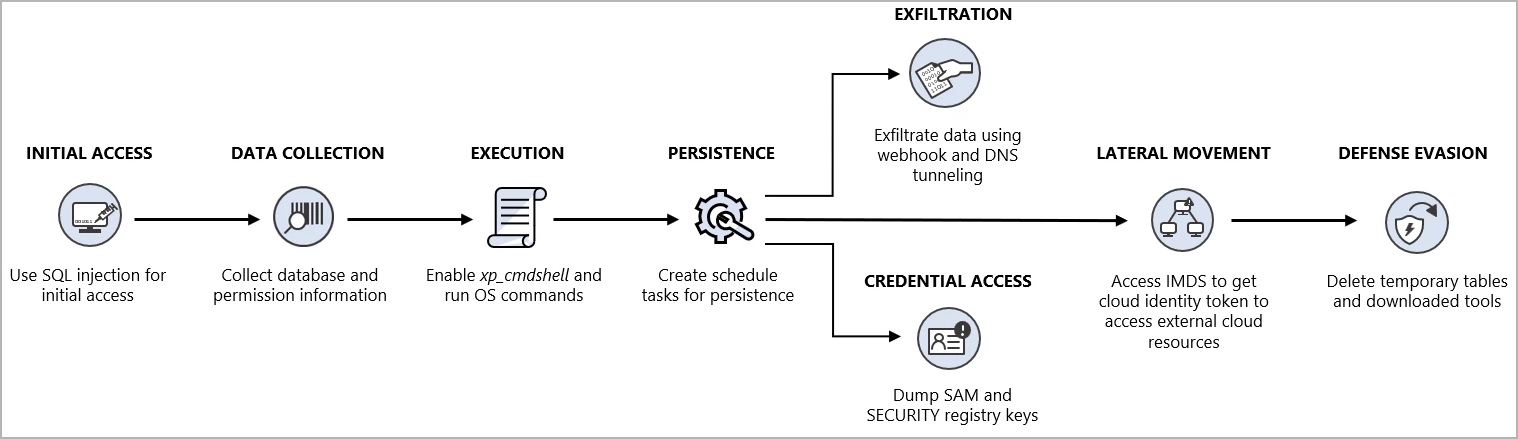
Hackers have been noticed attempting to breach cloud environments by Microsoft SQL Servers weak to SQL injection.
Microsoft’s safety researchers report that this lateral motion approach has been beforehand seen in assaults on different providers like VMs and Kubernetes clusters.
Nonetheless, that is the primary time they’ve seen SQL Servers leveraged for this objective.
Assault chain
The assaults Microsoft noticed begin with exploiting an SQL injection vulnerability in an software within the goal’s atmosphere.
This allows the risk actors to realize entry to the SQL Server occasion hosted on Azure Digital Machine with elevated permissions to execute SQL instructions and extract helpful information.
This consists of information on databases, desk names, schemas, database variations, community configuration, and skim/write/delete permissions.
If the compromised software has elevated permissions, the attackers could activate the ‘xp_cmdshell’ command to run working system (OS) instructions through SQL, giving them a shell within the host.
The instructions executed by the attackers at this stage embody the next:
- Learn directories, listing processes, and test community shares.
- Obtain encoded and compressed executables and PowerShell scripts.
- Arrange a scheduled job to launch a backdoor script.
- Retrieve person credentials by dumping SAM and SECURITY registry keys.
- Exfiltrate information utilizing a singular technique that entails the ‘webhook.website’ free service, which facilitates HTTP request and electronic mail inspection and debugging.
Utilizing a legit service for information exfiltration makes the exercise much less more likely to seem suspicious or elevate any flags by safety merchandise, permitting the attackers to discreetly steal information from the host.
Subsequent, the attackers tried to take advantage of the cloud id of the SQL Server occasion to entry the IMDS (Instantaneous Metadata Service) and procure the cloud id entry key.
In Azure, sources are sometimes assigned managed identities for authentication with different cloud sources and providers. If the attackers maintain that token, they’ll use it to entry any cloud useful resource the id has permissions to.
Microsoft says the attackers didn’t efficiently leverage this system as a result of errors, however the method stays legitimate and constitutes a dire risk to organizations.
Lastly, the risk actors deleted any downloaded scripts and wiped non permanent database modifications to erase traces of the assault.
Defending suggestions
Microsoft suggests utilizing Defender for Cloud and Defender for Endpoint to catch SQL injections and suspicious SQLCMD exercise, each employed within the noticed assault.
To mitigate the risk, Microsoft recommends making use of the precept of least privilege when granting person permissions, which at all times provides friction in lateral motion makes an attempt.
Searching queries for 365 Defender and Sentinel are offered within the appendix of Microsoft’s report.

